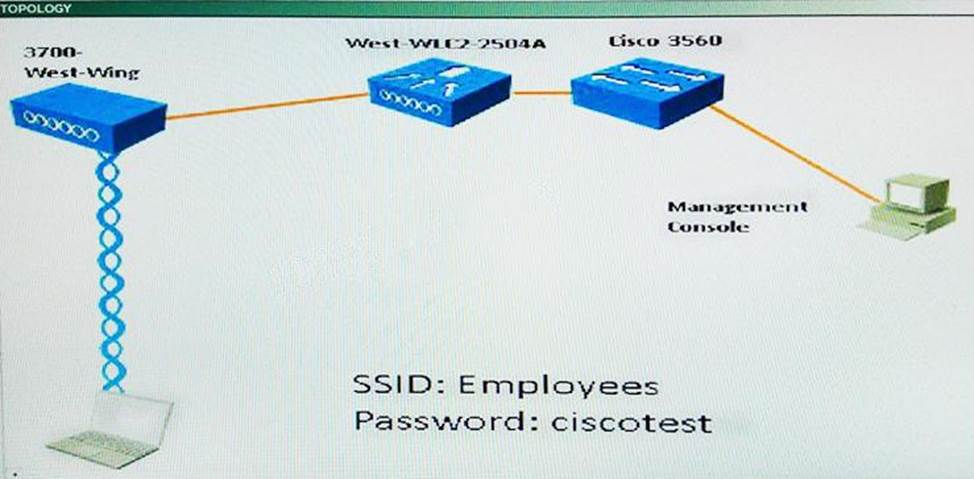
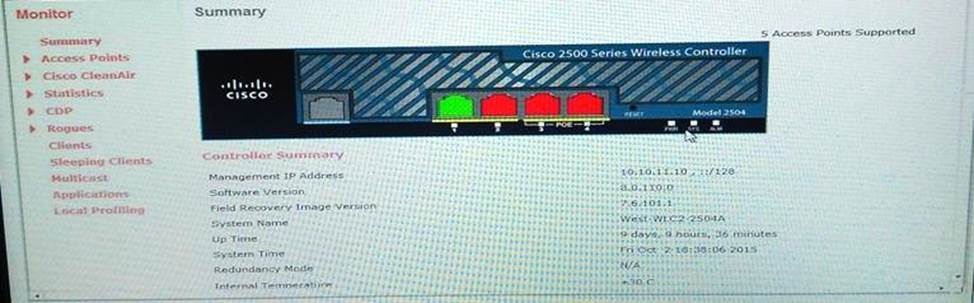
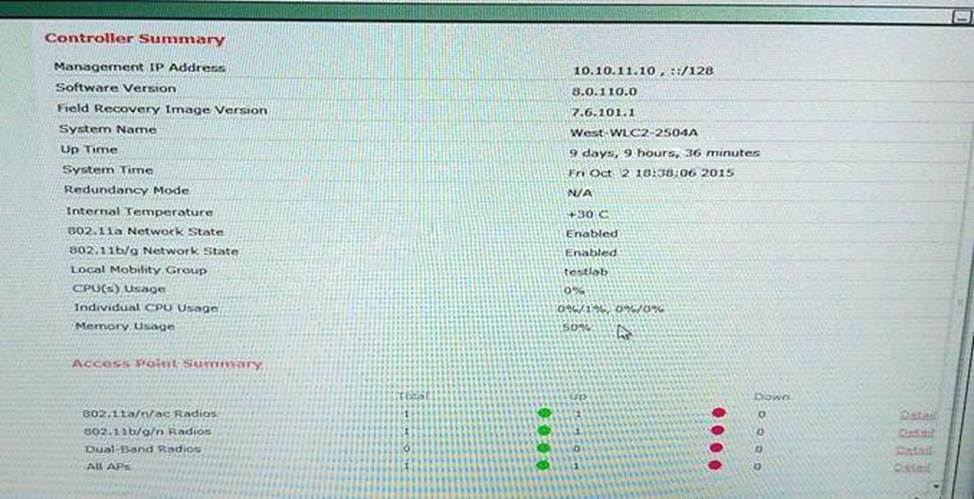
Cisco 300-375 Securing Wireless Enterprise Networks Online Training
Cisco 300-375 Online Training
The questions for 300-375 were last updated at Feb 02,2026.
- Exam Code: 300-375
- Exam Name: Securing Wireless Enterprise Networks
- Certification Provider: Cisco
- Latest update: Feb 02,2026
An engineer requires authentication for WPA2 that will use fast rekeying to enable clients to roam from one access point to another without going through the controller.
Which security option should be configured?
- A . PSK
- B . AES
- C . Cisco Centralized key Management
- D . 802.1x
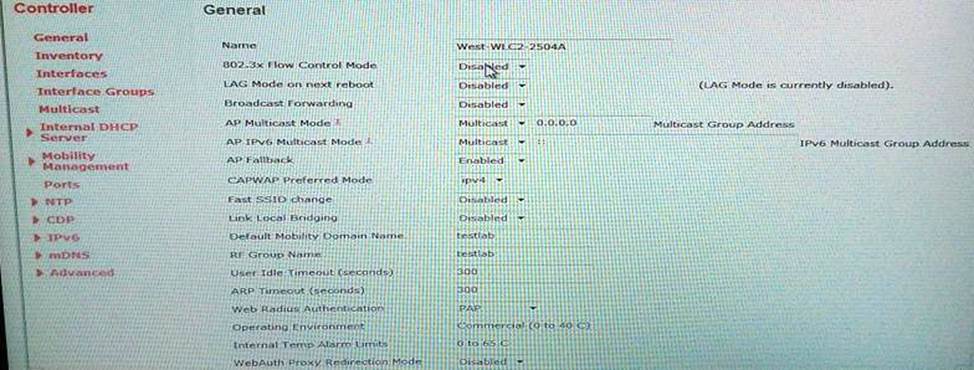
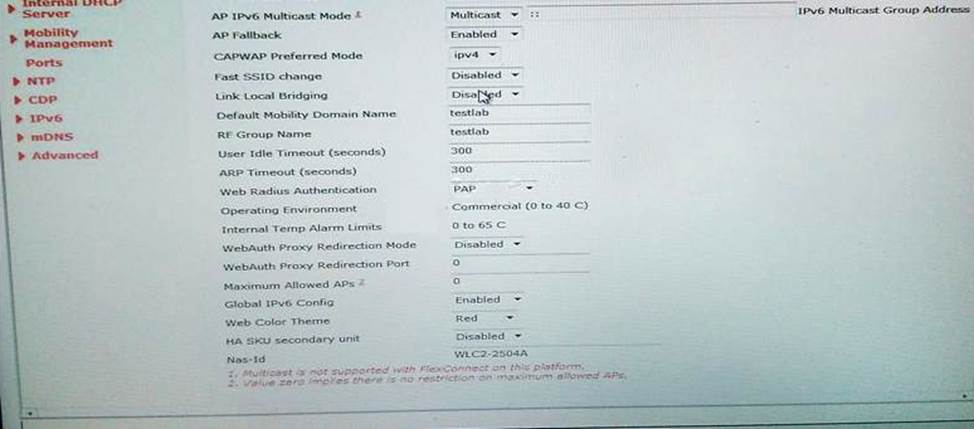
Refer to the exhibit.
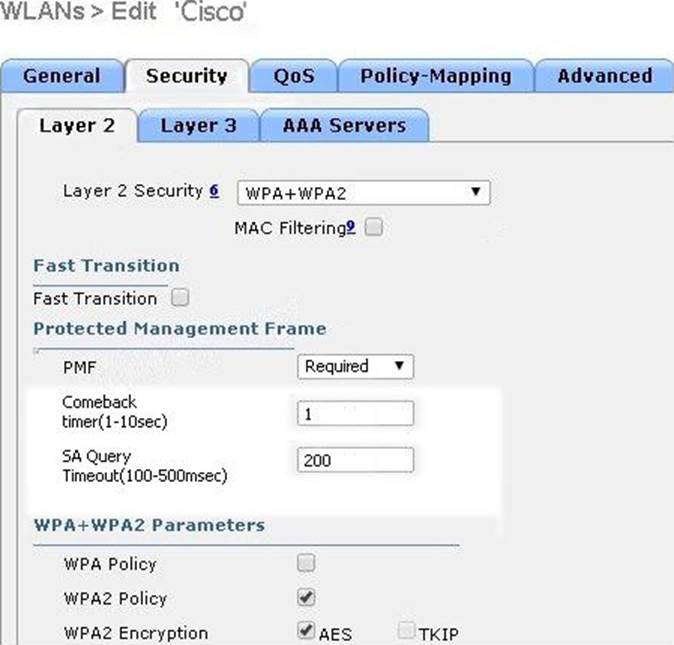
A customer is having problems with clients associating to me wireless network.
Based on the configuration, which option describes the most likely cause of the issue?
- A . Both AES and TKIP must be enabled
- B . SA Query Timeout is set too low
- C . Comeback timer is set too low
- D . PME is set to "required"
- E . MAC Filtering must be enabled
Which Cisco feature must an engineer configure on a cisco WLC to enable PCI specification compliance for communication of neighbor radio information?
- A . RF Grouping
- B . MFP
- C . Rogue Access Point Detection
- D . RRM NDP
- E . Off Channel Scanning
MFP is enabled globally on a WLAN with default settings on single controller wireless network. Older client devices are disconnected from the network during a deauthentication attack.
What is the cause of this issue?
- A . The client devices do not support WPA.
- B . The client devices do not support CCXv5.
- C . The MFP on the WLAN is set to optional
- D . The NTP server is not configured on the controller.
An engineer must enable EAP on a new WLAN and is ensuring that the necessary components are available.
Which component uses EAP and 802.1x to pass user authentication to the authenticator?
- A . AP
- B . AAA server
- C . supplicant
- D . controller
Which three configuration steps are necessary on the WLC when implementing central web authentication in conjunction with Cisco ISE. (Choose three.)
- A . Set P2P Blocking Action to Drop.
- B . Enable Security Layer 3 Web Policy.
- C . Set NAC state to SNMP NAC.
- D . Enable Allow AAA override.
- E . Enable Security Layer 2 MAC Filtering.
- F . Set NAC state to RADIUS NAC.
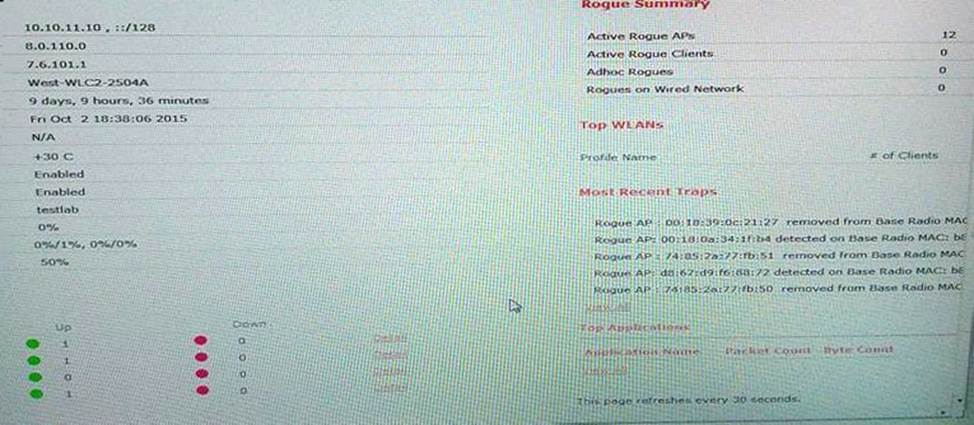
Refer to the exhibit.
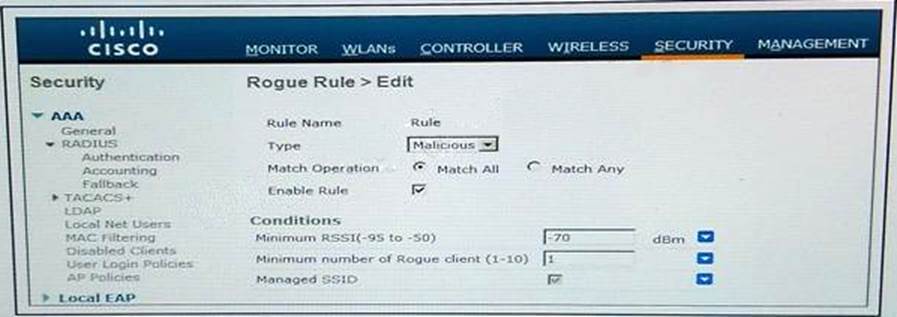
A WLAN with the SSID "Enterprise" is configured.
Which rogue is marked as malicious?
- A . a rogue with two clients, broadcasting the SSID "Employee" heard at -50 dBm
- B . a rogue with no clients, broadcasting the SSID "Enterprise" heard at -50 dBm
- C . a rouge with two clients, broadcasting the SSID "Enterprise" heard at -80 dBm
- D . a rogue with two clients, broadcasting the SSID "Enterprise" heard at -50 dBm
Which option describes the purpose of configuring switch peer groups?
- A . enforces RF profiles
- B . enables location services
- C . restricts roaming traffic to certain switches
- D . allows template based configuration changes
Which of the following user roles can access CMX Visitor Connect?
- A . Administrator
- B . Power User
- C . Guest User
- D . Super Administrator
Latest 300-375 Dumps Valid Version with 147 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund