Cisco 350-201 Performing CyberOps Using Core Security Technologies (CBRCOR) Online Training
Cisco 350-201 Online Training
The questions for 350-201 were last updated at Mar 01,2026.
- Exam Code: 350-201
- Exam Name: Performing CyberOps Using Core Security Technologies (CBRCOR)
- Certification Provider: Cisco
- Latest update: Mar 01,2026
An audit is assessing a small business that is selling automotive parts and diagnostic services. Due to increased customer demands, the company recently started to accept credit card payments and acquired a POS terminal .
Which compliance regulations must the audit apply to the company?
- A . HIPAA
- B . FISMA
- C . COBIT
- D . PCI DSS
Refer to the exhibit.
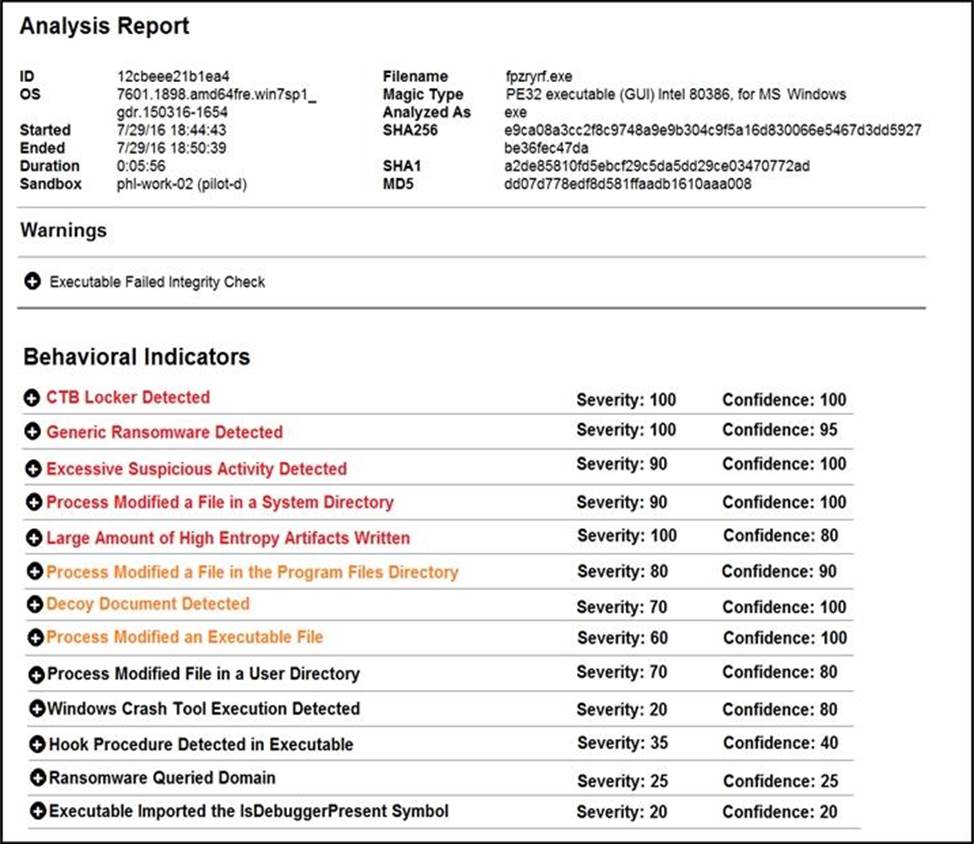
Cisco Advanced Malware Protection installed on an end-user desktop has automatically submitted a low prevalence file to the Threat Grid analysis engine for further analysis .
What should be concluded from this report?
- A . The prioritized behavioral indicators of compromise do not justify the execution of the “ransomware” because the scores do not indicate the likelihood of malicious ransomware.
- B . The prioritized behavioral indicators of compromise do not justify the execution of the “ransomware” because the scores are high and do not indicate the likelihood of malicious ransomware.
- C . The prioritized behavioral indicators of compromise justify the execution of the “ransomware” because the scores are high and indicate the likelihood that malicious ransomware has been detected.
- D . The prioritized behavioral indicators of compromise justify the execution of the “ransomware” because the scores are low and indicate the likelihood that malicious ransomware has been detected.
Engineers are working to document, list, and discover all used applications within an organization. During the regular assessment of applications from the HR backup server, an engineer discovered an unknown application. The analysis showed that the application is communicating with external addresses on a non- secure, unencrypted channel. Information gathering revealed that the unknown application does not have an owner and is not being used by a business unit .
What are the next two steps the engineers should take in this investigation? (Choose two.)
- A . Determine the type of data stored on the affected asset, document the access logs, and engage the incident response team.
- B . Identify who installed the application by reviewing the logs and gather a user access log from the HR department.
- C . Verify user credentials on the affected asset, modify passwords, and confirm available patches and updates are installed.
- D . Initiate a triage meeting with department leads to determine if the application is owned internally or used by any business unit and document the asset owner.
Refer to the exhibit.
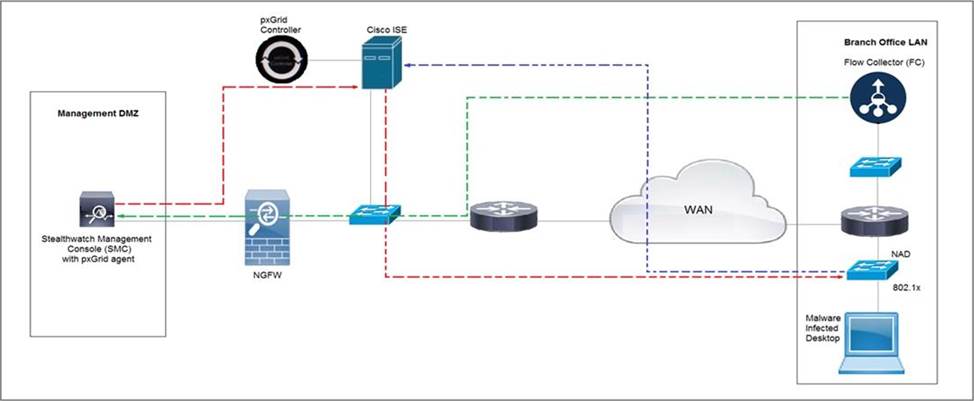
Rapid Threat Containment using Cisco Secure Network Analytics (Stealthwatch) and ISE detects the threat of malware-infected 802.1x authenticated endpoints and places that endpoint into a quarantine VLAN using Adaptive Network Control policy .
Which method was used to signal ISE to quarantine the endpoints?
- A . SNMP
- B . syslog
- C . REST API
- D . pxGrid
A European-based advertisement company collects tracking information from partner websites and stores it on a local server to provide tailored ads .
Which standard must the company follow to safeguard the resting data?
- A . HIPAA
- B . PCI-DSS
- C . Sarbanes-Oxley
- D . GDPR
Refer to the exhibit.
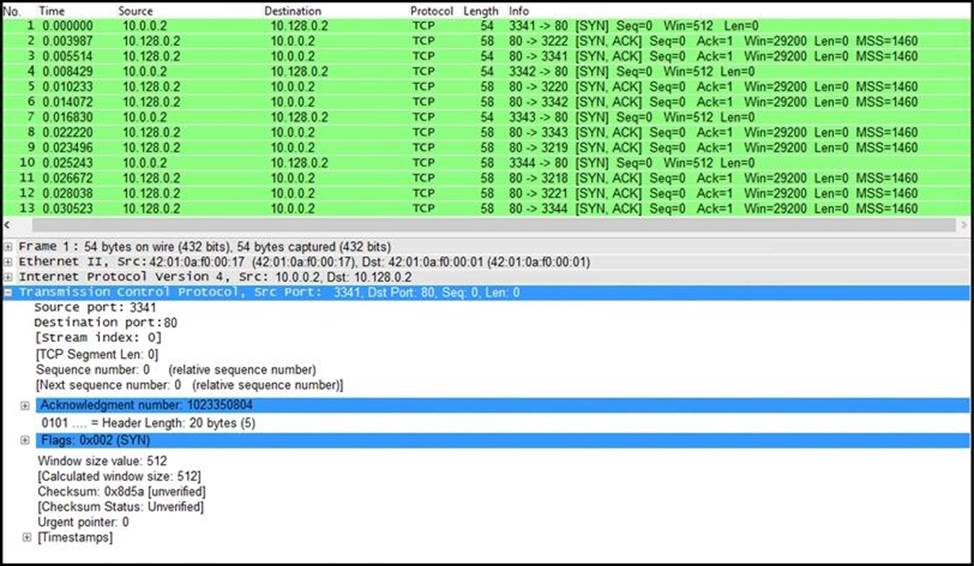
What is the threat in this Wireshark traffic capture?
