A security analyst is reviewing the network security monitoring logs listed below:
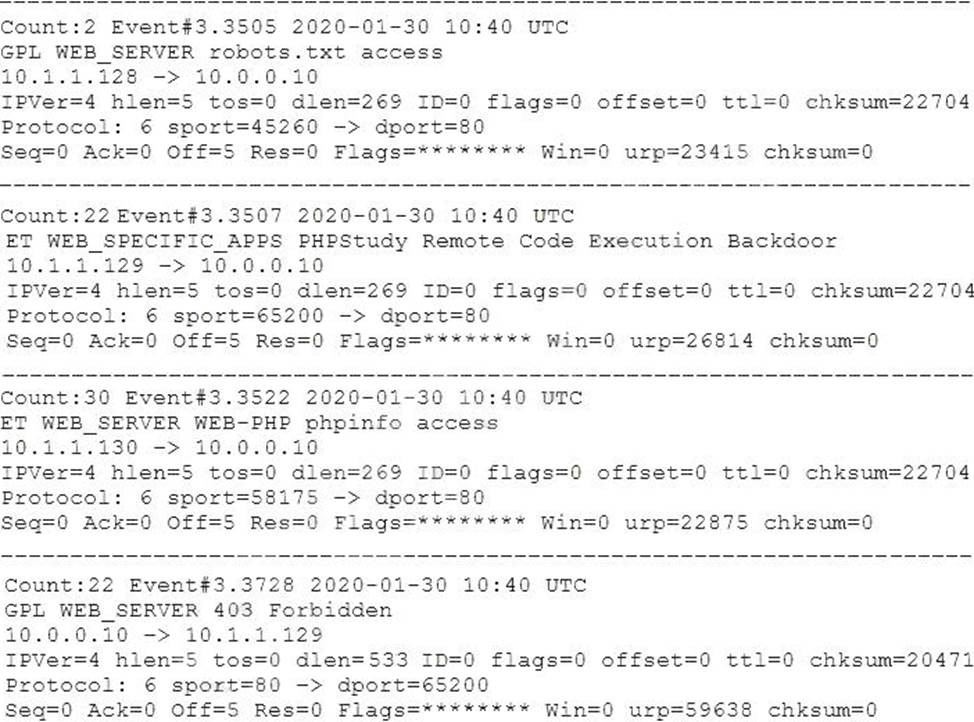
Which of the following is the analyst MOST likely observing? (Select TWO).
- A . 10.1.1.128 sent malicious requests, and the alert is a false positive.
- B . 10.1.1.129 sent potential malicious requests to the web server.
- C . 10.1.1.129 sent non-malicious requests, and the alert is a false positive.
- D . 10.1.1.128 sent potential malicious traffic to the web server.
- E . 10.1.1 .129 successfully exploited a vulnerability on the web server.
In web application scanning, static analysis refers to scanning:
- A . the system for vulnerabilities before installing the application.
- B . the compiled code of the application to detect possible issues.
- C . an application that is installed and active on a system.
- D . an application that is installed on a system that is assigned a static IP.
A security analyst discovered a specific series of IP addresses that are targeting an organization. None of the attacks have been successful.
Which of the following should the security analyst perform NEXT?
- A . Begin blocking all IP addresses within that subnet.
- B . Determine the attack vector and total attack surface.
- C . Begin a kill chain analysis to determine the impact.
- D . Conduct threat research on the IP addresses
Which of the following technologies can be used to store digital certificates and is typically used in high security implementations where integrity is paramount?
- A . HSM
- B . eFuse
- C . UEFI
- D . Self-encrypting drive
CORRECT TEXT
SIMULATION
Malware is suspected on a server in the environment.
The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one of the servers may be malware.
INSTRUCTIONS
Servers 1, 2, and 4 are clickable. Select the Server and the process that host the malware.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
An organization developed a comprehensive modern response policy Executive management approved the policy and its associated procedures.
Which of the following activities would be MOST beneficial to evaluate personnel’s familiarity with incident response procedures?
- A . A simulated breach scenario evolving the incident response team
- B . Completion of annual information security awareness training by ail employees
- C . Tabtetop activities involving business continuity team members
- D . Completion of lessons-learned documentation by the computer security incident response team
- E . External and internal penetration testing by a third party
A team of security analysts has been alerted to potential malware activity. The initial examination indicates one of the affected workstations is beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445.
Which of the following should be the team’s NEXT step during the detection phase of this response process?
- A . Escalate the incident to management, who will then engage the network infrastructure team to keep them informed.
- B . Depending on system criticality, remove each affected device from the network by disabling wired and wireless connections.
- C . Engage the engineering team to block SMB traffic internally and outbound HTTP traffic to the five IP addresses.
- D . Identify potentially affected systems by creating a correlation search in the SIEM based on the network traffic.
The SFTP server logs show thousands of failed login attempts from hundreds of IP addresses worldwide.
Which of the following controls would BEST protect the service?
- A . Whitelisting authorized IP addresses
- B . Enforcing more complex password requirements
- C . Blacklisting unauthorized IP addresses
- D . Establishing a sinkhole service
A cybersecurity analyst is reading a daily intelligence digest of new vulnerabilities. The type of vulnerability that should be disseminated FIRST is one that:
- A . enables remote code execution that is being exploited in the wild.
- B . enables data leakage but is not known to be in the environment
- C . enables lateral movement and was reported as a proof of concept
- D . affected the organization in the past but was probably contained and eradicated
Which of the following BEST describes the process by which code is developed, tested, and deployed in small batches?
- A . Agile
- B . Waterfall
- C . SDLC
- D . Dynamic code analysis
A
Explanation:
Reference: https://www.cleverism.com/software-development-life-cycle-sdlc-methodologies/
An analyst performs a routine scan of a host using Nmap and receives the following output:
Which of the following should the analyst investigate FIRST?
- A . Port 21
- B . Port 22
- C . Port 23
- D . Port 80
A large amount of confidential data was leaked during a recent security breach. As part of a forensic investigation, the security team needs to identify the various types of traffic that were captured between two compromised devices.
Which of the following should be used to identify the traffic?
- A . Carving
- B . Disk imaging
- C . Packet analysis
- D . Memory dump
- E . Hashing
During an investigation, a security analyst determines suspicious activity occurred during the night shift over the weekend. Further investigation reveals the activity was initiated from an internal IP going to an external website.
Which of the following would be the MOST appropriate recommendation to prevent the activity from happening in the future?
- A . An IPS signature modification for the specific IP addresses
- B . An IDS signature modification for the specific IP addresses
- C . A firewall rule that will block port 80 traffic
- D . A firewall rule that will block traffic from the specific IP addresses
An organization’s Chief Information Security Officer (CISO) has asked department leaders to coordinate on communication plans that can be enacted in response to different cybersecurity incident triggers.
Which of the following is a benefit of having these communication plans?
- A . They can help to prevent the inadvertent release of damaging information outside the organization.
- B . They can quickly inform the public relations team to begin coordinating with the media as soon as a breach is detected.
- C . They can help to keep the organization’s senior leadership informed about the status of patching during the recovery phase.
- D . They can help to limit the spread of worms by coordinating with help desk personnel earlier in the recovery phase.
CORRECT TEXT
While investigating an incident in a company’s SIEM console, a security analyst found hundreds of failed SSH login attempts, which all occurred in rapid succession. The failed attempts were followed by a successful login on the root user Company policy allows systems administrators to manage their systems only from the company’s internal network using their assigned corporate logins.
Which of the following are the BEST actions the analyst can take to stop any further compromise? (Select TWO).
A Configure /etc/sshd_config to deny root logins and restart the SSHD service.
B. Add a rule on the network IPS to block SSH user sessions
C. Configure /etc/passwd to deny root logins and restart the SSHD service.
D. Reset the passwords for all accounts on the affected system.
E. Add a rule on the perimeter firewall to block the source IP address.
F. Add a rule on the affected system to block access to port TCP/22.
The computer incident response team at a multinational company has determined that a breach of sensitive data has occurred in which a threat actor has compromised the organization’s email system. Per the incident response procedures, this breach requires notifying the board immediately.
Which of the following would be the BEST method of communication?
- A . Post of the company blog
- B . Corporate-hosted encrypted email
- C . VoIP phone call
- D . Summary sent by certified mail
- E . Externally hosted instant message
A security analyst is attempting to utilize the blowing threat intelligence for developing detection capabilities:
In which of the following phases is this APT MOST likely to leave discoverable artifacts?
- A . Data collection/exfiltration
- B . Defensive evasion
- C . Lateral movement
- D . Reconnaissance
Which of the following software security best practices would prevent an attacker from being able to run arbitrary SQL commands within a web application? (Choose two.)
- A . Parameterized queries
- B . Session management
- C . Input validation
- D . Output encoding
- E . Data protection
- F . Authentication
A,C
Explanation:
Reference: https://www.ptsecurity.com/ww-en/analytics/knowledge-base/how-to-prevent-sql-injection-attacks/
A web-based front end for a business intelligence application uses pass-through authentication to authenticate users. The application then uses a service account, to perform queries and look up data m a database A security analyst discovers employees are accessing data sets they have not been authorized to use.
Which of the following will fix the cause of the issue?
- A . Change the security model to force the users to access the database as themselves
- B . Parameterize queries to prevent unauthorized SQL queries against the database
- C . Configure database security logging using syslog or a SIEM
- D . Enforce unique session IDs so users do not get a reused session ID
A security analyst needs to develop a brief that will include the latest incidents and the attack phases of the incidents. The goal is to support threat intelligence and identify whether or not the incidents are linked.
Which of the following methods would be MOST appropriate to use?
- A . An adversary capability model
- B . The MITRE ATT&CK framework
- C . The Cyber Kill Chain
- D . The Diamond Model of Intrusion Analysis
A security analyst discovers accounts in sensitive SaaS-based systems are not being removed in a timely manner when an employee leaves the organization.
To BEST resolve the issue, the organization should implement
- A . federated authentication
- B . role-based access control.
- C . manual account reviews
- D . multifactor authentication.
A threat feed notes malicious actors have been infiltrating companies and exfiltration data to a specific set of domains Management at an organization wants to know if it is a victim.
Which of the following should the security analyst recommend to identity this behavior without alerting any potential malicious actors?
- A . Create an IPS rule to block these domains and trigger an alert within the SIEM tool when these domains are requested
- B . Add the domains to a DNS sinkhole and create an alert m the SIEM toot when the domains are queried
- C . Look up the IP addresses for these domains and search firewall logs for any traffic being sent to those IPs over port 443
- D . Query DNS logs with a SIEM tool for any hosts requesting the malicious domains and create alerts based on this information
A security analyst was alerted to a tile integrity monitoring event based on a change to the vhost-paymonts .conf file.
The output of the diff command against the known-good backup reads as follows:
Which of the following MOST likely occurred?
- A . The file was altered to accept payments without charging the cards
- B . The file was altered to avoid logging credit card information
- C . The file was altered to verify the card numbers are valid.
- D . The file was altered to harvest credit card numbers
Which of the following are components of the intelligence cycle? (Select TWO.)
- A . Collection
- B . Normalization
- C . Response
- D . Analysis
- E . Correction
- F . Dissension
A security technician is testing a solution that will prevent outside entities from spoofing the company’s email domain, which is comptiA.org. The testing is successful, and the security technician is prepared to fully implement the solution.
Which of the following actions should the technician take to accomplish this task?
- A . Add TXT @ "v=spf1 mx include:_spf.comptiA.org all" to the DNS record.
- B . Add TXT @ "v=spf1 mx include:_spf.comptiA.org all" to the email server.
- C . Add TXT @ "v=spf1 mx include:_spf.comptiA.org +all" to the domain controller.
- D . Add TXT @ "v=spf1 mx include:_spf.comptiA.org +all" to the web server.
A
Explanation:
Reference: https://blog.finjan.com/email-spoofing/
A development team is testing a new application release. The team needs to import existing client PHI data records from the production environment to the test environment to test accuracy and functionality.
Which of the following would BEST protect the sensitivity of this data while still allowing the team to perform the testing?
- A . Deidentification
- B . Encoding
- C . Encryption
- D . Watermarking
An organization is upgrading its network and all of its workstations. The project will occur in phases, with infrastructure upgrades each month and workstation installs every other week. The schedule should accommodate the enterprise-wide changes, while minimizing the impact to the network.
Which of the following schedules BEST addresses these requirements?
- A . Monthly topology scans, biweekly host discovery scans, weekly vulnerability scans
- B . Monthly vulnerability scans, biweekly topology scans, daily host discovery scans
- C . Monthly host discovery scans; biweekly vulnerability scans, monthly topology scans
- D . Monthly topology scans, biweekly host discovery scans, monthly vulnerability scans
A Chief Executive Officer (CEO) is concerned about the company’s intellectual property being leaked to competitors. The security team performed an extensive review but did not find any indication of an outside breach. The data sets are currently encrypted using the Triple Data Encryption Algorithm.
Which of the following courses of action is appropriate?
- A . Limit all access to the sensitive data based on geographic access requirements with strict role-based access controls.
- B . Enable data masking and reencrypt the data sets using AES-256.
- C . Ensure the data is correctly classified and labeled, and that DLP rules are appropriate to prevent disclosure.
- D . Use data tokenization on sensitive fields, reencrypt the data sets using AES-256, and then create an MD5 hash.
A security analyst is investigating a malware infection that occurred on a Windows system. The system was not connected to a network and had no wireless capability Company policy prohibits using portable media or mobile storage. The security analyst is trying to determine which user caused the malware to get onto the system.
Which of the following registry keys would MOST likely have this information?
- A . HKEY_USERS<user SID>SoftwareMicrosoftWindowsCurrentVersionRun
- B . HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun
- C . HKEY_USERS<user SID>SoftwareMicrosoftWindowsexplorerMountPoints2
- D . HKEY_USERS<user SID>SoftwareMicrosoftInternet ExplorerTyped URLs
- E . HKEY_LOCAL_MACHINESYSTEMControlSet001serviceseventlogSystemiusb3hub
Which of the following should a database administrator implement to BEST protect data from an untrusted server administrator?
- A . Data encryption
- B . Data deidentification
- C . Data masking
- D . Data minimization
While analyzing network traffic, a security analyst discovers several computers on the network are connecting to a malicious domain that was blocked by a DNS sinkhole. A new private IP range is now visible, but no change requests were made to add it.
Which of the following is the BEST solution for the security analyst to implement?
- A . Block the domain IP at the firewall.
- B . Blacklist the new subnet
- C . Create an IPS rule.
- D . Apply network access control.
A security analyst has a sample of malicious software and needs to know what the sample does. The analyst runs the sample in a carefully controlled and monitored virtual machine to observe the software behavior.
Which of the following malware analysis approaches is this?
- A . White box testing
- B . Fuzzing
- C . Sandboxing
- D . Static code analysis
A security analyst is generating a list of recommendations for the company’s insecure API.
Which of the following is the BEST parameter mitigation rec?
- A . Implement parameterized queries.
- B . Use effective authentication and authorization methods.
- C . Validate all incoming data.
- D . Use TLs for all data exchanges.
The steering committee for information security management annually reviews the security incident register for the organization to look for trends and systematic issues. The steering committee wants to rank the risks based on past incidents to improve the security program for next year Below is the incident register for the organization.
Which of the following should the organization consider investing in FIRST due to the potential impact of availability?
- A . Hire a managed service provider to help with vulnerability management
- B . Build a warm site in case of system outages
- C . Invest in a failover and redundant system, as necessary
- D . Hire additional staff for the IT department to assist with vulnerability management and log review
C
Explanation:
Both on July 31 and November 24, the organization could not restore multiple days due to missing disaster recovery plan. Therefore, failover systems are very important for this organization.
Which of the following technologies can be used to house the entropy keys for disk encryption on desktops and laptops?
- A . Self-encrypting drive
- B . Bus encryption
- C . TPM
- D . HSM
During an incident investigation, a security analyst acquired a malicious file that was used as a backdoor but was not detected by the antivirus application. After performing a reverse-engineering procedure, the analyst found that part of the code was obfuscated to avoid signature detection.
Which of the following types of instructions should the analyst use to understand how the malware was obfuscated and to help deobfuscate it?
- A . MOV
- B . ADD
- C . XOR
- D . SUB
- E . MOVL
A user’s computer has been running slowly when the user tries to access web pages.
A security analyst runs the command netstat -aon from the command line and receives the following output:
Which of the following lines indicates the computer may be compromised?
- A . Line 1
- B . Line 2
- C . Line 3
- D . Line 4
- E . Line 5
- F . Line 6
An information security analyst is reviewing backup data sets as part of a project focused on eliminating archival data sets.
Which of the following should be considered FIRST prior to disposing of the electronic data?
- A . Sanitization policy
- B . Data sovereignty
- C . Encryption policy
- D . Retention standards
A security analyst is investigating a system compromise. The analyst verities the system was up to date on OS patches at the time of the compromise.
Which of the following describes the type of vulnerability that was MOST likely expiated?
- A . Insider threat
- B . Buffer overflow
- C . Advanced persistent threat
- D . Zero day
Which of the following would MOST likely be included in the incident response procedure after a security breach of customer PII?
- A . Human resources
- B . Public relations
- C . Marketing
- D . Internal network operations center
An analyst is reviewing the following code output of a vulnerability scan:
Which of the following types of vulnerabilities does this MOST likely represent?
- A . A insecure direct object reference vulnerability
- B . An HTTP response split vulnerability
- C . A credential bypass vulnerability
- D . A XSS vulnerability
A user receives a potentially malicious email that contains spelling errors and a PDF document. A security analyst reviews the email and decides to download the attachment to a Linux sandbox for review.
Which of the following commands would MOST likely indicate if the email is malicious?
- A . sha256sum ~/Desktop/file.pdf
- B . file ~/Desktop/file.pdf
- C . strings ~/Desktop/file.pdf | grep "<script"
- D . cat < ~/Desktop/file.pdf | grep -i .exe
A security analyst is reviewing the following web server log:
Which of the following BEST describes the issue?
- A . Directory traversal exploit
- B . Cross-site scripting
- C . SQL injection
- D . Cross-site request forgery
A remote code execution vulnerability was discovered in the RDP. An organization currently uses RDP for remote access to a portion of its VDI environment. The analyst verified network-level authentication is enabled.
Which of the following is the BEST remediation for this vulnerability?
- A . Verify the latest endpoint-protection signature is in place.
- B . Verify the corresponding patch for the vulnerability is installed^
- C . Verify the system logs do not contain indicator of compromise.
- D . Verify the threat intelligence feed is updated with the latest solutions
A company recently experienced financial fraud, which included shared passwords being compromised and improper levels of access being granted. The company has asked a security analyst to help improve its controls.
Which of the following will MOST likely help the security analyst develop better controls?
- A . An evidence summarization
- B . An indicator of compromise
- C . An incident response plan
- D . A lessons-learned report
Understanding attack vectors and integrating intelligence sources are important components of:
- A . proactive threat hunting
- B . risk management compliance.
- C . a vulnerability management plan.
- D . an incident response plan.
An information security analyst is working with a data owner to identify the appropriate controls to preserve the confidentiality of data within an enterprise environment One of the primary concerns is exfiltration of data by malicious insiders.
Which of the following controls is the MOST appropriate to mitigate risks?
- A . Data deduplication
- B . OS fingerprinting
- C . Digital watermarking
- D . Data loss prevention
Joe, a penetration tester, used a professional directory to identify a network administrator and ID administrator for a client’s company. Joe then emailed the network administrator, identifying himself as the ID administrator, and asked for a current password as part of a security exercise.
Which of the following techniques were used in this scenario?
- A . Enumeration and OS fingerprinting
- B . Email harvesting and host scanning
- C . Social media profiling and phishing
- D . Network and host scanning
An analyst wants to identify hosts that are connecting to the external FTP servers and what, if any, passwords are being used.
Which of the following commands should the analyst use?
- A . tcpdump CX dst port 21
- B . ftp ftp.server Cp 21
- C . nmap Co ftp.server Cp 21
- D . telnet ftp.server 21
A security analyst needs to assess the web server versions on a list of hosts to determine which are running a vulnerable version of the software and output that list into an XML file named webserverlist.xml. The host list is provided in a file named webserverlist.txt.
Which of the following Nmap commands would BEST accomplish this goal?
- A . nmap -iL webserverlist.txt -sC -p 443 -oX webserverlist.xml
- B . nmap -iL webserverlist.txt -sV -p 443 -oX webserverlist.xml
- C . nmap -iL webserverlist.txt -F -p 443 -oX webserverlist.xml
- D . nmap –takefile webserverlist.txt –outputfileasXML webserverlist.xml Cscanports 443
A small electronics company decides to use a contractor to assist with the development of a new FPGA-based device. Several of the development phases will occur off-site at the contractor’s labs.
Which of the following is the main concern a security analyst should have with this arrangement?
- A . Making multiple trips between development sites increases the chance of physical damage to the FPGAs.
- B . Moving the FPGAs between development sites will lessen the time that is available for security testing.
- C . Development phases occurring at multiple sites may produce change management issues.
- D . FPGA applications are easily cloned, increasing the possibility of intellectual property theft.
D
Explanation:
Reference: https://www.eetimes.com/how-to-protect-intellectual-property-in-fpgas-devices-part-1/#
An organization wants to move non-essential services into a cloud computing environment. Management has a cost focus and would like to achieve a recovery time objective of 12 hours.
Which of the following cloud recovery strategies would work BEST to attain the desired outcome?
- A . Duplicate all services in another instance and load balance between the instances.
- B . Establish a hot site with active replication to another region within the same cloud provider.
- C . Set up a warm disaster recovery site with the same cloud provider in a different region
- D . Configure the systems with a cold site at another cloud provider that can be used for failover.
During an investigation, an analyst discovers the following rule in an executive’s email client:
IF * TO <executive@anycompany.com> THEN mailto: <someaddress@domain.com>
SELECT FROM ‘sent’ THEN DELETE FROM <executive@anycompany.com>
The executive is not aware of this rule.
Which of the following should the analyst do FIRST to evaluate the potential impact of this security incident?
- A . Check the server logs to evaluate which emails were sent to <someaddress@domain.com>
- B . Use the SIEM to correlate logging events from the email server and the domain server
- C . Remove the rule from the email client and change the password
- D . Recommend that management implement SPF and DKIM
A security analyst is supporting an embedded software team.
Which of the following is the BEST recommendation to ensure proper error handling at runtime?
- A . Perform static code analysis.
- B . Require application fuzzing.
- C . Enforce input validation
- D . Perform a code review
Because some clients have reported unauthorized activity on their accounts, a security analyst is reviewing network packet captures from the company’s API server.
A portion of a capture file is shown below:
POST /services/v1_0/Public/Members.svc/soap <s:Envelope+xmlns:s="http://schemas.s/soap/envelope/"><s:Body><GetIPLocation+xmlns="http://tempuri.org/">
<request+xmlns:a="http://schemas.somesite.org"+xmlns:i="http://www.w3.org/2001/XMLSchema-instance"></s:Body></s:Envelope> 192.168.1.22 –api.somesite.com 200 0 1006 1001 0 192.168.1.22
POST /services/v1_0/Public/Members.svc/soap <<a:Password>Password123</a:Password><a:ResetPasswordToken+i:nil="true"/> <a:ShouldImpersonatedAuthenticationBePopulated+i:nil="true"/><a:Username>somebody@companyname.com</a:Username></request></Login></s:Body></s:Envelope> 192.168.5.66 –api.somesite.com 200 0 11558 1712 2024 192.168.4.89
POST /services/v1_0/Public/Members.svc/soap <s:Envelope+xmlns:s="http://schemas.xmlsoap.org/soap/envelope/"><s:Body><GetIPLocation+xmlns="http://tempuri.org/"> <a:IPAddress>516.7.446.605</a:IPAddress><a:ZipCode+i:nil="true"/></request></GetIPLocation></s:Body></s:Envelope> 192.168.1.22 –api.somesite.com 200 0 1003 1011 307 192.168.1.22
POST /services/v1_0/Public/Members.svc/soap <s:Envelope+xmlns:s="http://schemas.xmlsoap.org/soap/envelope/"><s:Body><IsLoggedIn+xmlns="http://tempuri.org/"> <request+xmlns:a="http://schemas.datacontract.org/2004/07/somesite.web+xmlns:i="http://www.w3.org/2001/XMLSchema-instance"><a:Authentication> <a:ApiToken>kmL4krg2CwwWBan5BReGv5Djb7syxXTNKcWFuSjd</a:ApiToken><a:ImpersonateUserId>0</a:ImpersonateUserId><a:LocationId>161222</a:LocationId> <a:NetworkId>4</a:NetworkId><a:ProviderId>”1=1</a:ProviderId><a:UserId>13026046</a:UserId></a:Authentication></request></IsLoggedIn></s:Body></s:Envelope> 192.168.5.66 –api.somesite.com 200 0 1378 1209 48 192.168.4.89
Which of the following MOST likely explains how the clients’ accounts were compromised?
- A . The clients’ authentication tokens were impersonated and replayed.
- B . The clients’ usernames and passwords were transmitted in cleartext.
- C . An XSS scripting attack was carried out on the server.
- D . A SQL injection attack was carried out on the server.
A security analyst is auditing firewall rules with the goal of scanning some known ports to check the firewall’s behavior and responses.
The analyst executes the following commands:
The analyst then compares the following results for port 22:
nmap returns “Closed”
hping3 returns “flags=RA”
Which of the following BEST describes the firewall rule?
- A . DNAT C-to-destination 1.1.1.1:3000
- B . REJECT with C-tcp-reset
- C . LOG C-log-tcp-sequence
- D . DROP
A security analyst recently used Arachni to perform a vulnerability assessment of a newly developed web application.
The analyst is concerned about the following output:
Which of the following is the MOST likely reason for this vulnerability?
- A . The developer set input validation protection on the specific field of search.aspx.
- B . The developer did not set proper cross-site scripting protections in the header.
- C . The developer did not implement default protections in the web application build.
- D . The developer did not set proper cross-site request forgery protections.
A cybersecurity analyst needs to rearchitect the network using a firewall and a VPN server to achieve the highest level of security.
To BEST complete this task, the analyst should place the:
- A . firewall behind the VPN server
- B . VPN server parallel to the firewall
- C . VPN server behind the firewall
- D . VPN on the firewall
Which of the following technologies can be used to house the entropy keys for task encryption on desktops and laptops?
- A . Self-encrypting drive
- B . Bus encryption
- C . TPM
- D . HSM
When attempting to do a stealth scan against a system that does not respond to ping, which of the following Nmap commands BEST accomplishes that goal?
- A . nmap CsA CO <system> -noping
- B . nmap CsT CO <system> -P0
- C . nmap CsS CO <system> -P0
- D . nmap CsQ CO <system> -P0
The Chief Information Officer (CIO) of a large healthcare institution is concerned about all machines having direct access to sensitive patient information.
Which of the following should the security analyst implement to BEST mitigate the risk of sensitive data exposure?
- A . A cloud access service broker system
- B . NAC to ensure minimum standards are met
- C . MFA on all workstations
- D . Network segmentation
Ransomware is identified on a company’s network that affects both Windows and MAC hosts. The command and control channel for encryption for this variant uses TCP ports from 11000 to 65000. The channel goes to good1. Iholdbadkeys.com, which resolves to IP address 72.172.16.2.
Which of the following is the MOST effective way to prevent any newly infected systems from actually encrypting the data on connected network drives while causing the least disruption to normal Internet traffic?
- A . Block all outbound traffic to web host good1 iholdbadkeys.com at the border gateway.
- B . Block all outbound TCP connections to IP host address 172.172.16.2 at the border gateway.
- C . Block all outbound traffic on TCP ports 11000 to 65000 at the border gateway.
- D . Block all outbound traffic on TCP ports 11000 to 65000 to IP host address 172.172.16.2 at the border gateway.
During a routine log review, a security analyst has found the following commands that cannot be identified from the Bash history log on the root user.
Which of the following commands should the analyst investigate FIRST?
- A . Line 1
- B . Line 2
- C . Line 3
- D . Line 4
- E . Line 5
- F . Line 6
A company’s senior human resources administrator left for another position, and the assistant administrator was promoted into the senior position. On the official start day, the new senior administrator planned to ask for extended access permissions but noticed the permissions were automatically granted on that day.
Which of the following describes the access management policy in place at the company?
- A . Mandatory-based
- B . Host-based
- C . Federated access
- D . Role-based
A company recently experienced a break-in whereby a number of hardware assets were stolen through unauthorized access at the back of the building.
Which of the following would BEST prevent this type of theft from occurring in the future?
- A . Motion detection
- B . Perimeter fencing
- C . Monitored security cameras
- D . Badged entry
Which of the following sets of attributes BEST illustrates the characteristics of an insider threat from a security perspective?
- A . Unauthorized, unintentional, benign
- B . Unauthorized, intentional, malicious
- C . Authorized, intentional, malicious
- D . Authorized, unintentional, benign
C
Explanation:
Reference: https://www.sciencedirect.com/topics/computer-science/insider-attack
An analyst needs to provide a recommendation that will allow a custom-developed application to have full access to the system’s processors and peripherals but still be contained securely from other applications that will be developed.
Which of the following is the BEST technology for the analyst to recommend?
- A . Software-based drive encryption
- B . Hardware security module
- C . Unified Extensible Firmware Interface
- D . Trusted execution environment
An organization developed a comprehensive incident response policy. Executive management approved the policy and its associated procedures.
Which of the following activities would be MOST beneficial to evaluate personnel’s familiarity with incident response procedures?
- A . A simulated breach scenario involving the incident response team
- B . Completion of annual information security awareness training by all employees
- C . Tabletop activities involving business continuity team members
- D . Completion of lessons-learned documentation by the computer security incident response team
- E . External and internal penetration testing by a third party
A company just chose a global software company based in Europe to implement a new supply chain management solution.
Which of the following would be the MAIN concern of the company?
- A . Violating national security policy
- B . Packet injection
- C . Loss of intellectual property
- D . International labor laws
A security analyst receives an alert to expect increased and highly advanced cyberattacks originating from a foreign country that recently had sanctions implemented.
Which of the following describes the type of threat actors that should concern the security analyst?
- A . Hacktivist
- B . Organized crime
- C . Insider threat
- D . Nation-state
Which of the following data security controls would work BEST to prevent real Pll from being used in an organization’s test cloud environment?
- A . Digital rights management
- B . Encryption
- C . Access control
- D . Data loss prevention
- E . Data masking
An analyst is working with a network engineer to resolve a vulnerability that was found in a piece of legacy hardware, which is critical to the operation of the organization’s production line. The legacy hardware does not have third-party support, and the OEM manufacturer of the controller is no longer in operation. The analyst documents the activities and verifies these actions prevent remote exploitation of the vulnerability.
Which of the following would be the MOST appropriate to remediate the controller?
- A . Segment the network to constrain access to administrative interfaces.
- B . Replace the equipment that has third-party support.
- C . Remove the legacy hardware from the network.
- D . Install an IDS on the network between the switch and the legacy equipment.
Which of the following types of policies is used to regulate data storage on the network?
- A . Password
- B . Acceptable use
- C . Account management
- D . Retention
D
Explanation:
Reference: http://www.css.edu/administration/information-technologies/computing-policies/computer-and-network-policies.html
The security team at a large corporation is helping the payment-processing team to prepare for a regulatory compliance audit and meet the following objectives:
✑ Reduce the number of potential findings by the auditors.
✑ Limit the scope of the audit to only devices used by the payment-processing team for activities directly impacted by the regulations.
✑ Prevent the external-facing web infrastructure used by other teams from coming into scope.
✑ Limit the amount of exposure the company will face if the systems used by the payment-processing team are compromised.
Which of the following would be the MOST effective way for the security team to meet these objectives?
- A . Limit the permissions to prevent other employees from accessing data owned by the business unit.
- B . Segment the servers and systems used by the business unit from the rest of the network.
- C . Deploy patches to all servers and workstations across the entire organization.
- D . Implement full-disk encryption on the laptops used by employees of the payment-processing team.
A Chief Information Security Officer (CISO) wants to upgrade an organization’s security posture by improving proactive activities associated with attacks from internal and external threats.
Which of the following is the MOST proactive tool or technique that feeds incident response capabilities?
- A . Development of a hypothesis as part of threat hunting
- B . Log correlation, monitoring, and automated reporting through a SIEM platform
- C . Continuous compliance monitoring using SCAP dashboards
- D . Quarterly vulnerability scanning using credentialed scans
A security analyst is reviewing the logs from an internal chat server. The chat.log file is too large to review manually, so the analyst wants to create a shorter log file that only includes lines associated with a user demonstrating anomalous activity.
Below is a snippet of the log:
Which of the following commands would work BEST to achieve the desired result?
- A . grep -v chatter14 chat.log
- B . grep -i pythonfun chat.log
- C . grep -i javashark chat.log
- D . grep -v javashark chat.log
- E . grep -v pythonfun chat.log
- F . grep -i chatter14 chat.log
A proposed network architecture requires systems to be separated from each other logically based on defined risk levels.
Which of the following explains the reason why an architect would set up the network this way?
- A . To complicate the network and frustrate a potential malicious attacker
- B . To reduce the number of IP addresses that are used on the network
- C . To reduce the attack surface of those systems by segmenting the network based on risk
- D . To create a design that simplifies the supporting network
As a proactive threat-hunting technique, hunters must develop situational cases based on likely attack scenarios derived from the available threat intelligence information.
After forming the basis of the scenario, which of the following may the threat hunter construct to establish a framework for threat assessment?
- A . Critical asset list
- B . Threat vector
- C . Attack profile
- D . Hypothesis
A security analyst received a series of antivirus alerts from a workstation segment, and users reported ransomware messages. During lessons-learned activities, the analyst determines the antivirus was able to alert to abnormal behavior but did not stop this newest variant of ransomware.
Which of the following actions should be taken to BEST mitigate the effects of this type of threat in the future?
- A . Enabling application blacklisting
- B . Enabling sandboxing technology
- C . Purchasing cyber insurance
- D . Installing a firewall between the workstations and Internet
A security analyst is looking at the headers of a few emails that appear to be targeting all users at an organization:
Which of the following technologies would MOST likely be used to prevent this phishing attempt?
- A . DNSSEC
- B . DMARC
- C . STP
- D . S/IMAP
A company’s security administrator needs to automate several security processes related to testing for the existence of changes within the environment Conditionally other processes will need to be created based on input from prior processes
Which of the following is the BEST method for accomplishing this task?
- A . Machine learning and process monitoring
- B . API integration and data enrichment
- C . Workflow orchestration and scripting
- D . Continuous integration and configuration management
An employee in the billing department accidentally sent a spreadsheet containing payment card data to a recipient outside the organization. The employee intended to send the spreadsheet to an internal staff member with a similar name and was unaware of the mistake until the recipient replied to the message.
In addition to retraining the employee, which of the following would prevent this from happening in the future?
- A . Implement outgoing filter rules to quarantine messages that contain card data
- B . Configure the outgoing mail filter to allow attachments only to addresses on the whitelist
- C . Remove all external recipients from the employee’s address book
- D . Set the outgoing mail filter to strip spreadsheet attachments from all messages.
A security analyst is reviewing the following log from an email security service.
Which of the following BEST describes the reason why the email was blocked?
- A . The To address is invalid.
- B . The email originated from the www.spamfilter.org URL.
- C . The IP address and the remote server name are the same.
- D . The IP address was blacklisted.
- E . The From address is invalid.
C
Explanation:
Reference: https://www.webopediA.com/TERM/R/RBL.html
Legacy medical equipment, which contains sensitive data, cannot be patched.
Which of the following is the BEST solution to improve the equipment’s security posture?
- A . Move the legacy systems behind a WAF
- B . Implement an air gap for the legacy systems.
- C . Implement a VPN between the legacy systems and the local network.
- D . Place the legacy systems in the DMZ
Massivelog log has grown to 40GB on a Windows server At this size, local tools are unable to read the file, and it cannot be moved off the virtual server where it is located.
Which of the following lines of PowerShell script will allow a user to extract the last 10.000 lines of the loq for review?
- A . tail -10000 Massivelog.log > extract.txt
- B . info tail n -10000 Massivelog.log | extract.txt;
- C . get content ‘./Massivelog.log’ CLast 10000 | extract.txt
- D . get-content ‘./Massivelog.log’ CLast 10000 > extract.txt;
A software development team asked a security analyst to review some code for security vulnerabilities.
Which of the following would BEST assist the security analyst while performing this task?
- A . Static analysis
- B . Dynamic analysis
- C . Regression testing
- D . User acceptance testing
A company recently experienced multiple DNS DDoS attacks, and the information security analyst must provide a DDoS solution to deploy in the company’s datacenter.
Which of the following would BEST prevent future attacks?
- A . Configure a sinkhole on the router.
- B . Buy a UTM to block the number of requests.
- C . Route the queries on the DNS server to 127.0.0.1.
- D . Call the Internet service provider to block the attack.
A Chief Information Security Officer (CISO) is concerned the development team, which consists of contractors, has too much access to customer data. Developers use personal workstations, giving the company little to no visibility into the development activities.
Which of the following would be BEST to implement to alleviate the CISO’s concern?
- A . DLP
- B . Encryption
- C . Test data
- D . NDA
During the forensic analysis of a compromised machine, a security analyst discovers some binaries that are exhibiting abnormal behaviors. After extracting the strings, the analyst finds unexpected content.
Which of the following is the NEXT step the analyst should take?
- A . Only allow whitelisted binaries to execute.
- B . Run an antivirus against the binaries to check for malware.
- C . Use file integrity monitoring to validate the digital signature.
- D . Validate the binaries’ hashes from a trusted source.
A security analyst is researching an incident and uncovers several details that may link to other incidents. The security analyst wants to determine if other incidents are related to the current incident.
Which of the following threat research methodologies would be MOST appropriate for the analyst to use?
- A . Reputation data
- B . CVSS score
- C . Risk assessment
- D . Behavioral analysis
Which of me following BEST articulates the benefit of leveraging SCAP in an organization’s cybersecurity analysis toolset?
- A . It automatically performs remedial configuration changes lo enterprise security services
- B . It enables standard checklist and vulnerability analysis expressions for automaton
- C . It establishes a continuous integration environment for software development operations
- D . It provides validation of suspected system vulnerabilities through workflow orchestration
A company’s blocklist has outgrown the current technologies in place. The ACLS are at maximum, and the IPS signatures only allow a certain
amount of space for domains to be added, creating the need for multiple signatures.
Which of the following configuration changes to the existing controls would be the MOST appropriate to improve performance?
- A . Create an IDS for the current blocklist to determine which domains are showing activity and may need to be removed.
- B . Implement a host-file based solution that will use a list of all domains to deny for all machines on the network
- C . Review the current blocklist to determine which domains can be removed from the list and then update the ACLs and IPS signatures.
- D . Review the current blocklist and prioritize it based on the level of threat severity. Add the domains with the highest severity to the blocklist and remove the lower-severity threats from it.
A system’s authority to operate (ATO) is set to expire in four days. Because of other activities and limited staffing, the organization has neglected to start reauthentication activities until now.
The cybersecurity group just performed a vulnerability scan with the partial set of results shown below:
Based on the scenario and the output from the vulnerability scan, which of the following should the security team do with this finding?
- A . Remediate by going to the web config file, searching for the enforce HTTP validation setting, and manually updating to the correct setting.
- B . Accept this risk for now because this is a “high” severity, but testing will require more than the four days available, and the system ATO needs to be competed.
- C . Ignore it. This is false positive, and the organization needs to focus its efforts on other findings.
- D . Ensure HTTP validation is enabled by rebooting the server.
Portions of a legacy application are being refactored to discontinue the use of dynamic SQL.
Which of the following would be BEST to implement in the legacy application?
- A . Multifactor authentication
- B . Web-application firewall
- C . SQL injection
- D . Parameterized queries
- E . Input validation
A Chief Security Officer (CSO) is working on the communication requirements (or an organization’s incident response plan.
In addition to technical response activities, which of the following is the main reason why communication must be addressed in an effective incident response program?
- A . Public relations must receive information promptly in order to notify the community.
- B . Improper communications can create unnecessary complexity and delay response actions.
- C . Organizational personnel must only interact with trusted members of the law enforcement community.
- D . Senior leadership should act as the only voice for the incident response team when working with forensics teams.
A Chief Security Officer (CSO) is working on the communication requirements (or an organization’s incident response plan.
In addition to technical response activities, which of the following is the main reason why communication must be addressed in an effective incident response program?
- A . Public relations must receive information promptly in order to notify the community.
- B . Improper communications can create unnecessary complexity and delay response actions.
- C . Organizational personnel must only interact with trusted members of the law enforcement community.
- D . Senior leadership should act as the only voice for the incident response team when working with forensics teams.
A Chief Security Officer (CSO) is working on the communication requirements (or an organization’s incident response plan.
In addition to technical response activities, which of the following is the main reason why communication must be addressed in an effective incident response program?
- A . Public relations must receive information promptly in order to notify the community.
- B . Improper communications can create unnecessary complexity and delay response actions.
- C . Organizational personnel must only interact with trusted members of the law enforcement community.
- D . Senior leadership should act as the only voice for the incident response team when working with forensics teams.
A Chief Security Officer (CSO) is working on the communication requirements (or an organization’s incident response plan.
In addition to technical response activities, which of the following is the main reason why communication must be addressed in an effective incident response program?
- A . Public relations must receive information promptly in order to notify the community.
- B . Improper communications can create unnecessary complexity and delay response actions.
- C . Organizational personnel must only interact with trusted members of the law enforcement community.
- D . Senior leadership should act as the only voice for the incident response team when working with forensics teams.
What is the executable file name or the malware?
A network attack that is exploiting a vulnerability in the SNMP is detected.
Which of the following should the cybersecurity analyst do FIRST?
- A . Apply the required patches to remediate the vulnerability.
- B . Escalate the incident to senior management for guidance.
- C . Disable all privileged user accounts on the network.
- D . Temporarily block the attacking IP address.
A
Explanation:
Reference: https://beyondsecurity.com/scan-pentest-network-vulnerabilities-snmp-protocol-version-detection.html
During routine monitoring, a security analyst discovers several suspicious websites that are communicating with a local host.
The analyst queries for IP 192.168.50.2 for a 24-hour period:
To further investigate, the analyst should request PCAP for SRC 192.168.50.2 and.
- A . DST 138.10.2.5.
- B . DST 138.10.25.5.
- C . DST 172.10.3.5.
- D . DST 172.10.45.5.
- E . DST 175.35.20.5.
During an investigation, a security analyst identified machines that are infected with malware the antivirus was unable to detect.
Which of the following is the BEST place to acquire evidence to perform data carving?
- A . The system memory
- B . The hard drive
- C . Network packets
- D . The Windows Registry
A
Explanation:
Reference:
https://resources.infosecinstitute.com/memory-forensics/#gref https://www.computerhope.com/jargon/d/data-carving.htm
A bad actor bypasses authentication and reveals all records in a database through an SQL injection. Implementation of which of the following would work BEST to prevent similar attacks in
- A . Strict input validation
- B . Blacklisting
- C . SQL patching
- D . Content filtering
- E . Output encoding