Cisco 350-901 Developing Applications using Cisco Core Platforms and APIs v1.0 Online Training
Cisco 350-901 Online Training
The questions for 350-901 were last updated at Dec 13,2025.
- Exam Code: 350-901
- Exam Name: Developing Applications using Cisco Core Platforms and APIs v1.0
- Certification Provider: Cisco
- Latest update: Dec 13,2025
A local Docker container with a Container ID of 391441516e7a is running a Python application.
Which command is used to connect to a bash shell in the running container?
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Refer to the exhibit.
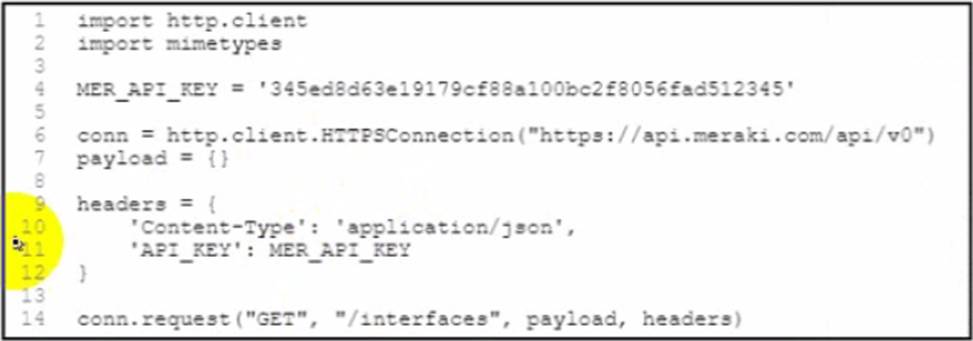
A developer created a Python script to retrieve interface information for the devices in a MeraKi network environment. A security analyst has reviewed the code and observed poor secret storage practices.
What is the appropriate password storage approach?
- A . Set the Base64 encoded version of the API key as MER_API_KEY in the code and Base64 decode before using in the header.
- B . Set an OS environment variable for MER_API_KEY to the API key during running the code and longer set MER_API_KEY within the code.
- C . Create a secret for the API key, set MER_API_KEY using the value from the secret in the Pod. and no longer set MER_API_KEY within the code.
- D . Leverage an external secret vault to retrieve MER_API_KEY and embed the vault key as a new variable before running the code.
A team of developers created their own CA and started signing certificates for all of their loT devices,.
Which action will make the browser
accept these certificates?
- A . Set the private keys 1024-bit RSA.
- B . Preload the developer CA on the trusted CA list of the browser.
- C . Enable HTTPS or port 443 on the browser.
- D . install a TLS instead of SSL certificate on the loT devices.
Which HTTP status code indicates that a client application is experiencing intentional rate limiting by the server?
- A . 202
- B . 401
- C . 429
- D . 503
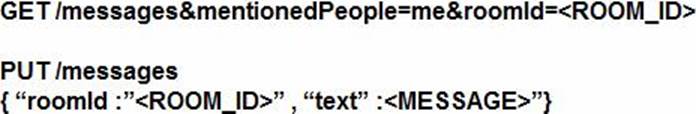
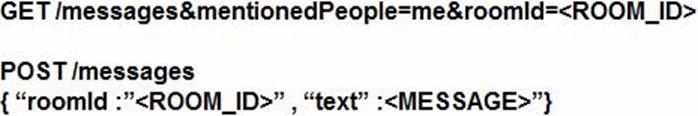
Refer to the exhibit.
Which set of API requests must be executed by a Webex Teams bot after receiving a webhook callback to process messages in a room and reply with a new message back to the same room?
A)
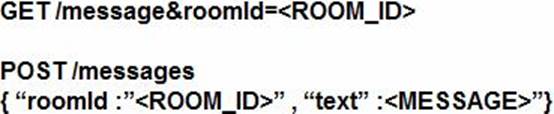
B)
C)
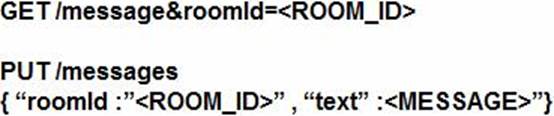
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
A developer is working on a new feature in a branch named ‘newfeay000222118’ and the current working primary branch is named ‘pnm409024967’. The developer requires a merge commit during a fast forward merge for record-keeping purposes.
Which Git command must Be used?
A)
![]()
B)
![]()
C)
![]()
D)
![]()
- A . Option A
- B . Option B
- C . Option C
- D . Option D
An enterprise refactors its monolithic application into a modem cloud-native application that is based on microservices. A key requirement of the application design is to ensure that the IT team is aware of performance issues or bottlenecks in the new application.
Which two approaches must be part of the design considerations? (Choose two)
- A . Periodically scale up the resources of the host machines when the application starts to experience high loads
- B . Instrument the application code to gather telemetry data from logs, metrics or tracing
- C . Adopt a service-oriented architecture to handle communication between the services that make up the application
- D . Deploy infrastructure monitoring agents into the operating system of the host machines
- E . Implement infrastructure monitoring to ensure that pipeline components interoperate smoothly and reliably
What is a benefit of running multiple instances of a back-end service and using load balancing to distribute the communication between the front-end and back-end services?
- A . The consistency of data for stateful services increases.
- B . High availability is provided for the back-end services.
- C . Scaling horizontally is automated out of the box.
- D . The total load on the database servers decreases.
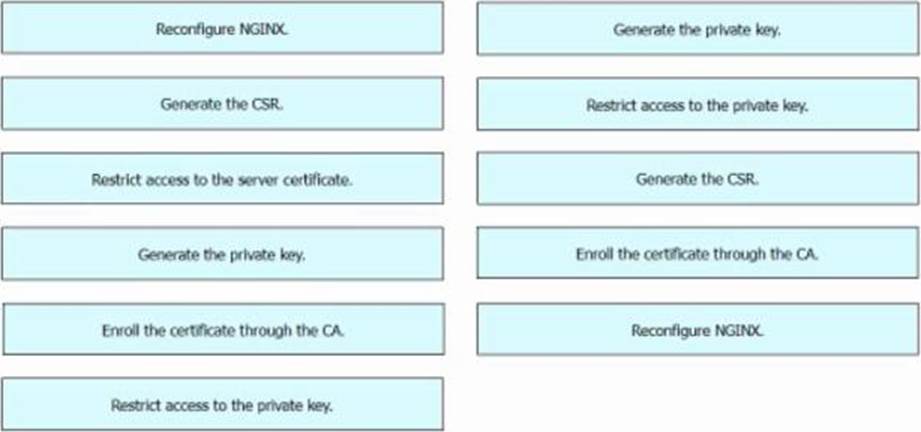
DRAG DROP
An engineer has created an NGINX web server. The server will be accessible from outside the organization. A public-key certificate must be installed before external access is allowed.
Drag and drop the steps from the left into the order on the right to configure the certificate. Not all options are used
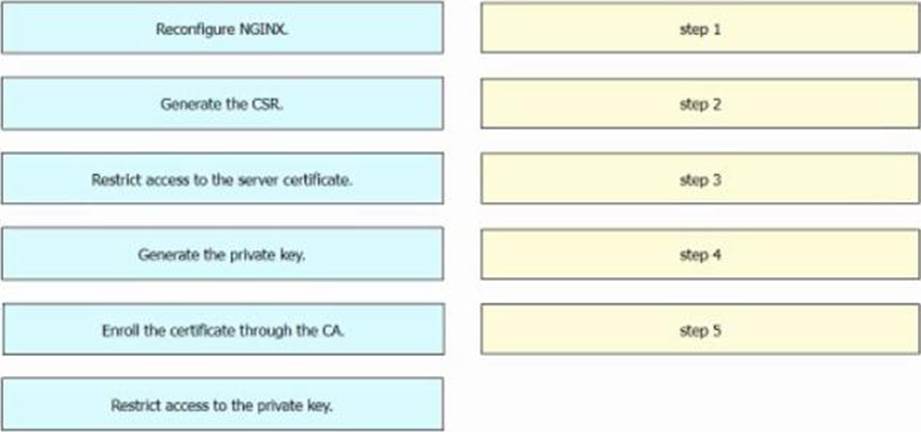
DRAG DROP
An engineer has created an NGINX web server. The server will be accessible from outside the organization. A public-key certificate must be installed before external access is allowed.
Drag and drop the steps from the left into the order on the right to configure the certificate. Not all options are used

Latest 350-901 Dumps Valid Version with 169 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund