Cisco 300-620 Implementing Cisco Application Centric Infrastructure (DCACI) Online Training
Cisco 300-620 Online Training
The questions for 300-620 were last updated at Mar 02,2026.
- Exam Code: 300-620
- Exam Name: Implementing Cisco Application Centric Infrastructure (DCACI)
- Certification Provider: Cisco
- Latest update: Mar 02,2026
Which two protocols support accessing backup files on a remote location from the APIC? (Choose two.)
- A . TFTP
- B . FTP
- C . SFTP
- D . SMB
- E . HTTPS
An engineer must advertise a selection of external networks learned from a BGP neighbor into the ACI fabric.
Which L3Out subnet configuration option creates an inbound route map for route filtering?
- A . External Subnets for the External EPG
- B . Shared Route Control Subnet
- C . Import Route Control Subnet
- D . Shared Security Import Subnet
A Cisco ACI endpoint group must have its gateway address migrated out of the ACI fabric. An engineer configures EPG-TEST with a static port binding and configures the encap VLAN with the required VLAN.
Which configuration set must be used on the bridge domain to meet these requirements?
- A . L2 Unknown Unicast: Hardware Proxy
Unicast Routing: Disabled
ARP Flooding: Enabled - B . L2 Unknown Unicast: Hardware Proxy
Unicast Routing: Disabled
ARP Flooding: Disabled - C . L2 Unknown Unicast: Flood
Unicast Routing: Disabled
ARP Flooding: Enabled - D . L2 Unknown Unicast: Flood
Unicast Routing: Enabled
ARP Flooding: Enabled
Which endpoint learning operation is completed on the ingress leaf switch when traffic is received from a Layer 3 Out?
- A . The source MAC address of the traffic is learned as a local endpoint.
- B . The source MAC address of the traffic is learned as a remote endpoint.
- C . The source IP address of the traffic is learned as a remote endpoint.
- D . The source IP address of the traffic is learned as a local endpoint.
Refer to the exhibit.
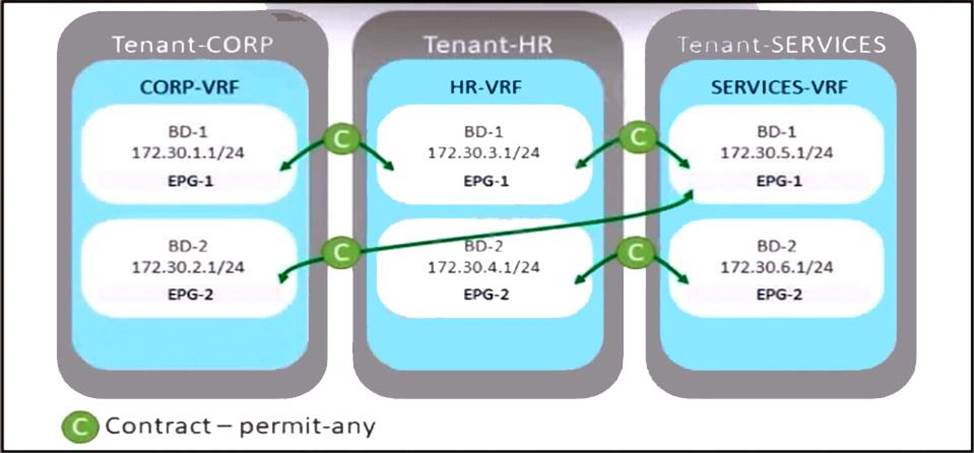
A company merges three of its departments: CORP, HR, and SERVICES, Currently, the connectivity between departments is achieved by using VRF route leaking. The requirement is to redesign the Cisco ACI networking architecture to communicate between EPGs and BDs from any tenant without configuring contracts or VRF route leaking.
Which configuration meets these criteria?
- A . Configure an unenforced VRF in the user tenant and map all required EPGs to it.
- B . Implement an enforced VRF in the common tenant and map all required BDs to it.
- C . Configure an enforced VRF in the user tenant and map all required EPGs to it.
- D . Implement an unenforced VRF in the common tenant and map all required BDs to it.
A bridge domain for an EPC called “Web Servers” must be created in the Cisco APIC.
The configuration must meet these requirements:
✑ Only traffic to known Mac addresses must be allowed to reduce noice.
✑ The multicast traffic must be limited to the ports that are participating in multicast routing.
✑ The endpoints within the bridge domain must be kept in the endpoint table for 20 minultes without any updates.
Which set of steps configures the bridge domain that satisfies the requirements?
- A . Select the ARP Flooding checkbox.
Create an Endpoint Retention Policy with a Remote Endpoint Aging Interval of 20 minutes. Set L3 Unknown Multicast Flooding to Optimized Flooding - B . Set L2 Unknown Unicast to Hardware Proxy.
Configure L3 Unknown Multicast Flooding to Optimized Flood.
Create an Endpoint Retention Policy with a Local Endpoint Aging interval of 1200 seconds. - C . Switch L2 Unknown Unicast to Flood.
Select the default Endpoint Retention Policy and set the Local Endpoint Aging to 20 minutes.
Set Multicast Destination Flooding to Flood in Encapsulation. - D . Multicast Destination Flooding should be set to Flood in BD.
Set L3 Unknown Multicast Flooding to Flood.
Select the default Endpoint Retention Policy with a Local Endpoint Aging Interval of 1200 seconds.
Refer to the exhibit.
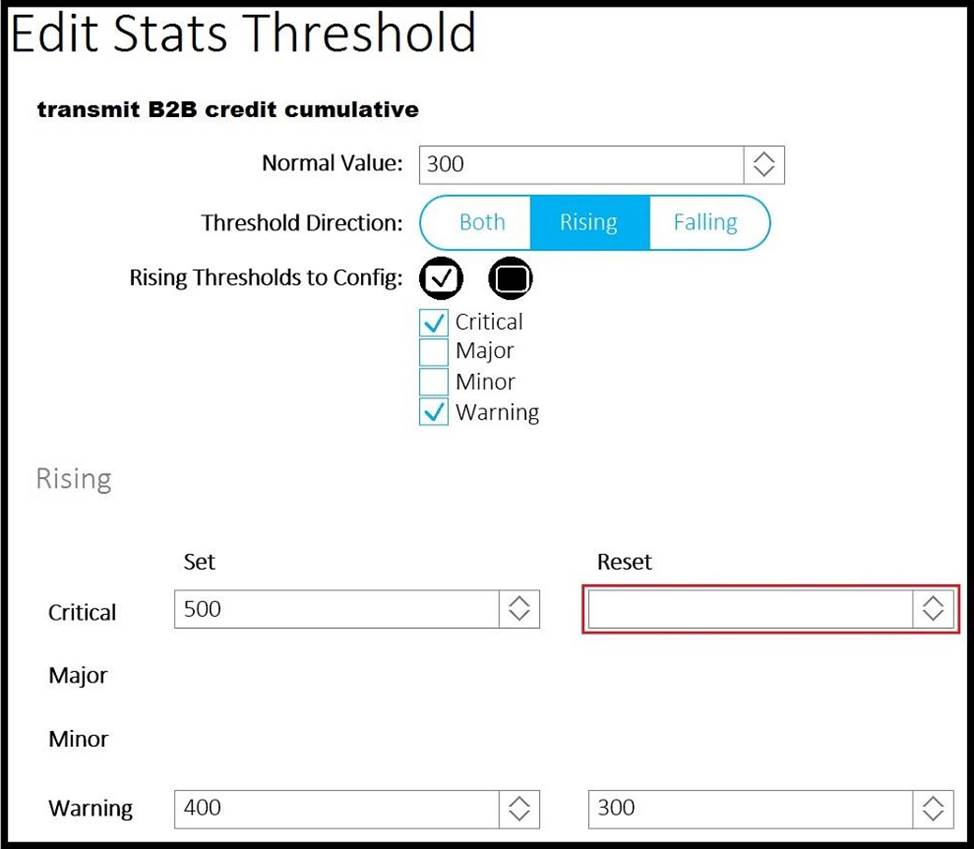
A client reports that the ACI domain connectivity to the fiber channel storage is experiencing a B2B credit oversubscription. The environment has a SYSLOG server for state collection messages.
Which value should be chosen to clear the critical fault?
- A . 300
- B . 410
- C . 350
- D . 510
A Solutions Architect is asked to design two data centers based on Cisco ACI technology that can extend L2/L3, VXLAN, and network policy across locations. ACI Multi-Pod has been selected.
Which two requirements must be considered in this design? (Choose two.)
- A . ACI underlay protocols, i.e. COOP, IS-IS and MP-BGP, spans across pods. Create QoS policies to make sure those protocols have higher priority.
- B . A single APIC Cluster is required in a Multi-Pod design. It is important to place the APIC
Controllers in different locations in order to maximize redundancy and reliability. - C . ACI Multi-Pod requires an IP Network supporting PIM-Bidir.
- D . ACI Multi-Pod does not support Firewall Clusters across Pods. Firewall Clusters should always be local.
- E . Multi-Pod requires multiple APIC Controller Clusters, one per pod. Make sure those clusters can communicate to each other through a highly available connection.
An engineer is implementing Cisco ACI at a large platform-as-a-service provider using APIC controllers, 9396PX leaf switches, and 9336PQ spine switches. The leaf switch ports are configured as IEEE 802.1p ports.
Where does the traffic exit from the EPG in IEEE 802.1p mode in this configuration?
- A . from leaf ports tagged as VLAN 0
- B . from leaf ports untagged
- C . from leaf ports tagged as VLAN 4094
- D . from leaf ports tagged as VLAN 1
An engineer must implement management policy and data plane separation in the Cisco ACI fabric.
Which ACI object must be created in Cisco APIC to accomplish this goal?
- A . Application profile
- B . Tenant
- C . Contract
- D . Bridge domain
Latest 300-620 Dumps Valid Version with 78 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

