CompTIA CAS-003 CompTIA Advanced Security Practitioner (CASP) Online Training
CompTIA CAS-003 Online Training
The questions for CAS-003 were last updated at Jun 18,2025.
- Exam Code: CAS-003
- Exam Name: CompTIA Advanced Security Practitioner (CASP)
- Certification Provider: CompTIA
- Latest update: Jun 18,2025
A legacy web application, which is being used by a hospital, cannot be upgraded for 12 months. A new vulnerability is found in the legacy application, and the networking team is tasked with mitigation. Middleware for mitigation will cost $100,000 per year .
Which of the following must be calculated to determine ROI? (Choose two.)
- A . ALE
- B . RTO
- C . MTBF
- D . ARO
- E . RPO
A security administrator was informed that a server unexpectedly rebooted.
The administrator received an export of syslog entries for analysis:
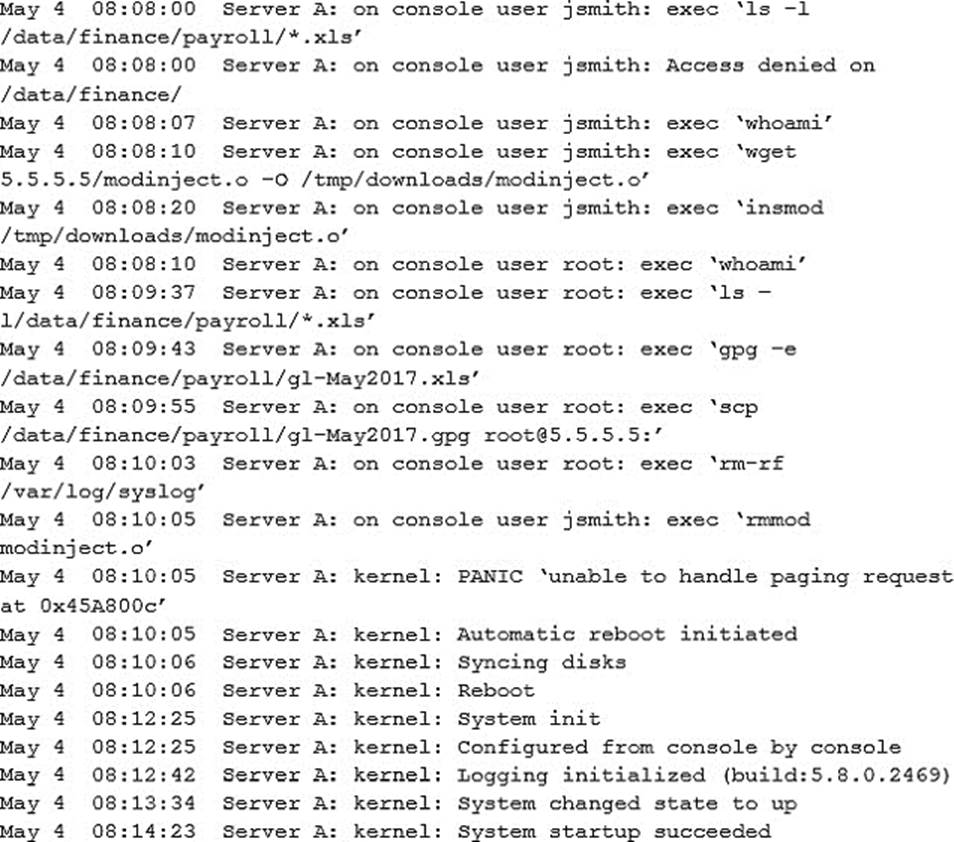
Which of the following does the log sample indicate? (Choose two.)
- A . A root user performed an injection attack via kernel module
- B . Encrypted payroll data was successfully decrypted by the attacker
- C . Jsmith successfully used a privilege escalation attack
- D . Payroll data was exfiltrated to an attacker-controlled host
- E . Buffer overflow in memory paging caused a kernel panic
- F . Syslog entries were lost due to the host being rebooted
Legal counsel has notified the information security manager of a legal matter that will require the preservation of electronic records for 2000 sales force employees. Source records will be email, PC, network shares, and applications.
After all restrictions have been lifted, which of the following should the information manager review?
- A . Data retention policy
- B . Legal hold
- C . Chain of custody
- D . Scope statement
An organization is in the process of integrating its operational technology and information technology areas. As part of the integration, some of the cultural aspects it would like to see include more efficient use of resources during change windows, better protection of critical infrastructure, and the ability to respond to incidents.
The following observations have been identified:
✑ The ICS supplier has specified that any software installed will result in lack of support.
✑ There is no documented trust boundary defined between the SCADA and corporate networks.
✑ Operational technology staff have to manage the SCADA equipment via the engineering workstation.
✑ There is a lack of understanding of what is within the SCADA network.
Which of the following capabilities would BEST improve the security position?
- A . VNC, router, and HIPS
- B . SIEM, VPN, and firewall
- C . Proxy, VPN, and WAF
- D . IDS, NAC, and log monitoring
A systems administrator has installed a disk wiping utility on all computers across the organization and configured it to perform a seven-pass wipe and an additional pass to overwrite the disk with zeros. The company has also instituted a policy that requires users to erase files containing sensitive information when they are no longer needed.
To ensure the process provides the intended results, an auditor reviews the following content from a randomly selected decommissioned hard disk:

Which of the following should be included in the auditor’s report based on the above findings?
- A . The hard disk contains bad sectors
- B . The disk has been degaussed.
- C . The data represents part of the disk BIOS.
- D . Sensitive data might still be present on the hard drives.
A security engineer is assisting a developer with input validation, and they are studying the following code block:
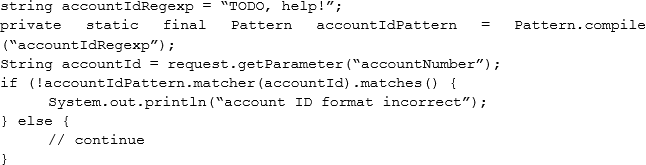
The security engineer wants to ensure strong input validation is in place for customer-provided account identifiers. These identifiers are ten-digit numbers. The developer wants to ensure input validation is fast because a large number of people use the system.
Which of the following would be the BEST advice for the security engineer to give to the developer?
- A . Replace code with Java-based type checks
- B . Parse input into an array
- C . Use regular expressions
- D . Canonicalize input into string objects before validation
An organization’s mobile device inventory recently provided notification that a zero-day vulnerability was identified in the code used to control the baseband of the devices. The device manufacturer is expediting a patch, but the rollout will take several months Additionally several mobile users recently returned from an overseas trip and report their phones now contain unknown applications, slowing device performance Users have been unable to uninstall these applications, which persist after wiping the devices.
Which of the following MOST likely occurred and provides mitigation until the patches are released?
- A . Unauthentic firmware was installed, disable OTA updates and carrier roaming via MDM.
- B . Users opened a spear-phishing email: disable third-party application stores and validate all signed code prior to execution.
- C . An attacker downloaded monitoring applications; perform a full factory reset of the affected devices.
- D . Users received an improperly encoded emergency broadcast message, leading to an integrity loss condition; disable emergency broadcast messages
A software development team is conducting functional and user acceptance testing of internally developed web applications using a COTS solution. For automated testing, the solution uses valid user credentials from the enterprise directory to authenticate to each application. The solution stores the username in plain text and the corresponding password as an encoded string in a script within a file, located on a globally accessible network share. The account credentials used belong to the development team lead.
To reduce the risks associated with this scenario while minimizing disruption to ongoing testing, which of the following are the BEST actions to take? (Choose two.)
- A . Restrict access to the network share by adding a group only for developers to the share’s ACL
- B . Implement a new COTS solution that does not use hard-coded credentials and integrates with directory services
- C . Obfuscate the username within the script file with encoding to prevent easy identification and the account used
- D . Provision a new user account within the enterprise directory and enable its use for authentication to the target applications. Share the username and password with all developers for use in their individual scripts
- E . Redesign the web applications to accept single-use, local account credentials for authentication
An architect was recently hired by a power utility to increase the security posture of the company’s power generation and distribution sites. Upon review, the architect identifies legacy hardware with highly vulnerable and unsupported software driving critical operations. These systems must exchange data with each other, be highly synchronized, and pull from the Internet time sources .
Which of the following architectural decisions would BEST reduce the likelihood of a successful attack without harming operational capability? (Choose two.)
- A . Isolate the systems on their own network
- B . Install a firewall and IDS between systems and the LAN
- C . Employ own stratum-0 and stratum-1 NTP servers
- D . Upgrade the software on critical systems
- E . Configure the systems to use government-hosted NTP servers
A Chief Information Officer (CIO) publicly announces the implementation of a new financial system.
As part of a security assessment that includes a social engineering task, which of the following tasks should be conducted to demonstrate the BEST means to gain information to use for a report on social vulnerability details about the financial system?
- A . Call the CIO and ask for an interview, posing as a job seeker interested in an open position
- B . Compromise the email server to obtain a list of attendees who responded to the invitation who is on the IT staff
- C . Notify the CIO that, through observation at events, malicious actors can identify individuals to befriend
- D . Understand the CIO is a social drinker, and find the means to befriend the CIO at establishments the CIO frequents
Latest CAS-003 Dumps Valid Version with 509 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


ddd
nnn