Cisco 300-615 Troubleshooting Cisco Data Center Infrastructure (DCIT) Online Training
Cisco 300-615 Online Training
The questions for 300-615 were last updated at Feb 01,2026.
- Exam Code: 300-615
- Exam Name: Troubleshooting Cisco Data Center Infrastructure (DCIT)
- Certification Provider: Cisco
- Latest update: Feb 01,2026
DRAG DROP
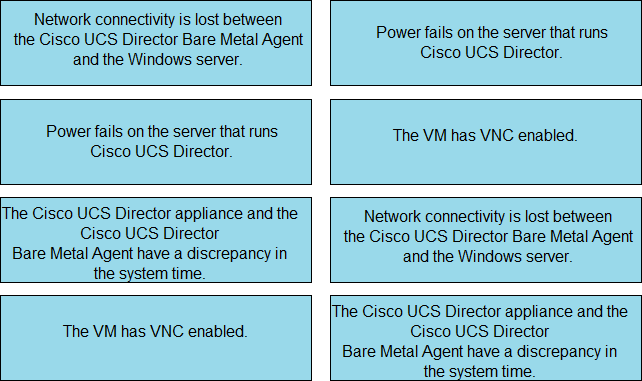
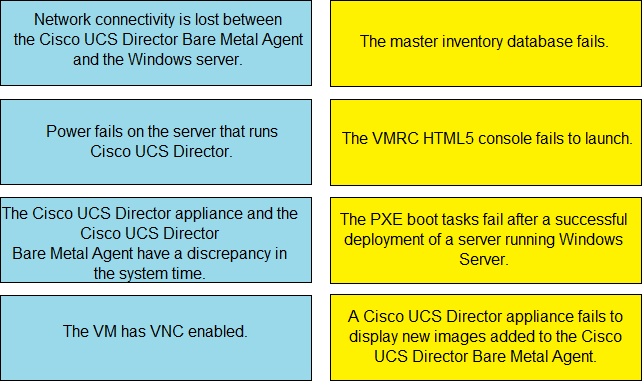
An engineer is troubleshooting issues in Cisco UCS Director.
Drag and drop the possible causes from the left onto the correct issues on the right.
Refer to the exhibit.
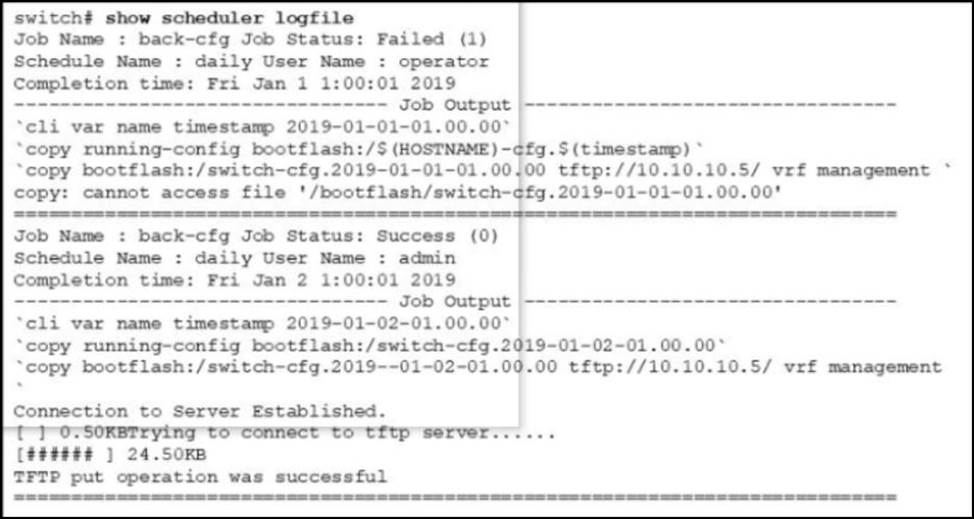
The scheduler job fails to run.
Which action resolves the issue?
- A . Change the file name.
- B . Configure the authentication credentials.
- C . Change the TFTP server address.
- D . Configure the RBAC authentication.
Refer to the exhibit.
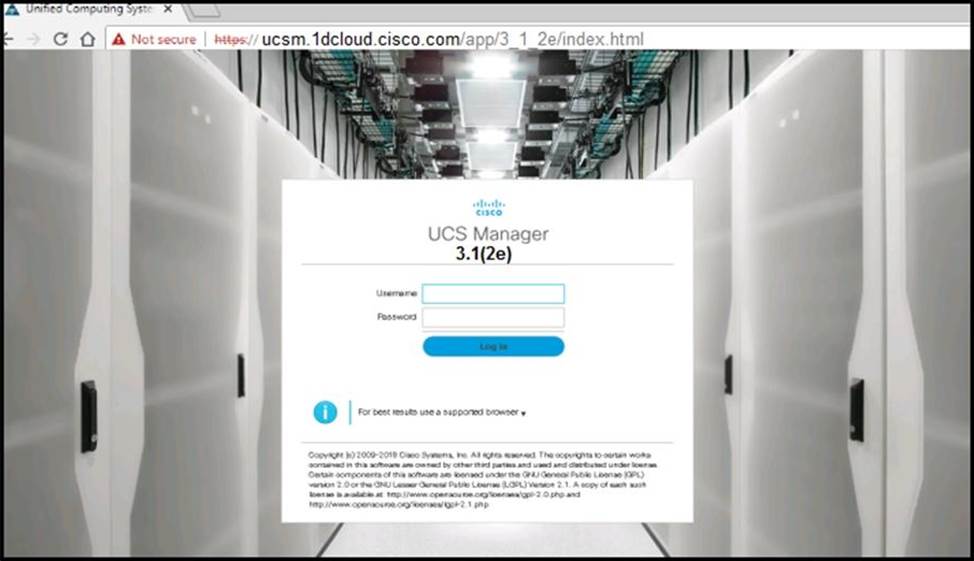
A web browser displays a “not secure” warning message when accessing the web interface of Cisco UCS Manager.
Which action resolves the issue?
- A . Load third-party certificate to UCS Manager.
- B . Use the correct TCP port for HTTPS.
- C . Use a supported web browser.
- D . Use a supported version of UCS Manager.
Refer to the exhibit.
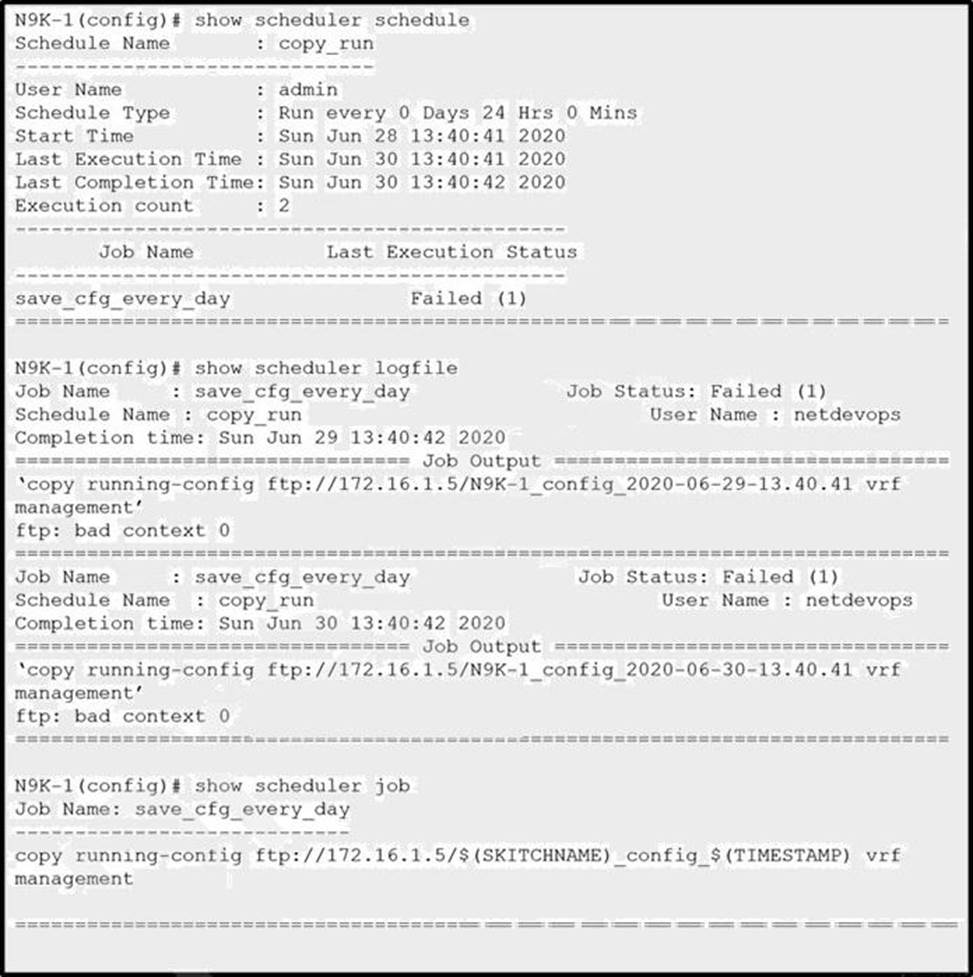
The scheduler was configured to save the running-config automatically daily. However, the scheduler is returning the error presented.
Which action resolves the issue?
- A . Reconfigure the scheduler using the admin user
- B . Use the kstack attribute for copying the configuration file
- C . Remove vrf management from the command
- D . Change the file transfer protocol to TFTP in scheduler job
A request to activate the port security database is rejected.
Which action do you perform to investigate the cause of the issue?
- A . Enable the auto-learning feature.
- B . Use the force option to identify rejected devices.
- C . Find conflicting entries between the active and configuration databases.
- D . Verify that devices are fully attached to the active database.
A request to activate the port security database is rejected.
Which action do you perform to investigate the cause of the issue?
- A . Enable the auto-learning feature.
- B . Use the force option to identify rejected devices.
- C . Find conflicting entries between the active and configuration databases.
- D . Verify that devices are fully attached to the active database.
A request to activate the port security database is rejected.
Which action do you perform to investigate the cause of the issue?
- A . Enable the auto-learning feature.
- B . Use the force option to identify rejected devices.
- C . Find conflicting entries between the active and configuration databases.
- D . Verify that devices are fully attached to the active database.
A request to activate the port security database is rejected.
Which action do you perform to investigate the cause of the issue?
- A . Enable the auto-learning feature.
- B . Use the force option to identify rejected devices.
- C . Find conflicting entries between the active and configuration databases.
- D . Verify that devices are fully attached to the active database.
A request to activate the port security database is rejected.
Which action do you perform to investigate the cause of the issue?
- A . Enable the auto-learning feature.
- B . Use the force option to identify rejected devices.
- C . Find conflicting entries between the active and configuration databases.
- D . Verify that devices are fully attached to the active database.
Enable the firmware on an adapter.
Latest 300-615 Dumps Valid Version with 95 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund