Cisco 350-901 Developing Applications using Cisco Core Platforms and APIs v1.0 Online Training
Cisco 350-901 Online Training
The questions for 350-901 were last updated at Dec 13,2025.
- Exam Code: 350-901
- Exam Name: Developing Applications using Cisco Core Platforms and APIs v1.0
- Certification Provider: Cisco
- Latest update: Dec 13,2025
How does the use of release packaging allow dependencies to be effectively managed during deployments?
- A . dependencies are staggered between multiple releases
- B . designed to prevent any dependencies between release units
- C . dependencies are tested after the release is deployed
- D . removal of release units if they have issues in testing
Refer to the exhibit.
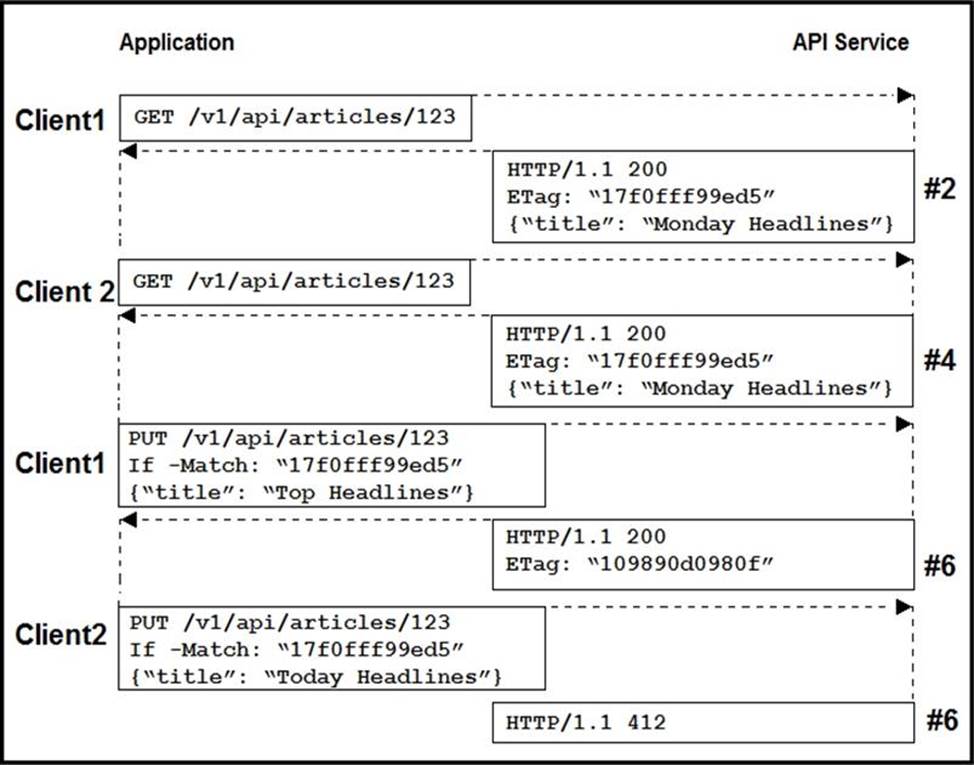
Two editors are concurrently updating an article’s headline from their mobile devices.
What results from this scenario based on this REST API sequence?
- A . The article is marked as “Conflicted”
- B . The article headline is “Monday Headlines”
- C . The article headline is “Today Headlines”
- D . The article headline is “Top Headlines”
DRAG DROP
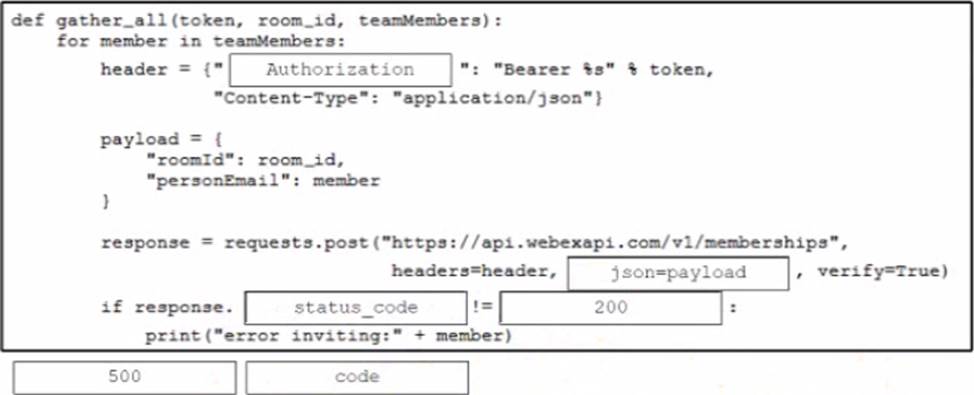
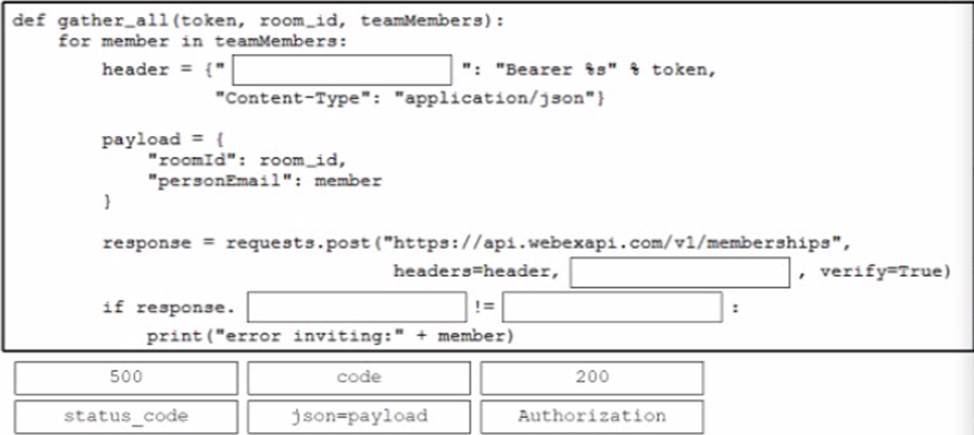
A developer is creating a Python function that adds network engineers to a Webex room to troubleshoot after a monitoring alert.
