Cisco 210-260 Implementing Cisco Network Security Online Training
Cisco 210-260 Online Training
The questions for 210-260 were last updated at Feb 23,2026.
- Exam Code: 210-260
- Exam Name: Implementing Cisco Network Security
- Certification Provider: Cisco
- Latest update: Feb 23,2026
CORRECT TEXT
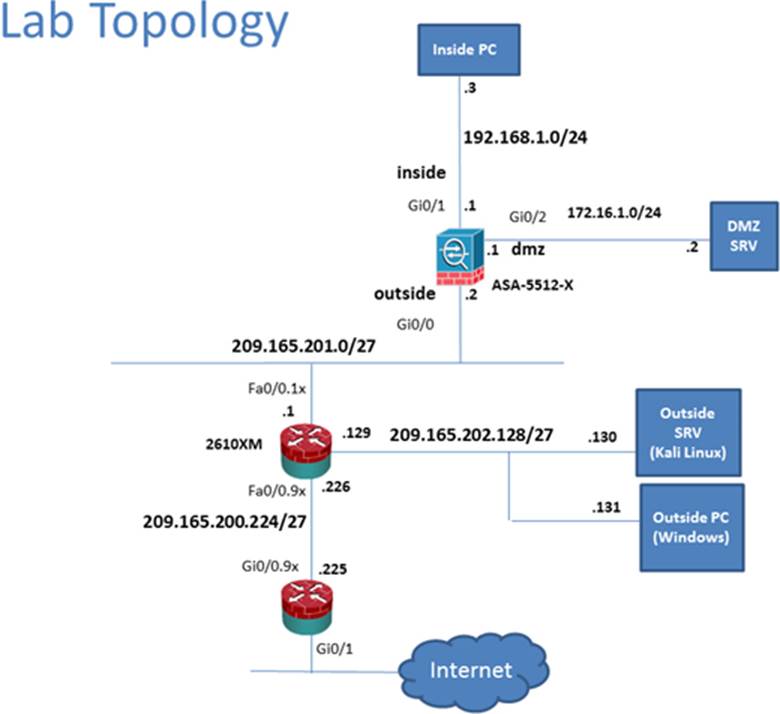
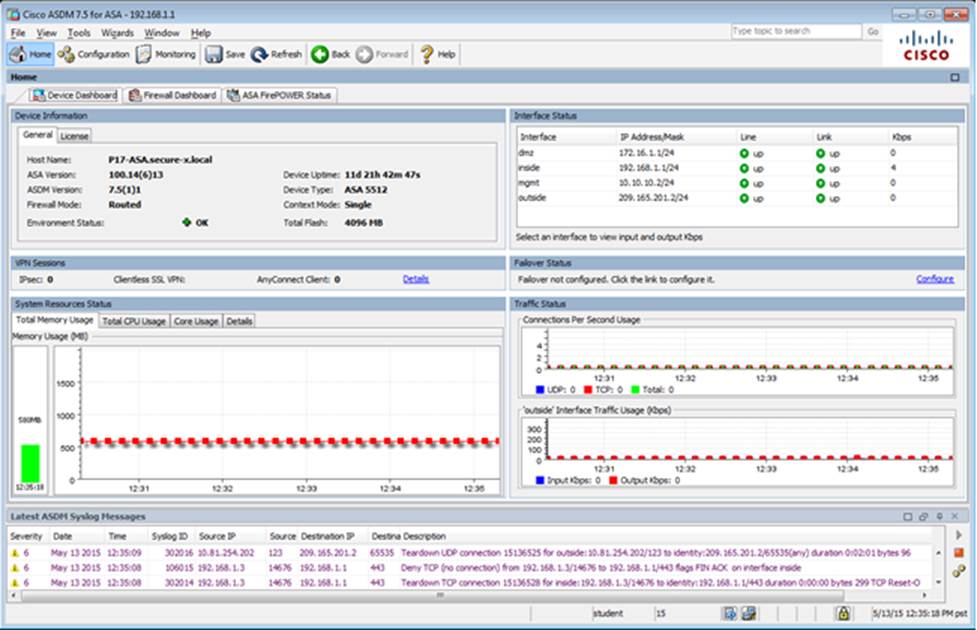
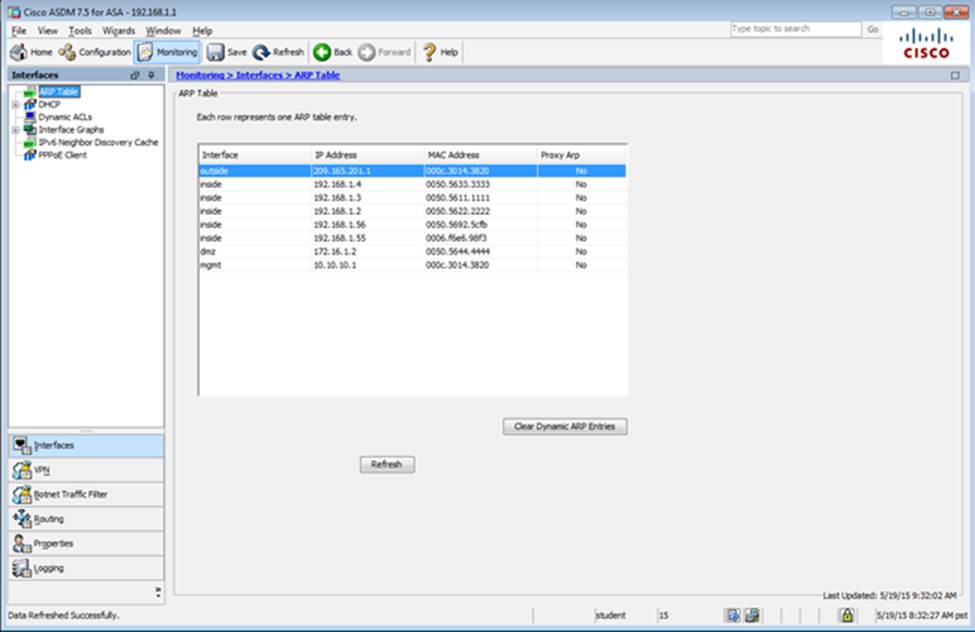
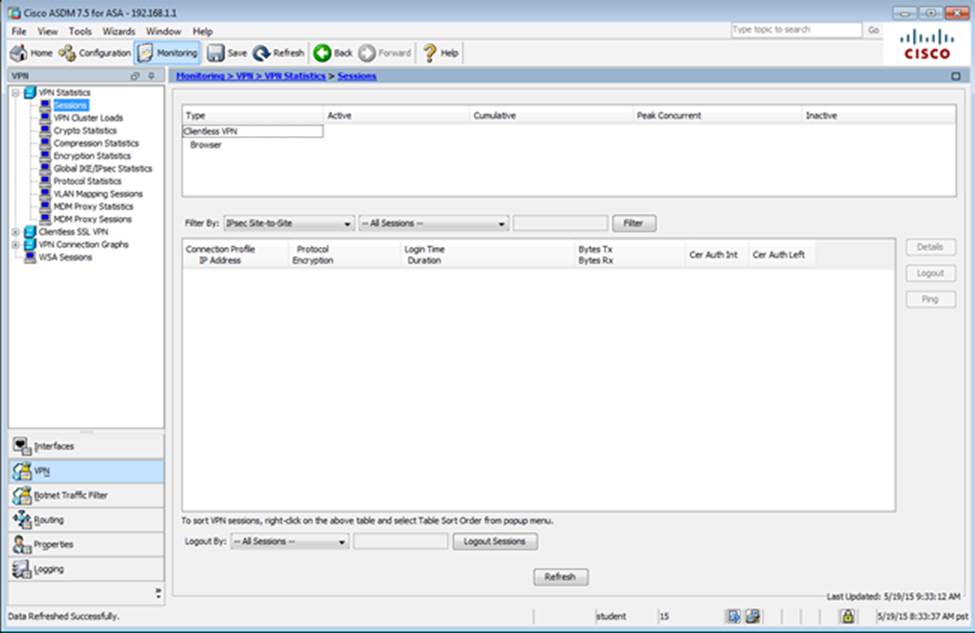
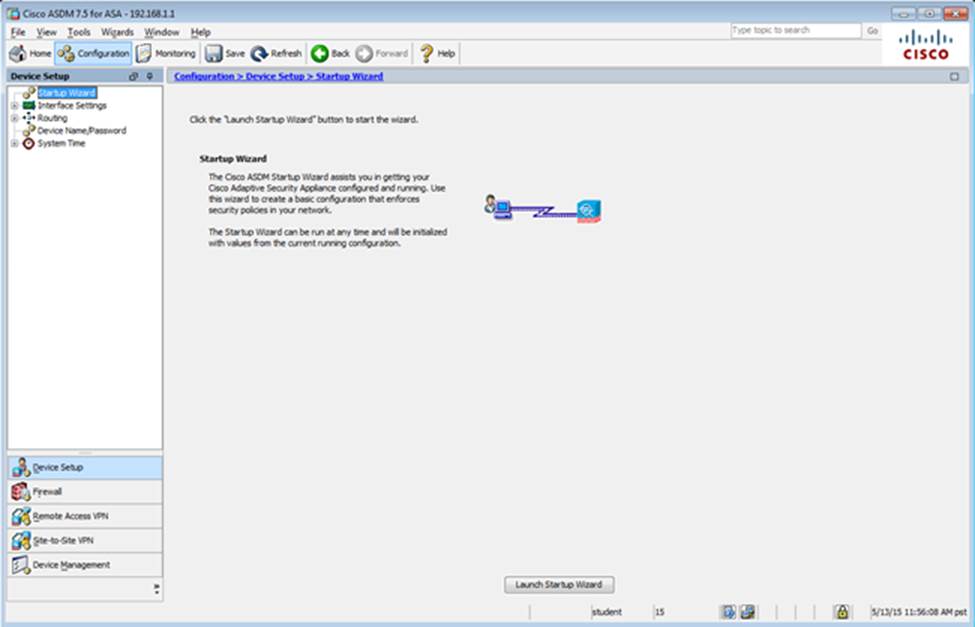
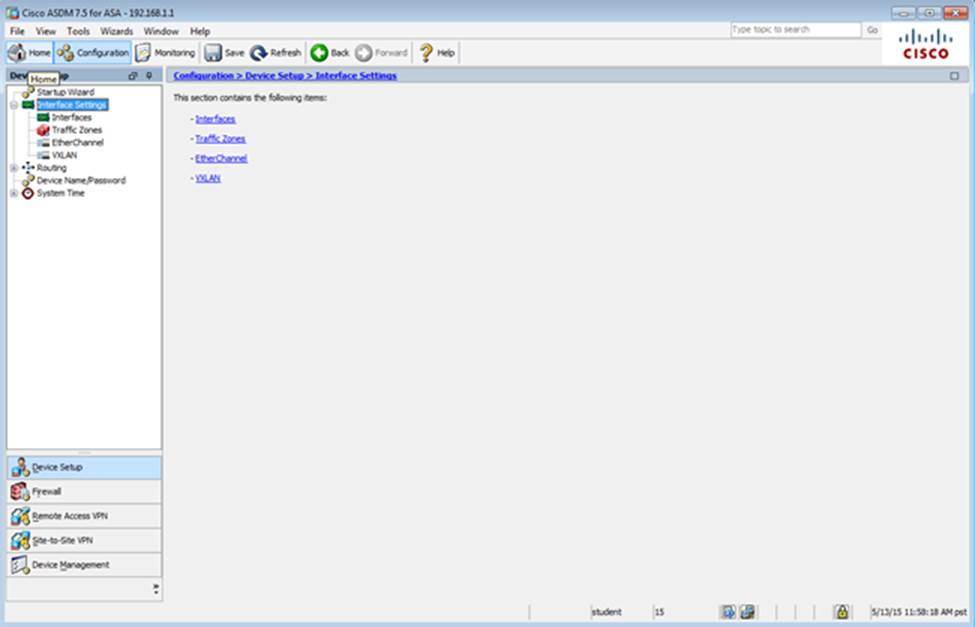
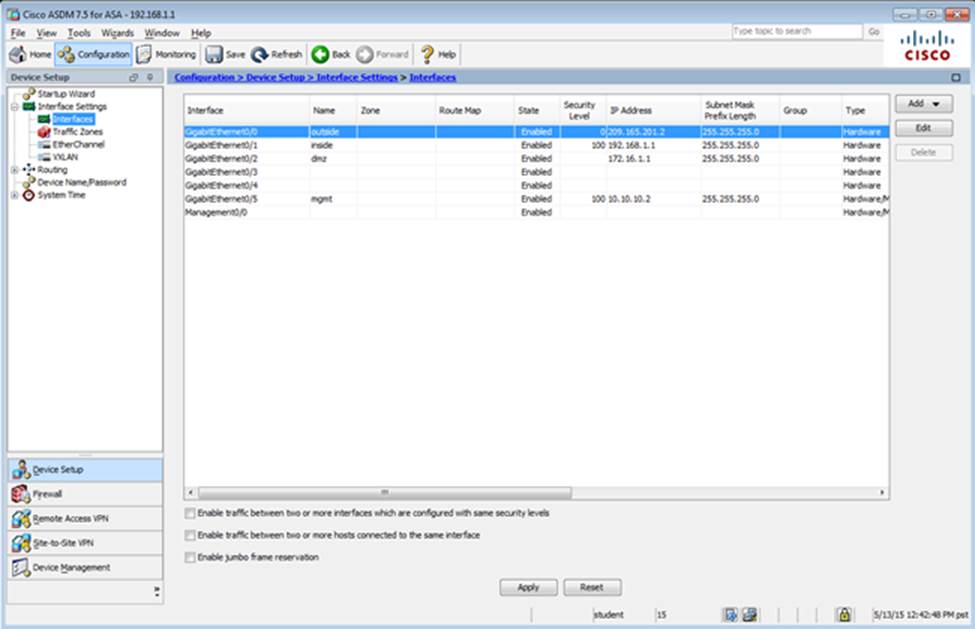
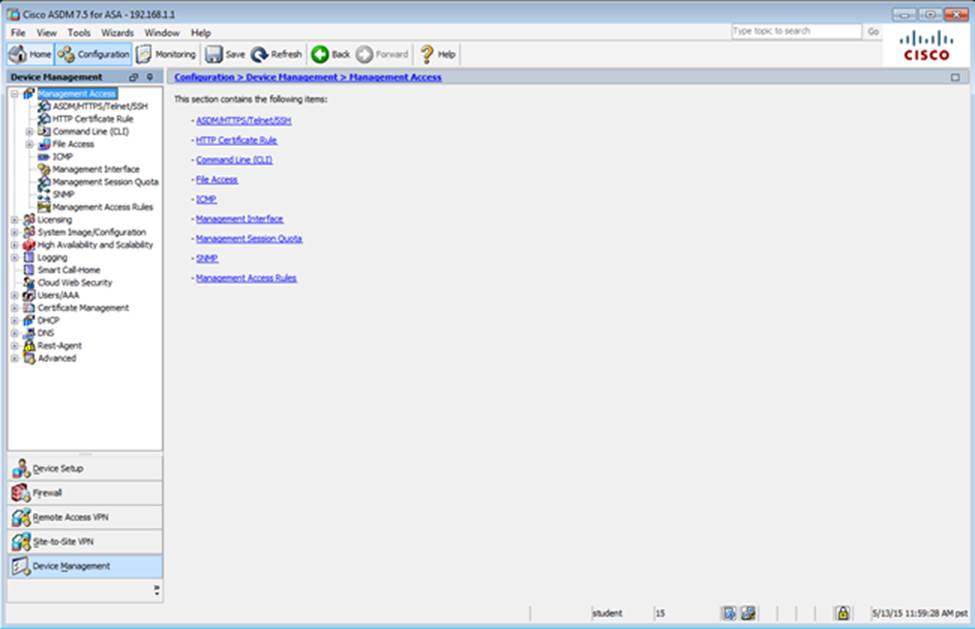
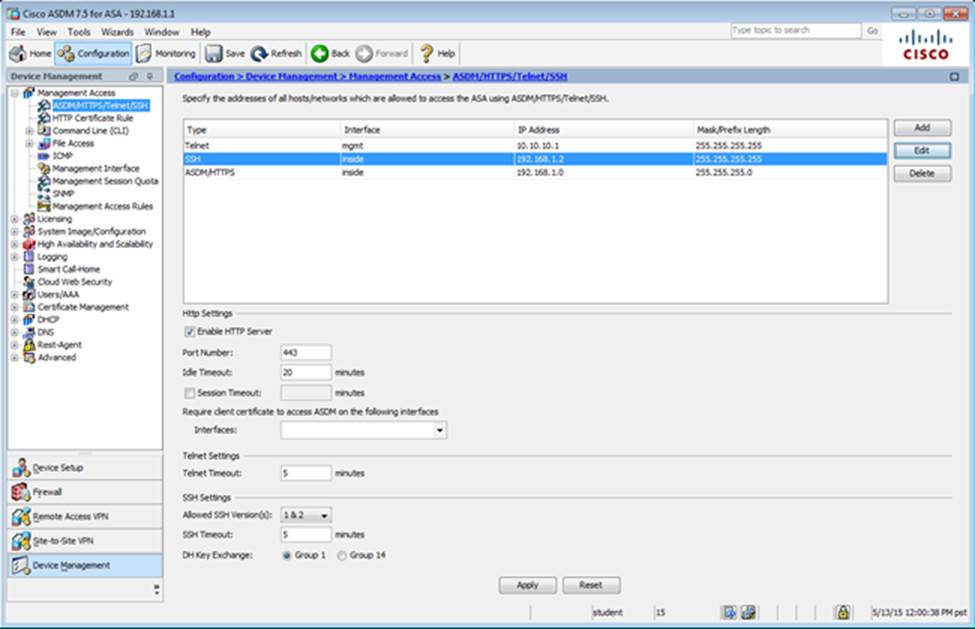
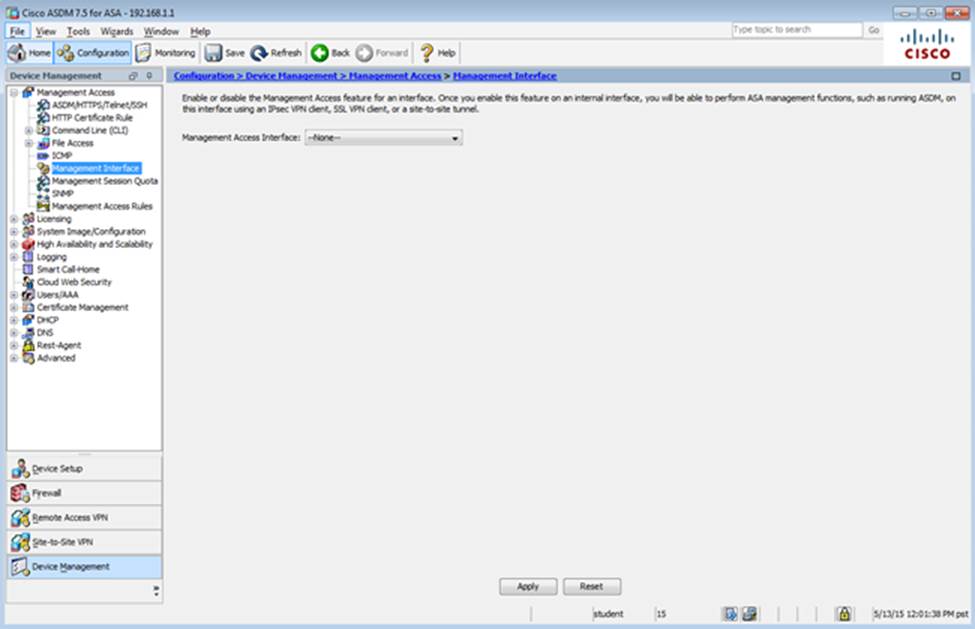
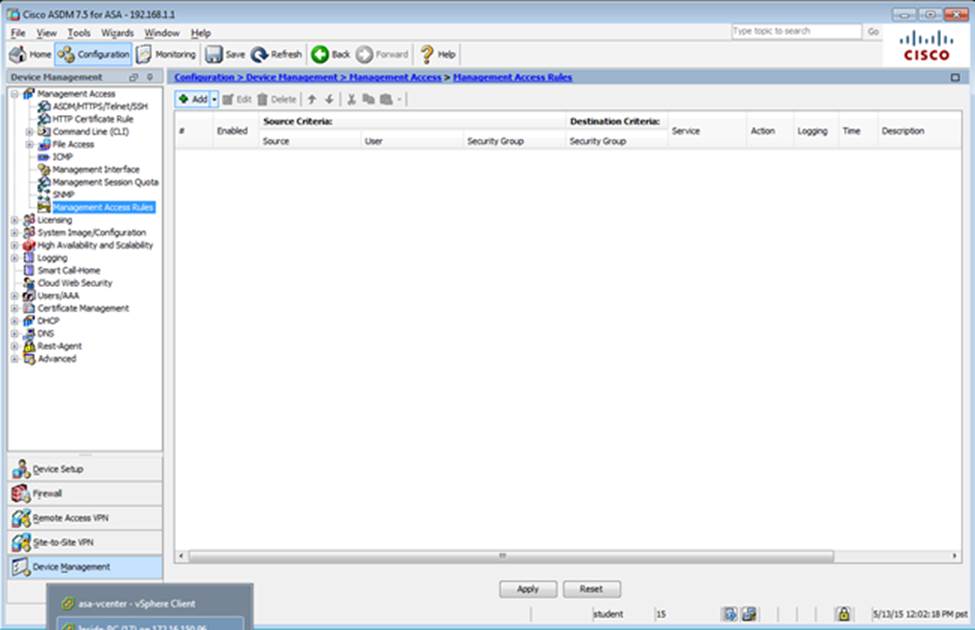
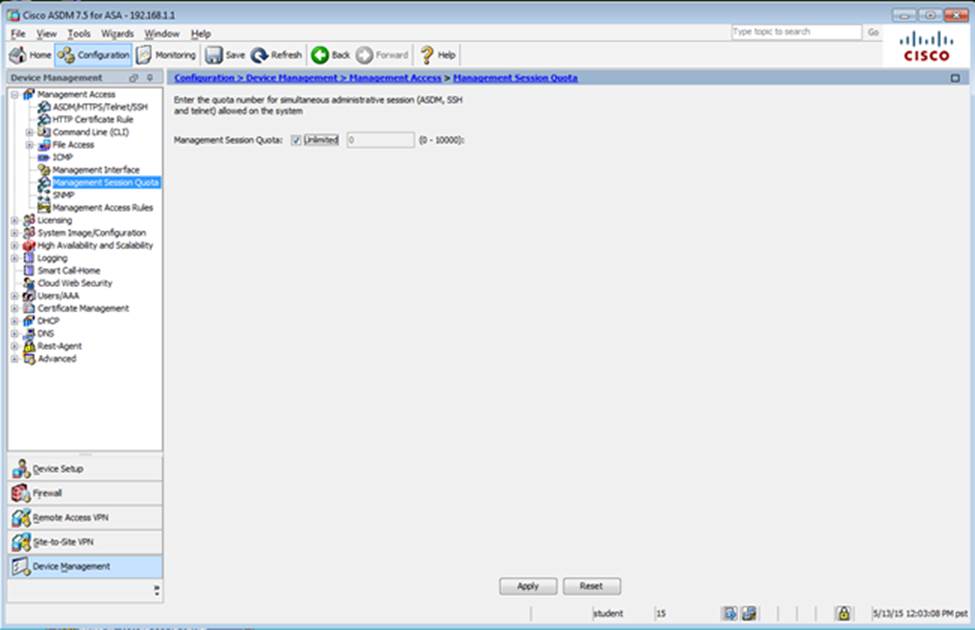
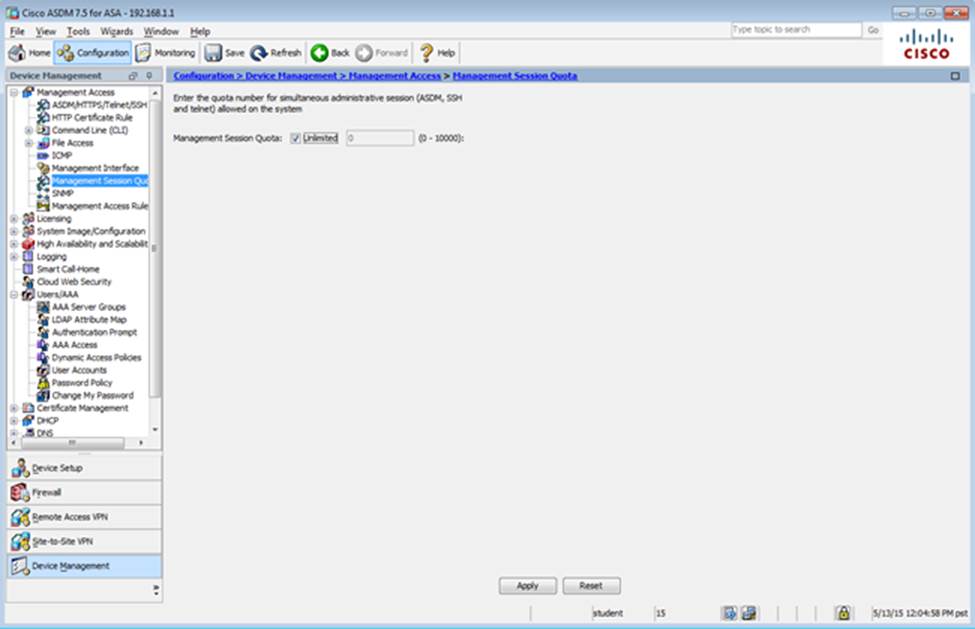
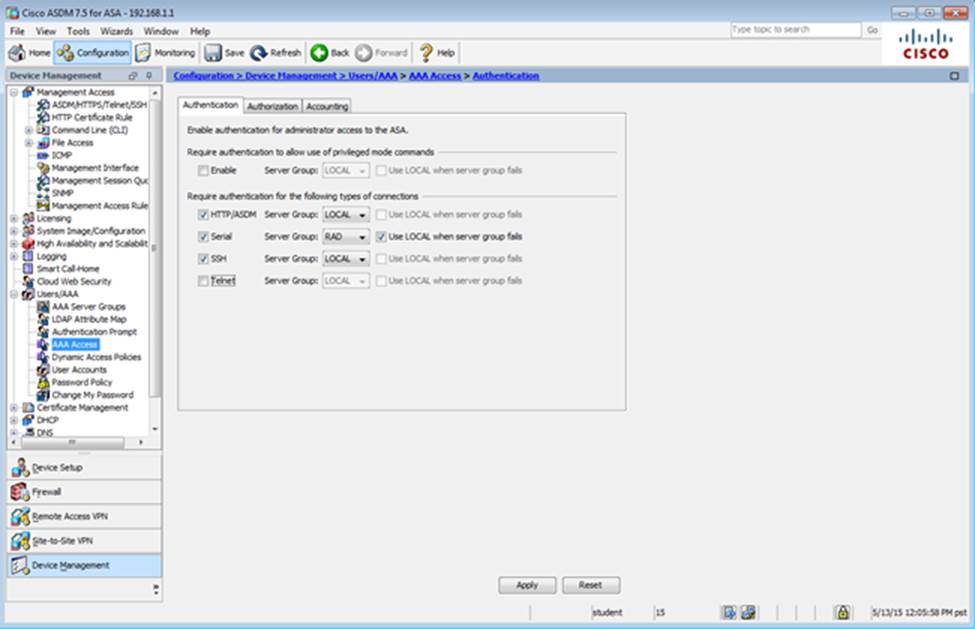
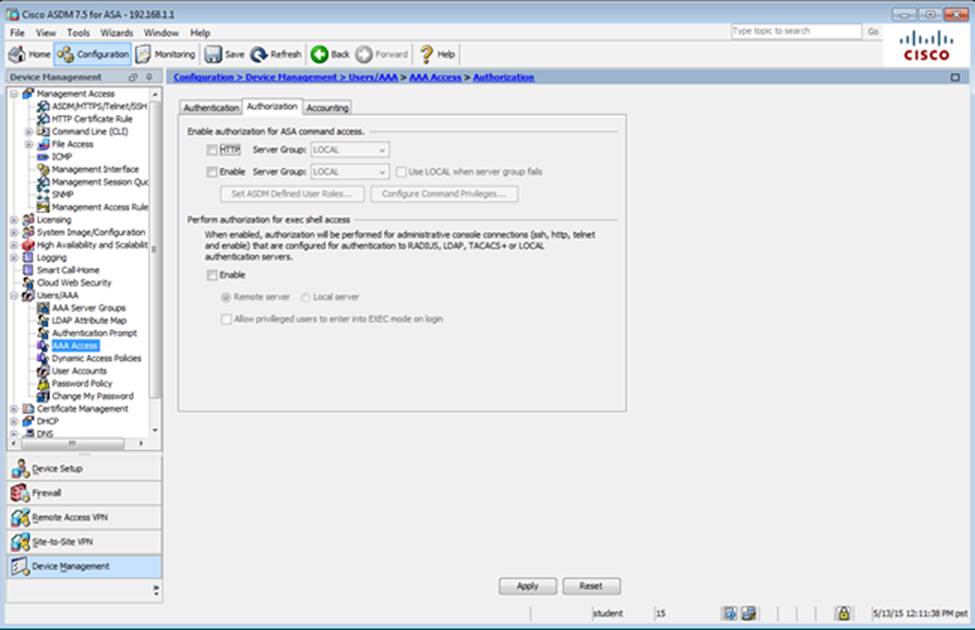
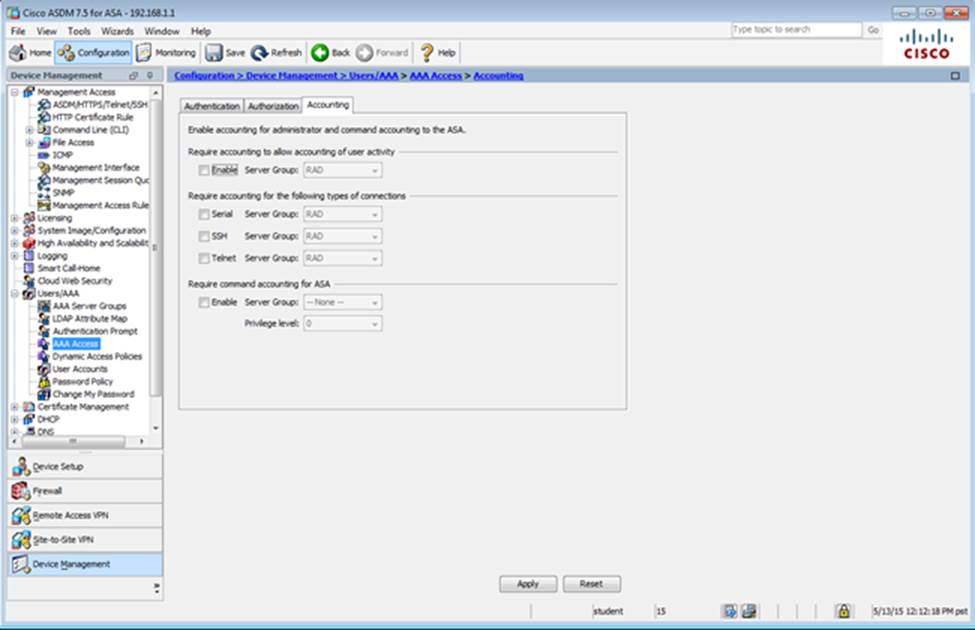
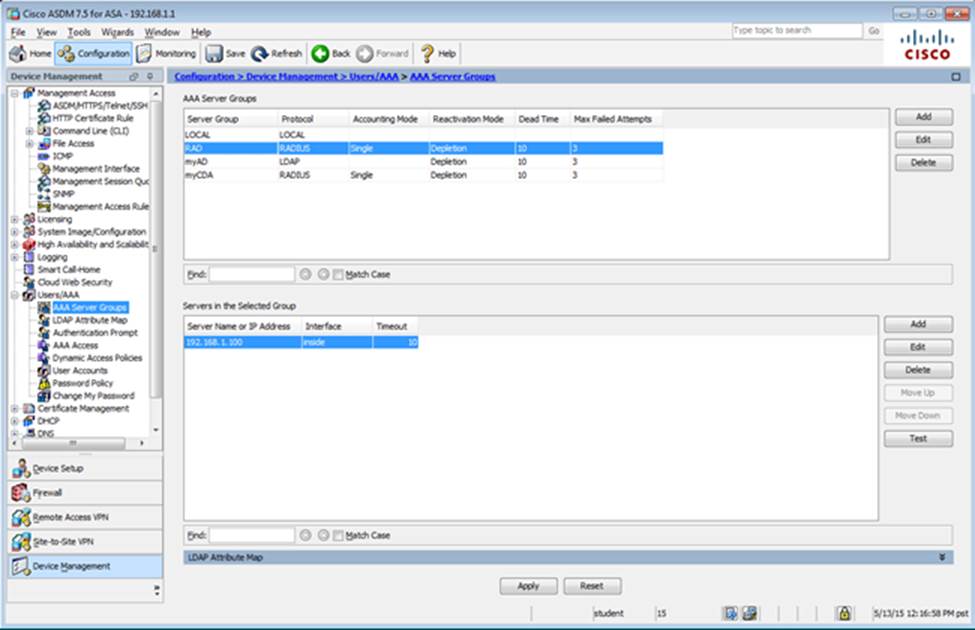
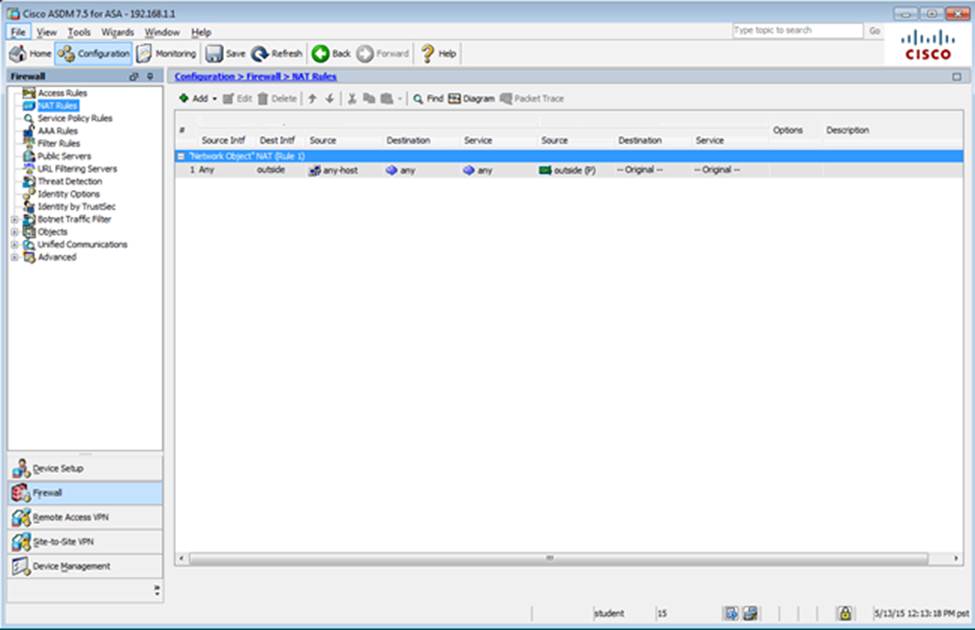
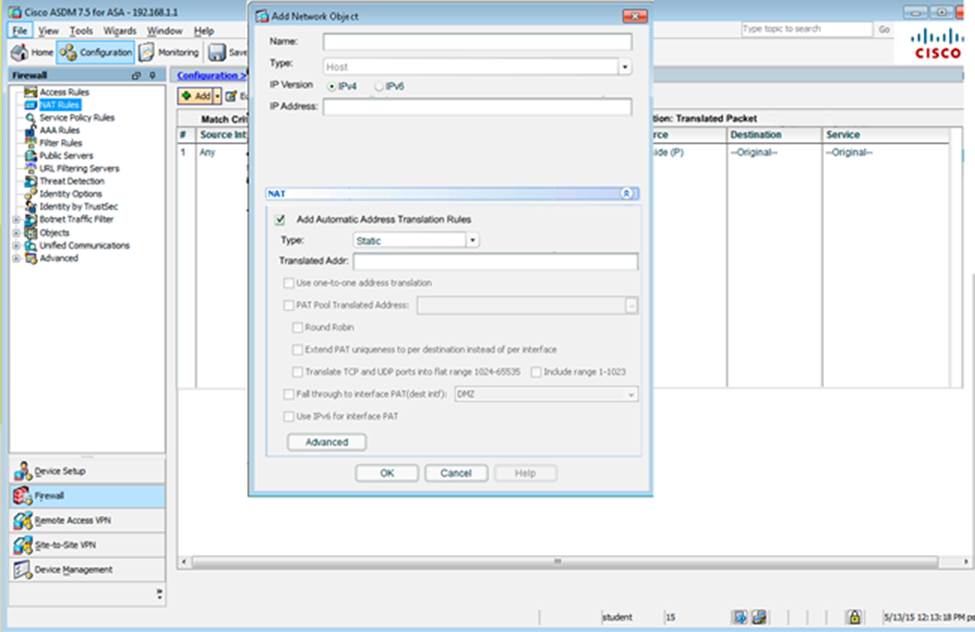
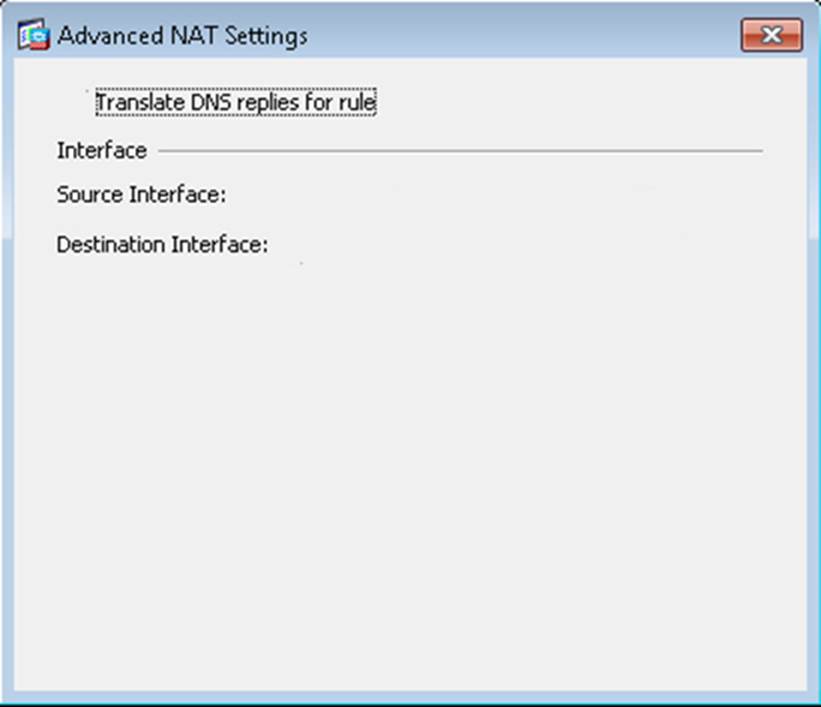
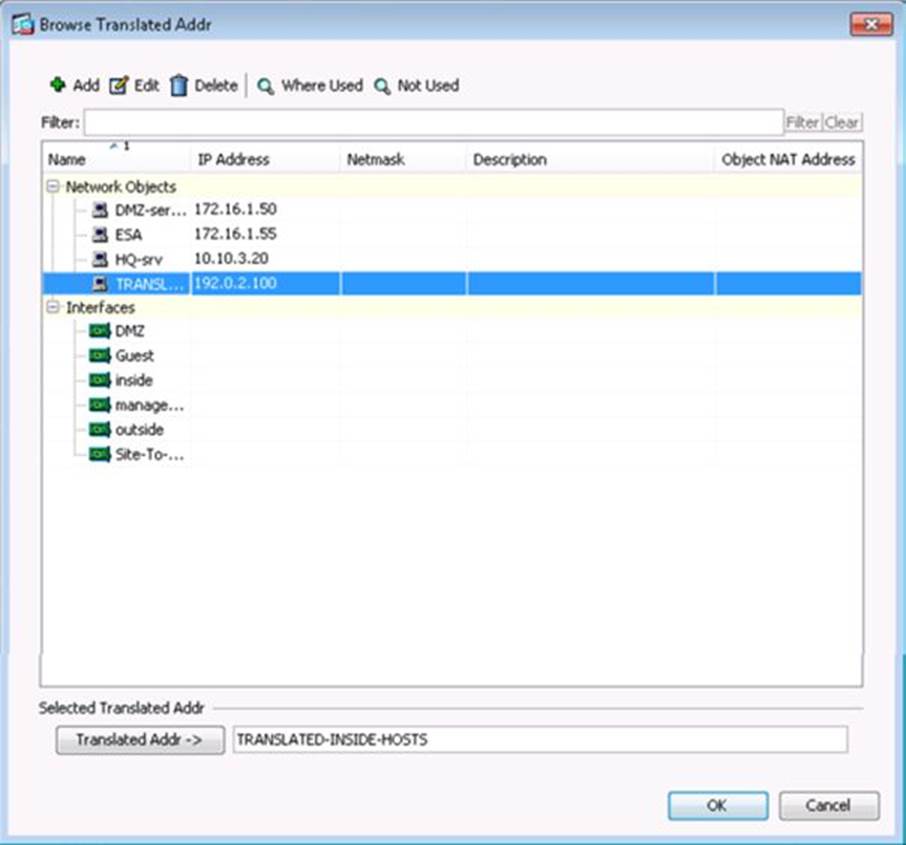
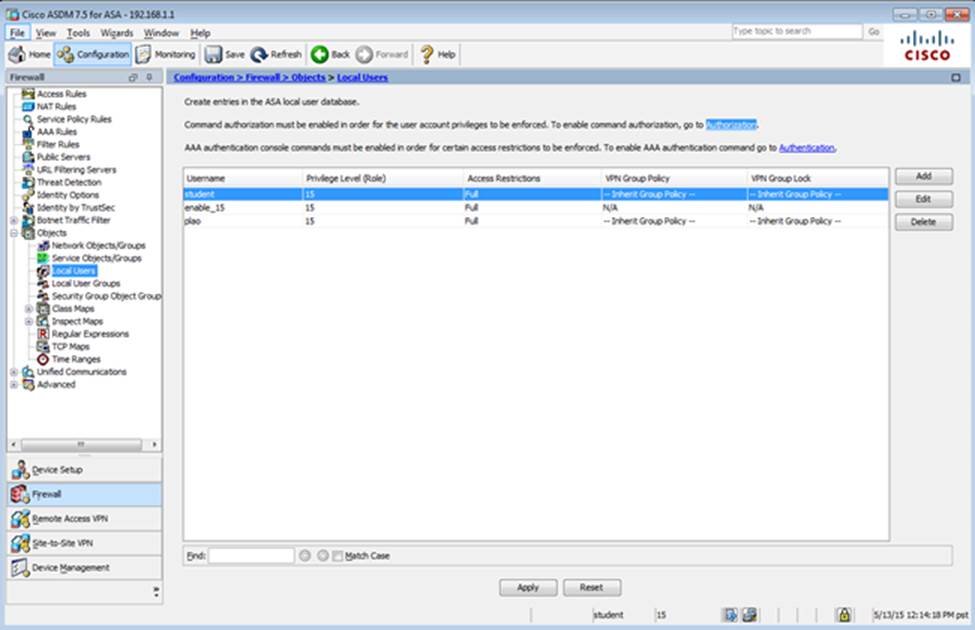
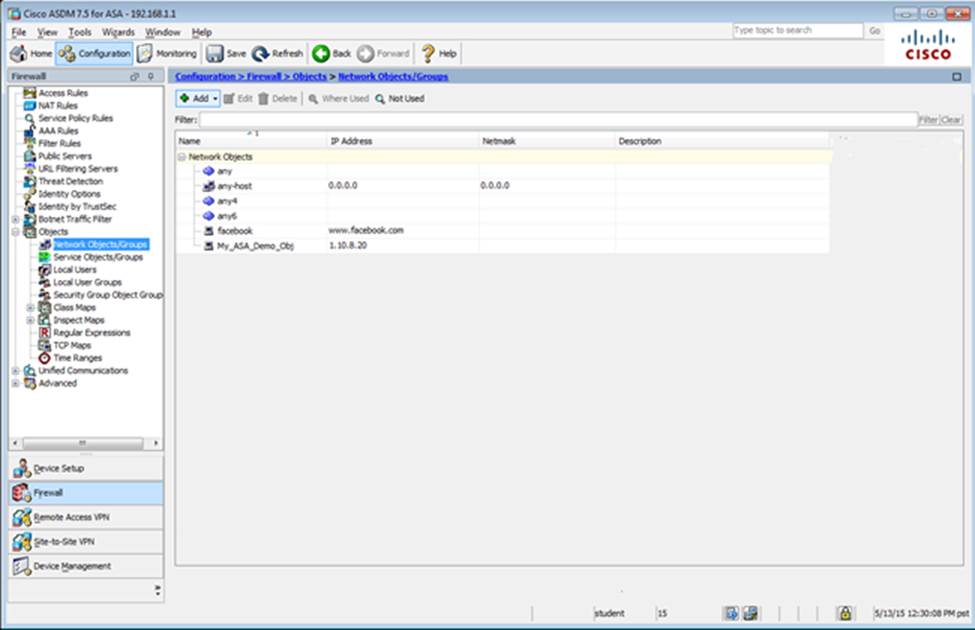
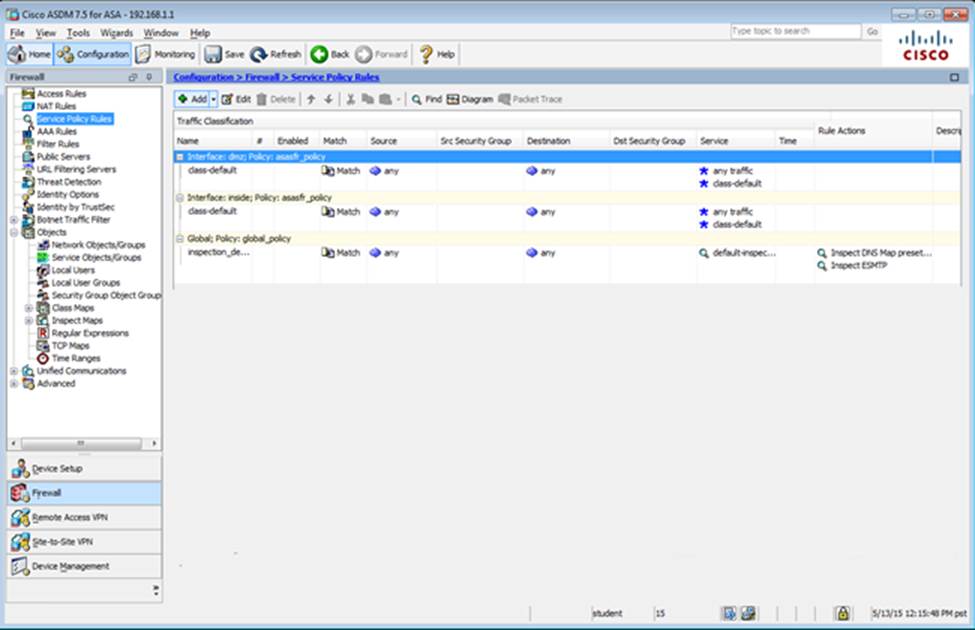
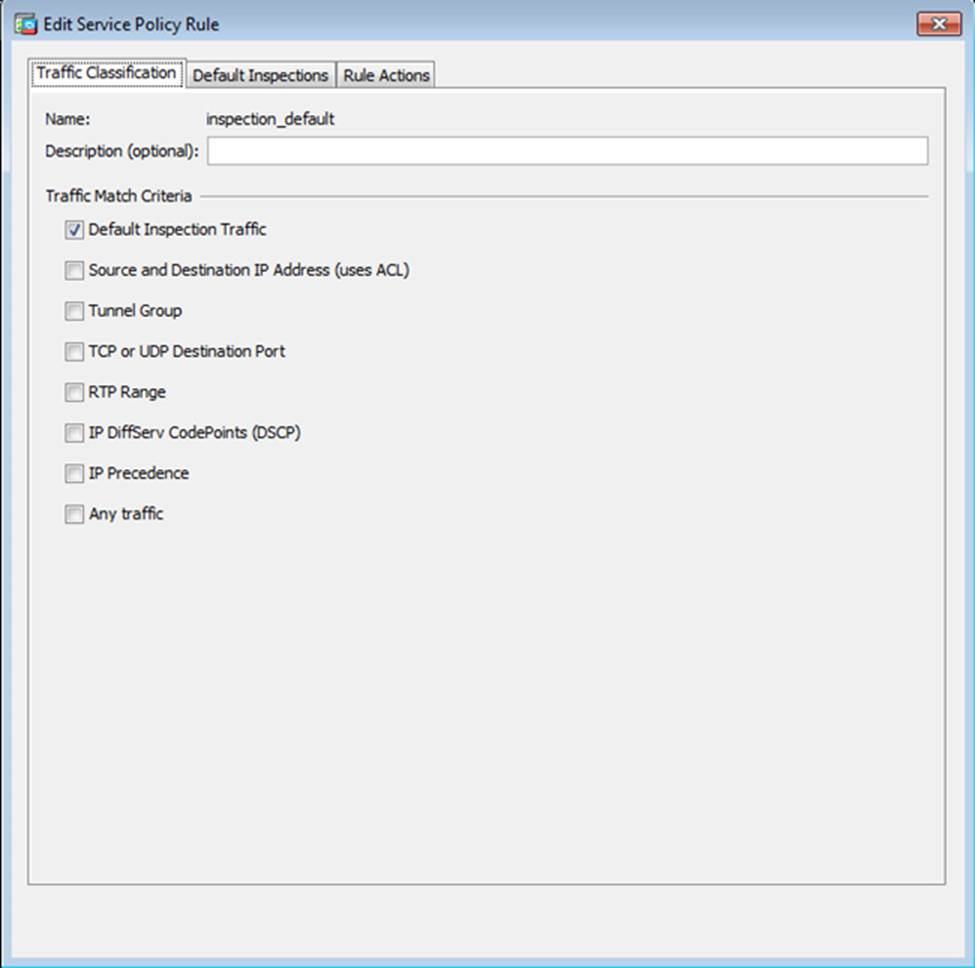
