Cisco 300-620 Implementing Cisco Application Centric Infrastructure (DCACI) Online Training
Cisco 300-620 Online Training
The questions for 300-620 were last updated at Mar 01,2026.
- Exam Code: 300-620
- Exam Name: Implementing Cisco Application Centric Infrastructure (DCACI)
- Certification Provider: Cisco
- Latest update: Mar 01,2026
What two actions should be taken to deploy a new Cisco ACI Multi-Pod setup? (Choose two.)
- A . Configure MP-BGP on IPN routers that face the Cisco ACI spines.
- B . Connect all spines to the IPN.
- C . Configure anycast RP for the underlying multicast protocol
- D . Configure the TEP pool of the new pod to be routable across the IPN.
- E . Increase interface MTU for all IPN routers to support VXLAN traffic.
Refer to the exhibit.
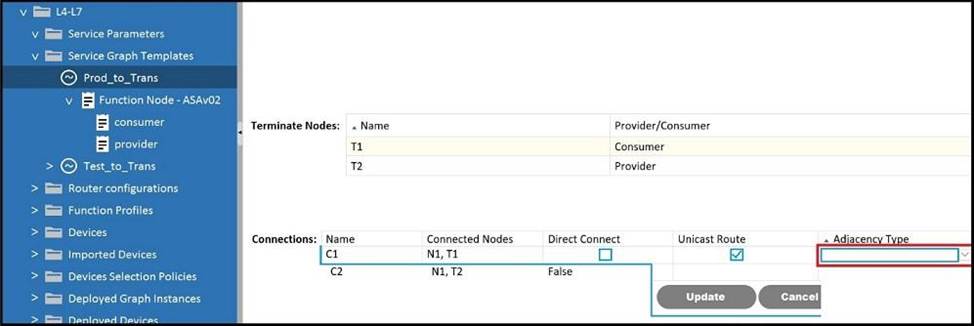
Which Adjacency Type value should be set when the client endpoint and the service node interface are in a different subnet?
- A . Routed
- B . Unicast
- C . L3Out
- D . L3
An engineer is implementing a connection that represents an external bridged network.
Which two configurations are used? (Choose two.)
- A . Layer 2 remote fabric
- B . Layer 2 outside
- C . Layers 2 internal
- D . Static path binding
- E . VXLAN outside
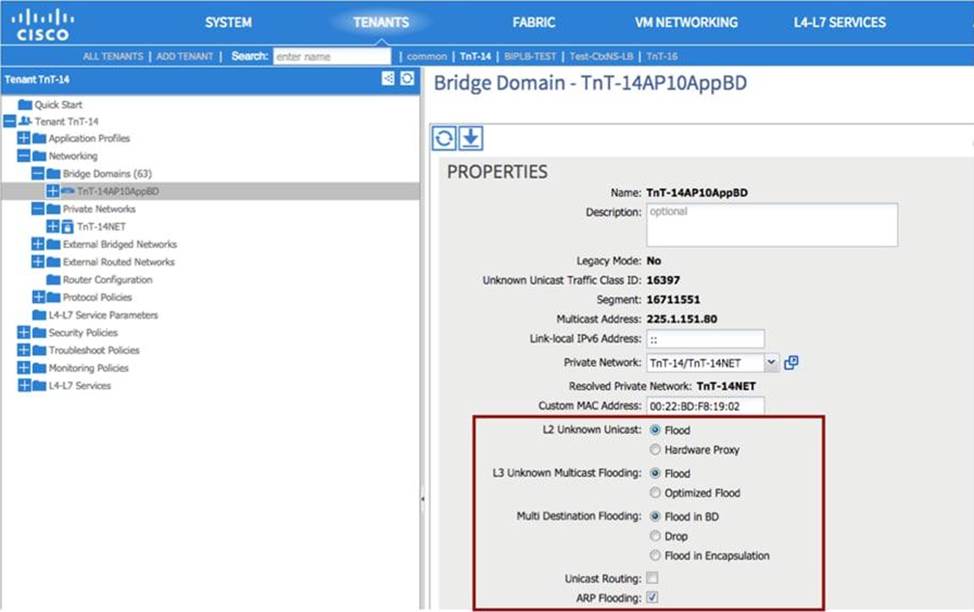
The existing network and ACI fabric have been connected to support workload migration. Servers will physically terminate at the Cisco ACI, but their gateway must stay in the existing network. The solution needs to adhere to Cisco’s best practices. The engineer started configuring the relevant Bridge Domain and needs to complete the configuration.
Which group of settings are required to meet these requirements?
- A . L2 Unknown Unicast: Hardware Proxy
L3 Unknown Multicast Flooding: Flood
Multi Destination Flooding: Flood in BD
ARP Flooding: Enable - B . L2 Unknown Unicast: Flood
L3 Unknown Multicast Flooding: Flood
Multi Destination Flooding: Flood in BD
ARP Flooding: Enable - C . L2 Unknown Unicast: Flood
L3 Unknown Multicast Flooding: Optimize Flood
Multi Destination Flooding: Flood in BD
ARP Flooding: Disable - D . L2 Unknown Unicast: Hardware Proxy
L3 Unknown Multicast Flooding: Optimize Flood
Multi Destination Flooding: Flood in BD
ARP Flooding: Disable
New ESXi hosts are procured in a data center compute expansion project. An engineer must update the configuration on the Cisco APIC controllers to support the addition of the new servers to the existing VMM domain.
Which action should be taken to support this change?
- A . Create a range of internal VLANs in the associated VLAN pool.
- B . Set the encapsulation mode as VXLAN.
- C . Enable infrastructure VLAN in the associated AEP.
- D . Map the leaf interface selector to the AEP that is associated with the VMM domain.
Refer to the exhibit.
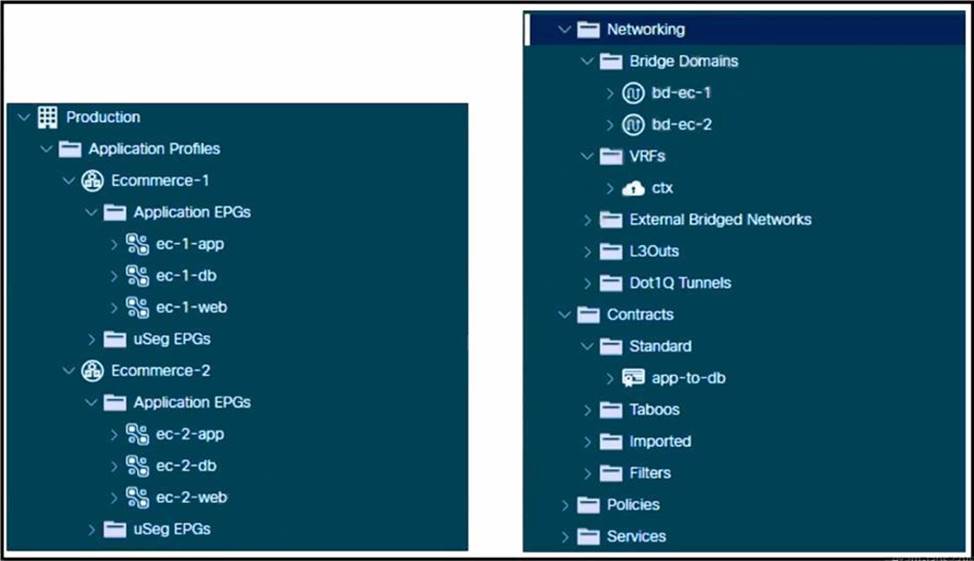
A Cisco ACI environment hosts two e-commerce applications. The default contract from a common tenant between different application tiers is used, and the applications work as expected. The customer wants to move to more specific contracts to prevent unwanted traffic between EPGs. A network administrator creates the app-to-db contract to meet this objective for the application and database tiers. The application EPGs must communicate only with their respective database EPGs.
How should this contract be configured to meet this requirement?
- A . Set the app-to-db scope to Global.
- B . Set the app-to-db scope to Application Profile.
- C . Implement the app-to-db scope as VRF.
- D . Implement the app-to-db as a Taboo contract.
Which protocol does ACI use to securely sane the configuration in a remote location?
- A . SCP
- B . HTTPS
- C . TFTP
- D . FTP
An engineer deploys a two-pod Cisco ACI Multi-Pod environment.
Why should no more than two Cisco APIC controllers be deployed in the same pod?
- A . to enable equal capacity to scale in each pod
- B . to avoid losing all replicas of a shard if a pod fails
- C . to avoid hair-pinning traffic that is destined for the primary APIC controller between pods
- D . to ensure that all nodes in all pods have local access to a controller
Which feature dynamically assigns or modifies the EPG association of virtual machines based on their attributes?
- A . vzAny contracts
- B . standard contracts
- C . application EPGs
- D . uSeg EPGs
When does the Cisco ACI leaf learn a source IP or MAC as a remote endpoint?
- A . When VXLAN traffic arrives on a leaf fabric port from the spine and outer source IP is in the Layer 3 Out EPG subnet range.
- B . When VXLAN traffic arrives on a leaf fabric port from the spine and outer source IP is in the bridge domain subnets range.
- C . When VXLAN traffic arrives on a leaf fabric port from the spine and inner source IP is in the Layer 3 Out EPG subnet range.
- D . When VXLAN traffic arrives on a leaf fabric port from the spine and inner source IP is in the bridge domain subnets range.
Latest 300-620 Dumps Valid Version with 78 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund