Cisco 352-001 Cisco Certified Design Expert Qualification Exam Online Training
Cisco 352-001 Online Training
The questions for 352-001 were last updated at Dec 12,2025.
- Exam Code: 352-001
- Exam Name: Cisco Certified Design Expert Qualification Exam
- Certification Provider: Cisco
- Latest update: Dec 12,2025
Two offices are connected via one 10 Gigabit Ethernet link.
What happens to the EIGRP neighborship if a link failure occurs?
- A . EIGRP neighbors stay up because the link has not gone down
- B . EIGRP neighbors drop and EIGRP begins the query process
- C . EIGRP neighbors drop after the EIGRP timers expire
- D . EIGRP neighbors drop immediately
Refer to the exhibit.
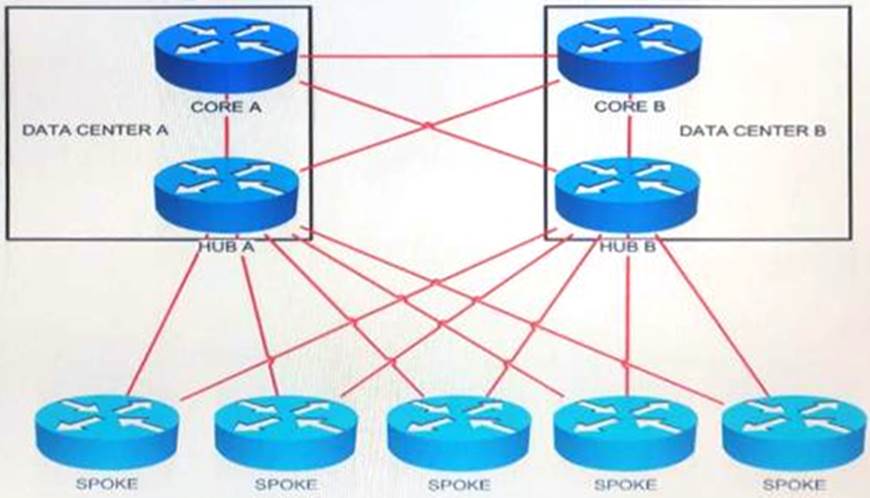
You must ensure that both A and core B devices have only the minimum information required for reaching the spoke routers, yet maintain full reachability during network failures.
Which of the following design solutions accomplishes these requirements?
- A . Implement PfR enhancements on hubs A and B
- B . Implement ODR for hub-to-spoke routing.
- C . route summarization, with GRE tunnel on hubs A and B
- D . route summarization, with specific route leaking on hubs A and B
Your design plan includes mutual redistribution of two OSPF networks at multiple locations, with connectivity to all locations in both networks.
How is this accomplished without creating Outing loops?
- A . Use route maps on the ASBRs to allow only internal routes to be redistributed.
- B . Use route maps on the ASBRs to allow internal and external routes to be redistributed.
- C . Use route maps on the ASBRs to set tags for redistributed routes.
- D . Use route maps on the ASBRs to filter routes with tags so they are not redistributed.
You are designing a GET VPN solution consisting of 30 group members.
Which measure helps product encrypted user traffic from replay attacks?
- A . RSA-encrypted nonce
- B . nonce payload
- C . time-based anti-replay
- D . counter based anti-replay
- E . digital certificates
You are designing the routing design for two merging companies that have overlapping IP address space.
Which of these must you consider when developing the routing and NAT design?
- A . Local to global NAT translation is done after routing
- B . Global to local NAT translation is done before routing.
- C . Local to global NAT translation is done before policy-based routing
- D . Global to local NAT translation is done after policy-based routing.
You have been hired to create a Layer 2 network design solution to allow a company to transition their Spanning tree Protocol to Multiple Spanning Tree The company is currently tunning a network core with a vPC switch pair and Rapid PVST+ If the company must avoid downtime in the network core, which step will be included in the design solution?
- A . It is not possible to change the Spanning Tree Protocol at a vPC switch pair without a downtime
- B . The Spanning tree Protocol must be disabled first at both vPC switches before enabling MST, to prevent any downtime
- C . Both vPC switches must be configured at the same time
- D . When Bridge Assurance is disabled, the order of the vPC switch that is configured! first does not matter
- E . The vPC switch with role "primary" must be configured first
- F . The vPC switch with role "secondary" must be configured first
Which design advantage of Ethernet VPN over VPLS is true?
- A . multitenancy support
- B . native support for multihoming with per-VLAN load balancing
- C . support of legacy protocols such as IPX
- D . increased PE scalability
In a VPLS design solution, which situation indicates that BGP must be used instead of LDP in the control plane?
- A . MAC address learning scales better through BGP
- B . BGP supports VPLS interworking
- C . Pseudowire configuration overhead is reduced
- D . There are no full-mesh pseudowire due to the route reflection feature of BGP
Your organization is working on a design solution for a new Internet-based remote access virtual private network that has 1000 remote sites A network administrator recommends GETVPN as the model because the network of today uses DMVPN, which results in a lot of background NHRP control traffic
What is a potential problem with using GETVPN for this design solution?
- A . GETVPN would require a high level of background traffic to maintain its IPsec SAs
- B . GETVPN requires an overlay routing control plane
- C . GETVPN key servers would be on public, hacker-reachable space and need higher security
- D . GETVPN is not scalable to a large number of remote sites
Which description of the RPF check in the multicast forwarding traffic is true?
- A . The source address of the multicast packet is checked in the unicast routing table. If the multicast packet arrived from the interface that matches with the interface to reach the source address, this packet passes the RPF check.
- B . The destination address of the multicast packet is checked in the BGP database. If the multicast packet arrived from the interface that mate with the interface to reach BGP peer that advertised the mutlicast prefix, this packet fails the RPF check.
- C . The source address of the multicast packet is checked in the unicast routing table. If the multicast packet arrived from the interface that matches with the interface to reach the source address, this packet fails the RPF check
- D . The unicast address of the multicast packet is checked in the BGP database. If the multicast packet arrived from the interface that matches with the interface to reach BGP peer that advertised the multicast prefix, this packet passes the RPF check
Latest 352-001 Dumps Valid Version with 232 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


