Cisco 300-610 Designing Cisco Data Center Infrastructure (DCID) Online Training
Cisco 300-610 Online Training
The questions for 300-610 were last updated at Feb 02,2026.
- Exam Code: 300-610
- Exam Name: Designing Cisco Data Center Infrastructure (DCID)
- Certification Provider: Cisco
- Latest update: Feb 02,2026
A Cisco engineer is preparing a service profile template for a design, which consists of 20 x UCS B200M6 blade servers 2 x UCS 6454 Fabric Interconnect in End Host Mode, and 3 x UCS 5108 server chassis with 2408 Fabric Extenders The blade servers are equipped with VIC 1480 adapters The engineer does not configure a vNIC/vHBA placement policy in the service profile and the vNICs and vHBAs are assigned to the vCon in a particular order What is the mapping scheme in which Cisco UCS assigns the vCons based on the type of server and the selected virtual slot?
- A . linear ordered
- B . network mesh
- C . cross match
- D . round robin
What can be implemented on Cisco Nexus 5600 Series Switches for link redundancy within
a Fibre Channel fabric?
- A . vPC+
- B . E-Trunk
- C . SAN port channel
- D . LACP port channel
An engineer is configuring a Cisco UCS Service Profile template for an environment that will host Windows servers Some of the servers require access to a Fibre Channel storage network The design requires the server HBA to send the maximum number of commands to a Fibre Channel disk using a single transmission.
Which action must be taken to meet these requirements?
- A . Set LUN Queue Depth to 240
- B . Decrease Link Down Timeout to 20.000
- C . Disable 10 Timeout Retry
- D . Increase Max Data Field Size to 2096
An engineer needs to configure multiple network devices using Ansible Device passwords must meet these requirements:
✑ be stored securely
✑ not be visible as plaintext
✑ be available to Ansible playbooks for executing scripts.
Which solution must the engineer choose?
- A . Encrypt a password variable file using Ansible Vault.
- B . Store the passwords within a Git repository Secrets Manager
- C . Encrypt passwords as Ansible environment variables
- D . Encrypt the passwords within the Ansible inventory file.
An engineer must design a DNS service available to multiple network zones as a shared service. The network zones are deployed as VRFs within the data center network and no firewall is available for communication between VRFs.
Which protocol is needed to implement the shared services?
- A . BGP
- B . OSPF
- C . ISIS
- D . VXLAN
An engineer must connect an existing Cisco Fabric Interconnect to an IP-based storage array. The connection be a channel made directly between the fabric interconnect expansion module and the storage array. The engineer must also consider that the environment is running FCoE for storage and uses QoS to prioritize traffic.
Which port type should be used to meet these requirements?
- A . Network
- B . Uplink
- C . Appliance
- D . server
A customer requires a tool to manage Cisco network hardware. The solution must use secure communication using a secure network protocol, support the use of declarative language to manage the state of resources, and periodically pull changes to the controlled nodes.
Which tool meets these requirements?
- A . Ansible
- B . SaltStack
- C . Puppet
- D . Nomir
A Cisco engineer is configuring MPLS VPN BGP at a customer site that is connected to the provider site by more than one path MPLS VPN BGP Local Convergence link protection is enabled. After the engineer installs the main forwarding path and the redundant backup path within the BGP, they assign a unique route distinguisher to each VRF table on all PE devices that serve as a backup to the link.
What is a prerequisite for this local convergence to work?
- A . Interautonomous system option A (back-to-back VRF) is active.
- B . BGP must support lossless switchover between operational paths
- C . IP/GRE is enabled.
- D . The system is performing a PE-CE link protection on both ends
Which two methods mitigate congestion in a SAN network? (Choose two.)
- A . Configure ER_RDY to allow splitting of each ISL between switches into separate virtual links.
- B . Use the port-monitor command to detect slow drain devices.
- C . Configure the port channel to enable individual buffer-to-buffer credits.
- D . Configure the port monitor to allow categorization of a specific device as slow.
- E . Configure the flow control for the FC to use R_RDY.
Refer to the exhibit.
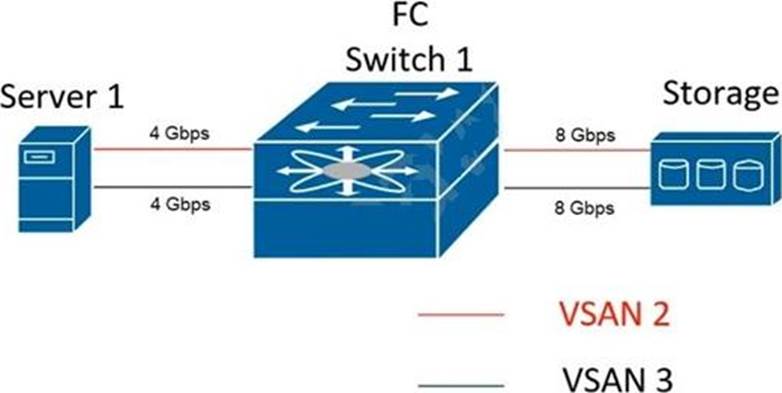
Server 1 fails to connect to the storage array over the Storage Area Network (SAN) of the Cisco NDS 9000 Series Switch.
The requirements are to redesign the storage network and keep these considerations in mind:
✑ The traffic from each of the server must be redundant and isolated.
✑ The design must tolerate hardware and software failures and upgrades of SAN fabric devices.
Which action must be taken to meet these requirements?
- A . Enable NPV and F-Port-channel on ports that face Server 1 on the Fibre Channel switch to create redundant paths.
- B . Create a SAN port channel that faces the storage device to sustain a link failure.
- C . Add an additional supervisor to the Fibre Channel switch to support nondisruptive upgrades.
- D . Place an additional Fibre Channel switch to create two physically independent storage fabrics.
Latest 300-610 Dumps Valid Version with 110 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund