Cisco 300-209 Implementing Cisco Secure Mobility Solutions Online Training
Cisco 300-209 Online Training
The questions for 300-209 were last updated at Feb 27,2026.
- Exam Code: 300-209
- Exam Name: Implementing Cisco Secure Mobility Solutions
- Certification Provider: Cisco
- Latest update: Feb 27,2026
Refer to the exhibit.
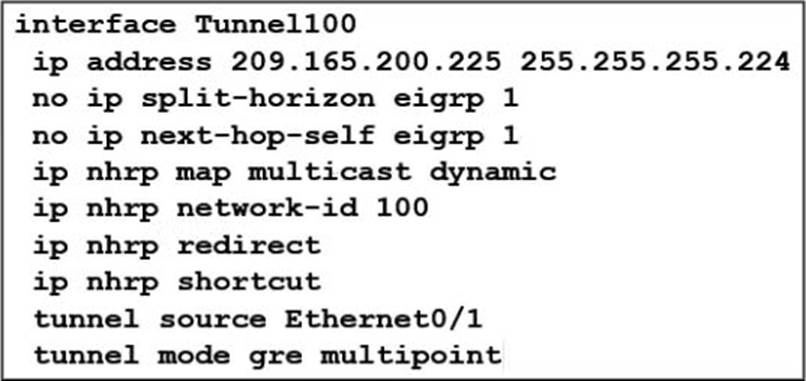
You implement a DMVPN Phase 3 full-mesh design. Spoke-to-spoke tunnels fail to establish successfully via the hub.
Which action do you take in the hub configuration to resolve the issue?
- A . Configure the hub to set itself as the next hop in the routing updates to the spokes.
- B . Configure the hub tunnel as a point-to-point GRE tunnel interface.
- C . Enable split horizon for EIGRP
- D . Configure a loopback interface as the source of the tunnel interface
Refer to the exhibit.
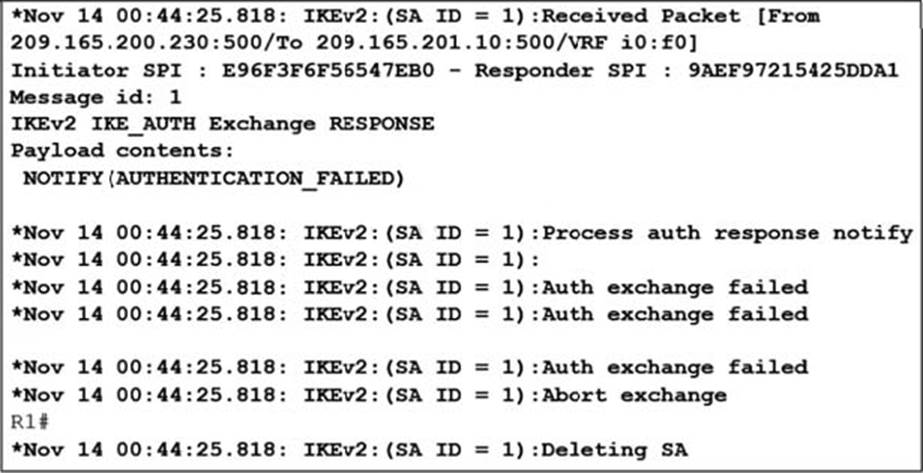
You are implementing an IKEv2 IPsec tunnel between two Internet routers by using PSKs. After the configuration is complete, the IPsec VPN tunnel fails to negotiate. You enable debugging to troubleshoot the issue.Which action do you take to resolve the issue?
- A . Verify the IKEv2 keyring address and PSK configuration on both routers.
- B . Configure an IKEv2 authorization policy to authorize the peer router.
- C . Configure the IKEv2 identity of each router by using an email address.
- D . Modify the Diffie-Hellman key used in the IKEv2 policy.
You must implement DMVPN Phase 3 by using EIGRP as the dynamic routing protocol for the tunnel overlay.
Which action do you take to allow EIGRP to advertise all routes between the hub and all the spokes?
- A . Summarize routes from the hub to the spokes.
- B . Disable split-horizon for EIGRP on the hub.
- C . Configure the hub to set itself as the next hop when advertising networks to the spoke.
- D . Add a distribute list to permit the spoke subnets and deny all other networks.
When a Cisco ASA is configured for Active/Standby failover, what is replicated between the devices?
- A . HostScan images
- B . Cisco AnyConnect profiles
- C . VPN sessions
- D . Cisco AnyConnect images
Refer to the exhibit.
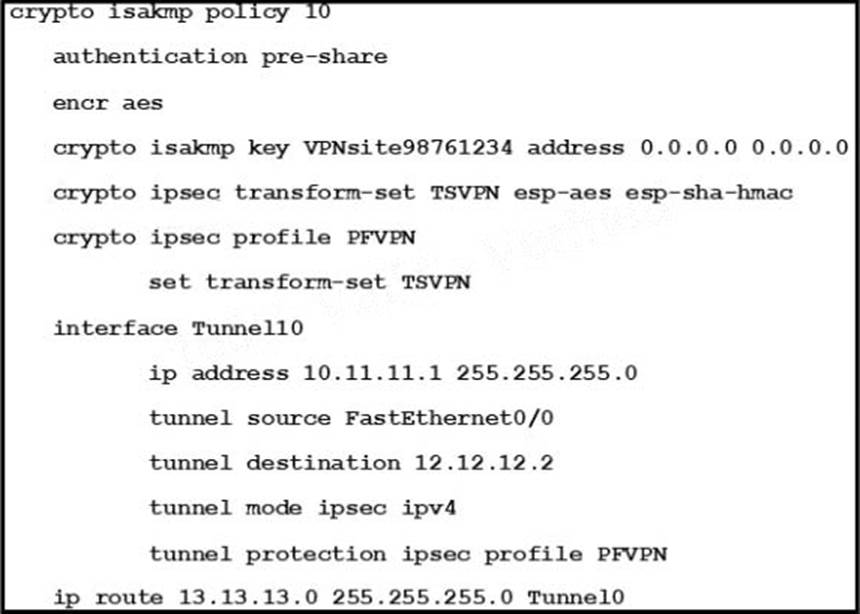
Which VPN technology produces this configuration output?
- A . DVTI
- B . SVTI
- C . DMVPN
- D . FlexVPN
When configuring a FlexVPN, which two components must be configured for IKEv2? (Choose two.)
- A . persistence
- B . profile
- C . proposal
- D . preference
- E . method
Refer to the exhibit.
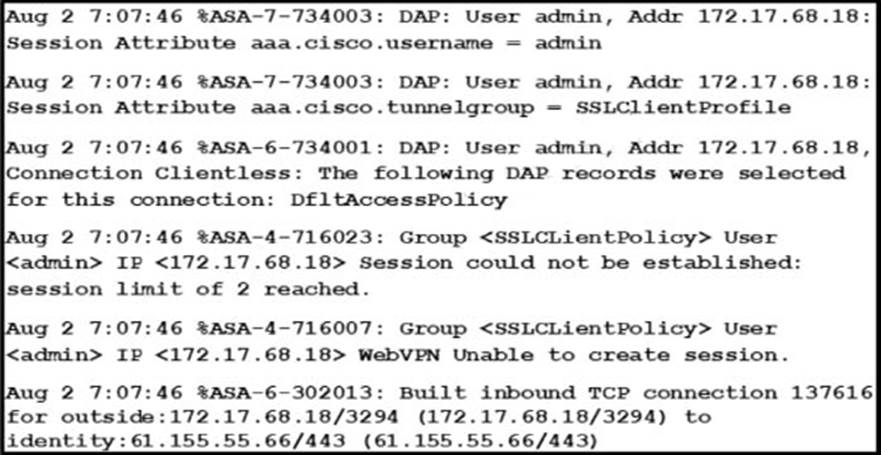
You configure Clientless SSL VPN on a Cisco ASA. Users from Company A cannot connect to the Clientless SSL VPN.
Which possible cause of the connection failure is most likely?
- A . The users have authentication issues
- B . The users are behind the same NAT IP address
- C . An ACL for DAP is blocking the users
- D . The license limit is exceeded
Refer to the exhibit.
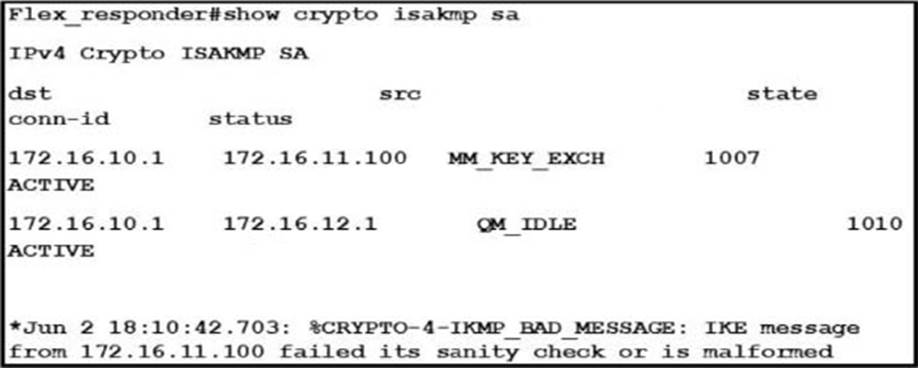
You are configuring FlexVPN on a router. The tunnel fails to come up.
Which type of mismatch is the root cause of the failure?
- A . access list
- B . peer ID
- C . preshared key
- D . transform proposal
When using Clientless SSL VPN on a Cisco ASA, which authentication method is required for single sign-on?
- A . TACACS
- B . LOCAL
- C . RADIUS
- D . SAML 2.0
Which VPN solution enables you to publish applications to users by using bookmarks?
- A . IPsec client
- B . SSL VPN full network access
- C . Clientless SSL VPN
- D . port forward
Latest 300-209 Dumps Valid Version with 394 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

