A company wants to implement a wireless infrastructure on its campus to meet the needs of its BYOD initiative. The company has users with legacy devices and wants to accommodate them while delivering speed to other users who have modern systems.
Which of the following standards BEST fits these requirements?
- A . 802.11a
- B . 802.11ac
- C . 802.11b
- D . 802.11g
A network technician has deployed an application that can remotely control desktops with different operating systems. The technician needs to be able to use a single client application for this control .
Which of the following has the technician utilized?
- A . RDP
- B . VPN
- C . VNC
- D . SSH
Which of the following protocols is used to transport outgoing mail across networks?
- A . POP
- B . SMTP
- C . IMAP
- D . LDAP
The help desk is receiving erase the hard drive to eliminate to a server. A help desk technician suspects the server Is unable to establish a three-way handshake due to a DoS attack .
Which of the following commands should a network administrator use to confirm the help desk technician’s claim?
- A . nmap
- B . arp
- C . tcpdump
- D . dig
A network technician is assisting a user who is having problems accessing a particular website. Other users are reporting that the website is accessible outside of the office. The technician suspects the problem is with the company’s firewall .
Which of the following should the technician use to troubleshoot?
- A . WiFi analyzer
- B . Bandwidth speed tester
- C . Dig
- D . Packet sniffer
A remote user is required to upload weekly reports to a server at the main office. Both the remote user and the server are using a Windows-based OS .
Which of the following represents the BEST method for the remote user to connect to the server?
- A . RDP
- B . Telnet
- C . SSH
- D . VNC
A technician is trying to identify the cause of an issue several wireless users are experiencing at an office. The office is in a square-shaped building, with four 802.11b WAPs with omnidirectional antennas located in the four corners of the building. Users near the center of the building report sporadic issues connecting to resources. The technician checks the signal strength in the middle of the building and determines it is adequate .
Which of the following is causing the reported issue?
- A . The antenna types are incorrect, and unidirectional should be used.
- B . MAC filtering has not been updated.
- C . There is channel overlap of the access points.
- D . The power levels are set too low on the WAPs.
A small team is overloaded with requests for database resources. The Chief Information Officer (CIO) is concerned the company does not have the resources to deploy and manage these additional services efficiently .
Which of the following types of cloud services would be the MOST effective?
- A . PaaS
- B . IaaS
- C . BaaS
- D . SaaS
A network technician is performing a firmware upgrade on a switch. The firmware needs to be downloaded to the device .
Which of the following methods should the technician use to retrieve the updated firmware?
- A . RDP
- B . SSH
- C . TFTP
- D . Telnet
HOTSPOT
You have been tasked with testing a CAT5e cable.
A summary of the test results can be found on the screen.
Instructions
Step 1: Select the tool that was used to create the cable test results.
Step 2: Interpret the test results and select the option that explains the results. After you are done with your analysis, click the ‘Submit’ button.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
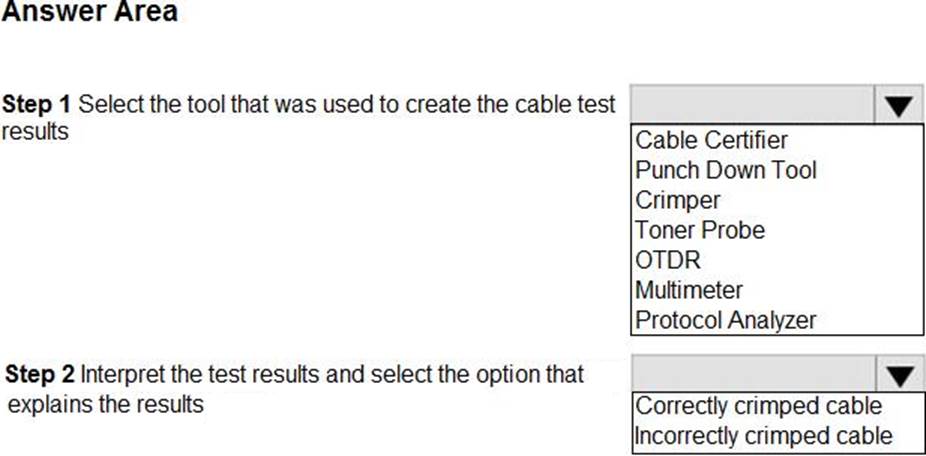
Explanation:
Step 1 – Cable certifier
Step 2 – correctly crimped cable
A network extension needs to be run to a location 500ft (152m) from the nearest switch.
Which of the following solutions would work BEST? (Select TWO).
- A . Cat 6 with a repeater placed in the middle of the run
- B . Cat 7
- C . Crossover cable
- D . Fiber-optic cabling
- E . Cat 7 with a patch panel placed in the middle of the run
A home user is unable to get to the Internet from a workstation that is connected to a wireless network. When reviewing the results of the ipconfig command, the user wants to verity the default gateway is correct .
Which of the following devices should be the gateway?
- A . Cable modem
- B . SOHO router
- C . DNS server
- D . Layer 2 switch
When using a network monitoring system, a network technician notices that a switch returns many object identifiers that do not have descriptions .
Which of the following should be imported into the monitoring system to describe these object identifiers?
- A . SNMPv3
- B . SIEM
- C . MIB
- D . SYSLOG
A department is reporting network Issues. Users can ping each other and the switch, but not the default gateway. When looking at a wiring diagram and a physical blueprint, a technician notices the 1000BaseLX SFP connects to a distribution switch via a cable that runs behind a large Industrial refrigerator. The technician also notices both switches have been worked on recently .
Which of the following Is MOST likely the issue?
- A . EMI
- B . TX/RX reverse
- C . Open/short
- D . Attenuation
A technician is preparing to dispose of old network devices .
Which of the following policies and best practices would outline procedures for removing sensitive information and configurations from surplus equipment?
- A . System life-cycle procedures
- B . Off-boarding procedures
- C . Safety procedures
- D . Appropriate use policy
A network technician receives a report that the company’s intranet web server is not responding. The technician verifies successful connectivity to the server via the ping and tracert commands. The technician also verifies the routers and switches are online and operational, and then runs Telnet to port 80 and receives a response .
Which of the following troubleshooting steps should the technician perform NEXT?
- A . Establish a plan to reset the company router.
- B . Escalate the issue to the server administrator.
- C . Duplicate the issue and continue testing.
- D . Report that an issue was not identified.
A network technician works in a large environment with several thousand users. Due to the needs of the organization, the network manager has asked the technician to design a solution that accommodates the data needs of all the users, while keeping all data on site .
Which of the following solutions should the technician Implement?
- A . SaaS
- B . SAN
- C . NAS
- D . laaS
A business with a point-to-point fiber-optic connection is suddenly unable to communicate between locations. A fiber cut is suspected .
Which of the following tools should the network technician use to determine the exact location of the cut?
- A . Reflectometer
- B . Cable tester
- C . Loopback tester
- D . Spectrum analyzers
A large company uses an AAA server to manage network device access. The engineers can use their domain credentials to access all other servers. Currently, the network engineers cannot access the AAA server using domain credentials, but they can access it using a local account .
Which of the following should the engineers update?
- A . Host-based firewall settings
- B . TACAS+ server time
- C . Server IP address
- D . DNS SRV record
A network technician is configuring network addresses and port numbers for a router ACL to block a peer-to-peer application .
Which of the following is the HIGHEST layer of the OSI model at which this router ACL operates?
- A . Transport
- B . Network
- C . Session
- D . Application
Which of the following should be performed on a regular basis to prevent unauthorized access to a company network? (Choose two.)
- A . Packet analysis
- B . Reviewing baselines
- C . Vulnerability scanning
- D . Patch management
- E . Log archiving
A company hires another firm to test the integrity of its information security controls.
This is an example of
- A . role separation.
- B . device hardening
- C . risk assessment
- D . penetration testing.
A technician wants to configure a SOHO network to use a specific public DNS server .
Which of the following network components should the technician configure to point all clients on a network to a new DNS server?
- A . Router
- B . Switch
- C . Load balancer
- D . Proxy server
The network support team is responsible for managing connections in a large, multipurpose venue where maintaining physical security is difficult.
