Cisco 300-206 Implementing Cisco Edge Network Security Solutions Online Training
Cisco 300-206 Online Training
The questions for 300-206 were last updated at Feb 28,2026.
- Exam Code: 300-206
- Exam Name: Implementing Cisco Edge Network Security Solutions
- Certification Provider: Cisco
- Latest update: Feb 28,2026
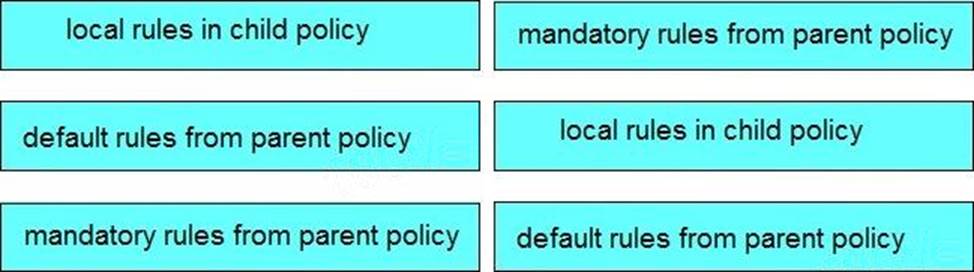
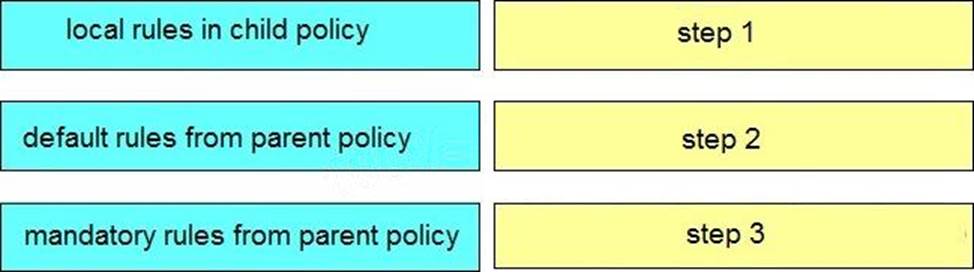
DRAG DROP
Drag and drop the steps on the left into the correct order of Cisco Security Manager rules when using inheritance on the right.
Which Cisco ASA command authenticates the Cisco ASDM client that accesses the security appliance using HTTPS with local user database?
- A . aaa authentication ssh console LOCAL
- B . aaa authentication serial console LOCAL
- C . aaa authentication telnet console LOCAL
- D . aaa authentication http console LOCAL
An engineer is applying best practices to step STP unauthorized changes from the user port.
Which two actions help to accomplish this task? (Choose two.)
- A . configure RSTP.
- B . enable STP Guard.
- C . disable STP
- D . enable BPDU Guard.
- E . enable Root Guard.
An engineer is configuring MACsec encryption.
Which two components does Cisco TrustSec NDAC MACsec support? (Choose two.)
- A . user-facing downlink port
- B . switch-to-switch connection
- C . switch-to-host connection
- D . host-facing links
- E . switch ports connected to other switches
An engineer is configuring control-plane protocol queue thresholding.
For which protocol can the engineer set queue limits?
- A . CDP
- B . ARP
- C . IPX
- D . BGP
An enterprise has enforced DHCP snooping on the enterprise switches. In which two cases does the switch drop a DHCP packet? (Choose two.)
- A . A packet is received on an untrusted interface, and the source MAC address and the DHCP
client hardware address match. - B . A DHCP relay agent forwards a DHCP packet that includes a 0.0.0.0 relay-agent IP address.
- C . The switch receives a DHCPRELEASE broadcast message that has a MAC address in the DHCP snooping binding database, and the interface information in the binding database matches the interface on which the message was received.
- D . A packet is received on an untrusted interface, and the source MAC address and the DHCP client hardware address do not match.
- E . A packet from a DHCP server, such as a DHCPOFFER or DHCPLEASEQUERY packet, is received from outside the network or firewall.
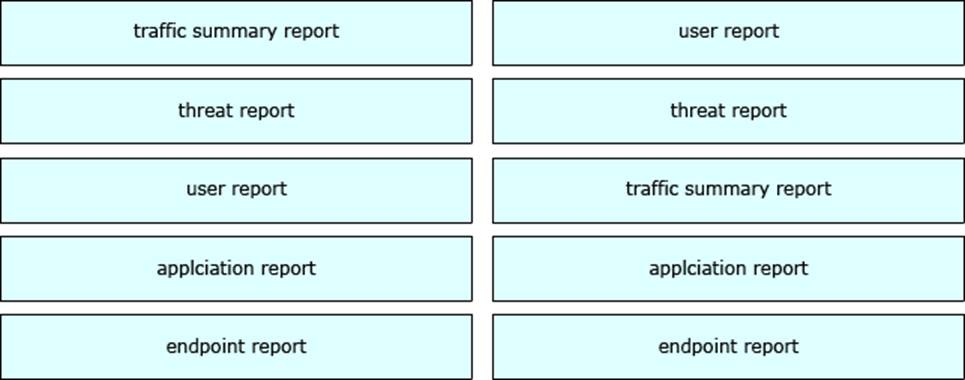
DRAG DROP
Drag and drop the Cisco Prime Security Manager available reports on the left onto the correct report examples on the right.

A web server has been configured to operate on port 1521. The web server traffic is passing through an ASA with default application inspection configured.
Which application inspection affects the web server traffic?
- A . HTTP
- B . MSCP
- C . HTTPS
- D . SQL *Net
Which two options can be used when configuring a packet capture from the command line within the ASA using the capture command? (Choose two.)
- A . host
- B . snap-length
- C . type
- D . detail
- E . real-time
An engineer is examining the configuration of an IOS device and notices that though SSH is configured properly, the ip ssh version 2 command is not explicitly configured.
How does the device behave in regards to SSH connections?
- A . only SSHv2 is allowed.
- B . SSHv1 and SSHv2 are denied.
- C . SSHv1 and SSHv2 are allowed.
- D . only SSHv1 is allowed.
Latest 300-206 Dumps Valid Version with 376 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund