Citrix 1Y0-440 Architecting a Citrix Networking Solution Online Training
Citrix 1Y0-440 Online Training
The questions for 1Y0-440 were last updated at Aug 13,2025.
- Exam Code: 1Y0-440
- Exam Name: Architecting a Citrix Networking Solution
- Certification Provider: Citrix
- Latest update: Aug 13,2025
Scenario: The Workspacelab team has implemented Citrix ADC high availability pair and Citrix ADC Management and Analytics System (Citrix Application Delivery Management). The Citrix Application Delivery Management was configured by a Citrix Architect to monitor and manage these devices. The Workspacelab team wants to load balance their Microsoft SharePoint servers on the Citrix ADC and needs the process to be streamlined and administered using Citrix Application Delivery Management.
The following requirements were discussed during the meeting:
✑ The Microsoft SharePoint server should be optimized, load balanced, and secured in the network and should be deployed using Citrix Application Delivery Management.
✑ All the configurations should be yenned before getting pushed to the Citrix
Application Delivery Management.
Which feature should the architect use to configure the Microsoft SharePoint server using Citrix Application Delivery Management?
- A . StyleBooks
- B . Orchestration
- C . Configuration
- D . Jobs Analytics
Which two features are supported on LbaaSV1? (Choose two.)
- A . Cookie Insertion
- B . Layer 7 Load Balancing
- C . Certificate Bundle
- D . Layer 4 Load balancing
- E . Server name Indicator
Scenario: A Citrix Architect needs to design a new Citrix ADC Gateway deployment to provide secure RDP access to backend Windows machines.
Click the Exhibit button to view additional requirements collected by the architect during the design discussions.
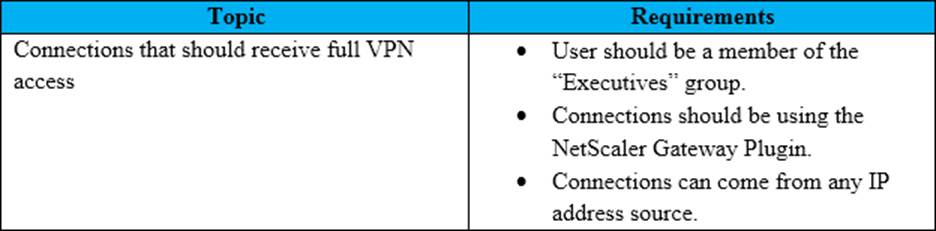
To meet the customer requirements, the architect should deploy the RDP proxy through _______, using a _________ solution. (Choose the correct option to complete the sentence.)
- A . ICAProxy, stateless gateway
- B . CVPN; single gateway
- C . CVPN; stateless gateway
- D . ICAProxy; single gateway
Scenario: A Citrix Architect and a team of Workspacelab members have met for a design discussion about the NetScaler Design Project.
They captured the following requirements:
✑ Two pairs of NetScaler MPX appliances will be deployed in the DMZ network and the internal network.
✑ High availability will be accessible between the pair of NetScaler MPX appliances in the DMZ network.
✑ Multi-factor authentication must be configured for the NetScaler Gateway virtual server.
✑ The NetScaler Gateway virtual server is integrated with XenApp/XenDesktop environment.
✑ Load balancing must be deployed for the users from the workspacelab.com and vendorlab.com domains.
✑ The logon page must show the workspacelab logo.
✑ Certificate verification must be performed to identify and extract the username.
✑ The client certificate must have UserPrincipalName as a subject.
✑ All the managed workstations for the workspace users must have a client identifications certificate installed on it.
✑ The workspacelab users connecting from a managed workstation with a client certificate on it should be authenticated using LDAP.
✑ The workspacelab users connecting from a workstation without a client certificate should be authenticated using LDAP and RADIUS.
✑ The vendorlab users should be authenticated using Active Directory Federation Service.
✑ The user credentials must NOT be shared between workspacelab and vendorlab.
✑ Single Sign-on must be performed between StoreFront and NetScaler Gateway.
✑ A domain drop down list must be provided if the user connects to the NetScaler
Gateway virtual server externally.
✑ The domain of the user connecting externally must be identified using the domain selected from the domain drop down list.
On performing the deployment, the architect observes that users are always prompted with two-factor authentication when trying to assess externally from an unmanaged workstation.
Click the exhibit button to view the configuration.
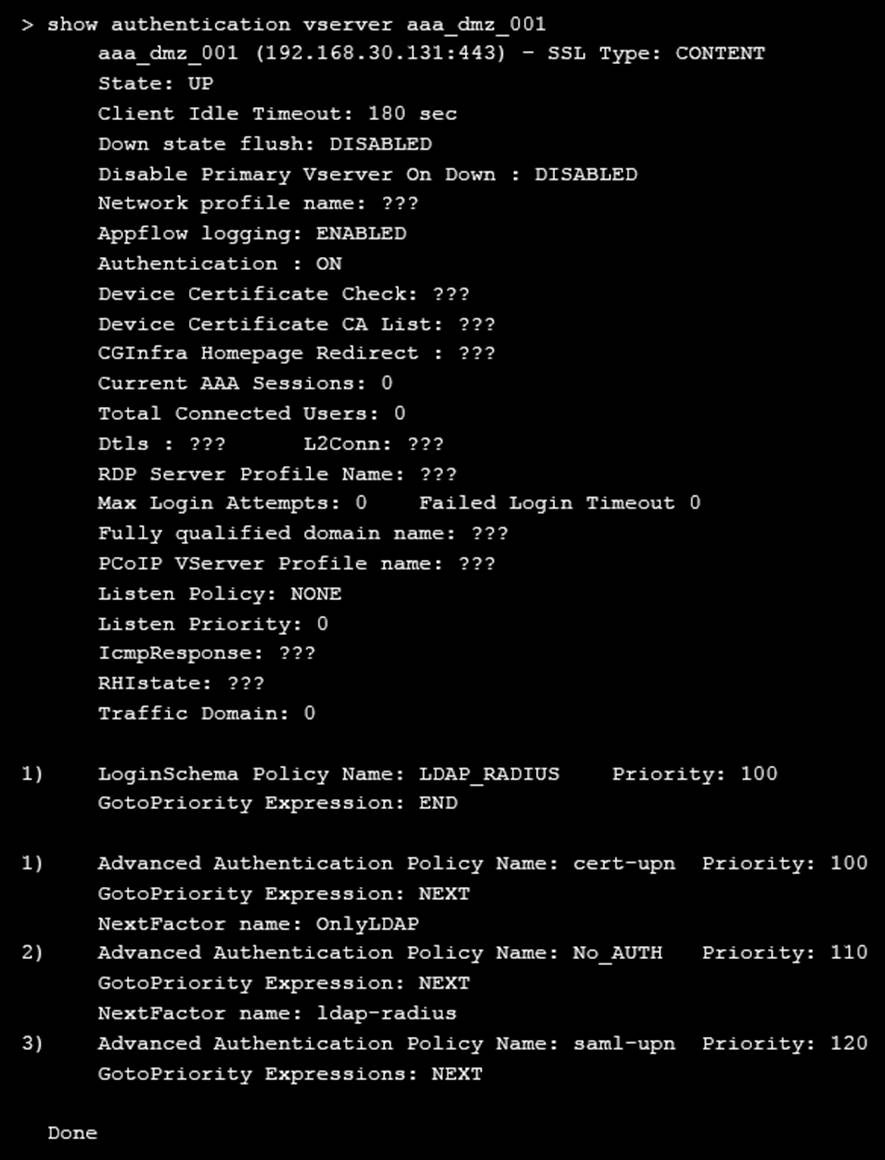
What should the architect do to correct this configuration?
- A . Update the binding LoginSchema Policy LDAP_RADIUS from the virtual server and set it as priority 1
- B . Bind the Portal theme as Domaindropdown.
- C . Bind the LoginSchema Policy Domaindropdown to priority 90.
- D . Bind the Default LoginSchema Policy as Domaindropdown.
Which statement is applicable to Citrix Gateway split tunneling?
- A . If you set split tunneling to reverse, the Citrix ADC Gateway plug-in sends only traffic destined for networks protected by Citrix ADC Gateway through the VPN tunnel. The Citrix ADC Gateway plug-in does NOT send network traffic destined for unprotected networks to Citrix ADC Gateway.
- B . If you set split tunneling to reverse, the intranet applications define the network traffic that Citrix ADC Gateway does NOT intercept.
- C . If you enable split tunneling, the intranet applications define the network traffic that Citrix ADC Gateway does NOT intercept.
- D . If you enable split tunneling, the Citrix ADC Gateway plug-in captures all network traffic originating from a user device and sends the traffic through the VPN tunnel to Citrix ADC Gateway.
- E . If you set split tunneling to reverse, the Citrix ADC Gateway plug-in captures all network traffic originating from a user device and sends the traffic through the VPN tunnel to Citrix ADC Gateway.
Under which two circumstances will a service be taken out of the slow start phase with automated slow start? (Choose two.)
- A . The service does NOT receive traffic for three successive increment intervals.
- B . The server request rate parameters are set above 25 requests per second.
- C . The actual request rate is slower than the new service request rate.
- D . The percentage of traffic that the new service must receive is greater or equal to 50.
- E . The request rate has been incremented 100 times.
A Citrix Architect can execute a configuration job using a DeployMasterConfiguration template on a NetScaler_________deployed_________. (Choose the correct option to complete sentence.)
- A . CPX; as part of a high availability pair
- B . CPX; as a stand alone device
- C . SDX; with less than 6 partitions and dedicated management interface
- D . MPX; as part of the cluster but Cluster IP is NOT configured
- E . SDX; with no partitions as a stand alone device
Which session parameter does the default authorization setting control when authentication, authorization, and auditing profiles are configured?
- A . Determines the default logging level
- B . Determines whether the NetScaler appliance will allow or deny access to content for which there is no specific authorization policy
- C . Determines the default period after which the user is automatically disconnected and must authenticate again to access the intranet
- D . Determines whether the NetScaler appliance will log users onto all web applications automatically after they authenticate or will pass users to the web application logon page to authenticate for each application.
- E . Controls are amount of time the users can be idle before they are automatically disconnected.
Scenario: A Citrix Engineer is asked by management at the workspacelab organization to review their existing Citrix ADC Configurations and make the necessary upgrades. The architect recommends small changes to the pre-existing Citrix ADC configuration. Currently, the Citrix ADC MPX devices are configured in high-availability pair, and the outbound traffic is load balanced between two internet service providers (ISPs), however, the failover is NOT happening correctly.
The following requirements were discussed during the design requirement phase:
✑ The return traffic for a specific flow should be routed through the same path while using Link Load Balancing.
✑ The link should fail over even if the ISP router is up and intermediary devices to an ISP router are down.
✑ Traffic going through one ISP router should fail over to the secondary ISP, and the traffic should not flow through both routers simultaneously.
What should the architect configure with Link Load Balancing LLB) to meet the requirement?
- A . Inverse NAT
- B . Least packets load balancing method
- C . Destination IP hash load balancing method
- D . Reverse NAT.
Scenario: More than 10,000 users will access a customer’s environment. The current networking infrastructure is capable of supporting the entire workforce of users. However, the number of support staff is limited, and management needs to ensure that they are capable of supporting the full user base.
Which two business driver is prioritized, based on the customer’s requirements?
- A . Simplify Management
- B . Increase Scalability
- C . Increase Flexibility
- D . Reduce Costs
- E . Enable Mobile Work Styles
- F . Increase Security
Latest 1Y0-440 Dumps Valid Version with 63 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

