Cisco 300-415 Implementing Cisco SD-WAN Solutions (ENSDWI) Online Training
Cisco 300-415 Online Training
The questions for 300-415 were last updated at Jan 18,2026.
- Exam Code: 300-415
- Exam Name: Implementing Cisco SD-WAN Solutions (ENSDWI)
- Certification Provider: Cisco
- Latest update: Jan 18,2026
What is the purpose of ‘’vpn 0’’ in the configuration template when onboarding a WAN edge node?
- A . It carries control traffic over secure DTLS or TLS connections between vSmart controllers and vEdge routers, and between vSmart and vBond
- B . It carries control out-of-band network management traffic among the Viptela devices in the overlay network.
- C . It carries control traffic over secure IPsec connections between vSmart controllers and vEdge routers, and between vSmart and vManager
- D . It carries control traffic over secure IPsec connections between vSmart controllers and vEdge routers, and between vSmart and vBond
Which device in the SD- WAN solution receives and categorizes event reports, and generates alarms?
- A . WAN Edge routers
- B . vSmart controllers
- C . vManage NMS
- D . vBond controllers
A network administrator is bringing up one WAN Edge for branch connectivity.
Which types of tunnels form when the WAN edge router connects to the SD-WAN fabric?
- A . DTLS or TLS tunnel with vBond controller and IPsec tunnel with vManage controller.
- B . DTLS or TLS tunnel with vBond controller and IPsec tunnel with other WAN Edge routers.
- C . DTLS or TLS tunnel with vSmart controller and IPsec tunnel with other Edge routers.
- D . DTLS or TLS tunnel with vSmart controller and IPsec tunnel with vBond controller.
When a WAN Edge device joins the SD-WAN overlay, which Cisco SD-WAN components orchestrates the connection between the WAN Edge device and a vSmart controller?
- A . vManage
- B . vBond
- C . OMP
- D . APIC-EM
An administrator needs to configure SD-WAN to divert traffic from the company’s private network to an ISP network.
What action should be taken to accomplish this goal?
- A . configure the control policy
- B . configure the data policy
- C . configure the data security policy
- D . configure the application aware policy
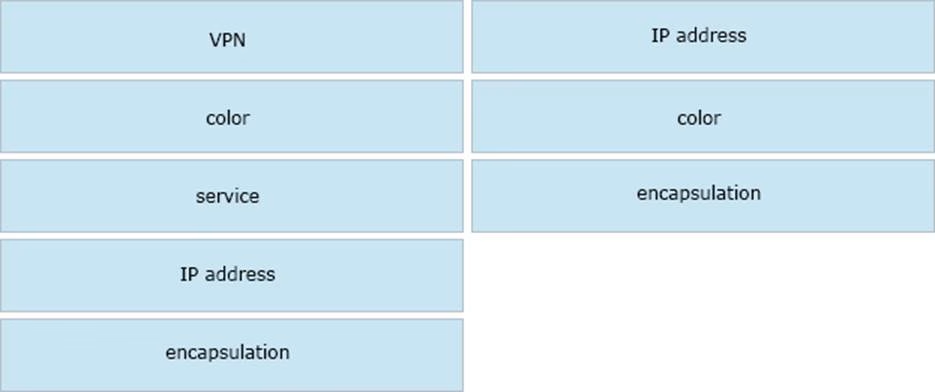
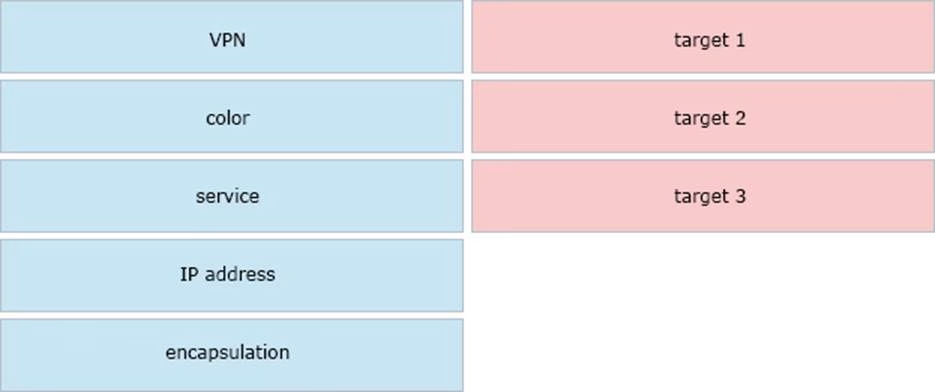
DRAG DROP
Drag and drop the attributes from the left that make each transport location unique onto the right. Not all options are used.
Refer to the exhibit.
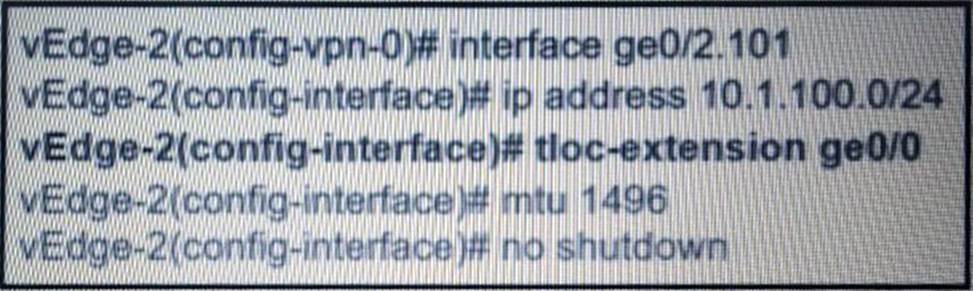
What binding is created using the tloc-extension command?
- A . between ge 0/2.101 of port-type service and ge 0/0 of port-type service
- B . between ge 0/2.101 of port-type transport and ge 0/0 of port-type service
- C . between ge 0/2.101 of port-type service and ge 0/0 of port-type transport
- D . between ge 0/2.101 of port-type transport and ge 0/0 of port-type transport
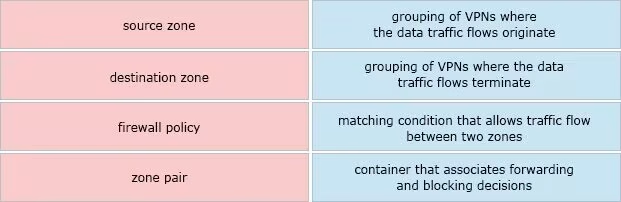
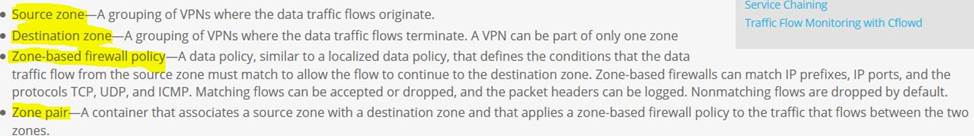
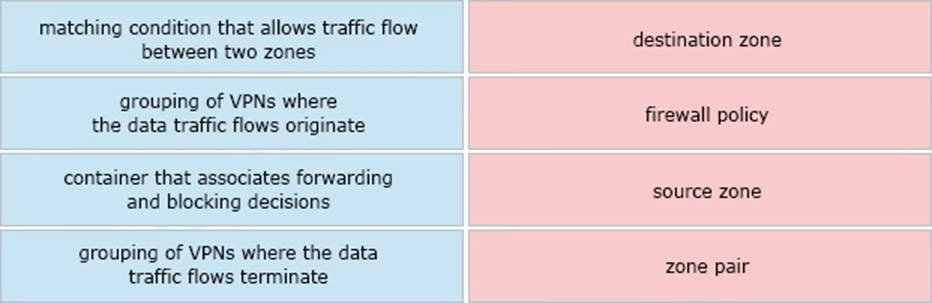
DRAG DROP
Drag and drop the definitions from the left to the configuration on the right.
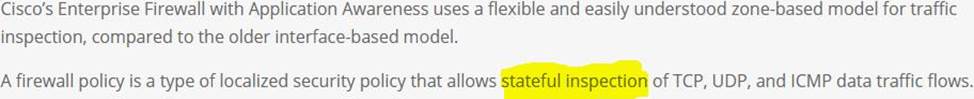
A network administrator is configuring an application-aware firewall between inside zones to an outside zone on a WAN edge router using vManage GUI.
What kind of Inspection is performed when the ‘’inspect’’ action is used?
- A . stateful inspection for TCP and UDP
- B . stateful inspection for TCP and stateless inspection of UDP
- C . IPS inspection for TCP and-Layer 4 inspection for UDP
- D . Layer 7 inspection for TCP and Layer 4 inspection for UDP
An engineer wants to track tunnel characteristics within an SLA-based policy for convergence.
Which policy configuration will achieve this goal?
- A . App-route policy
- B . VPN membership policy
- C . Control policy
- D . Data policy
Latest 300-415 Dumps Valid Version with 151 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund