Cisco 350-201 Performing CyberOps Using Core Security Technologies (CBRCOR) Online Training
Cisco 350-201 Online Training
The questions for 350-201 were last updated at Mar 02,2026.
- Exam Code: 350-201
- Exam Name: Performing CyberOps Using Core Security Technologies (CBRCOR)
- Certification Provider: Cisco
- Latest update: Mar 02,2026
Refer to the exhibit.
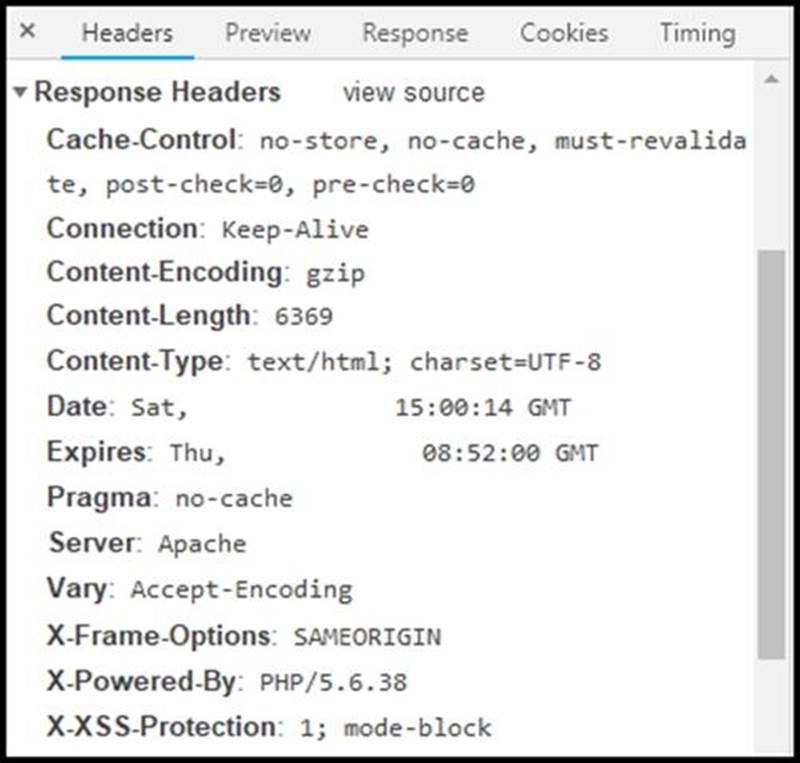
Where are the browser page rendering permissions displayed?
- A . X-Frame-Options
- B . X-XSS-Protection
- C . Content-Type
- D . Cache-Control
What is the difference between process orchestration and automation?
- A . Orchestration combines a set of automated tools, while automation is focused on the tools to automate process flows.
- B . Orchestration arranges the tasks, while automation arranges processes.
- C . Orchestration minimizes redundancies, while automation decreases the time to recover from redundancies.
- D . Automation optimizes the individual tasks to execute the process, while orchestration optimizes frequent and repeatable processes.
Refer to the exhibit.
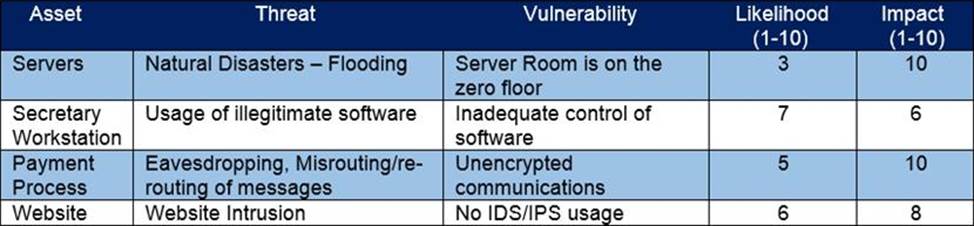
Which asset has the highest risk value?
- A . servers
- B . website
- C . payment process
- D . secretary workstation
An organization installed a new application server for IP phones. An automated process fetched user credentials from the Active Directory server, and the application will have access to on-premises and cloud services .
Which security threat should be mitigated first?
- A . aligning access control policies
- B . exfiltration during data transfer
- C . attack using default accounts
- D . data exposure from backups
An analyst received multiple alerts on the SIEM console of users that are navigating to malicious URLs. The analyst needs to automate the task of receiving alerts and processing the data for further investigations. Three variables are available from the SIEM console to include in an automation script: console_ip, api_token, and reference_set_name .
What must be added to this script to receive a successful HTTP response?
#!/usr/bin/python import sys import requests
- A . {1}, {2}
- B . {1}, {3}
- C . console_ip, api_token
- D . console_ip, reference_set_name
An organization is using a PKI management server and a SOAR platform to manage the certificate lifecycle. The SOAR platform queries a certificate management tool to check all endpoints for SSL certificates that have either expired or are nearing expiration. Engineers are struggling to manage problematic certificates outside of PKI management since deploying certificates and tracking them requires searching server owners manually .
Which action will improve workflow automation?
- A . Implement a new workflow within SOAR to create tickets in the incident response system, assign problematic certificate update requests to server owners, and register change requests.
- B . Integrate a PKI solution within SOAR to create certificates within the SOAR engines to track, update, and monitor problematic certificates.
- C . Implement a new workflow for SOAR to fetch a report of assets that are outside of the PKI zone, sort assets by certification management leads and automate alerts that updates are needed.
- D . Integrate a SOAR solution with Active Directory to pull server owner details from the AD
and send an automated email for problematic certificates requesting updates.
A SOC analyst detected a ransomware outbreak in the organization coming from a malicious email attachment. Affected parties are notified, and the incident response team is assigned to the case. According to the NIST incident response handbook, what is the next step in handling the incident?
- A . Create a follow-up report based on the incident documentation.
- B . Perform a vulnerability assessment to find existing vulnerabilities.
- C . Eradicate malicious software from the infected machines.
- D . Collect evidence and maintain a chain-of-custody during further analysis.
Refer to the exhibit.
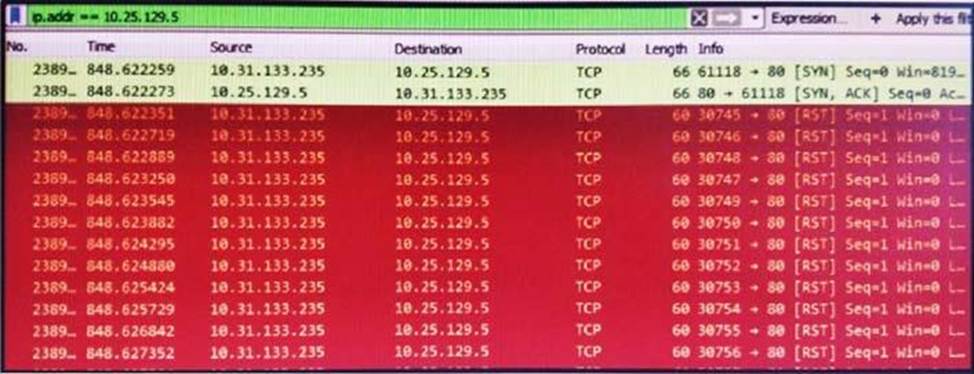
What is occurring in this packet capture?
- A . TCP port scan
- B . TCP flood
- C . DNS flood
- D . DNS tunneling
The network operations center has identified malware, created a ticket within their ticketing system, and assigned the case to the SOC with high-level information. A SOC analyst was able to stop the malware from spreading and identified the attacking host .
What is the next step in the incident response workflow?
- A . eradication and recovery
- B . post-incident activity
- C . containment
- D . detection and analysis
A security architect in an automotive factory is working on the Cyber Security Management System and is implementing procedures and creating policies to prevent attacks .
Which standard must the architect apply?
- A . IEC62446
- B . IEC62443
- C . IEC62439-3
- D . IEC62439-2
Latest 350-201 Dumps Valid Version with 139 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

