A user contacts a technician about an issue with a laptop. The user states applications open without being launched and the browser redirects when trying to go to certain websites.
Which of the following is MOST likely the cause of the user’s issue?
- A . Keylogger
- B . Cryptominers
- C . Virus
- D . Malware
D
Explanation:
The most likely cause of the user’s issue of applications opening without being launched and browser redirects when trying to go to certain websites is malware. Malware is a general term that refers to any software or code that is malicious or harmful to a computer or system. Malware can perform various unwanted or unauthorized actions on a computer or system, such as opening applications, redirecting browsers, displaying ads, stealing data, encrypting files or damaging hardware. Malware can infect a computer or system through various means, such as email attachments, web downloads, removable media or network connections. Keylogger is a type of malware that records and transmits the keystrokes made by a user on a keyboard. Keylogger can be used to steal personal or sensitive information, such as passwords, credit card numbers or chat messages. Keylogger does not typically open applications or redirect browsers but only captures user inputs. Cryptominers are a type of malware that use the computing resources of a computer or system to mine cryptocurrency, such as Bitcoin or Ethereum. Cryptominers can degrade the performance and increase the power consumption of a computer or system. Cryptominers do not typically open applications or redirect browsers but only consume CPU or GPU cycles. Virus is a type of malware that infects and replicates itself on other files or programs on a computer or system.
Which of the following is MOST likely contained in an EULA?
- A . Chain of custody
- B . Backup of software code
- C . Personally identifiable information
- D . Restrictions of use
D
Explanation:
An EULA (End-User License Agreement) is a legally binding contract between a software supplier and a customer or end-user, generally made available to the customer via a retailer acting as an intermediary. A EULA specifies in detail the rights and restrictions which apply to the use of the software. Some of the main terms included in an EULA are the terms and scope of the license, any licensing fees, warranties and disclaimers, limitation of liability, revocation or termination of the license, and intellectual property information and restrictions on using the license (e.g. modification and copying)1 https://www.termsfeed.com/blog/eula-vs-terms-conditions/
A technician has been asked to set up a new wireless router with the best possible security.
Which of the following should the technician implement?
- A . WPS
- B . TKIP
- C . WPA3
- D . WEP
C
Explanation:
WPA3 (Wi-Fi Protected Access version 3) is the latest version of Wi-Fi security and offers the highest level of protection available. It is designed to protect against brute force password attempts and protect against eavesdropping and man-in-the-middle attacks. WPA3 also supports the use of stronger encryption algorithms, such as the Advanced Encryption Standard (AES), which provides additional protection for wireless networks. WPA3 should be implemented in order to ensure the best possible security for the new wireless router.
A user purchased a netbook that has a web-based, proprietary operating system.
Which of the following operating systems is MOST likely installed on the netbook?
- A . macOS
- B . Linux
- C . Chrome OS
- D . Windows
C
Explanation:
A user purchased a netbook that has a web-based, proprietary operating system.
Which of the following operating systems is MOST likely installed on the netbook?
- A . macOS
- B . Linux
- C . Chrome OS
- D . Windows
C
Explanation:
A technician needs to formal a USB drive to transfer 20GB of data from a Linux computer to a Windows computer.
Which of the following filesystems will the technician MOST likely use?
- A . FAT32
- B . ext4
- C . NTFS
- D . exFAT
D
Explanation:
A technician needs to manually set an IP address on a computer that is running macOS.
Which of the following commands should the technician use?
- A . ipconfig
- B . ifconfig
- C . arpa
- D . ping
B
Explanation:
ifconfig is a command-line utility that allows you to configure network interfaces on macOS and other Unix-like systems1. To set an IP address using ifconfig, you need to know the name of the network interface you want to configure (such as en0 or en1), and the IP address you want to assign (such as 192.168.0.150). You also need to use sudo to run the command with administrative privileges2. The syntax of the command is: sudo ifconfig interface address
For example, to set the IP address of en1 to 192.168.0.150, you would type:
sudo ifconfig en1 192.168.0.150
You may also need to specify other parameters such as subnet mask, gateway, or DNS servers, depending on your network configuration3. The other commands are not directly related to setting an IP address on macOS. ipconfig is a similar command for Windows systems4, arpa is a domain name used for reverse DNS lookup, and ping is a command for testing network connectivity.
A Chief Executive Officer has learned that an exploit has been identified on the web server software, and a patch is not available yet.
Which of the following attacks MOST likely occurred?
- A . Brute force
- B . Zero day
- C . Denial of service
- D . On-path
B
Explanation:
A zero-day attack is an attack that exploits a previously unknown vulnerability in a computer application, meaning that the attack occurs on “day zero” of awareness of the vulnerability
✑ Configuring AAA Services. Retrieved from https://www.cisco.com/c/en/us/td/docs/routers/crs/software/crs_r4-0/security/configuration/guide/sc40crsbook_chapter1.html
An organization’s Chief Financial Officer (CFO) is concerned about losing access to very sensitive, legacy unmaintained PII on a workstation if a ransomware outbreak occurs. The CFO has a regulatory requirement to retain this data for many years.
Which of the following backup methods would BEST meet the requirements?
- A . A daily, incremental backup that is saved to the corporate file server
- B . An additional, secondary hard drive in a mirrored RAID configuration
- C . A full backup of the data that is stored of site in cold storage
- D . Weekly, differential backups that are stored in a cloud-hosting provider
C
Explanation:
According to CompTIA A+ Core 2 objectives, a full backup stored off-site provides the greatest protection against data loss in the event of a ransomware attack or other data disaster. By storing the backup in a separate physical location, it is less likely to be affected by the same event that could cause data loss on the original system. Cold storage is a term used for data archiving, which typically refers to a long-term storage solution that is used for retaining data that is infrequently accessed, but still needs to be kept for regulatory or compliance reasons.
A user reports a computer is running slow.
Which of the following tools will help a technician identity the issued
- A . Disk Cleanup
- B . Group Policy Editor
- C . Disk Management
- D . Resource Monitor
D
Explanation:
Resource Monitor will help a technician identify the issue when a user reports a computer is running slow1
A technician has verified that a user’s computer has a virus, and the antivirus software is out Of date.
Which of the following steps should the technician take NEXT?
- A . Quarantine the computer.
- B . use a previous restore point,
- C . Educate the end user about viruses
- D . Download the latest virus definitions
A
Explanation:
Quarantining the computer should be the next step because it prevents the virus from spreading to other systems in the network. This can help to contain the infection while further actions are taken to remove the virus. After quarantining the computer, the technician can proceed with steps such as updating the antivirus software, scanning the system, and removing any detected threats.
Which of the following is used as a password manager in the macOS?
- A . Terminal
- B . FileVault
- C . Privacy
- D . Keychain
D
Explanation:
Keychain is a feature of macOS that securely stores passwords, account numbers, and other confidential information for your Mac, apps, servers, and websites1. You can use the Keychain Access app on your Mac to view and manage your keychains and the items stored in them1. Keychain can also sync your passwords and other secure information across your devices using iCloud Keychain1. Keychain can be used as a password manager in macOS to help you keep track of and protect your passwords.
References: 1: Manage passwords using keychains on Mac (https://support.apple.com/guide/mac-help/use-keychains-to-store-passwords-mchlf375f392/mac)
A user received the following error upon visiting a banking website:
The security presented by website was issued a different website’ s address.
A technician should instruct the user to:
- A . clear the browser cache and contact the bank.
- B . close out of the site and contact the bank.
- C . continue to the site and contact the bank.
- D . update the browser and contact the bank.
B
Explanation:
A Windows user recently replaced a computer The user can access the public internet on the computer; however, an internal site at https7/companyintranet.com:8888 is no longer loading.
Which of the following should a technician adjust to resolve the issue?
- A . Default gateway settings
- B . DHCP settings
- C . IP address settings
- D . Firewall settings
- E . Antivirus settings
D
Explanation:
The technician should adjust the firewall settings to resolve the issue of not being able to access an internal site at https://companyintranet.com:8888. The firewall settings control how the firewall filters and allows network traffic based on rules and policies. The firewall settings may be blocking or preventing the access to the internal site by mistake or by default, especially if the site uses a non-standard port number such as 8888. The technician should check and modify the firewall settings to allow the access to the internal site or its port number. Default gateway settings determine how a computer connects to other networks or the internet. Default gateway settings are not likely to cause the issue of not being able to access an internal site if the user can access the public internet. DHCP settings determine how a computer obtains its IP address and other network configuration parameters automatically from a DHCP server. DHCP settings are not likely to cause the issue of not being able to access an internal site if the user can access other network resources. IP address settings determine how a computer identifies itself and communicates with other devices on a network. IP address settings are not likely to cause the issue of not being able to access an internal site if the user can access other network resources. Antivirus settings control how the antivirus software scans and protects the computer from malware and threats. Antivirus settings are less likely to cause the issue of not being able to access an internal site than firewall settings, unless the antivirus software has its own firewall feature that may interfere with the network traffic. References: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 1.6
A technician needs to recommend the best backup method that will mitigate ransomware attacks. Only a few files are regularly modified, however, storage space is a concern.
Which of the following backup methods would BEST address these concerns?
- A . Full
- B . Differential
- C . Off-site
- D . Grandfather-father-son
B
Explanation:
The differential backup method would best address these concerns. Differential backups only back up files that have changed since the last full backup, which means that only a few files would be backed up each time. This would help to mitigate the risk of ransomware attacks, as only a few files would be affected if an attack occurred. Additionally, differential backups require less storage space than full backups.
A user is unable to access a website, which is widely used across the organization, and receives the following error message:
The security certificate presented by this website has expired or is not yet valid.
The technician confirms the website works when accessing it from another computer but not from the user’s computer.
Which of the following should the technician perform NEXT to troubleshoot the issue?
- A . Reboot the computer.
- B . Reinstall the OS.
- C . Configure a static 12
- D . Check the computer’s date and time.
D
Explanation:
The error message indicates that the security certificate presented by the website has either expired or is not yet valid. This can happen if the computer’s clock has the wrong date or time, as SSL/TLS certificates have a specific validity period. If the clock is off by too much, it may cause the certificate to fail to validate. Therefore, the technician should check the computer’s date and time and ensure that they are correct.
Once weekly a user needs Linux to run a specific open-source application that is not available for the currently installed Windows platform. The user has limited bandwidth throughout the day.
Which of the following solutions would be the MOST efficient, allowing for parallel execution of the Linux application and Windows applications?
- A . Install and run Linux and the required application in a PaaS cloud environment
- B . Install and run Linux and the required application as a virtual machine installed under the Windows OS
- C . Use a swappable drive bay for the boot drive and install each OS with applications on its own drive Swap the drives as needed
- D . Set up a dual boot system by selecting the option to install Linux alongside Windows
B
Explanation:
The user should install and run Linux and the required application as a virtual machine installed under the Windows OS. This solution would allow for parallel execution of the Linux application and Windows applications2.
The MOST efficient solution that allows for parallel execution of the Linux application and Windows applications is to install and run Linux and the required application as a virtual machine installed under the Windows OS. This is because it allows you to run both Linux and Windows together without the need to keep the Linux portion confined to a VM window 3.
The network was breached over the weekend System logs indicate that a single user’s account was successfully breached after 500 attempts with a dictionary attack.
Which of the following would BEST mitigate this threat?
- A . Encryption at rest
- B . Account lockout
- C . Automatic screen lock
- D . Antivirus
B
Explanation:
Account lockout would best mitigate the threat of a dictionary attack1
A technician is setting up a backup method on a workstation that only requires two sets of tapes to restore.
Which of the following would BEST accomplish this task?
- A . Differential backup
- B . Off-site backup
- C . Incremental backup
- D . Full backup
A
Explanation:
HOTSPOT
Welcome to your first day as a Fictional Company. LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
Click on individual tickers to see the ticket details. View attachments to determine the problem.
Select the appropriate issue from the ‘issue’ drop-down menu. Then, select the MOST efficient resolution from the ‘Resolution’ drop-down menu. Finally, select the proper command or verification to remediate or confirm your fix of the issue from the Verify Resolve drop-down menu.
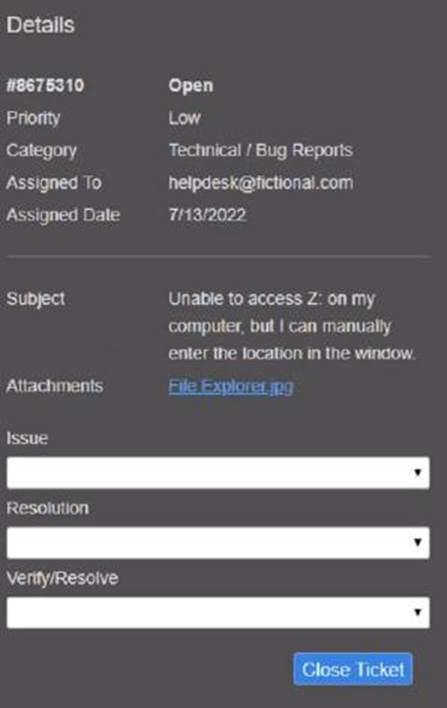
Explanation:
Graphical user interface, text, application
Description automatically generated
A technician is troubleshooting a PC that has been performing poorly. Looking at the Task Manager, the technician sees that CPU and memory resources seem fine, but disk throughput is at 100%.
Which of the following types of malware is the system MOST likely infected with?
- A . Keylogger
- B . Rootkit
- C . Ransomware
- D . Trojan
C
Explanation:
Ransomware is a type of malware that encrypts the files on the victim’s computer and demands a ransom for their decryption. Ransomware can cause high disk throughput by encrypting large amounts of data in a short time.
A user is attempting to browse the internet using Internet Explorer. When trying to load a familiar web page, the user is unexpectedly redirected to an unfamiliar website.
Which of the following would MOST likely solve the issue?
- A . Updating the operating system
- B . Changing proxy settings
- C . Reinstalling the browser
- D . Enabling port forwarding
B
Explanation:
Sensitive data was leaked from a user’s smartphone. A technician discovered an unapproved application was installed, and the user has full access to the device’s command shell.
Which of the following is the NEXT step the technician should take to find the cause of the leaked data?
- A . Restore the device to factory settings.
- B . Uninstall the unapproved application.
- C . Disable the ability to install applications from unknown sources.
- D . Ensure the device is connected to the corporate WiFi network.
B
Explanation:
The technician should disable the user’s access to the device’s command shell. This will prevent the user from accessing sensitive data and will help to prevent further data leaks. The technician should then investigate the unapproved application to determine if it is the cause of the data leak. If the application is found to be the cause of the leak, the technician should uninstall the application and restore the device to factory settings. If the application is not the cause of the leak, the technician should investigate further to determine the cause of the leak. Disabling the ability to install applications from unknown sources can help to prevent future data leaks, but it is not the next step the technician should take in this scenario. Ensuring the device is connected to the corporate WiFi network is not relevant to this scenario1
Which of the following Linux commands would be used to install an application?
- A . yum
- B . grep
- C . Is
- D . sudo
A
Explanation:
Which of the following default system tools can be used in macOS to allow the technician to view the screen simultaneously with the user?
- A . Remote Assistance
- B . Remote Desktop Protocol
- C . Screen Sharing
- D . Virtual Network Computing
C
Explanation:
Screen Sharing is the default system tool that can be used in macOS to allow the technician to view the screen simultaneously with the user. Screen Sharing is a built-in app that lets users share their Mac screen with another Mac on the network. The user can enable screen sharing in the System Preferences > Sharing pane, and then allow other users to request or enter a password to access their screen1. The technician can launch the Screen Sharing app from the Spotlight search or the Finder sidebar, and then enter the user’s name, address, or Apple ID to connect to their screen2. Remote Assistance is a Windows feature that allows users to invite someone to help them with a problem on their PC3. Remote Desktop Protocol (RDP) is a protocol that allows users to connect to a remote computer over a network4. Virtual Network Computing (VNC) is a technology that allows users to share their screen with other devices using a VNC viewer app1. These are not default system tools in macOS, although they can be used with third-party software or settings.
References:
1: https://support.apple.com/guide/mac-help/share-the-screen-of-another-mac-mh14066/mac
2: https://www.howtogeek.com/449239/how-to-share-your-macs-screen-with-another-mac/
3: https://support.microsoft.com/en-us/windows/solve-pc-problems-over-a-remote-connection-b077e31a-16f4-2529-1a47-21f6a9040bf3
4: https://docs.microsoft.com/en-us/windows-server/remote/remote-desktop-services/clients/remote-desktop-protocol
A systems administrator is creating a new document with a list of the websites that users are allowed to access.
Which of the following types of documents is the administrator MOST likely creating?
- A . Access control list
- B . Acceptable use policy
- C . Incident report
- D . Standard operating procedure
B
Explanation:
A user receives an error message from an online banking site that states the following:
Your connection is not private. Authority invalid.
Which of the following actions should the user take NEXT?
- A . Proceed to the site.
- B . Use a different browser.
- C . Report the error to the bank.
- D . Reinstall the browser.
C
Explanation:
The error message “Your connection is not private. Authority invalid.” means that the web browser cannot verify the identity or security of the website’s SSL certificate. This could indicate that the website has been compromised, has a configuration error, or has an expired or invalid certificate. The user should not proceed to the site or use a different browser, as this could expose their sensitive information to potential attackers. The user should also not reinstall the browser, as this is unlikely to fix the error and could cause data loss. The best action for the user to take is to report the error to the bank and wait for them to resolve it.
References: : How to Fix “Your Connection Is Not Private” Errors (https://www.howtogeek.com/874436/how-to-fix-your-connection-is-not-private-errors/) : Fix connection errors (https://support.google.com/chrome/answer/6098869?hl=en)
A company needs to securely dispose of data stored on optical discs.
Which of the following is the MOST effective method to accomplish this task?
- A . Degaussing
- B . Low-level formatting
- C . Recycling
- D . Shredding
D
Explanation:
Shredding is the most effective method to securely dispose of data stored on optical discs12
References: 4.
How Can I Safely Destroy Sensitive Data CDs/DVDs? – How-To Geek. Retrieved from https://www.howtogeek.com/174307/how-can-i-safely-destroy-sensitive-data-cdsdvds/ 5. Disposal ― UK Data Service. Retrieved from https://ukdataservice.ac.uk/learning-hub/research-data-management/store-your-data/disposal/
Which of the following is a data security standard for protecting credit cards?
- A . PHI
- B . NIST
- C . PCI
- D . GDPR
C
Explanation:
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure that ALL companies that accept, process, store or transmit credit card information maintain a secure environment.
A technician is setting up a desktop computer in a small office. The user will need to access files on a drive shared from another desktop on the network.
Which of the following configurations should the technician employ to achieve this goal?
- A . Configure the network as private
- B . Enable a proxy server
- C . Grant the network administrator role to the user
- D . Create a shortcut to public documents
A
Explanation:
The technician should configure the network as private to allow the user to access files on a drive shared from another desktop on the network1
Which of the following only has a web browser interface?
- A . Linux
- B . Microsoft Windows
- C . iOS
- D . Chromium
D
Explanation:
Chromium is an operating system that only has a web browser interface. Chromium is an open-source project that provides the source code and framework for Chrome OS, which is a Linux-based operating system developed by Google. Chromium and Chrome OS are designed to run web applications and cloud services through the Chrome web browser, which is the only user interface available on the system. Chromium and Chrome OS are mainly used on devices such as Chromebooks, Chromeboxes and Chromebits. Linux is an operating system that does not only have a web browser interface but also a graphical user interface and a command-line interface. Linux is an open-source and customizable operating system that can run various applications and services on different devices and platforms. Linux can also support different web browsers, such as Firefox, Opera and Chromium. Microsoft Windows is an operating system that does not only have a web browser interface but also a graphical user interface and a command-line interface. Microsoft Windows is a proprietary and popular operating system that can run various applications and services on different devices and platforms. Microsoft Windows can also support different web browsers, such as Edge, Internet Explorer and Chrome. iOS is an operating system that does not only have a web browser interface but also a graphical user interface and a voice-based interface. iOS is a proprietary and mobile operating system developed by Apple that can run various applications and services on devices such as iPhone, iPad and iPod Touch. iOS can also support different web browsers, such as Safari, Firefox and Chrome. References: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 1.1
An administrator has submitted a change request for an upcoming server deployment.
Which of the following must be completed before the change can be approved?
- A . Risk analysis
- B . Sandbox testing
- C . End user acceptance
- D . Lessons learned
A
Explanation:
A risk analysis must be completed before a change request for an upcoming server deployment can be approved 1 Risk analysis is an important step in the change management process because it helps identify and mitigate potential risks before changes are implemented. Once the risks have been analyzed and the appropriate measures have been taken to minimize them, the change can be approved and implemented.
A developer is creating a shell script to automate basic tasks in Linux.
Which of the following file types are supported by default?
- A . .py
- B . .js
- C . .vbs
- D . .sh
D
Explanation:
https://www.educba.com/shell-scripting-in-linux/
A change advisory board just approved a change request.
Which of the following is the MOST likely next step in the change process?
- A . End user acceptance
- B . Perform risk analysis
- C . Communicate to stakeholders
- D . Sandbox testing
C
Explanation:
Which of the following is the STRONGEST wireless configuration?
- A . WPS
- B . WPA3
- C . WEP
- D . WMN
B
Explanation:
The strongest wireless configuration is B. WPA3. WPA3 is the most up-to-date wireless encryption protocol and is the most secure choice. It replaces PSK with SAE, a more secure way to do the initial key exchange. At the same time, the session key size of WPA3 increases to 128-bit in WPA3-Personal mode and 192-bit in WPA3-Enterprise, which makes the password harder to crack than the previous Wi-Fi security standards https://www.makeuseof.com/tag/wep-wpa-wpa2-wpa3-explained/
A customer calls a service support center and begins yelling at a technician about a feature for a product that is not working to the customer’s satisfaction. This feature is not supported by the service support center and requires a field technician to troubleshoot. The customer continues to demand service.
Which of the following is the BEST course of action for the support center representative to take?
- A . Inform the customer that the issue is not within the scope of this department.
- B . Apologize to the customer and escalate the issue to a manager.
- C . Ask the customer to explain the issue and then try to fix it independently.
- D . Respond that the issue is something the customer should be able to fix.
B
Explanation:
Apologizing to the customer and escalating the issue to a manager is the best course of action for the support center representative to take. This shows empathy and professionalism and allows the manager to handle the situation and provide the appropriate service or resolution for the customer.
A user calls the help desk to report that none of the files on a PC will open. The user also indicates a program on the desktop is requesting payment in exchange for file access A technician verifies the user’s PC is infected with ransorrrware.
Which of the following should the technician do FIRST?
- A . Scan and remove the malware
- B . Schedule automated malware scans
- C . Quarantine the system
- D . Disable System Restore
C
Explanation:
The technician should quarantine the system first1
Reference: CompTIA A+ Certification Exam: Core 2 Objectives Version 4.0. Retrieved from https://partners.comptia.org/docs/default-source/resources/comptia-a-220-1102-exam-objectives-(3-0)
A new spam gateway was recently deployed at a small business However; users still occasionally receive spam. The management team is concerned that users will open the messages and potentially
infect the network systems.
Which of the following is the MOST effective method for dealing with this Issue?
- A . Adjusting the spam gateway
- B . Updating firmware for the spam appliance
- C . Adjusting AV settings
- D . Providing user training
D
Explanation:
The most effective method for dealing with spam messages in a small business is to provide user training1. Users should be trained to recognize spam messages and avoid opening them1. They should also be trained to report spam messages to the IT department so that appropriate action can be taken1. In addition, users should be trained to avoid clicking on links or downloading attachments from unknown sources1. By providing user training, the management team can reduce the risk of users opening spam messages and potentially infecting the network systems1.
A user calls the help desk to report that Windows installed updates on a laptop and rebooted overnight. When the laptop started up again, the touchpad was no longer working. The technician thinks the software that controls the touchpad might be the issue.
Which of the following tools should the technician use to make adjustments?
- A . eventvwr.msc
- B . perfmon.msc
- C . gpedic.msc
- D . devmgmt.msc
D
Explanation:
The technician should use devmgmt.msc tool to make adjustments for the touchpad issue after Windows installed updates on a laptop. Devmgmt.msc is a command that opens the Device Manager, which is a utility that allows users to view and manage the hardware devices and drivers installed on a computer. The technician can use the Device Manager to check the status, properties and compatibility of the touchpad device and its driver, and perform actions such as updating, uninstalling or reinstalling the driver, enabling or disabling the device, or scanning for hardware changes. Eventvwr.msc is a command that opens the Event Viewer, which is a utility that allows users to view and monitor the system logs and events. The Event Viewer may provide some information or clues about the touchpad issue, but it does not allow users to manage or troubleshoot the device or its driver directly. Perfmon.msc is a command that opens the Performance Monitor, which is a utility that allows users to measure and analyze the performance of the system
In which of the following scenarios would remote wipe capabilities MOST likely be used? (Select TWO).
- A . A new IT policy requires users to set up a lock screen PIN.
- B . A user is overseas and wants to use a compatible international SIM Card.
- C . A user left the phone at home and wants to prevent children from gaining access to the phone.
- D . A user traded in the company phone for a cell carrier upgrade by mistake.
- E . A user cannot locate the phone after attending a play at a theater.
- F . A user forgot the phone in a taxi, and the driver called the company to return the device.
D,E
Explanation:
A network administrator is deploying a client certificate lo be used for Wi-Fi access for all devices m an organization. The certificate will be used in conjunction with the user’s existing username and password.
Which of the following BEST describes the security benefits realized after this deployment?
- A . Multifactor authentication will be forced for Wi-Fi
- B . All Wi-Fi traffic will be encrypted in transit
- C . Eavesdropping attempts will be prevented
- D . Rogue access points will not connect
A
Explanation:
Multifactor authentication will be forced for Wi-Fi after deploying a client certificate to be used for Wi-Fi access for all devices in an organization3 References:
✑ CompTIA Security+ (Plus) Practice Test Questions | CompTIA. Retrieved from https://www.comptia.org/training/resources/comptia-security-practice-tests
A technician is troubleshooting a customer’s PC and receives a phone call. The technician does not take the call and sets the phone to silent.
Which of the following BEST describes the technician’s actions?
- A . Avoid distractions
- B . Deal appropriately with customer’s confidential material.
- C . Adhere to user privacy policy
- D . Set and meet timelines
A
Explanation:
The technician’s action of setting the phone to silent while troubleshooting the customer’s PC is an example of avoiding distractions. By setting the phone to silent, the technician is ensuring that they are able to focus on the task at hand without any distractions that could potentially disrupt their workflow. This is an important practice when handling customer’s confidential material, as it ensures that the technician is able to focus on the task and not be distracted by any external sources. Furthermore, it also adheres to user privacy policies, as the technician is not exposing any confidential information to any external sources.
A technician is installing a program from an ISO file.
Which of the following steps should the technician take?
- A . Mount the ISO and run the installation file.
- B . Copy the ISO and execute on the server.
- C . Copy the ISO file to a backup location and run the ISO file.
- D . Unzip the ISO and execute the setup.exe file.
A
Explanation:
Mounting the ISO and running the installation file is the correct way to install a program from an ISO file. An ISO file is an image of a disc that contains all the files and folders of a program. Mounting the ISO means creating a virtual drive that can access the ISO file as if it were a physical disc. Running the installation file means executing the setup program that will install the program on the computer
A bank would like to enhance building security in order to prevent vehicles from driving into the building while also maintaining easy access for customers.
Which of the following BEST addresses this need?
- A . Guards
- B . Bollards
- C . Motion sensors
- D . Access control vestibule
B
Explanation:
Bollards are the best solution to enhance building security in order to prevent vehicles from driving into the building while also maintaining easy access for customers4 References: 2. Bollards. Retrieved from https://en.wikipedia.org/wiki/Bollard
A technician is upgrading the backup system for documents at a high-volume law firm. The current backup system can retain no more than three versions of full backups before failing. The law firm is not concerned about restore times but asks the technician to retain more versions when possible.
Which of the following backup methods should the technician MOST likely implement?
- A . Full
- B . Mirror
- C . Incremental
- D . Differential
C
Explanation:
Incremental backup is a backup method that only backs up the files that have changed since the last backup, whether it was a full or an incremental backup. Incremental backup can save storage space and bandwidth, as it does not copy the same files over and over again. Incremental backup can also retain more versions of backups, as it only stores the changes made to the files. However, incremental backup can have longer restore times, as it requires restoring the last full backup and all the subsequent incremental backups in order to recover the data. The law firm is not concerned about restore times but asks the technician to retain more versions when possible, so incremental backup would be a suitable choice for them.
A user receives a notification indicating the antivirus protection on a company laptop is out of date. A technician is able to ping the user’s laptop. The technician checks the antivirus parent servers and sees the latest signatures have been installed. The technician then checks the user’s laptop and finds the antivirus engine and definitions are current.
Which of the following has MOST likely occurred?
- A . Ransomware
- B . Failed OS updates
- C . Adware
- D . Missing system files
C
Explanation:
Each time a user tries to go to the selected web search provider, a different website opens.
Which of the following should the technician check FIRST?
- A . System time
- B . IP address
- C . DNS servers
- D . Windows updates
C
Explanation:
When a user experiences unexpected or erratic behavior while browsing the internet, it could be caused by the DNS servers. DNS translates human-readable domain names (like google.com) into IP addresses, which computers can use to communicate with web servers. If the DNS servers are not functioning correctly or have been compromised, it can result in the browser being redirected to unintended websites.
A technician is troubleshooting an issue involving programs on a Windows 10 machine that are loading on startup but causing excessive boot times.
Which of the following should the technician do to selectively prevent programs from loading?
- A . Right-click the Windows button, then select Run entering shell startup and clicking OK, and then move items one by one to the Recycle Bin
- B . Remark out entries listed HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows>CurrentVersion>Run
- C . Manually disable all startup tasks currently listed as enabled and reboot checking for issue resolution at startup
- D . Open the Startup tab and methodically disable items currently listed as enabled and reboot, checking for issue resolution at each startup.
D
Explanation:
This is the most effective way to selectively prevent programs from loading on a Windows 10 machine. The Startup tab can be accessed by opening Task Manager and then selecting the Startup tab. From there, the technician can methodically disable items that are currently listed as enabled, reboot the machine, and check for issue resolution at each startup. If the issue persists, the technician can then move on to disabling the next item on the list.
A user calls the help desk to report potential malware on a computer. The anomalous activity began after the user clicked a link to a free gift card in a recent email The technician asks the user to describe any unusual activity, such as slow performance, excessive pop-ups, and browser redirections.
Which of the following should the technician do NEXT?
- A . Advise the user to run a complete system scan using the OS anti-malware application
- B . Guide the user to reboot the machine into safe mode and verify whether the anomalous activities are still present
- C . Have the user check for recently installed applications and outline those installed since the link in the email was clicked
- D . Instruct the user to disconnect the Ethernet connection to the corporate network.
D
Explanation:
First thing you want to do is quarantine/disconnect the affected system from the network so whatever malicious software doesn’t spread.
A mobile phone user has downloaded a new payment application that allows payments to be made with a mobile device. The user attempts to use the device at a payment terminal but is unable to do so successfully. The user contacts a help desk technician to report the issue.
Which of the following should the technician confirm NEXT as part of the troubleshooting process?
- A . If airplane mode is enabled
- B . If Bluetooth is disabled
- C . If NFC is enabled
- D . If WiFi is enabled
- E . If location services are disabled
C
Explanation:
NFC stands for Near Field Communication, and it is a wireless technology that allows your phone to act as a contactless payment device, among other things2. Payment applications that allow payments to be made with a mobile device usually rely on NFC to communicate with the payment terminal1. Therefore, if NFC is disabled on the phone, the payment will not work.
To enable NFC on an Android phone, you need to follow these steps3:
✑ On your Android device, open the Settings app.
✑ Select Connected devices.
✑ Tap on Connection preferences.
✑ You should see the NFC option. Toggle it on.
The other options are not directly related to using a payment application with a mobile device. Airplane mode is a setting that disables all wireless communication on the phone, including NFC4, but it also affects calls, texts, and internet access. Bluetooth is a wireless technology that allows you to connect your phone with other devices such as headphones or speakers, but it is not used for contactless payments. Wi-Fi is a wireless technology that allows you to access the internet or a local network, but it is also not used for contactless payments. Location services are a feature that allows your phone to determine your geographic location using GPS or other methods, but they are not required for contactless payments.
A company is deploying mobile phones on a one-to-one basis, but the IT manager is concerned that users will root/jailbreak their phones.
Which of the following technologies can be implemented to prevent this issue?
- A . Signed system images
- B . Antivirus
- C . SSO
- D . MDM
D
Explanation:
MDM stands for Mobile Device Management, and it is a way of remotely managing and securing mobile devices that are used for work purposes1. MDM can enforce policies and restrictions on the devices, such as preventing users from installing unauthorized apps, modifying system settings, or accessing root privileges2. MDM can also monitor device status, wipe data, lock devices, or locate lost or stolen devices1.
A user enabled a mobile device’s screen lock function with pattern unlock. The user is concerned someone could access the mobile device by repeatedly attempting random patterns to unlock the device.
Which of the following features BEST addresses the user’s concern?
- A . Remote wipe
- B . Anti-maIware
- C . Device encryption
- D . Failed login restrictions
D
Explanation:
A technician suspects the boot disk of a user’s computer contains bad sectors.
Which of the following should the technician verify in the command prompt to address the issue without making any changes?
- A . Run sfc / scannow on the drive as the administrator.
- B . Run clearnmgr on the drive as the administrator
- C . Run chkdsk on the drive as the administrator.
- D . Run dfrgui on the drive as the administrator.
C
Explanation:
The technician should verify bad sectors on the user’s computer by running chkdsk on the drive as the administrator. Chkdsk (check disk) is a command-line utility that detects and repairs disk errors, including bad sectors. It runs a scan of the disk and displays any errors that are found
A SOHO client is having trouble navigating to a corporate website.
Which of the following should a technician do to allow access?
- A . Adjust the content filtering.
- B . Unmap port forwarding.
- C . Disable unused ports.
- D . Reduce the encryption strength
A
Explanation:
Content filtering is a process that manages or screens access to specific emails or webpages based on their content categories1. Content filtering can be used by organizations to control content access through their firewalls and enforce corporate policies around information system management2. A SOHO client may have content filtering enabled on their network and may need to adjust it to allow access to a corporate website that is blocked by default. The client can use a software program, a hardware device, or a subscription service to configure the content filtering settings and whitelist the desired website2.
References:
1: Web content filtering (https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/web-content-filtering?view=o365-worldwide)
2: What is Content Filtering? Definition and Types of Content Filters (https://www.fortinet.com/resources/cyberglossary/content-filtering)
A technician needs to transfer a large number of files over an unreliable connection. The technician should be able to resume the process if the connection is interrupted.
Which of the following tools can be used?
- A . afc
- B . ehkdsk
- C . git clone
- D . zobocopy
D
Explanation:
A customer called the help desk to report that a machine that was recently updated is no longer working. The support technician checks the latest logs to see what updates were deployed, but nothing was deployed in more than three weeks.
Which of the following should the support technician do to BEST resolve the situation?
- A . Offer to wipe and reset the device for the customer.
- B . Advise that the help desk will investigate and follow up at a later date.
- C . Put the customer on hold and escalate the call to a manager.
- D . Use open-ended questions to further diagnose the issue.
D
Explanation:
Open-ended questions are questions that require more than a yes or no answer and encourage the customer to provide more details and information. Using open-ended questions can help the support technician to understand the problem better, identify the root cause, and find a suitable solution.
Some examples of open-ended questions are:
✑ What exactly is not working on your machine?
✑ When did you notice the problem?
✑ How often does the problem occur?
✑ What were you doing when the problem happened?
✑ What have you tried to fix the problem?
Offering to wipe and reset the device for the customer is not a good option, as it may result in data loss and inconvenience for the customer. It should be used as a last resort only if other troubleshooting steps fail. Advising that the help desk will investigate and follow up at a later date is not a good option, as it may leave the customer unsatisfied and frustrated. It should be used only if the problem requires further research or escalation and cannot be resolved on the first call. Putting the customer on hold and escalating the call to a manager is not a good option, as it may waste time and resources. It should be used only if the problem is beyond the support technician’s scope or authority and requires managerial intervention.
A user in a corporate office reports the inability to connect to any network drives. No other users have reported this issue.
Which of the following is the MOST likely reason the user is having this issue?
- A . The user is not connected to the VPN.
- B . The file server is offline.
- C . A low battery is preventing the connection.
- D . The log-in script failed.
A technician is attempting to mitigate micro power outages, which occur frequently within the area of operation. The outages are usually short, with the longest occurrence lasting five minutes.
Which of the following should the technician use to mitigate this issue?
- A . Surge suppressor
- B . Battery backup
- C . CMOS battery
- D . Generator backup
B
Explanation:
A battery backup, also known as an uninterruptible power supply (UPS), is a device that provides backup power during a power outage. When the power goes out, the battery backup provides a short amount of time (usually a few minutes up to an hour, depending on the capacity of the device) to save any work and safely shut down the equipment.
When a user calls in to report an issue, a technician submits a ticket on the user’s behalf.
Which of the following practices should the technician use to make sure the ticket is associated with the correct user?
- A . Have the user provide a callback phone number to be added to the ticket
- B . Assign the ticket to the department’s power user
- C . Register the ticket with a unique user identifier
- D . Provide the user with a unique ticket number that can be referenced on subsequent calls.
C
Explanation:
A technician receives a call from a user who is on vacation. The user provides the necessary credentials and asks the technician to log in to the
users account and read a critical email that the user has been expecting. The technician refuses because this is a violation of the:
- A . acceptable use policy.
- B . regulatory compliance requirements.
- C . non-disclosure agreement
- D . incident response procedures
A
Explanation:
Logging into a user’s account without their explicit permission is a violation of the acceptable use policy, which outlines the rules and regulations by which a user must abide while using a computer system. By logging into the user’s account without their permission, the technician would be violating this policy. Additionally, this action could be seen as a breach of confidentiality, as the technician would have access to information that should remain confidential.
A technician downloaded software from the Internet that required the technician to scroll through a text box and at the end of the text box, click a button labeled Accept.
Which of the following agreements IS MOST likely in use?
- A . DRM
- B . NDA
- C . EULA
- D . MOU
C
Explanation:
The most likely agreement in use here is a EULA (End User License Agreement). This is a legally binding agreement between the user and the software developer, outlining the terms and conditions that the user must agree to in order to use the software. It is important that the user understands and agrees to the EULA before they can proceed with downloading and installing the software. As stated in the CompTIA A+ Core 2 exam objectives, users should be aware of the EULA before downloading any software.
A Windows workstation that was recently updated with approved system patches shut down instead of restarting. Upon reboot, the technician notices an alert stating the workstation has malware in the root OS folder. The technician promptly performs a System Restore and reboots the workstation, but the malware is still detected.
Which of the following BEST describes why the system still has malware?
- A . A system patch disabled the antivirus protection and host firewall.
- B . The system updates did not include the latest anti-malware definitions.
- C . The system restore process was compromised by the malware.
- D . The malware was installed before the system restore point was created.
D
Explanation:
The best explanation for why the system still has malware after performing a System Restore is that the malware was installed before the system restore point was created. A system restore point is a snapshot of the system settings and configuration at a certain point in time. A System Restore is a feature that allows users to restore their system to a previous state in case of problems or errors. However, a System Restore does not affect personal files or folders, and it may not remove malware that was already present on the system before the restore point was created. A system patch disabling the antivirus protection and host firewall may increase the risk of malware infection, but it does not explain why the malware persists after a System Restore. The system updates not including the latest anti-malware definitions may reduce the effectiveness of malware detection and removal, but it does not explain why the malware persists after a System Restore. The system restore process being compromised by the malware may prevent a successful System Restore, but it does not explain why the malware persists after a System Restore. References: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 1.3
A user reports that text on the screen is too small. The user would like to make the text larger and easier to see.
Which of the following is the BEST way for the user to increase the size of text, applications, and other items using the Windows 10 Settings tool?
- A . Open Settings select Devices, select Display, and change the display resolution to a lower resolution option
- B . Open Settings, select System, select Display, and change the display resolution to a lower resolution option.
- C . Open Settings Select System, select Display, and change the Scale and layout setting to a higher percentage.
- D . Open Settings select Personalization, select Display and change the Scale and layout setting to a higher percentage
C
Explanation:
Open Settings, select System, select Display, and change the Scale and layout setting to a higher percentage123
Reference: 4.
How to Increase the Text Size on Your Computer. Retrieved from https://www.laptopmag.com/articles/increase-text-size-computer 5.
How to Change the Size of Text in Windows 10. Retrieved from https://www.howtogeek.com/370055/how-to-change-the-size-of-text-in-windows-10/ 6. Change the size of text in Windows. Retrieved from https://support.microsoft.com/en-us/windows/change-the-size-of-text-in-windows-1d5830c3-eee3-8eaa-836b-abcc37d99b9a
A technician is preparing to remediate a Trojan virus that was found on a workstation.
Which of the following steps should the technician complete BEFORE removing the virus?
- A . Disable System Restore.
- B . Schedule a malware scan.
- C . Educate the end user.
- D . Run Windows Update.
A
Explanation:
Before removing a Trojan virus from a workstation, a technician should disable System Restore. System Restore is a feature that allows users to restore their system to a previous state in case of problems or errors. However, System Restore can also restore infected files or registry entries that were removed by antivirus software or manual actions. By disabling System Restore, a technician can ensure that the Trojan virus is completely removed and does not reappear after a system restore operation. Scheduling a malware scan may help detect and remove some malware but may not be effective against all types of Trojan viruses. Educating the end user may help prevent future infections but does not address the current issue of removing the Trojan virus. Running Windows Update may help patch some security vulnerabilities but does not guarantee that the Trojan virus will be removed. References: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 1.3
A technician is in the process of installing a new hard drive on a server but is called away
to another task. The drive has been unpackaged and left on a desk.
Which of the following should the technician perform before leaving?
- A . Ask coworkers to make sure no one touches the hard drive.
- B . Leave the hard drive on the table; it will be okay while the other task is completed.
- C . Place the hard drive in an antistatic bag and secure the area containing the hard drive.
- D . Connect an electrostatic discharge strap to the drive.
C
Explanation:
The technician should place the hard drive in an antistatic bag and secure the area containing the hard drive before leaving. This will protect the hard drive from electrostatic discharge (ESD), dust, moisture, and physical damage. Asking coworkers to make sure no one touches the hard drive is not a reliable or secure way to prevent damage. Leaving the hard drive on the table exposes it to ESD and other environmental hazards. Connecting an electrostatic discharge strap to the drive is not enough to protect it from dust, moisture, and physical damage.
