Cisco 350-401 Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR) Online Training
Cisco 350-401 Online Training
The questions for 350-401 were last updated at Jan 27,2026.
- Exam Code: 350-401
- Exam Name: Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)
- Certification Provider: Cisco
- Latest update: Jan 27,2026
How is 802.11 traffic handled in a fabric-enabled SSID?
- A . centrally switched back to WLC where the user traffic is mapped to a VXLAN on the WLC
- B . converted by the AP into 802.3 and encapsulated into VXLAN
- C . centrally switched back to WLC where the user traffic is mapped to a VLAN on the WLC
- D . converted by the AP into 802.3 and encapsulated into a VLAN
Which measurement is used from a post wireless survey to depict the cell edge of the access points?
- A . SNR
- B . Noise
- C . RSSI
- D . CCI
Refer to the exhibit.
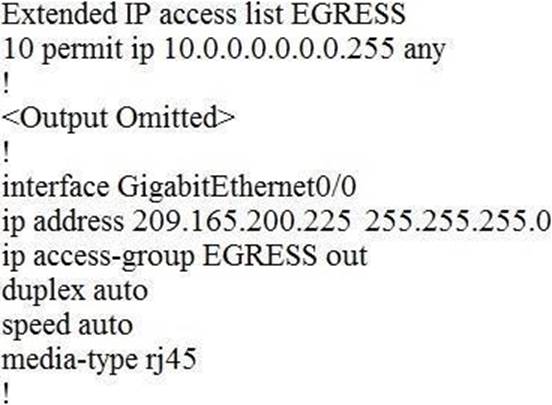
An engineer must block all traffic from a router to its directly connected subnet 209.165.200.0/24. The engineer applies access control list EGRESS in the outbound direction on the GigabitEthernet0/0 interface of the router However, the router can still ping hosts on the 209.165.200.0/24 subnet.
Which explanation of this behavior is true?
- A . Access control lists that are applied outbound to a router interface do not affect traffic that is sourced from the router.
- B . Only standard access control lists can block traffic from a source IP address.
- C . After an access control list is applied to an interface, that interface must be shut and no shut for the access control list to take effect.
- D . The access control list must contain an explicit deny to block traffic from the router.
Refer to the exhibit.
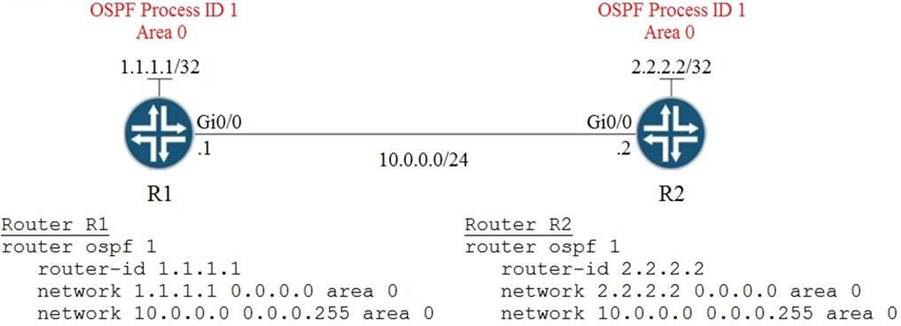
A network engineer is configuring OSPF between router R1 and router R2. The engineer must ensure that a DR/BDR election does not occur on the Gigabit Ethernet interfaces in area 0.
Which configuration set accomplishes this goal?
- A . R1(config-if)interfaceGi0/0
R1(config-if)ipospf network point-to-point
R2(config-if)interface Gi0/0
R2(config-if)ipospf network point-to-point - B . R1(config-if)interfaceGi0/0
R1(config-if)ipospf network broadcast
R2(config-if)interface Gi0/0
R2(config-if)ipospf network broadcast - C . R1(config-if)interfaceGi0/0
R1(config-if)ipospf database-filter all out
R2(config-if)interface Gi0/0
R2(config-if)ipospf database-filter all out - D . R1(config-if)interfaceGi0/0
R1(config-if)ipospf priority 1
R2(config-if)interface Gi0/0
R2(config-if)ipospf priority 1
Which design principle slates that a user has no access by default to any resource, and unless a resource is explicitly granted, it should be denied?
- A . least privilege
- B . fail-safe defaults
- C . economy of mechanism
- D . complete mediation
How does an on-premises infrastructure compare to a cloud infrastructure?
- A . On-premises can increase compute power faster than cloud
- B . On-premises requires less power and cooling resources than cloud
- C . On-premises offers faster deployment than cloud
- D . On-premises offers lower latency for physically adjacent systems than cloud.
Refer to the Exhibit.
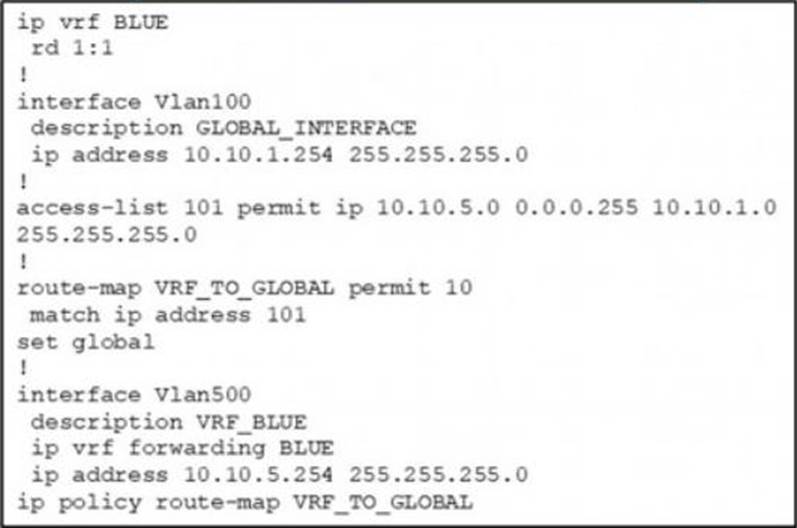
An engineer attempts to create a configuration to allow the Blue VRF to leak into the global routing table, but the configuration does not function as expected.
Which action resolves this issue?
- A . Change the access-list destination mask to a wildcard.
- B . Change the source network that Is specified in access-list 101.
- C . Change the route-map configuration to VRF_BLUE.
- D . Change the access-list number in the route map
What is a consideration when designing a Cisco SD-Access underlay network?
- A . End user subnets and endpoints are part of the underlay network.
- B . The underlay switches provide endpoint physical connectivity for users.
- C . Static routing is a requirement,
- D . It must support IPv4 and IPv6 underlay networks
How is Layer 3 roaming accomplished in a unified wireless deployment?
- A . An EoIP tunnel is created between the client and the anchor controller to provide seamless connectivity as the client is associated with the new AP.
- B . The client entry on the original controller is passed to the database on the new controller.
- C . The new controller assigns an IP address from the new subnet to the client
- D . The client database on the original controller is updated the anchor entry, and the new controller database is updated with the foreign entry.
A customer has recently implemented a new wireless infrastructure using WLC-5520 at a site directly next to a large commercial airport. Users report that they intermittently lose WI-FI connectivity, and troubleshooting reveals it is due to frequent channel changes.
Which two actions fix this issue? (Choose two)
- A . Remove UNII-2 and Extended UNII-2 channels from the 5 Ghz channel list
- B . Restore the DCA default settings because this automatically avoids channel interference.
- C . Configure channels on the UNIk2 and the Extended UNII-2 sub-bands of the 5 Ghz band only
- D . Enable DFS channels because they are immune to radar interference.
- E . Disable DFS channels to prevent interference with Doppler radar
Latest 350-401 Dumps Valid Version with 404 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


Question 91 has a wrong answer marked s correct. The answer is B.
BPDU filter is the only option to block BPDUs while not going inte err disabled when a BPDU is received.
https://www.exam4training.com/which-command-set-must-be-configured-on-switch1-to-achieve-the-following-results-on-port-fa0-1/
https://www.cisco.com/en/US/docs/switches/metro/me3600x_3800x/trash/swstpopt.html#:~:text=The%20BPDU%20filtering%20feature%20can,bpdufilter%20default%20global%20configuration%20command.