Citrix 1Y0-440 Architecting a Citrix Networking Solution Online Training
Citrix 1Y0-440 Online Training
The questions for 1Y0-440 were last updated at Nov 20,2025.
- Exam Code: 1Y0-440
- Exam Name: Architecting a Citrix Networking Solution
- Certification Provider: Citrix
- Latest update: Nov 20,2025
Scenario: A Citrix Architect has deployed load balancing for SharePoint 2010 on a Citrix ADC instance.
While editing the document, the architect observed the error displayed below:
Sorry, we couldn’t open ‘https://sharepointcs.emea.in/Shared Documents/Citrix Enhancement Request Form.doc’
After troubleshooting, the architect discovers the issue. When a user opens a document, it opens in the browser, but while editing the document, thd session is transferred from the browser to the Word application During this time, the cookies should be transferred from the browser to the Word application.
Which two configurations should the architect modify to ensure that the cookies are shared between the browser and non-browser applications? (Choose two.)
- A . Enable Persistent Cookie
- B . Disable Persistent Cookie
- C . Set HTTPOnly Cookie to NO
- D . Set the NSC_AAAC cookie with HTTPOnly Flag
- E . Set lb vserver -persistenceType COOKIEINSERT
- F . Set HTTPOnly Cookie to Yes
Scenario: A Citrix Architect has set up NetScaler MPX devices in high availability mode with version 12.0. 53.13 nc. These are placed behind a Cisco ASA 5505 Firewall is configured to block traffic using access control lists. The network address translation (NAT) is also performed on the firewall.
The following requirements were captured by the architect during the discussion held as part of the NetScaler security implementation project with the customer’s security team:
The NetScaler device:
✑ Should monitor the rate of traffic either on a specific virtual entity or on the device. It should be able to mitigate the attacks from a hostile client sending a flood of requests. The NetScaler device should be able to stop the HTTP, TCP, and DNS based requests.
✑ Needs to protect backend servers from overloading.
✑ Needs to queue all the incoming requests on the virtual server level instead of the service level.
✑ Should provide access to resources on the basis of priority.
✑ Should provide protection against well-known Windows exploits, virus-infected personal computers, centrally managed automated botnets, compromised webservers, known spammers/hackers, and phishing proxies.
✑ Should provide flexibility to enforce the desired level of security check inspections for the requests originating from a specific geolocation database.
✑ Should block the traffic based on a pre-determined header length, URL length, and cookie length. The device should ensure that characters such as a single straight quote (*); backslash(), and semicolon (;) are either blocked, transformed, or dropped while being sent to the backend server.
Which two security features should the architect configure to meet these requirements? (Choose two.)
- A . Pattern sets
- B . Rate limiting
- C . HTTP DDOS
- D . Data sets
- E . APPQOE
Scenario: A Citrix Architect needs to design a hybrid Citrix Virtual App and Citrix Virtual Desktop environment which will include as well as resource locations in an on-premises datacenter and Microsoft Azure.
Organizational details and requirements are as follows:
✑ Active Citrix Virtual App and Citrix Virtual Desktop Service subscription
✑ No existing Citrix deployment
✑ Minimization of additional costs
✑ All users should use same access point, regardless of network location
✑ No multi-factor authentication is required
Click the Exhibit button to view the conceptual environment architecture.
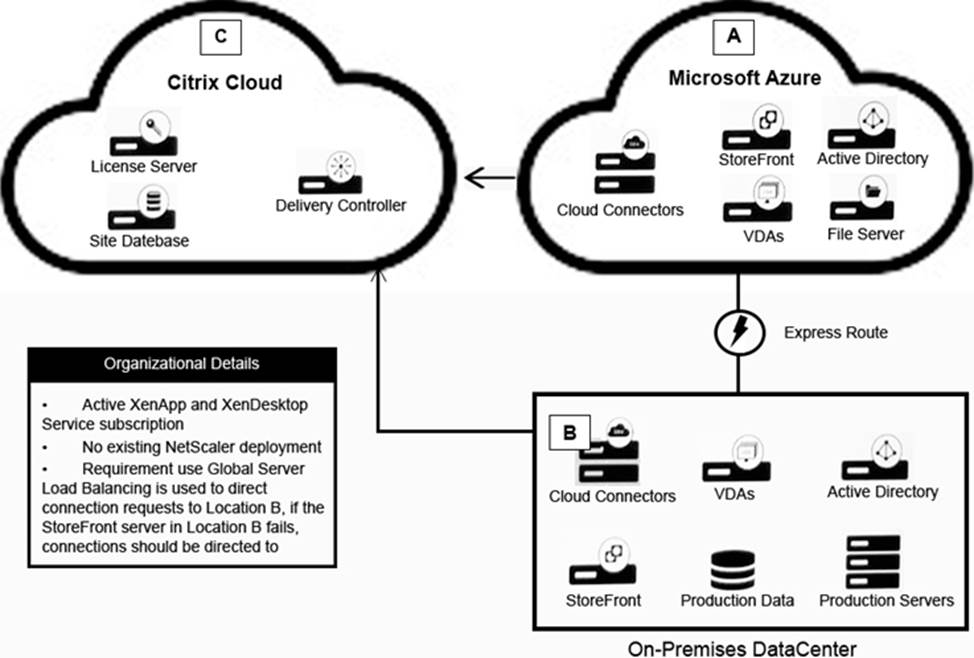
The architect should use___________ in Location A, and should use _______________ in Location B. (Choose the correct option to complete the sentence.)
- A . No Citrix ADC products; Citrix ICA Proxy (cloud-licensed)
- B . Citrix Gateway as a Service; Citrix ICA Proxy (cloud-licensed)
- C . Citrix Gateway as a Service; no Citrix ADC products
- D . No Citrix ADC products; Citrix Gateway appliance
- E . Citrix gateway as a Service; Citrix ADC (BYO)
- F . No Citrix ADC products; Citrix ADC (BYO)
Scenario: A Citrix Architect has implemented two high availability pairs of MPX 5500 and MPX 11500 devices respectively with 12.0.53.13 nc version. The NetScaler devices are set up to handle NetScaler Gateway, Load Balancing, Application Firewall, and Content Switching. The Workspacelab infrastructure is set up to be monitored with NMAS version 12.0.53.13 nc by the Workspacelab administrators. The Workspacelab team wants to implement one more pair of NetScaler MPX 7500 devices with version 12.0.53.13 nc.
The Citrix consulting team has assigned the task to implement these NetScaler devices in the infrastructure and set them up to be monitored and managed by NMAS.
The following are the requirements that were discussed during the project initiation call:
✑ NMAS should be configured to get the infrastructure information under sections such as HDX Insight, WEB Insight, and Security Insight.
✑ Configuration on the new MPX devices should be identical to MPX 11500 devices.
✑ Configuration changes after the deployment and initial setup should be optimized
using NMAS.
✑ NMAS should be utilized to configure templates that can be utilized by the Workspacelab team in future deployment.
✑ As per the requirement from the Workspacelab team, NMAS should be store the audited data for only 15 days.
Which process should the architect utilize to ensure that the deployment of MPX 11500 devices are optimized and that it is correct, before deploying the devices in production?
- A . Under Stylebooks; Inbuilt and composite stylebook templates should be utilized prior to deployment.
- B . Under Stylebooks; Public and composite stylebook templates should be utilized prior to deployment.
- C . Under Configuration Management; Configuration Audit and Advice should be used prior to deployment.
- D . Under Configuration jobs; Configuration Audit and Advice should be used prior to deployment.
Scenario: A Citrix Architect has deployed two MPX devices. 12.0.53.13 nc and MPX 11500 models, in a high availability (HA) pair for the Workspace labs team. The deployment method is two-arm and the devices are installed behind a CISCO ASA 5585 Firewall. The architect enabled the following features on the Citrix ADC devices. Content Switching. SSL Offloading, Load Balancing, Citrix Gateway. Application Firewall in hybrid security and Appflow. All are enabled to send monitoring information to Citrix Application Delivery Management 12.0.53.13 nc build. The architect is preparing to configure load balancing for Microsoft Exchange 2016 server.
The following requirements were discussed during the implementation:
✑ All traffic needs to be segregated based on applications, and the fewest number of IP addresses should be utilized during the configuration.
✑ All traffic should be secured and any traffic coming Into FITTP should be redirected to HTTPS.
✑ Single Sign-on should be created for Microsoft Outlook web access (OWA).
✑ Citrix ADC should recognize Uniform Resource Identifier (URI) and close the session to Citrix ADC when users hit the Logoff button In Microsoft Outlook web access.
✑ Users should be able to authenticate using either user principal name (UPN) or sAMAccountName.
✑ The Layer 7 monitor should be configured to monitor the Microsoft Outlook web access servers and the monitor probes must be sent on SSL.
Which monitor will meet these requirements?
- A . add lb monitor mon.rpc HTTP-ECV -send "GET /rpc/healthcheck.htm" recv 200 -LRTM DISABLED -secure YES
- B . add lb monitor mon.rpc HTTP -send "GET /rpc/healthcheck.htm" recv 200 -LRTM DISABLED -secure YES
- C . add lb monitor mon.rpc HTTP-ECV -send "GET /owa/healthcheck.htm" recv 200 -LRTM DISABLED
- D . add lb monitor mon.rpc HTTP-ECV -send "GET /owa/healthcheck.htm" recv 200 -LRTM ENABLED
- E . add lb monitor mon.rpc HTTP-ECV -send "GET /rpc/healthcheck.htm" recv 200 -LRTM ENABLED
Scenario: A Citrix Architect and a team of Workspacelab members have met for a design discussion about the NetScaler Design Project.
They captured the following requirements:
✑ Two pairs of NetScaler MPX appliances will be deployed in the DMZ network and the internal network.
✑ High availability will be accessible between the pair of NetScaler MPX appliances in the DMZ network.
✑ Multi-factor authentication must be configured for the NetScaler Gateway virtual server.
✑ The NetScaler Gateway virtual server is integrated with XenApp/XenDesktop environment.
✑ Load balancing must be deployed for the users from the workspacelab.com and vendorlab.com domains.
✑ The logon page must show the workspacelab logo.
✑ Certificate verification must be performed to identify and extract the username.
✑ The client certificate must have UserPrincipalName as a subject.
✑ All the managed workstations for the workspace users must have a client identifications certificate installed on it.
✑ The workspacelab users connecting from a managed workstation with a client certificate on it should be authenticated using LDAP.
✑ The workspacelab users connecting from a workstation without a client certificate should be authenticated using LDAP and RADIUS.
✑ The vendorlab users should be authenticated using Active Directory Federation Service.
✑ The user credentials must NOT be shared between workspacelab and vendorlab.
✑ Single Sign-on must be performed between StoreFront and NetScaler Gateway.
✑ A domain drop down list must be provided if the user connects to the NetScaler
Gateway virtual server externally.
✑ The domain of the user connecting externally must be identified using the domain selected from the domain drop down list.
On performing the deployment, the architect observes that users are always prompted with two-factor authentication when trying to assess externally from an unmanaged workstation.
Click the exhibit button to view the configuration.
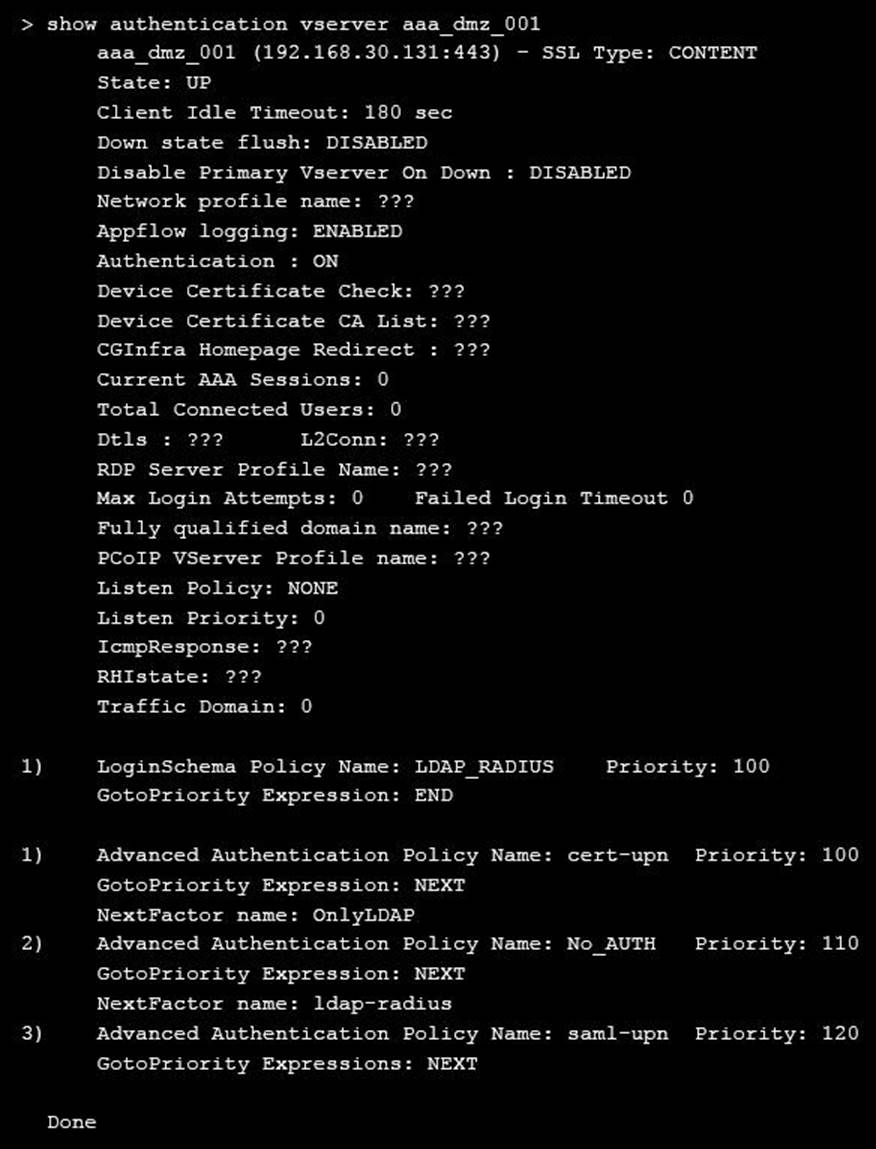
What should the architect do to correct this configuration?
- A . Unbind LoginSchema Policy LDAP_RADIUS from the virtual server.
- B . Bind the Portal theme as Domaindropdown.
- C . Bind the LoginSchema Policy Domaindropdown to priority 90.
- D . Bind the Default LoginSchema Policy as Domaindropdown.
Scenario: A Citrix Architect needs to assess a NetScaler Gateway deployment that was recently completed by a customer and is currently in pre-production testing. The NetScaler Gateway needs to use ICA proxy to provide access to a XenApp and XenDesktop environment. During the assessment, the customer informs the architect that users are NOT able to launch published resources using the Gateway virtual server.
Click the Exhibit button to view the troubleshooting details collected by the customer.
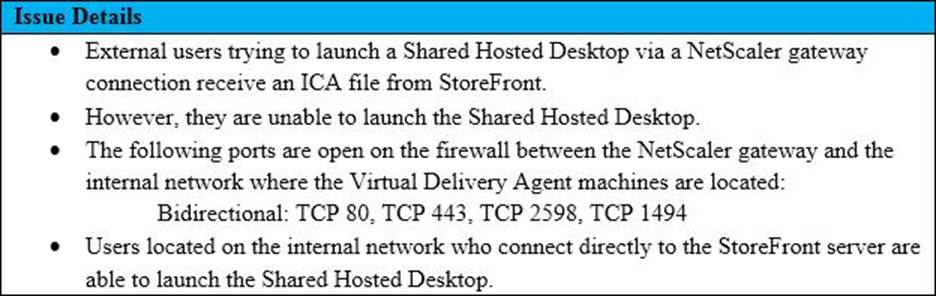
What is the cause of this issue?
- A . The required ports have NOT been opened on the firewall between the NetScaler gateway and the Virtual Delivery Agent (VDA) machines.
- B . The StoreFront URL configured in the NetScaler gateway session profile is incorrect.
- C . The Citrix License Server is NOT reachable.
- D . The Secure Ticket Authority (STA) servers are load balanced on the NetScaler.
Scenario: A Citrix Architect needs to design a NetScaler deployment in Microsoft Azure. An Active-Passive NetScaler VPX pair will provide load balancing for three distinct web applications.
The architect has identified the following requirements:
✑ Minimize deployment costs where possible.
✑ Provide dedicated bandwidth for each web application.
✑ Provide a different public IP address for each web application.
For this deployment, the architect should configure each NetScaler VPX machine to have ______ network interface(s) and configure IP address by using ________. (Choose the correct option to complete the sentence).
- A . 4; Port Address Translation
- B . 1; Network Address Translation
- C . 1; Port Address Translation
- D . 2; Network Address Translation
- E . 4; Network Address Translation
- F . 2; Port Address Translation
Which NetScaler Management and Analytics System (NMAS) utility can a Citrix Architect utilize to verify the configuration template created by the NMAS StyleBook, before actually executing it on the NetScaler?
- A . Dry Run
- B . configpack
- C . NITRO API
- D . configcheck
What can help a Citrix Architect prepare to discuss time scales and resource requirements?
- A . Creating a high-level project plan.
- B . Meeting with each member of the project team to assign tasks.
- C . Designing the new environment.
- D . Setting expectations with the project’s key stakeholders.
- E . Identifying challenges associated with the project.
Latest 1Y0-440 Dumps Valid Version with 63 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