- A . A high rate of SYN packets being sent from multiple sources toward a single destination IP
- B . A flood of ACK packets coming from a single source IP to multiple destination IPs
- C . A high rate of SYN packets being sent from a single source IP toward multiple destination IPs
- D . A flood of SYN packets coming from a single source IP to a single destination IP
Refer to the exhibit.
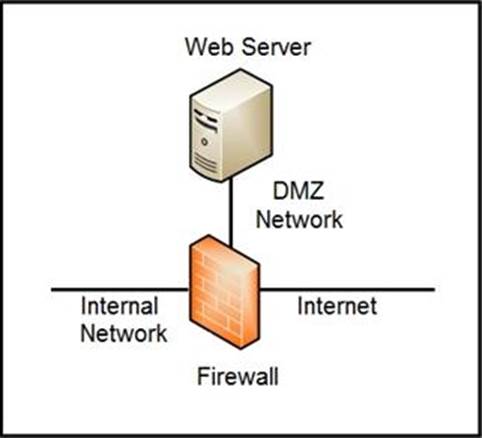
Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)
- A . Create an ACL on the firewall to allow only TLS 1.3
- B . Implement a proxy server in the DMZ network
- C . Create an ACL on the firewall to allow only external connections
- D . Move the webserver to the internal network
What is needed to assess risk mitigation effectiveness in an organization?
- A . analysis of key performance indicators
- B . compliance with security standards
- C . cost-effectiveness of control measures
- D . updated list of vulnerable systems
A security architect is working in a processing center and must implement a DLP solution to detect and prevent any type of copy and paste attempts of sensitive data within unapproved applications and removable devices .
Which technical architecture must be used?
- A . DLP for data in motion
- B . DLP for removable data
- C . DLP for data in use
- D . DLP for data at rest
Refer to the exhibit.
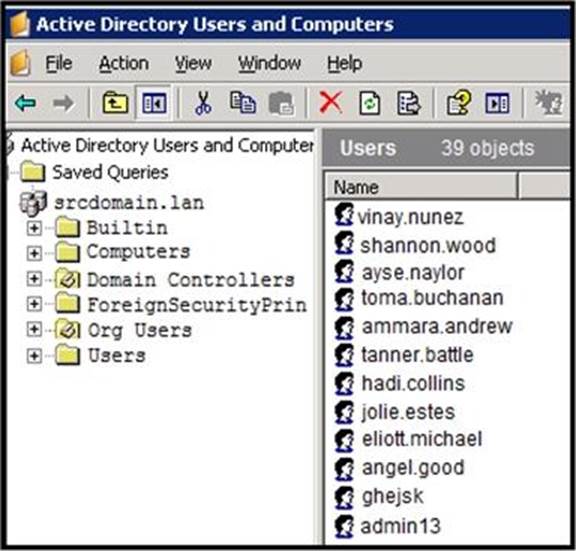
An engineer is investigating a case with suspicious usernames within the active directory. After the engineer investigates and cross-correlates events from other sources, it appears that the 2 users are privileged, and their creation date matches suspicious network traffic that was initiated from the internal network 2 days prior .
Which type of compromise is occurring?
- A . compromised insider
- B . compromised root access
- C . compromised database tables
- D . compromised network
Latest 350-201 Dumps Valid Version with 139 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