Drag and drop the code from the bottom onto the box where the code is missing in the Python function to add the engineers to the room. Not all options are used.
FILL BLANK
Fill in the blanks to complete the Python script to enable the SSID with a name of “371767916” in the network resource “11111111” using the Meraki Dashboard API.

FILL BLANK
Fill in the blanks to complete the Python script to enable the SSID with a name of “371767916” in the network resource “11111111” using the Meraki Dashboard API.

FILL BLANK
Fill in the blanks to complete the Python script to enable the SSID with a name of “371767916” in the network resource “11111111” using the Meraki Dashboard API.

FILL BLANK
Fill in the blanks to complete the Python script to enable the SSID with a name of “371767916” in the network resource “11111111” using the Meraki Dashboard API.

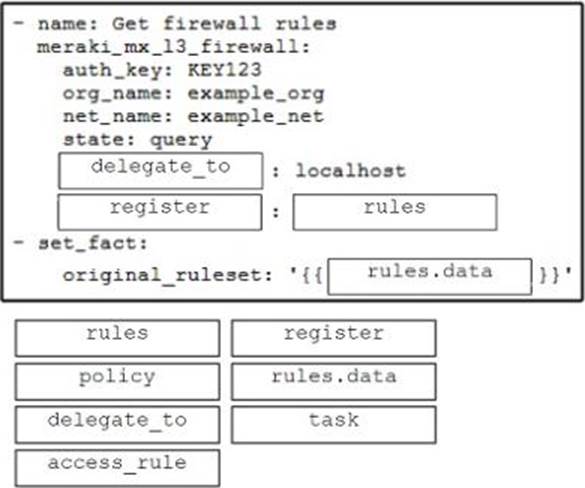
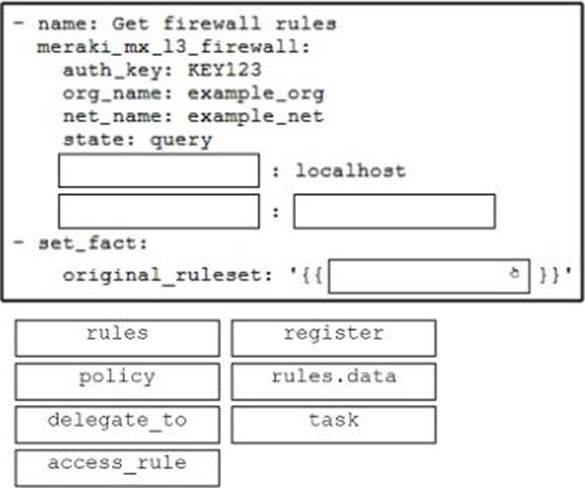
DRAG DROP
Drag and drop the code from the bottom onto the box where the code is missing in the Ansible script to get the existing firewall rules from Cisco Meraki and store the results to a new variable. Not all options are used.
Refer to the exhibit.
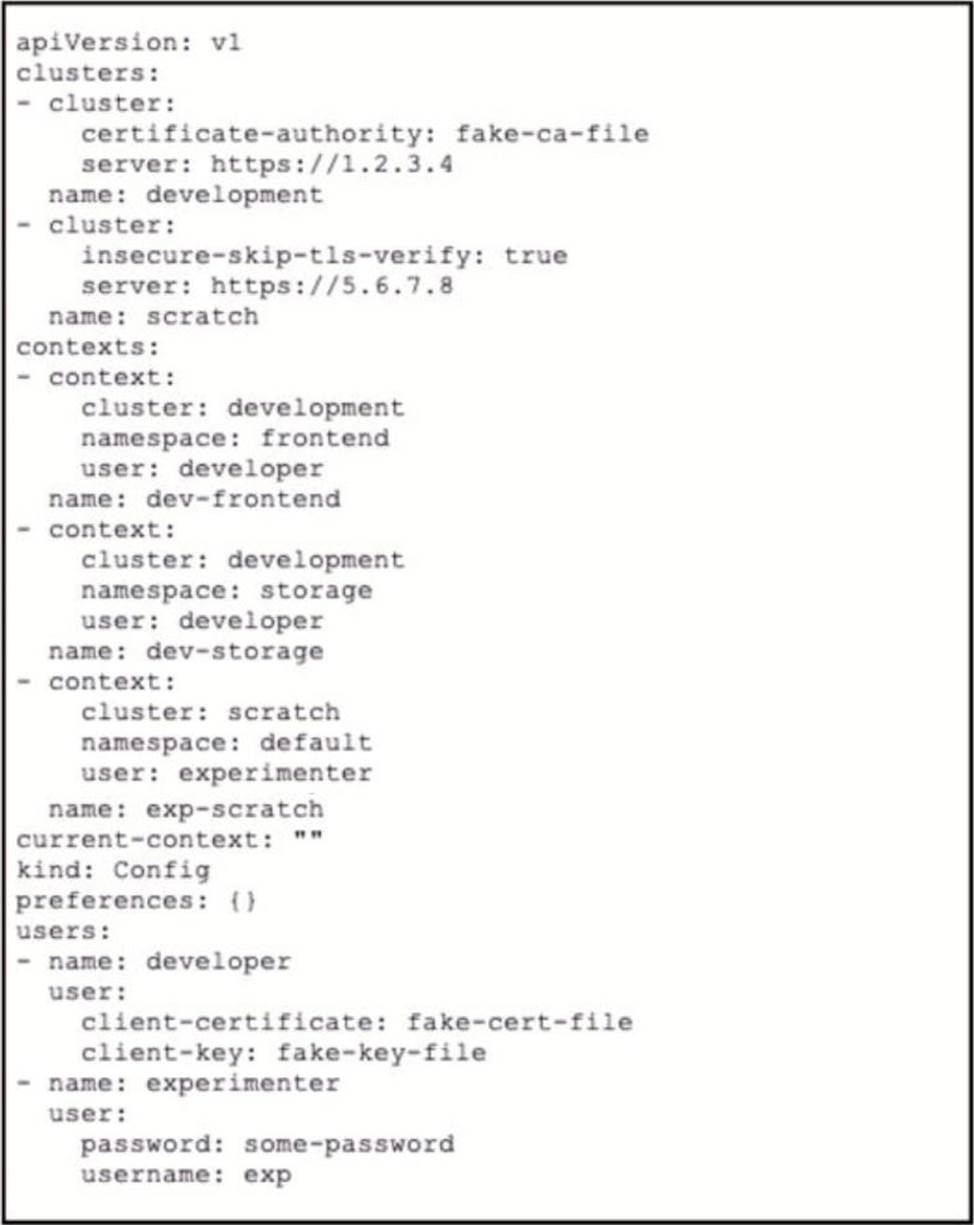
A kubeconfig file to manage access to Kubernetes clusters is shown.
How many Kubernetes clusters are defined in the file, and which cluster FS accessed using username/password authentication rather than using a certificate?
- A . three dusters; scratch
- B . three clusters: development
- C . two dusters; development
- D . two clusters: scratch
Refer to the exhibit.
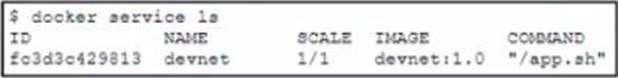
A Docker swarm service is currently running m a local data center. The service is hosting an HTML website it the container fads then the service becomes unavailable.
The design must meet these requirements
• The service must be highly available and resilient against a data center outage.
• The service must be accessible from a single URL
• The HTTP session must remain on the server from which the original request was sent
• Failure of the server must force the client to reconnect
Which two design approaches must be used to meet the requirements? (Choose two.)
- A . Create another swarm cluster within a data center and deploy a secondary instance of the service.
- B . Create another node in the swarm duster to scale the service across the nodes over two replicas.
- C . Configure an external load balancer to route requests to the swarm service by using session persistence
- D . Scale the Docker swarm service to 2 and set endpoint-mode to DNSRR instead of the default value of VIP
- E . Configure a routing mesh to route requests to the swarm service by using NAT on the network side
Latest 350-901 Dumps Valid Version with 169 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund