Cisco 300-206 Implementing Cisco Edge Network Security Solutions Online Training
Cisco 300-206 Online Training
The questions for 300-206 were last updated at Feb 28,2026.
- Exam Code: 300-206
- Exam Name: Implementing Cisco Edge Network Security Solutions
- Certification Provider: Cisco
- Latest update: Feb 28,2026
Refer to the exhibit.
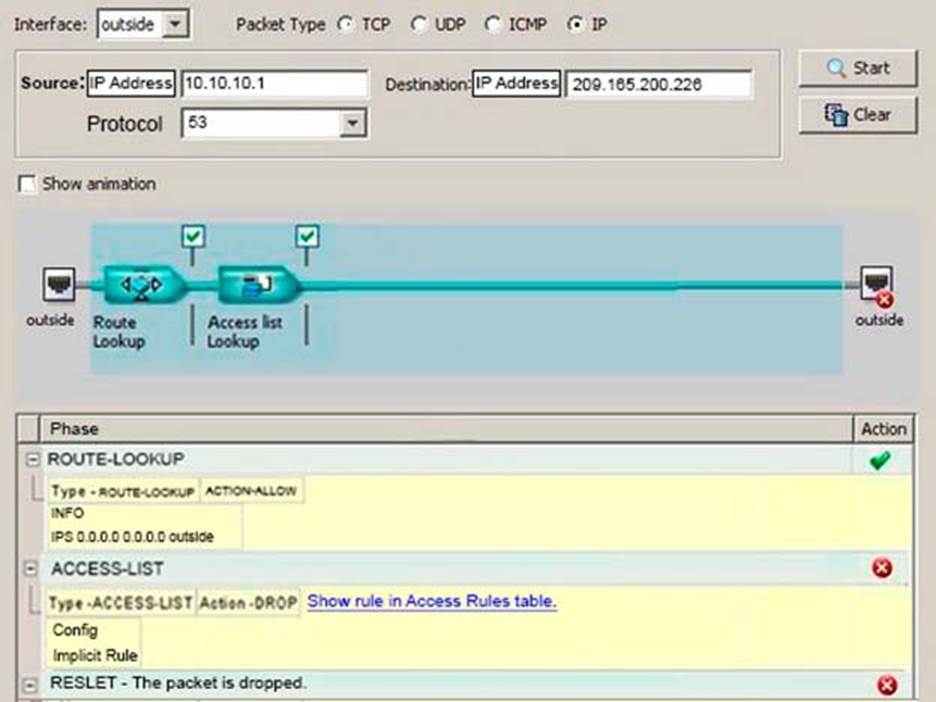
The security engineer is troubleshooting internal access to the public DNS server at 209.165.200.226.
Which description of the issue is true?
- A . The routes of the Cisco ASA are incorrectly identifying traffic from 10.10.10.1 on the outside interface of the firewall.
- B . To accurately test DNS, the packet tracer should be run using packet type UDP and destination port 53.
- C . To allow DNS, a rule specifically allowing the DNS access must be added in the rule base.
- D . The engineer must verify the NAT rules of the firewall to ensure that correct NATing is taking place.
An engineer is using Cisco Security Manager and is using default ports configuration.
What port must be open to connect the Cisco Security Manager Client to an ASA?
- A . 22
- B . 23
- C . 80
- D . 443
Which command must be used to implement the unicast RPF feature on a Cisco ASA device?
- A . ip verify source port-security
- B . ip source-route
- C . ip verify unicast reverse-path
- D . ip verify reverse-path interface <interface name>
Refer to the exhibit.
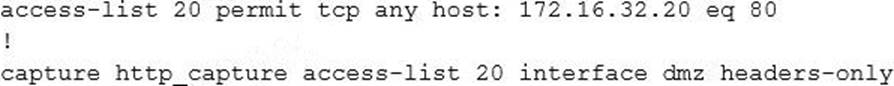
A network engineer applies the configuration shown to set up a capture on a Cisco Adaptive Security Appliance. When attempting to start a capture, this error message is observed:
ERROR: Capture doesn’t support access-list <20> containing mixed policies
For which two reasons does this error message occur? (Choose two.)
- A . The ACL number is incorrect.
- B . Access list type is incorrect.
- C . IPv6 is enabled on the Cisco ASA.
- D . A named ACL is required.
- E . IPv6 is not specified on the access list with “any4” keyword.
What is the maximum number of servers configurable in a Cisco Prime Infrastructure high availability
implementation?
- A . 2 servers
- B . 4 servers
- C . 8 servers
- D . 16 servers
An enterprise is hosting an application that opens a secondary UDP point. The initial session on a well-known port is used to negotiate the secondary dynamically assigned port.
Which feature on Cisco ASA monitors sessions to identify the dynamic port assignments and permits sata exchange on these ports?
- A . Allow Any
- B . NAT
- C . Protocol Inspection
- D . High & Low Security level
An engineer must secure a current monitoring environment by using the strongest encryption allowed within SNMPv3 configuration.
Which two encryption methods meet this requirement? (Choose two.)
- A . 3DES
- B . AES
- C . RSA-SIG
- D . DES
- E . MD5
Refer to the exhibit.
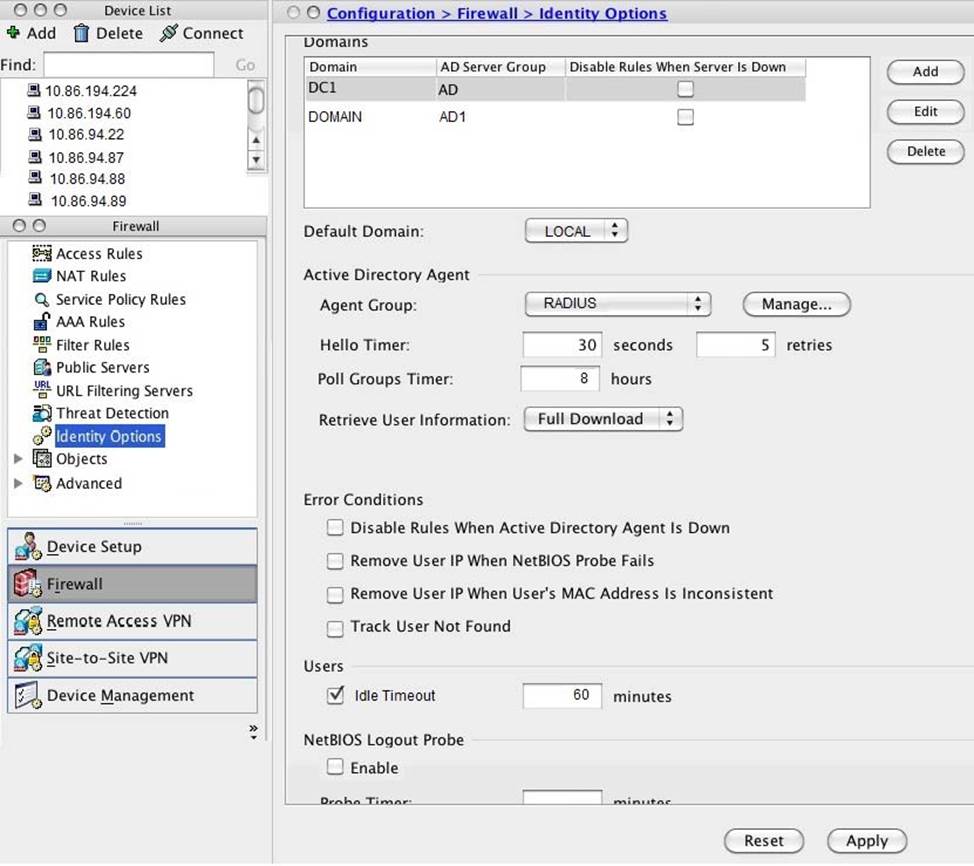
An engineer has configured identify options on an ASA using ASDM.
Which domain is used for a user who does not have an explicitly configured domain?
- A . DOMAIN1
- B . PIXTEST
- C . NetBIOS domain name configured on the Active Directory domain controller
- D . LOCAL domain name for all locally defined users and groups
Which type of traffic would make use of the ASA’s default route while running in transparent mode?
- A . untrusted traffic
- B . NAT traffic
- C . encrypted traffic
- D . management traffic
- E . Internet traffic
With the crypto key generate rsa command, how many bits minimum must the RSA key size be to enable SSH2 on a router?
- A . 512 bits
- B . 768 bits
- C . 1024 bits
- D . 2048 bits
Latest 300-206 Dumps Valid Version with 376 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