A desktop specialist needs to prepare a laptop running Windows 10 for a newly hired employee.
Which of the following methods should the technician use to refresh the laptop?
- A . Internet-based upgrade
- B . Repair installation
- C . Clean install
- D . USB repair
- E . In place upgrade
C
Explanation:
The desktop specialist should use a clean install to refresh the laptop. A clean install will remove all data and applications from the laptop and install a fresh copy of Windows 10, ensuring that the laptop is ready for the newly hired employee.
A kiosk, which is running Microsoft Windows 10, relies exclusively on a numeric keypad to allow customers to enter their ticket numbers but no other information. If the kiosk is idle for four hours, the login screen locks.
Which of the following sign-on options would allow any employee the ability to unlock the kiosk?
- A . Requiring employees to enter their usernames and passwords
- B . Setting up facial recognition for each employee
- C . Using a PIN and providing it to employees
- D . Requiring employees to use their fingerprints
C
Explanation:
The best sign-on option that would allow any employee the ability to unlock the kiosk that relies exclusively on a numeric keypad is to use a PIN and provide it to employees. A PIN is a Personal Identification Number that is a numeric code that can be used as part of authentication or access control. A PIN can be entered using only a numeric keypad and can be easily shared with employees who need to unlock the kiosk. Requiring employees to enter their usernames and passwords may not be feasible or convenient if the kiosk only has a numeric keypad and no other input devices. Setting up facial recognition for each employee may not be possible or secure if the kiosk does not have a camera or biometric sensor. Requiring employees to use their fingerprints may not be possible or secure if the kiosk does not have a fingerprint scanner or biometric sensor. References: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 3.3
While browsing a website, a staff member received a message that the website could not be trusted. Shortly afterward, several other colleagues reported the same issue across numerous other websites. Remote users who were not connected to corporate resources did not have any issues.
Which of the following is MOST likely the cause of this issue?
- A . A bad antivirus signature update was installed.
- B . A router was misconfigured and was blocking traffic.
- C . An upstream internet service provider was flapping.
- D . The time or date was not in sync with the website.
D
Explanation:
A user is unable to log in to the network. The network uses 802.1X with EAP-TLS to authenticate on the wired network. The user has been on an extended leave and has not logged in to the computer in several months.
Which of the following is causing the login issue?
- A . Expired certificate
- B . OS update failure
- C . Service not started
- D . Application crash
- E . Profile rebuild needed
A
Explanation:
EAP-TLS is a method of authentication that uses certificates to establish a secure tunnel between the client and the server3. The certificates have a validity period and must be renewed before they expire1. If the user has been on an extended leave and has not logged in to the computer in several months, it is possible that the certificate on the client or the server has expired and needs to be renewed2. The other options are not directly related to EAP-TLS authentication or 802.1X network access.
A technician installed a known-good, compatible motherboard on a new laptop. However, the motherboard is not working on the laptop.
Which of the following should the technician MOST likely have done to prevent damage?
- A . Removed all jewelry
- B . Completed an inventory of tools before use
- C . Practiced electrical fire safety
- D . Connected a proper ESD strap
D
Explanation:
The technician should have connected a proper ESD strap to prevent damage to the motherboard. ESD (electrostatic discharge) can cause damage to electronic components, and an ESD strap helps to prevent this by grounding the technician and preventing the buildup of static electricity. Removing all jewelry is also a good practice, but it is not the most likely solution to this problem.
During a recent flight an executive unexpectedly received several dog and cat pictures while trying to watch a movie via in-flight Wi-Fi on an iPhone. The executive has no records of any contacts sending pictures like these and has not seen these pictures before.
To BEST resolve this issue, the executive should:
- A . set AirDrop so that transfers are only accepted from known contacts
- B . completely disable all wireless systems during the flight
- C . discontinue using iMessage and only use secure communication applications
- D . only allow messages and calls from saved contacts
A
Explanation:
To best resolve this issue, the executive should set AirDrop so that transfers are only accepted from known contacts (option A). AirDrop is a feature on iOS devices that allows users to share files, photos, and other data between Apple devices. By setting AirDrop so that it only accepts transfers from known contacts, the executive can ensure that unwanted files and photos are not sent to their device. Additionally, the executive should ensure that the AirDrop setting is only enabled when it is necessary, as this will protect their device from any unwanted files and photos.
A new employee was hired recently.
Which of the following documents will the new employee need to sign before being granted login access to the network?
- A . MSDS
- B . EULA
- C . UAC
- D . AUP
D
Explanation:
A new employee will need to sign an AUP before being granted login access to the network. An AUP is an Acceptable Use Policy that defines the rules and guidelines for using network resources and services in an organization. An AUP typically covers topics such as security, privacy, ethics, compliance and liability issues related to network usage. An AUP helps protect the organization and its users from legal, regulatory and reputational risks associated with network activities. An MSDS is a Material Safety Data Sheet that provides information about hazardous substances and how to handle them safely. An MSDS is not related to network access or usage. A EULA is an End User License Agreement that specifies the terms and conditions for using a software product or service. A EULA is usually provided by software vendors or developers and does not apply to network access or usage in general. A UAC is a User Account Control that is a security feature that prompts users for permission or confirmation before performing certain actions that require elevated privileges or affect system settings. A UAC is not a document that needs to be signed by users but a mechanism that helps prevent unauthorized changes or malware infections on a system. References: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 5.1
A call center technician receives a call from a user asking how to update Windows.
Which of the following describes what the technician should do?
- A . Have the user consider using an iPad if the user is unable to complete updates
- B . Have the user text the user’s password to the technician.
- C . Ask the user to click in the Search field, type Check for Updates, and then press the Enter key
- D . Advise the user to wait for an upcoming, automatic patch
C
Explanation:
The technician should guide the user to update Windows through the built-in "Check for Updates" feature. This can be done by having the user click in the Search field, type "Check for Updates", and then press the Enter key. This will bring up the Windows Update function, which will search for any available updates and give the user the option to install them.
A user has been unable to receive emails or browse the internet from a smartphone while traveling. However, text messages and phone calls are working without issue.
Which of the following should a support technician check FIRST?
- A . User account status
- B . Mobile OS version
- C . Data plan coverage
- D . Network traffic outages
C
Explanation:
The first thing that a support technician should check to resolve the issue of not being able to receive emails or browse the internet from a smartphone while traveling is the data plan coverage. The data plan coverage determines how much data and where the user can use on the smartphone’s cellular network. The data plan coverage may vary depending on the user’s location, carrier and subscription. The data plan coverage may not include or support certain areas or countries that the user is traveling to, or may charge extra fees or limit the speed or amount of data that the user can use. The data plan coverage does not affect text messages and phone calls, which use different network services and protocols. User account status is not likely to cause the issue of not being able to receive emails or browse the internet from a smartphone while traveling, unless the user account has been suspended or terminated by the carrier or the email provider. Mobile OS version is not likely to cause the issue of not being able to receive emails or browse the internet from a smartphone while traveling, unless the mobile OS has a major bug or compatibility problem with the network or the email app. Network traffic outages may cause the issue of not being able to receive emails or browse the internet from a smartphone while traveling, but they are less likely and less common than data plan coverage issues, and they should also affect text messages and phone calls. References: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 1.5
A technician wants to enable BitLocker on a Windows 10 laptop and is unable to find the BitLocker Drive Encryption menu item in Control Panel.
Which of the following explains why the technician unable to find this menu item?
- A . The hardware does not meet BitLocker’s minimum system requirements.
- B . BitLocker was renamed for Windows 10.
- C . BitLocker is not included on Windows 10 Home.
- D . BitLocker was disabled in the registry of the laptop
C
Explanation:
BitLocker is only available on Windows 10 Pro, Enterprise, and Education editions1. Therefore, the technician is unable to find the BitLocker Drive Encryption menu item in Control Panel because it is not included in the Windows 10 Home edition1.
A police officer often leaves a workstation for several minutes at a time.
Which of the following is the BEST way the officer can secure the workstation quickly when walking away?
- A . Use a key combination to lock the computer when leaving.
- B . Ensure no unauthorized personnel are in the area.
- C . Configure a screensaver to lock the computer automatically after approximately 30 minutes of inactivity.
- D . Turn off the monitor to prevent unauthorized visibility of information.
A
Explanation:
The BEST way to secure the workstation quickly when walking away is to use a key combination to lock the computer when leaving1
A macOS user reports seeing a spinning round cursor on a program that appears to be frozen.
Which of the following methods does the technician use to force the program to close in macOS?
- A . The technician presses the Ctrl+Alt+Del keys to open the Force Quit menu, selects the frozen application in the list, and clicks Force Quit.
- B . The technician clicks on the frozen application and presses and holds the Esc key on the keyboard for 10 seconds. Which causes the application to force quit.
- C . The technician opens Finder, navigates to the Applications folder, locates the application that is frozen in the list, right-clicks on the application, and selects the Force Quit option.
- D . The technician opens the Apple icon menu, selects Force Quit, selects the frozen application in the list, and clicks Force Quit.
D
Explanation:
The technician opens the Apple icon menu, selects Force Quit, selects the frozen application in the list, and clicks Force Quit. This is the most common method of force quitting a program in macOS. This can be done by clicking on the Apple icon in the top left of the screen, selecting Force Quit, selecting the frozen application in the list, and then clicking Force Quit. This will force the application to quit and the spinning round cursor will disappear.
A user is unable to log in to the domain with a desktop PC, but a laptop PC is working properly on the same network. A technician logs in lo the desktop PC with a local account but is unable to browse to the secure intranet site to get troubleshooting tools.
Which of the following is the MOST likely cause of the issue?
- A . Time drift
- B . Dual in-line memory module failure
- C . Application crash
- D . Filesystem errors
A
Explanation:
The most likely cause of the issue is a “time drift”. Time drift occurs when the clock on a computer is not synchronized with the clock on the domain controller. This can cause authentication problems when a user tries to log in to the domain. The fact that the technician is unable to browse to the secure intranet site to get troubleshooting tools suggests that there may be a problem with the network connection or the firewall settings on the desktop PC12
DRAG DROP
A customer recently experienced a power outage at a SOHO. The customer does not think the components are connected properly. A print job continued running for several minutes after the power failed, but the customer was not able to interact with the computer. Once the UPS stopped beeping, all functioning devices also turned off.
In case of a future power failure, the customer wants to have the most time available to save cloud documents and shut down the computer without losing any data.
Explanation:
UPS > Surge protector = Computer, wifi router, cable modem
Surge protector = wallOutlet, printer and scanner
A user’s mobile phone has become sluggish A systems administrator discovered several malicious applications on the device and reset the phone. The administrator installed MDM software.
Which of the following should the administrator do to help secure the device against this threat in the future? (Select TWO).
- A . Prevent a device root
- B . Disable biometric authentication
- C . Require a PIN on the unlock screen
- D . Enable developer mode
- E . Block a third-party application installation
- F . Prevent GPS spoofing
A,E
Explanation:
A help desk technician is troubleshooting a workstation in a SOHO environment that is running above normal system baselines. The technician discovers an unknown executable with a random string name running on the system. The technician terminates the process, and the system returns to normal operation. The technician thinks the issue was an infected file, but the antivirus is not detecting a threat. The technician is concerned other machines may be infected with this unknown virus.
Which of the following is the MOST effective way to check other machines on the network for this unknown threat?
- A . Run a startup script that removes files by name.
- B . Provide a sample to the antivirus vendor.
- C . Manually check each machine.
- D . Monitor outbound network traffic.
B
Explanation:
A user is trying to use a third-party USB adapter but is experiencing connection issues.
Which of the following tools should the technician use to resolve this issue?
- A . taskschd.msc
- B . eventvwr.msc
- C . de vmgmt. msc
- D . diskmgmt.msc
C
Explanation:
The tool that the technician should use to resolve the connection issues with the third-party USB adapter is devmgmt.msc. Devmgmt.msc is a command that opens the Device Manager, which is a utility that allows users to view and manage the hardware devices and drivers installed on a computer. The technician can use the Device Manager to check the status, properties and compatibility of the USB adapter and its driver, and perform actions such as updating, uninstalling or reinstalling the driver, enabling or disabling the device, or scanning for hardware changes. Taskschd.msc is a command that opens the Task Scheduler, which is a utility that allows users to create and manage tasks that run automatically at specified times or events. The Task Scheduler is not relevant or useful for resolving connection issues with the USB adapter. Eventvwr.msc is a command that opens the Event Viewer, which is a utility that allows users to view and monitor the system logs and events. The Event Viewer may provide some information or clues about the connection issues with the USB adapter, but it does not allow users to manage or troubleshoot the device or its driver directly. Diskmgmt.msc is a command that opens the Disk Management, which is a utility that allows users to view and manage the disk drives and partitions on a computer. The Disk Management is not relevant or useful for resolving connection issues with the USB adapter. References: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 1.6
A user has a license for an application that is in use on a personal home laptop. The user approaches a systems administrator about using the same license on multiple computers on the corporate network.
Which of the following BEST describes what the systems administrator should tell the user?
- A . Use the application only on the home laptop because it contains the initial license.
- B . Use the application at home and contact the vendor regarding a corporate license.
- C . Use the application on any computer since the user has a license.
- D . Use the application only on corporate computers.
B
Explanation:
Use the application at home and contact the vendor regarding a corporate license. The user should use the application only on the home laptop because it contains the initial license. The user should contact the vendor regarding a corporate license if they want to use the application on multiple computers on the corporate network1
A technician has an external SSD. The technician needs to read and write to an external SSD on both Macs and Windows PCs.
Which of the following filesystems is supported by both OS types?
- A . NTFS
- B . APFS
- C . ext4
- D . exFAT
D
Explanation:
The filesystem that is supported by both Macs and Windows PCs is D.
exFAT. exFAT is a file system that is designed to be used on flash drives like USB sticks and SD cards. It is supported by both Macs and Windows PCs, and it can handle large files and volumes
https://www.diskpart.com/articles/file-system-for-mac-and-windows-0310.html
A user tries to access commonly used web pages but is redirected to unexpected websites. Clearing the web browser cache does not resolve the issue.
Which of the following should a technician investigate NEXT to resolve the issue?
- A . Enable firewall ACLs.
- B . Examine the localhost file entries.
- C . Verify the routing tables.
- D . Update the antivirus definitions.
B
Explanation:
A possible cause of the user being redirected to unexpected websites is that the localhost file entries have been modified by malware or hackers to point to malicious or unwanted websites. The localhost file is a text file that maps hostnames to IP addresses and can override DNS settings. By examining the localhost file entries, a technician can identify and remove any suspicious or unauthorized entries that may cause the redirection issue. Enabling firewall ACLs may not resolve the issue if the firewall rules do not block the malicious or unwanted websites. Verifying the routing tables may not resolve the issue if the routing configuration is correct and does not affect the web traffic. Updating the antivirus definitions may help prevent future infections but may not remove the existing malware or changes to the localhost file. References: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 1.3
A network technician installed a SOHO router for a home office user. The user has read reports about home routers being targeted by malicious actors and then used in DDoS attacks.
Which of the following can the technician MOST likely do to defend against this threat?
- A . Add network content filtering.
- B . Disable the SSID broadcast.
- C . Configure port forwarding.
- D . Change the default credentials.
D
Explanation:
One of the most effective ways to defend against malicious actors targeting home routers for DDoS attacks is to change the default credentials of the router. The default credentials are often well-known or easily guessed by attackers, who can then access and compromise the router settings and firmware. By changing the default credentials to strong and unique ones, a technician can prevent unauthorized access and configuration changes to the router. Adding network content filtering may help block some malicious or unwanted websites but may not prevent attackers from exploiting router vulnerabilities or backdoors.
Disabling the SSID broadcast may help reduce the visibility of the wireless network but may not prevent attackers from scanning or detecting it. Configuring port forwarding may help direct incoming traffic to specific devices or services but may not prevent attackers from sending malicious packets or requests to the router. References: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 3.3
An IT security team is implementing a new Group Policy that will return a computer to the login after three minutes.
Which of the following BEST describes the change in policy?
- A . Login times
- B . Screen lock
- C . User permission
- D . Login lockout attempts
B
Explanation:
Screen lock is a feature that returns a computer to the login screen after a period of inactivity, requiring the user to enter their credentials to resume their session. Screen lock can be configured using Group Policy settings, such as Screen saver timeout and Interactive logon: Machine inactivity limit. Screen lock can help prevent unauthorized access to a computer when the user is away from their desk. Login times are not a feature that returns a computer to the login screen, but a measure of how long it takes for a user to log in to a system. User permission is not a feature that returns a computer to the login screen, but a set of rights and privileges that determine what a user can do on a system. Login lockout attempts are not a feature that returns a computer to the login screen, but a security policy that locks out a user account after a number of failed login attempts. https://woshub.com/windows-lock-screen-after-idle-via-gpo/
Which of the following could be used to implement secure physical access to a data center?
- A . Geofence
- B . Alarm system
- C . Badge reader
- D . Motion sensor
C
Explanation:
Badge readers are used to implement secure physical access to a data center. They are used to read the identification information on an employee’s badge and grant access to the data center if the employee is authorized2.
This system requires individuals to have an access badge that contains their identification information or a unique code that can be scanned by a reader. After the badge is scanned, the system compares the information on the badge with the authorized personnel database to authenticate if the individual has the required clearance to enter that area. The other options listed, such as a geofence, alarm system, or motion sensor are security measures that may be used in conjunction with badge readers, but do not provide identification and authentication features.
Which of the following change management documents includes how to uninstall a patch?
- A . Purpose of change
- B . Rollback plan
- C . Scope of change
- D . Risk analysis
B
Explanation:
The change management document that includes how to uninstall a patch is called the “rollback plan”. The rollback plan is a document that outlines the steps that should be taken to undo a change that has been made to a system. In the case of a patch, the rollback plan would include instructions on how to uninstall the patch if it causes problems or conflicts with other software12
A technician is installing new network equipment in a SOHO and wants to ensure the equipment is secured against external threats on the Internet.
Which of the following actions should the technician do FIRST?
- A . Lock all devices in a closet.
- B . Ensure all devices are from the same manufacturer.
- C . Change the default administrative password.
- D . Install the latest operating system and patches
C
Explanation:
The technician should change the default administrative password FIRST to ensure the network equipment is secured against external threats on the Internet. Changing the default administrative password is a basic security measure that can help prevent unauthorized access to the network equipment. Locking all devices in a closet is a physical security measure that can help prevent theft or damage to the devices, but it does not address external threats on the Internet. Ensuring all devices are from the same manufacturer is not a security measure and does not address external threats on the Internet. Installing the latest operating system and patches is important for maintaining the security of the network equipment, but it is not the first action the technician should take1
A technician needs to interconnect two offices to the main branch while complying with good practices and security standards.
Which of the following should the technician implement?
- A . MSRA
- B . VNC
- C . VPN
- D . SSH
C
Explanation:
A technician needs to interconnect two offices to the main branch while complying with good practices and security standards. The technician should implement VPN
A user updates a mobile device’s OS. A frequently used application becomes consistently unresponsive immediately after the device is launched.
Which of the following troubleshooting steps should the user perform FIRST?
- A . Delete the application’s cache.
- B . Check for application updates.
- C . Roll back the OS update.
- D . Uninstall and reinstall the application.
B
Explanation:
Sometimes, an OS update can cause compatibility issues with some applications that are not optimized for the new version of the OS. To fix this, the user should check if there are any updates available for the application that can resolve the issue.
The user can check for application updates by following these steps:
✑ On an Android device, open the Google Play Store app and tap on the menu icon in the top left corner. Then tap on My apps & games and look for any updates available for the application. If there is an update, tap on Update to install it.
✑ On an iOS device, open the App Store app and tap on the Updates tab at the bottom. Then look for any updates available for the application. If there is an update, tap on Update to install it.
A small business owner wants to install newly purchased software on all networked PCs. The network is not configured as a domain, and the owner wants to use the easiest method possible.
Which of the following is the MOST deficient way lor the owner to install the application?
- A . Use a network share to share the installation files.
- B . Save software to an external hard drive to install.
- C . Create an imaging USB for each PC.
- D . Install the software from the vendor’s website
A
Explanation:
A user reports a workstation has been performing strangely after a suspicious email was opened on it earlier in the week.
Which of the following should the technician perform FIRST?
- A . Escalate the ticket to Tier 2.
- B . Run a virus scan.
- C . Utilize a Windows restore point.
- D . Reimage the computer.
B
Explanation:
https://partners.comptia.org/docs/default-source/resources/comptia-a-220-1102-exam-objectives-(3-0)
When a user reports that their workstation is behaving strangely after opening a suspicious email, the first step a technician should take is to run a virus scan on the computer. This is because opening a suspicious email is a common way for viruses and malware to infect a computer. Running a virus scan can help identify and remove any infections that may be causing the computer to behave strangely.
A user wants to set up speech recognition on a PC In which of the following Windows Settings tools can the user enable this option?
- A . Language
- B . System
- C . Personalization
- D . Ease of Access
D
Explanation:
The user can enable speech recognition on a PC in the Ease of Access settings tool. To set up Speech Recognition on a Windows PC, the user should open Control Panel, click on Ease of Access, click on Speech Recognition, and click the Start Speech Recognition link. Language settings can be used to change the language of the speech recognition feature, but they will not enable the feature. System settings can be used to configure the hardware and software of the PC, but they will not enable the speech recognition feature. Personalization settings can be used to customize the appearance and behavior of the PC, but they will not enable the speech recognition feature1
Open up ease of access, click on speech, then there is an on and off button for speech recognition.
A user updates a mobile device’s OS. A frequently used application becomes consistently unresponsive immediately after the device is launched.
Which of the following troubleshooting steps should the user perform FIRST?
- A . Delete the application’s cache.
- B . Check for application updates.
- C . Roll back the OS update.
- D . Uninstall and reinstall the application.
B
Explanation:
Checking for application updates is the first troubleshooting step that the user should perform, because the application may not be compatible with the new OS version and may need an update to fix the issue. Deleting the application’s cache, rolling back the OS update, or uninstalling and reinstalling the application are possible solutions, but they are more time-consuming and disruptive than checking for updates.
References:
https://www.comptia.org/training/resources/exam-objectives/comptia-a-core-2-exam-objectives: https://www.lifewire.com/how-to-update-apps-on-android-4173855
Someone who is fraudulently claiming to be from a reputable bank calls a company employee.
Which of the following describes this incident?
- A . Pretexting
- B . Spoofing
- C . Vishing
- D . Scareware
C
Explanation:
Vishing is a type of social engineering attack where a fraudulent caller impersonates a legitimate entity, such as a bank or financial institution, in order to gain access to sensitive information. The caller will typically use a variety of techniques, such as trying to scare the target or providing false information, in order to get the target to provide the information they are after. Vishing is often used to gain access to usernames, passwords, bank account information, and other sensitive data.
Upon downloading a new ISO, an administrator is presented with the following string:
59d15a16ce90cBcc97fa7c211b767aB
Which of the following BEST describes the purpose of this string?
- A . XSS verification
- B . AES-256 verification
- C . Hash verification
- D . Digital signature verification
C
Explanation:
Hash verification is a process that verifies the integrity of a file by comparing the hash value of the downloaded file to the hash value provided by the source1
All the desktop icons on a user’s newly issued PC are very large. The user reports that the PC was working fine until a recent software patch was deployed.
Which of the following would BEST resolve the issue?
- A . Rolling back video card drivers
- B . Restoring the PC to factory settings
- C . Repairing the Windows profile
- D . Reinstalling the Windows OS
A
Explanation:
Rolling back video card drivers is the best way to resolve the issue of large desktop icons on a user’s newly issued PC. This means restoring the previous version of the drivers that were working fine before the software patch was deployed. The software patch may have caused compatibility issues or corrupted the drivers, resulting in display problems
A technician is troubleshooting application crashes on a Windows workstation.
Each time the workstation user tries to open a website in a browser, the following message is displayed:
crypt32.d11 is missing not found
Which of the following should the technician attempt FIRST?
- A . Rebuild Windows profiles.
- B . Reimage the workstation
- C . Roll back updates
- D . Perform a system file check
D
Explanation:
If this file is missing or corrupted, it can cause application crashes or errors when trying to open websites in a browser. To fix this, the technician can perform a system file check, which is a utility that scans and repairs corrupted or missing system files1.
To perform a system file check, the technician can follow these steps:
✑ Open the Command Prompt as an administrator. To do this, type cmd in the search box on the taskbar, right-click on Command Prompt, and select Run as administrator.
✑ In the Command Prompt window, type sfc /scannow and hit Enter. This will start the scanning and repairing process, which may take some time.
✑ Wait for the process to complete. If any problems are found and fixed, you will see a message saying Windows Resource Protection found corrupt files and successfully repaired them. If no problems are found, you will see a message saying Windows Resource Protection did not find any integrity violations.
✑ Restart your computer and check if the issue is resolved.
Which of the following is a consequence of end-of-lite operating systems?
- A . Operating systems void the hardware warranty.
- B . Operating systems cease to function.
- C . Operating systems no longer receive updates.
- D . Operating systems are unable to migrate data to the new operating system.
C
Explanation:
End-of-life operating systems are those which have reached the end of their life cycle and are no longer supported by the software developer. This means that the operating system will no longer receive updates, security patches, or other new features. This can leave users vulnerable to security threats, as the system will no longer be protected against the latest threats. Additionally, this can make it difficult to migrate data to a newer operating system, as the old system is no longer supported.