Cisco 400-007 Cisco Certified Design Expert Online Training
Cisco 400-007 Online Training
The questions for 400-007 were last updated at Jan 18,2026.
- Exam Code: 400-007
- Exam Name: Cisco Certified Design Expert
- Certification Provider: Cisco
- Latest update: Jan 18,2026
Which three Cisco products are used in conjunction with Red Hat to provide an NFVi solution? (Choose three.)
- A . Cisco Prime Service Catalog
- B . Cisco Open Virtual Switch
- C . Cisco Nexus switches
- D . Cisco UCS
- E . Cisco Open Container Platform
- F . Cisco Virtual Network Function
Which three elements help network designers to construct secure systems that protect information and resources (such as devices, communication, and data) from unauthorized access, modification, inspection, or destruction? (Choose three.)
- A . confidential
- B . serviceability
- C . reliability
- D . availability
- E . integrity
- F . scalability
An architect receives a business requirement from a CTO that states the RTO and RPO for a new system should be as close as possible to zero.
Which replication method and datacenter technology should be used?
- A . asynchronous replication over dual data centers via DWDM
- B . synchronous replication over geographically dispersed dual data centers via MPLS
- C . synchronous replication over dual data centers via Metro Ethernet
- D . asynchronous replication over geographically dispersed dual data centers via CWDM
Which DCI technology utilizes a “flood and learn” technique to populate the Layer2 forwarding table?
- A . LISP
- B . OTV
- C . VPLS
- D . EVPN
While reviewing an existing network design, you are discussing the characteristics of different STP versions.
Which protocol minimizes unicast flooding during a Topology Change Notification in a Layer 2 switched network with many VLANs?
- A . PVRSTP
- B . MST
- C . STP
- D . PVSTP+
Company ABC wants to minimize the risk of users plugging unauthorized switches and hubs into the network.
Which two features can be used on the LAN access ports to support this design requirement? (Choose two.)
- A . Loop Guard
- B . PortFast
- C . DTF
- D . Root Guard
- E . BPDU Guard
Which best practice ensures data security in the private cloud?
- A . Use IPsec for communication between unsecured network connection
- B . Encrypt data at rest and in transition.
- C . Use the same vendor for consistent encryption.
- D . Anonymize data ownership to comply with privacy rules.
A multicast network is sing Bidirectional PIM.
Which two combined actions achieve high availability so that two RPs within the same network can act in a redundant manner? (Choose two)
- A . Use two phantom RP addresses
- B . Manipulate the administration distance of the unicast routes to the two RPs
- C . Manipulate the multicast routing table by creating static mroutes to the two RPs
- D . Advertise the two RP addresses in the routing protocol
- E . Use anycast RP based on MSDP peering between the two RPs
- F . Control routing to the two RPs through a longest match prefix
You have been asked to design a remote access VPN solution to support up to 2000 devices. You must ensure that only corporate assets are allowed to connect to the VPN, and users must authenticate to gain access of their based on their user role. Users must use a password that they are already using to access existing applications. A user may not always use the same device to access the VPN.
Which two options combined meet the requirements? (Choose two)
- A . Use local usernames and passwords on the VPN device
- B . Deploy a central authentication directory that users can be authenticated and authorized against
- C . Deploy certificates that are unique to each user
- D . Deploy an IPsec VPN solution
- E . Deploy certificates that are unique to each device
- F . Deploy a SSL VPN solution
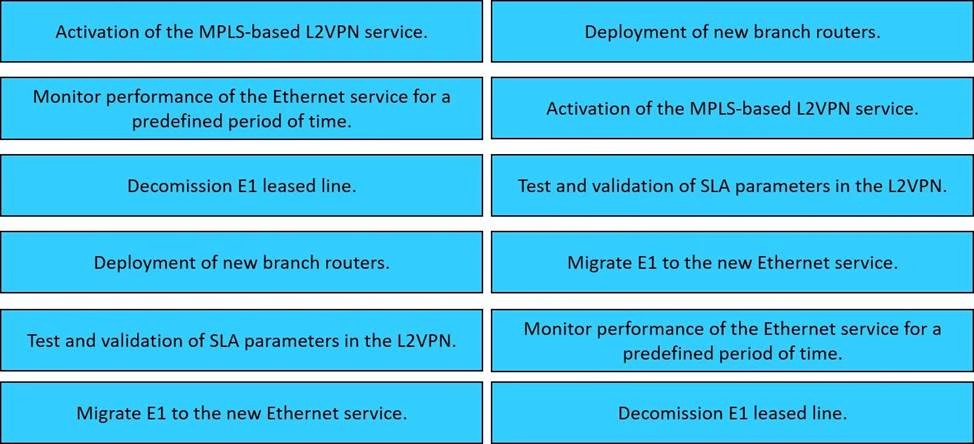
DRAG DROP
The network team in XYZ Corp wants to modernize their infrastructure and is evaluating an implementation and migration plan to allow integration MPLS-based, Layer 2 Ethernet services managed by a service provider to connect branches and remote offices. To decrease OpEx and improve response times when network components fail, XYZ Corp decided to acquire and deploy new routers. The network currently is operated over E1 leased lines (2 Mbps) with a managed CE service provided by the telco.
Drag and drop the implementation steps from the left onto the corresponding targets on the right in the correct order.
Latest 400-007 Dumps Valid Version with 141 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund