Cisco 350-701 Implementing and Operating Cisco Security Core Technologies (SCOR) Online Training
Cisco 350-701 Online Training
The questions for 350-701 were last updated at Mar 03,2026.
- Exam Code: 350-701
- Exam Name: Implementing and Operating Cisco Security Core Technologies (SCOR)
- Certification Provider: Cisco
- Latest update: Mar 03,2026
What is a characteristic of traffic storm control behavior?
- A . Traffic storm control drops all broadcast and multicast traffic if the combined traffic exceeds the level within the interval.
- B . Traffic storm control cannot determine if the packet is unicast or broadcast.
- C . Traffic storm control monitors incoming traffic levels over a 10-second traffic storm control interval.
- D . Traffic storm control uses the Individual/Group bit in the packet source address to determine if the packet is unicast or broadcast.
An engineer is configuring a Cisco ESA and wants to control whether to accept or reject email messages to a recipient address.
Which list contains the allowed recipient addresses?
- A . SAT
- B . BAT
- C . HAT
- D . RAT
Refer to the exhibit.
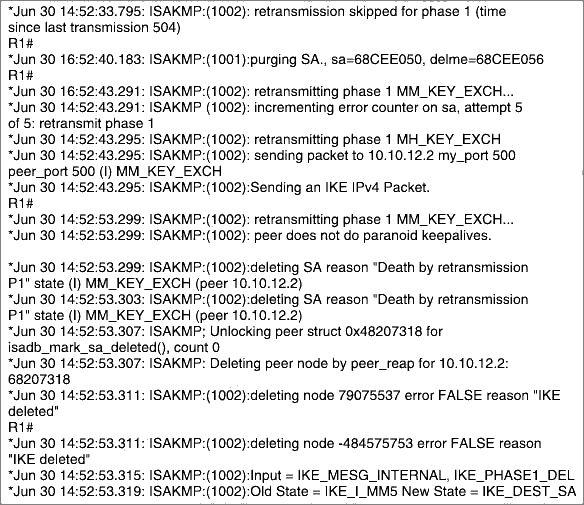
A network administrator configured a site-to-site VPN tunnel between two Cisco IOS routers, and hosts are unable to communicate between two sites of VPN. The network administrator runs the debug crypto isakmp sa command to track VPN status.
What is the problem according to this command output?
- A . hashing algorithm mismatch
- B . encryption algorithm mismatch
- C . authentication key mismatch
- D . interesting traffic was not applied
Which two deployment model configurations are supported for Cisco FTDv in AWS? (Choose two)
- A . Cisco FTDv configured in routed mode and managed by an FMCv installed in AWS
- B . Cisco FTDv with one management interface and two traffic interfaces configured
- C . Cisco FTDv configured in routed mode and managed by a physical FMC appliance on premises
- D . Cisco FTDv with two management interfaces and one traffic interface configured
- E . Cisco FTDv configured in routed mode and IPv6 configured
What are two list types within AMP for Endpoints Outbreak Control? (Choose two)
- A . blocked ports
- B . simple custom detections
- C . command and control
- D . allowed applications
- E . URL
Which feature is configured for managed devices in the device platform settings of the Firepower Management Center?
- A . quality of service
- B . time synchronization
- C . network address translations
- D . intrusion policy
Which two features are used to configure Cisco ESA with a multilayer approach to fight viruses and malware? (Choose two)
- A . Sophos engine
- B . white list
- C . RAT
- D . outbreak filters
- E . DLP
Which two capabilities does TAXII support? (Choose two)
- A . Exchange
- B . Pull messaging
- C . Binding
- D . Correlation
- E . Mitigating
Which Cisco solution does Cisco Umbrella integrate with to determine if a URL is malicious?
- A . AMP
- B . AnyConnect
- C . DynDNS
- D . Talos
An engineer wants to generate NetFlow records on traffic traversing the Cisco ASA.
Which Cisco ASA
command must be used?
- A . flow-export destination inside 1.1.1.1 2055
- B . ip flow monitor input
- C . ip flow-export destination 1.1.1.1 2055
- D . flow exporter
Latest 350-701 Dumps Valid Version with 327 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