Implementing which of the following standards would BEST help to prevent unauthorized connections to the wired network?
- A . 802.1X
- B . 802.1q
- C . 802.3at
- D . 802.3af
A bookstore uses a Faraday cage to comply with credit card regulations Customers report that their cellular phones have no signal when they are in the bookstore.
Which of the following is the MOST likely cause?
- A . The Faraday cage is creating interference within the bookstore
- B . The Faraday cage prevents access by redirecting signals
- C . The Faraday cage is creating latency on the cellular network
- D . The Faraday cage is creating attenuation of the cellular network
A network administrator wants to reduce the amount of time each user takes to log In to different systems in the network .
Which of the following would reduce the time spent authenticating?
- A . Kerberos
- B . RADIUS
- C . Certificate
- D . SSO
- E . MFA
- F . NAC
Two computers are connected to a multilayer switch, and both can access the corporate file server. The computers cannot talk to one another .
Which of the following is MOST likley the cause?
- A . Duplex/speed mismatch
- B . ACL misconfiguration
- C . Bad port
- D . Crosstalk
A network engineer is working on a network connectivity problem between a site in California and a site in New York. The connection went down overnight and the engineer is unsure where the connection failed. The technician is logged into the primary switch in the customer’s network, which is also the company’s connection to the WAN .
Which of the following toots should the technician use to determine the last available network hop?
- A . netstat
- B . Nmap
- C . traceroute
- D . pathping
A development team has been testing a web server on a virtual server to create a web application. Once satisfied, the development team clones the entire virtual server into production. The development team needs to use HTTP, HTTPS, and SSH to connect to the new server .
Which of the following should the network administrator do to help secure this new production VM? (Choose two.)
- A . Disable the HTTP port in the host firewall.
- B . Upgrade the firmware on the firewall.
- C . Generate new SSH host keys.
- D . Remove unnecessary testing accounts.
- E . Issue a new self-signed certificate.
An administrator is redesigning a company’s network and wants to reduce the amount of hardware needed Currently, all VLAN routing goes out a single switch interface to a router .
Which of the following would reduce the number of devices in this configuration?
- A . Bridge
- B . Multilayer switch
- C . Switch
- D . Next-generation firewall
A technician wants to have the ability to transfer files from home to the company’s network on a regular basis .
Which of the following is a remote access protocol the technician can utilize to bypass interactive user authentication by using a list of known host public keys?
- A . FTP
- B . SCP
- C . TFTP
- D . Telnet
A network technician is installing a new wireless network for a client. The client has experienced issues with other building tenants connecting to the wireless network and utilizing the bandwidth. The client wants to prevent this from happening by using certificate-based authentication .
Which of the following technologies should the network administrator implement?
- A . WPA-PSK
- B . EAP-TLS
- C . AES-CCMP
- D . WEP-TKIP
A network technician has been asked to create secure private networks between a company’s headquarters and several branch locations. The company has provided the on-premises equipment, but each branch has a different ISP .
Which of the following technologies should the technician consider using to accomplish this?
- A . Site-to-site
- B . Client-to-site
- C . Point-to-point
- D . Point-to-multipoint
Which of the following should be configured to allow for IP-to-name resolutions?
- A . CNAME
- B . A
- C . PTR
- D . NS
A new technician is connecting an access switch to a distribution switch uplink in a datacenter using fiber cables .
Which of the following are transceivers the technician should use to perform this job? (Select TWO).
- A . RJ45
- B . DB-9
- C . LC
- D . SFTP
- E . GBIC
- F . SC
A network manager is concerned about visitors taking advantage of open cubicles at a company’s facilities .
Which of the following would mitigate this issue?
- A . Create a VLAN for all unused switchports
- B . Implement a DM2 for all external services
- C . Implement root guard on all switches
- D . Create a honeypot to attract attackers
Management is concerned there is excessive traffic on the network. A network technician wants to run a quick port scan to see any systems that have open ports .
Which of the following tools should be used to do this?
- A . tcp dump
- B . dig
- C . nmap
- D . netstat
A network technician notices that switches of the same model have different commands and security features while administering them .
Which of the following hardening techniques should the technician perform on a regular schedule to ensure all switches have the same features and security functionality?
- A . Change the default credentials.
- B . Verify the firmware file hash.
- C . Disable unused switchports.
- D . Apply patches and updates.
Which of the following network topologies typically has all devices on a network directly connected to every other network device?
- A . Mesh
- B . Star
- C . Ad hoc
- D . Ring
A university has a lecture hall containing 100 students. Currently, the lecture hall has two 802.11ac wireless access points, which can accommodate up to 50 devices each. Several students report they are unable to connect devices to the wireless network .
Which of the following is MOST likely the issue?
- A . One of the wireless access points is on the wrong frequency
- B . The students are attempting to connect 802.11g devices
- C . The students are using more than one wireless device port seat.
- D . Distance limitations are preventing the students from connecting.
A company has procured a new office building and started the process of assigning employees to work at that location. The company has also purchased equipment for the new location. There are 5033 laptops, 6000 monitors, and 857 printers .
Which of the following steps is the technician most likely to complete FIRST?
- A . Create a rack diagram
- B . Create a network baseline
- C . Create an inventory database
- D . Create a port location diagram
A network technician arrives at a remote office and is unable to connect a laptop to corporate resources using the wireless network. After checking the IP address, the network technician notices the assigned IP address does not belong to the corporate network IP scheme .
Which of the following has the network technician discovered?
- A . Evil twin
- B . ARP poisoning
- C . DHCP exhaustion
- D . Social engineering
Which of the following is created on a 48-port switch with five active VLANs?
- A . 48 networks, five segments
- B . 48 collision domains, five broadcast domains
- C . 240 private networks
- D . 240 usable IP addresses
A network technician is reviewing switch ACLs to determine if they are causing communication issues with one PC. The PC’s IP address is 192.168.12.66 .
Which of the following is the network range found in the ACL that could have affected this PC?
- A . 192.168.12.97 255.255.255.192
- B . 192.168.12.97 255.255.255.224
- C . 192.168.12.97 255.255.255.240
- D . 192.168.12.97 255.255.255.248
Which of the following is the MOST secure type of remote administration?
- A . SSH over iPSec client-to-site VPN
- B . RDP over SSLv2 HTTPS terminal services gateway
- C . HTTP over WPA2-TKIP WiFi
- D . Telnet over PSTN
A WAP has been dropping off the network sporadically and reconnecting shortly thereafter.
The Cat5 wire connecting the access point is a long run of 265ft (81m) and goes through the business area and the mechanical room .
Which of the following should the technician do to fix the AP connectivity issue?
- A . Install a repeater to boost the signal to its destination
- B . Replace the UTP cable with plenum cable.
- C . Upgrade the cable from Cat 5 to Cat 5e.
- D . Set the AP to half duplex to compensate for signal loss.
Which of the following can a network administrator use to access a network switch using standard AAA configurations?
- A . TACACS+
- B . Single sign-on
- C . LDAP
- D . Local authentication
A network administrator is installing a campus network of two routers, 24 switches, 76 APs, and 492 VoIP phone sets .
Which of the following additional devices should the administrator install to help manage this network?
- A . VoIP PBX
- B . Content filter
- C . RADIUS server
- D . Wireless controller
A company runs Linux servers in its own datacenter and also on a popular public cloud service provider. The servers hosted by the cloud provider can only be accessed with proper authorization and are only accessed by the company’s datacenter .
Which of the following BEST describes the type of cloud architecture being used? (Choose two.)
- A . Private
- B . Hybrid
- C . Public
- D . IaaS
- E . PaaS
- F . SaaS
A utility company has installed a wireless device at a residence that allows the company to view power consumption online. The resident reports the 802.11ac home wireless intermittently loses connectivity for about 15 minutes twice a day.
Which of the following is the MOST likely cause?
- A . The utility company throttles power during peak hours.
- B . There is additional data being transferred over the wireless network.
- C . There is interference with the smart reader.
- D . An IoT device is causing a DoS attack on the wireless network.
A technician is sent to troubleshoot a faulty network connection. The technician tests the cable, and data passes through successfully. No changes were made in the environment, however, when a network device is connected to the switch using the cable, the switchport will not light up .
Which of the following should the technician attempt NEXT?
- A . Modify the speed and duplex
- B . Plug in to another port
- C . Replace the NIC
- D . Change the switch
Which of the following technologies is used to attach multiple guest operating systems to a single physical network port?
- A . Virtual switch
- B . FCoE
- C . VPC
- D . vSAN
- E . Fibre Channel
A technician has received a report that details the need for a patch and a complete list of the affected systems .
Which of the following activities MOST likely generated the report?
- A . Port enumeration
- B . Baseline review
- C . Vulnerability scanning
- D . Packet analysis
After several changes to the network, a technician needs to ensure a client is checking for
new hostname and IP pairings .
Which of the following commands should the technician use to force new lookups?
- A . ipconfig /flushdns
- B . ipconfig /release
- C . ipconfig /renew
- D . ipconfig /all
A zero-day vulnerability is discovered that affects a specific network device. This vulnerability only affects services on port 21. This network device is restricted to use only secure protocols and services .
Which of the following explains why this device is secure?
- A . Because secure protocols would reject malicious packets
- B . Because SCP is not a secure service
- C . Because FTP is not a secure service
- D . Because a secure firewall will protect the device
Which of the following OSI layers do TCP and UDP operate within?
- A . Data link
- B . Network
- C . Session
- D . Transport
- E . Presentation
- F . Application
A network technician needs to monitor the traffic going to a mission-critical server in the datacenter .
Which of the following is the BEST method to perform this?
- A . Use port mirroring
- B . Install an inline tap
- C . Periodically view the server logs
- D . Configure port aggregation
Which of the following policies would be the MOST useful for defining the proper procedures when an employee is terminated abruptly?
- A . Offboarding
- B . Remote access
- C . AUP
- D . Incident response
- E . DLP
A technician is moving a company to a cloud email service. Several external recipients are reporting that email sent from the company is going to their junk folders because the sender’s identity cannot be verified .
Which of the following DNS record types should the technician modify to minimize this problem?
- A . CNAME
- B . PTR
- C . TXT
- D . SRV
Users report that the network is slow. Upon investigation, the technician notices all users are on one large subnet .
Which of the following devices should be used to break up broadcast domains?
- A . Layer 2 switch
- B . Layer 3 switch
- C . Signal repeater
- D . Bridge
- E . Domain server
A network engineer created a guest wireless network named "Visitor" for clients to use when they are on site. After a couple of months, visiting clients state they cannot access the Internet after connecting to the "Visitor" wireless network, even though configuration changes have not been made .
Which of the following is the MOST likely cause of this issue?
- A . The access point’s antenna is not powerful enough to allow all the visitors to establish a connection.
- B . The SSID suggests there is a rogue access point masquerading as the guest network.
- C . The visiting clients are trying to connect to the corporate network without the proper credentials.
- D . The network Is overlapping with the internal corporate wireless network and causing signal loss.
A network technician is troubleshooting a problem with a user’s client-to-site VPN connection. The user is unable to establish a connection to the server, but the error message that appears on screen does not contain useful information .
Which of the following should the technician do NEXT to troubleshoot the issue?
- A . Reconfigure the user’s VPN connection in the router to fix profile corruption.
- B . Inform the user that provisioning sometimes fails and the connection needs to be attempted again.
- C . Review the logs in the VPN client to check for any informational messages.
- D . Verify the system has the latest OS patches installed.
When deploying UTP cables In a networking environment, which of the following are acceptable standards? (Select TWO).
- A . 10Base2
- B . 10Base5
- C . 10GBaseT
- D . 1000BaseLX
- E . 1000BaseSX
- F . 1000BaseT
A network technician is assisting a user who is experiencing connectivity problems with the VPN. The technician has confirmed the VPN is functioning and other users at the site cannot access the Internet .
Which of the following commands would MOST likely be used to further troubleshoot?
- A . tracert
- B . netstat
- C . arp
- D . dig
Management requires remote access to network devices when the ISP is down .
Which of the following devices would provide the BEST solution?
- A . Router
- B . Firewall
- C . Bridge
- D . Modem
Which of the following technologies should be used in high-throughput networks to reduce network overhead?
- A . iscsi
- B . QoStags
- C . Port aggregation
- D . Jumbo frames
During a weekend event, several people reported they were unable to get onto the wireless network. On Monday, the technician could not find a problem .
Which of the following is the MOST likely cause?
- A . Cross talk
- B . Overcapacity
- C . Channel overlap
- D . Wrong passphrase
Log files show the admin user has logged into a public-facing device on several occasions in the evening. None of the technicians admit to doing any after-hours work, and the password has been changed several times but failed to prevent the logins .
Which of the following should be the NEXT step to attempt to harden the device?
- A . Disable unused ports.
- B . Reset the two-factor token.
- C . Disable virtual ports.
- D . Upgrade the firmware.
An employee reports an error when visiting a website using SSL, and a message is displayed warning of an invalid certificate .
Which of the following could be occurring?
- A . Phishing
- B . DDoS
- C . Evil twin
- D . MITM
- E . OCSP stapling
Which of the following devices would allow a network administrator to block an application at Layer7 on the network?
- A . Firewall
- B . NGFW
- C . Router
- D . Spam filter
Which of the following storage network technologies has the HIGHEST throughput?
- A . FCoE
- B . InfiniBand
- C . iSCSI
- D . OC3
A network engineer for a manufacturing company is implementing a wireless network that provides reliable coverage throughout the facility. There are several large, electric, motorized machines installed on the shop floor for automating the manufacturing process. These machines are known to be significant sources of RF interference .
Which of the following frequencies should the wireless network use to MINIMIZE this interference?
- A . 2.4 GHz
- B . 56MHz
- C . 5GHz
- D . 900MHz
Which of the following default ports should be opened on a firewall to allow for SSH and Telnet? (Select TWO)
- A . 21
- B . 22
- C . 23
- D . 25
- E . 123
- F . 443
A network administrator reviews the following command output while troubleshooting a system that is unable to connect to the www.comptia.com website:
Which of the following is the reason the system cannot connect?
- A . The DNS server is under maintenance.
- B . A cable is not connected to the NIC.
- C . The domain complia.com is having network issues.
- D . The interface eth0 Is using an APIPA address.
The engineering department wants to bring a legacy computer online to test a failed component. When patching the device into the switch, there are no link lights or connectivity. The legacy computer can ping its loopback address successfully. Another device can connect to that same port without issues .
Which of the following should the network technician check NEXT? (Choose two.)
- A . Speed setting on the switch
- B . Duplex requirements
- C . Firmware version
- D . Protocols the legacy computer supports
- E . Network card drivers
- F . VLAN settings
Which of the following can be used to prevent unauthorized employees from entering restricted areas?
- A . Sign-in sheets
- B . Video cameras
- C . Motion sensors
- D . Swipe badges
A wireless access point that was working in a large warehouse last week is now offline. The technician observes there is no power to the device. The technician verifies PoE is working on the switchport, and then confirms the wireless access point is still not powering up .
Which of the following is the MOST likely issue?
- A . Attenuation
- B . Incorrect pin-out
- C . Damaged cable
- D . Switch configuration
Which of the following would a network technician MOST likely connect to power wireless access points in drop ceilings?
- A . Powerline extender
- B . Ethernet-over-power adapter
- C . Power-over-Ethernet switch
- D . Power distribution unit
- E . Ethernet power controller
A human resources manager notifies the IT manager the night before an employee will be terminated so the employee’s access rights can be removed .
Which of the following policies is being exercised?
- A . Privileged user agreement
- B . AUP
- C . Non-disclosure agreement
- D . Offboarding
A technician is troubleshooting a server In the finance office that hosts an internal accounting program. The ticketing desk has received several calls from users reporting that access to the accounting program is degraded, and they are experiencing severe delays, sometimes timing out entirely. The problem has been isolated to the server .
Which of the following tools should the technician use on the server to narrow down the issue?
- A . nslookup
- B . iptables
- C . pathping
- D . netstat