CompTIA CAS-003 CompTIA Advanced Security Practitioner (CASP) Online Training
CompTIA CAS-003 Online Training
The questions for CAS-003 were last updated at Dec 19,2025.
- Exam Code: CAS-003
- Exam Name: CompTIA Advanced Security Practitioner (CASP)
- Certification Provider: CompTIA
- Latest update: Dec 19,2025
A Chief Information Security Officer (CISO) is developing a new BIA for the organization. The CISO wants to gather requirements to determine the appropriate RTO and RPO for the organization’s ERP .
Which of the following should the CISO interview as MOST qualified to provide RTO/RPO metrics?
- A . Data custodian
- B . Data owner
- C . Security analyst
- D . Business unit director
- E . Chief Executive Officer (CEO)
DRAG DROP
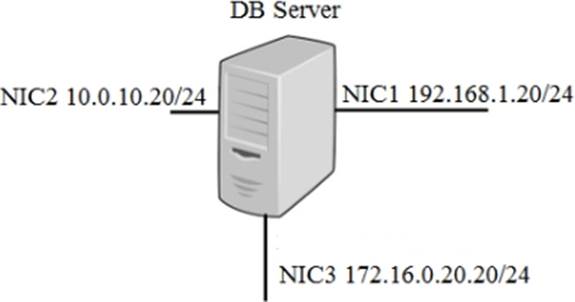
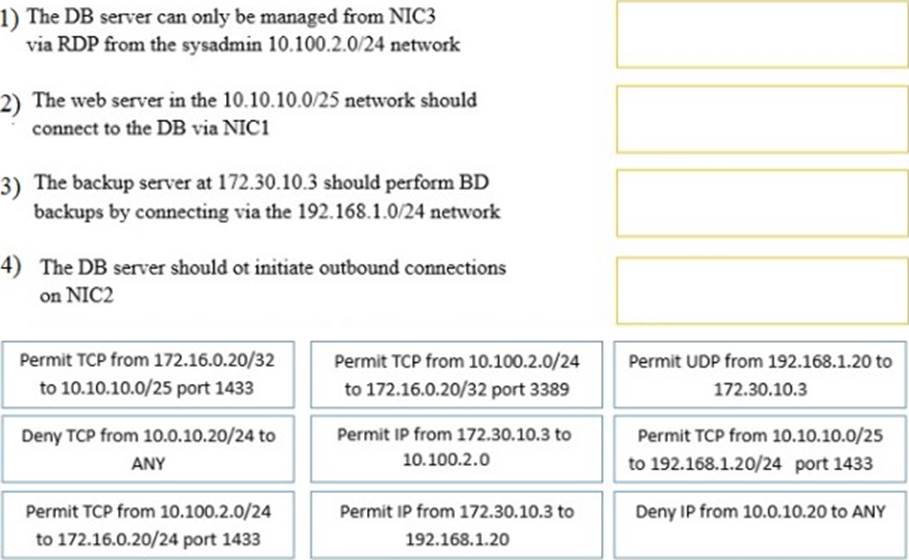
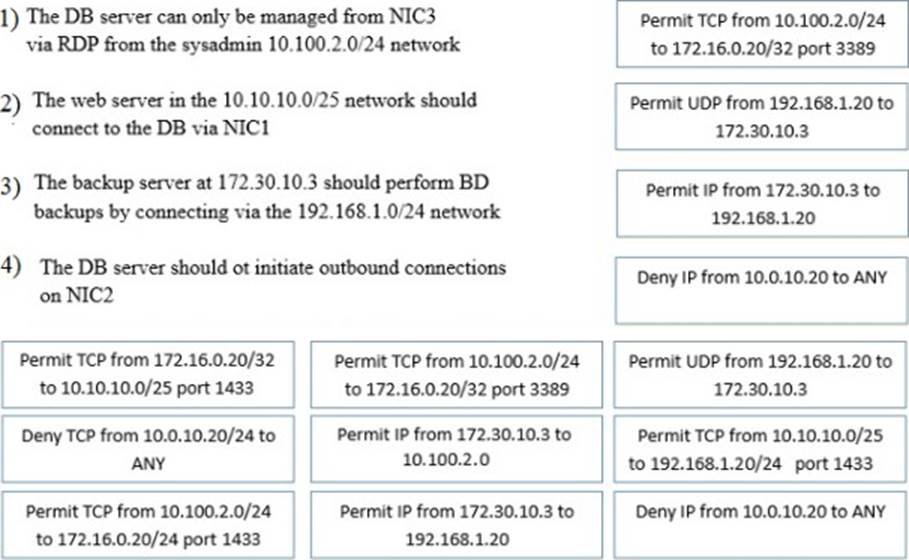
A security administrator must configure the database server shown below to comply with the four requirements listed.
Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.
In the past, the risk committee at Company A has shown an aversion to even minimal amounts of risk acceptance. A security engineer is preparing recommendations regarding the risk of a proposed introducing legacy ICS equipment. The project will introduce a minor vulnerability into the enterprise. This vulnerability does not significantly expose the enterprise to risk and would be expensive against.
Which of the following strategies should the engineer recommended be approved FIRST?
- A . Avoid
- B . Mitigate
- C . Transfer
- D . Accept
A penetration tester noticed special characters in a database table. The penetration tester configured the browser to use an HTTP interceptor to verify that the front-end user registration web form accepts invalid input in the user’s age field. The developer was notified and asked to fix the issue.
Which of the following is the MOST secure solution for the developer to implement?
- A . IF $AGE == “!@#%^&*()_+<>?”:{}[]” THEN ERROR
- B . IF $AGE == [1234567890] {1,3} THEN CONTINUE
- C . IF $AGE != “a-bA-Z!@#$%^&*()_+<>?”{}[]”THEN CONTINUE
- D . IF $AGE == [1-0] {0,2} THEN CONTINUE
An organization is preparing to develop a business continuity plan. The organization is required to meet regulatory requirements relating to confidentiality and availability, which are well-defined. Management has expressed concern following initial meetings that the organization is not fully aware of the requirements associated with the regulations.
Which of the following would be MOST appropriate for the project manager to solicit additional resources for during this phase of the project?
- A . After-action reports
- B . Gap assessment
- C . Security requirements traceability matrix
- D . Business impact assessment
- E . Risk analysis
A developer emails the following output to a security administrator for review:
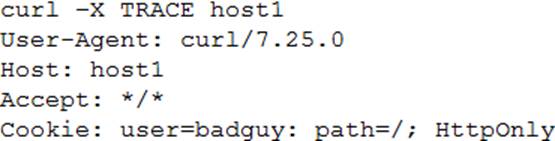
Which of the following tools might the security administrator use to perform further security assessment of this issue?
- A . Port scanner
- B . Vulnerability scanner
- C . Fuzzer
- D . HTTP interceptor
An organization is currently performing a market scan for managed security services and EDR capability .
Which of the following business documents should be released to the prospective vendors in the first step of the process? (Select TWO).
- A . MSA
- B . RFP
- C . NDA
- D . RFI
- E . MOU
- F . RFQ
Providers at a healthcare system with many geographically dispersed clinics have been fined five times this year after an auditor received notice of the following SMS messages:
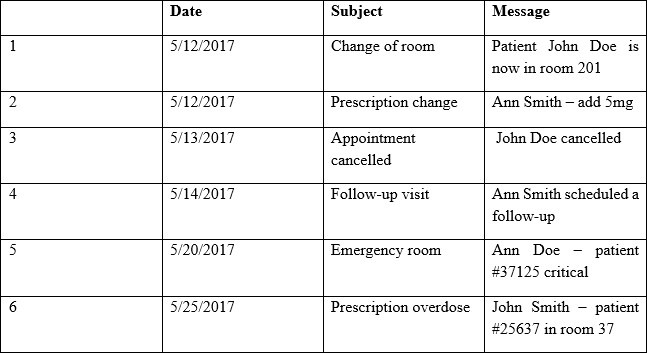
Which of the following represents the BEST solution for preventing future fines?
- A . Implement a secure text-messaging application for mobile devices and workstations.
- B . Write a policy requiring this information to be given over the phone only.
- C . Provide a courier service to deliver sealed documents containing public health informatics.
- D . Implement FTP services between clinics to transmit text documents with the information.
- E . Implement a system that will tokenize patient numbers.
A security engineer has been hired to design a device that will enable the exfiltration of data from within a well-defended network perimeter during an authorized test. The device must bypass all firewalls and NIDS in place, as well as allow for the upload of commands from a centralized command and control answer. The total cost of the device must be kept to a minimum in case the device is discovered during an assessment .
Which of the following tools should the engineer load onto the device being designed?
- A . Custom firmware with rotating key generation
- B . Automatic MITM proxy
- C . TCP beacon broadcast software
- D . Reverse shell endpoint listener
An engineer wants to assess the OS security configurations on a company’s servers. The engineer has downloaded some files to orchestrate configuration checks.
When the engineer opens a file in a text editor, the following excerpt appears:
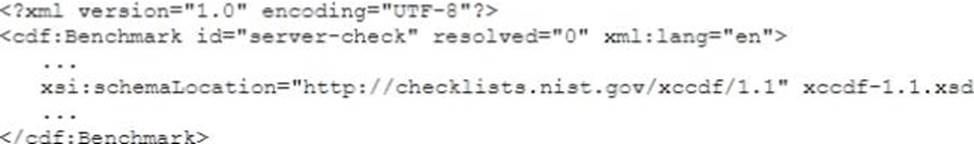
Which of the following capabilities would a configuration compliance checker need to support to interpret this file?
- A . Nessus
- B . Swagger file
- C . SCAP
- D . Netcat
- E . WSDL
Latest CAS-003 Dumps Valid Version with 509 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


ddd
nnn