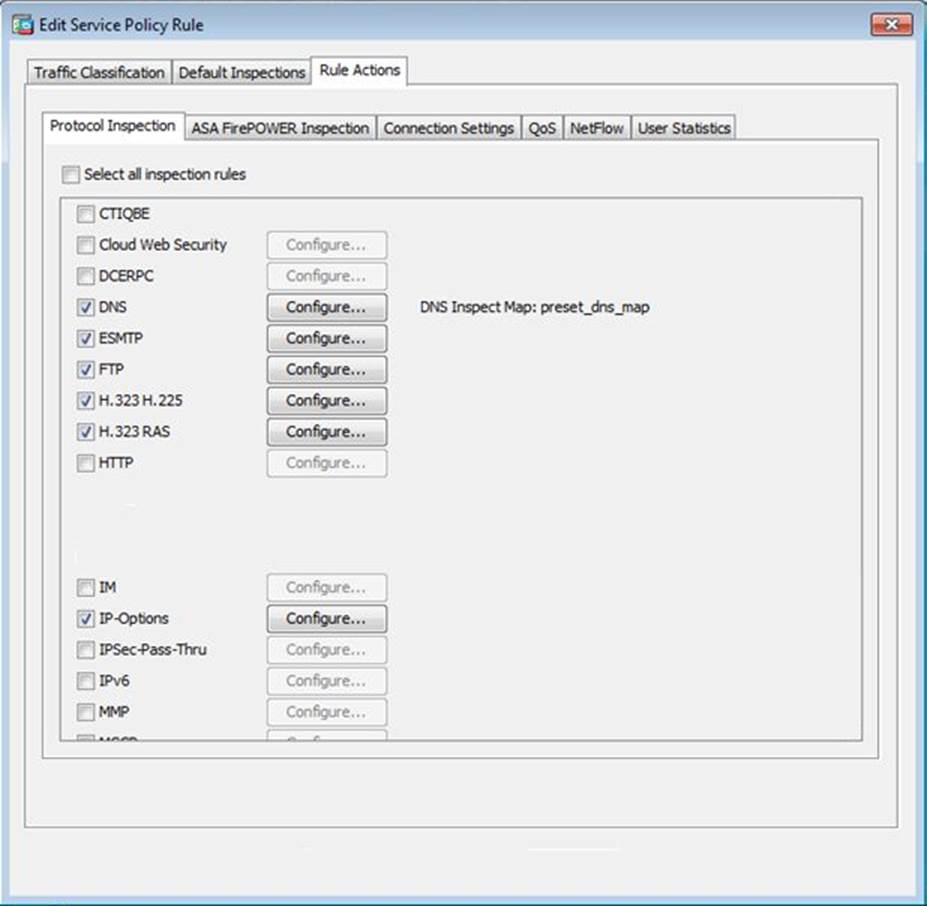
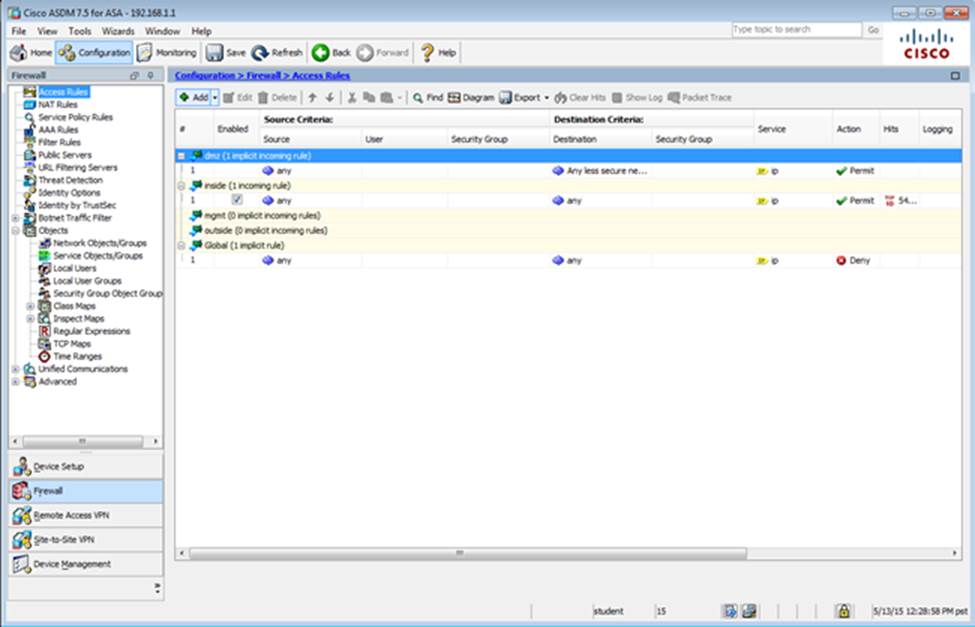
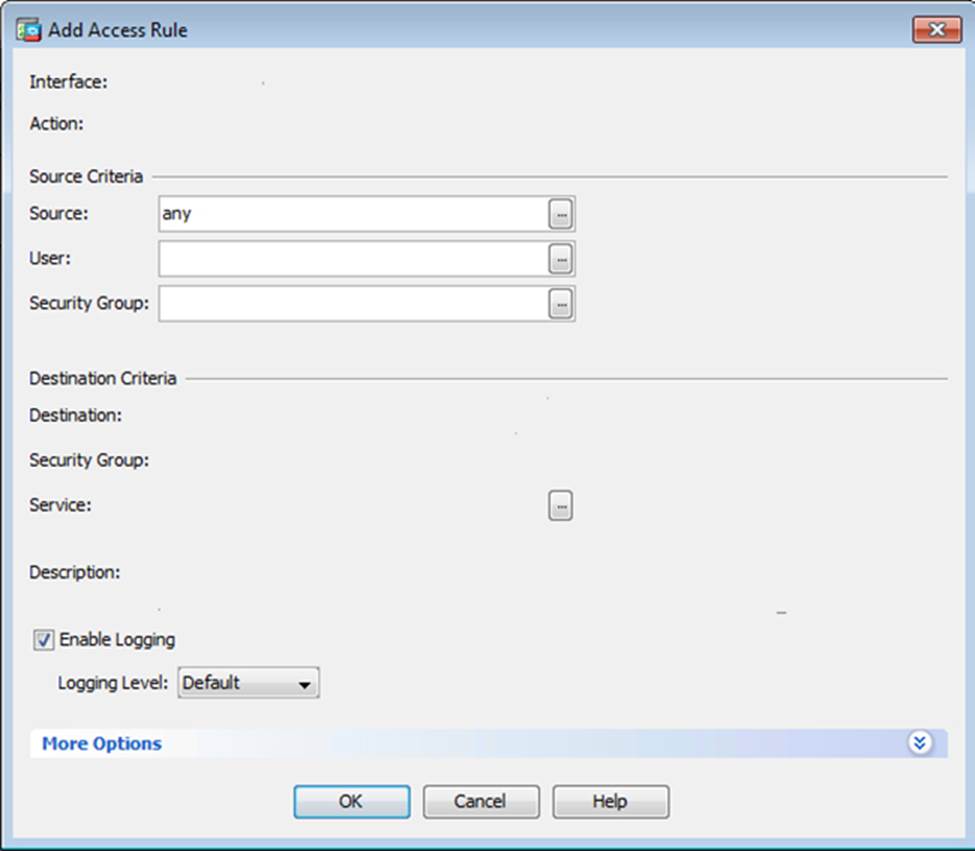
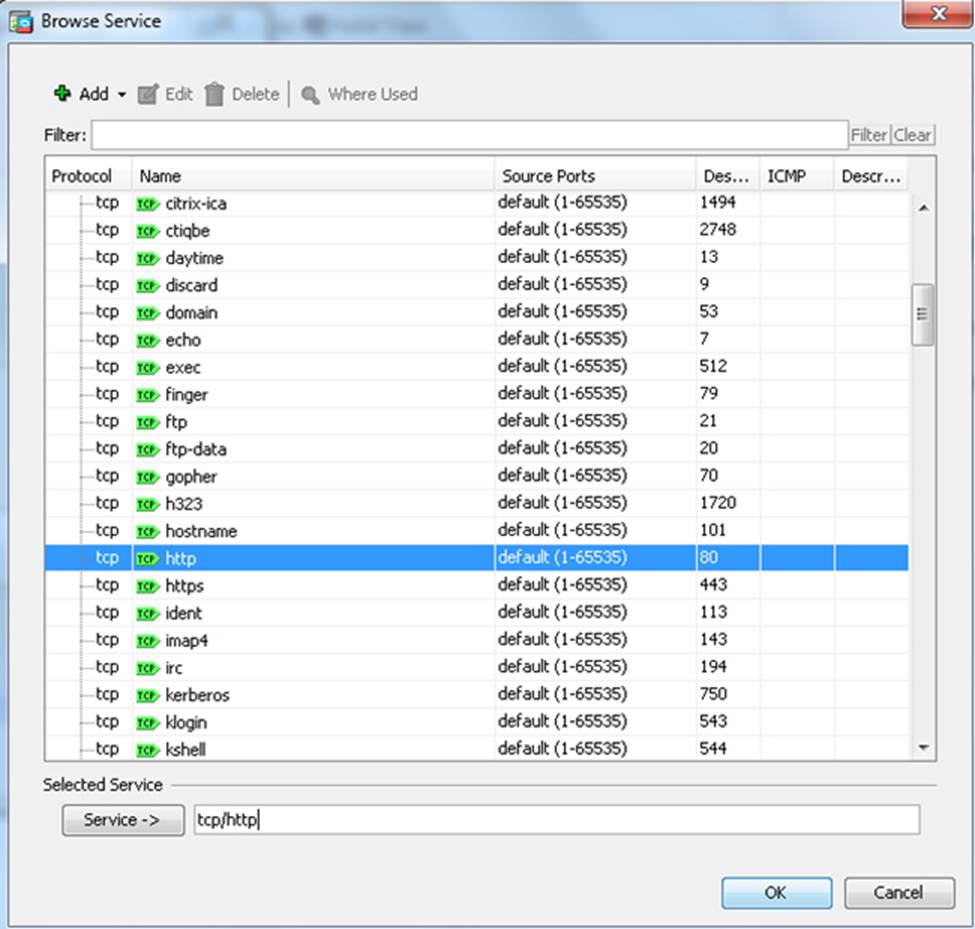
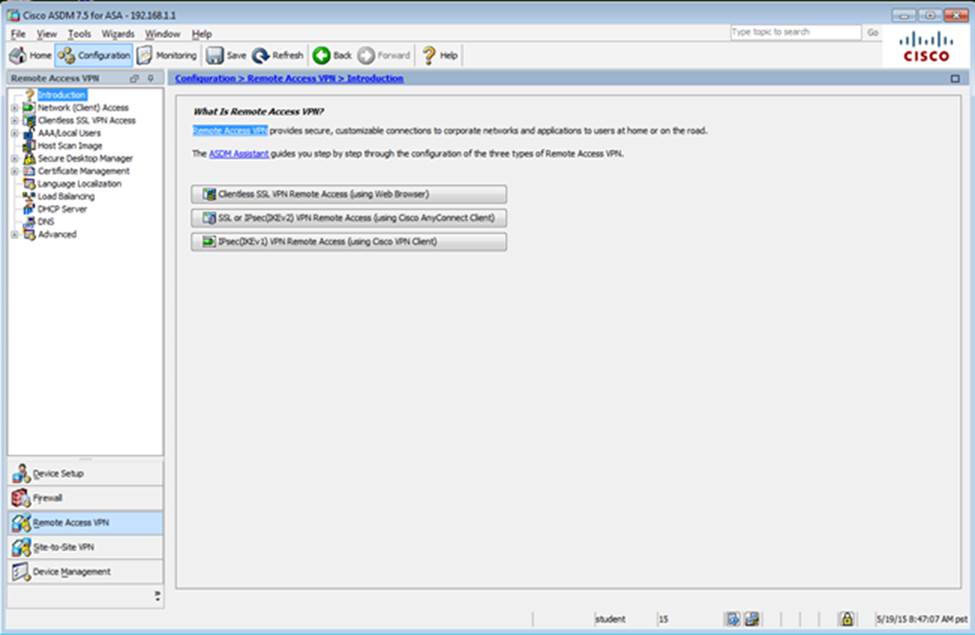
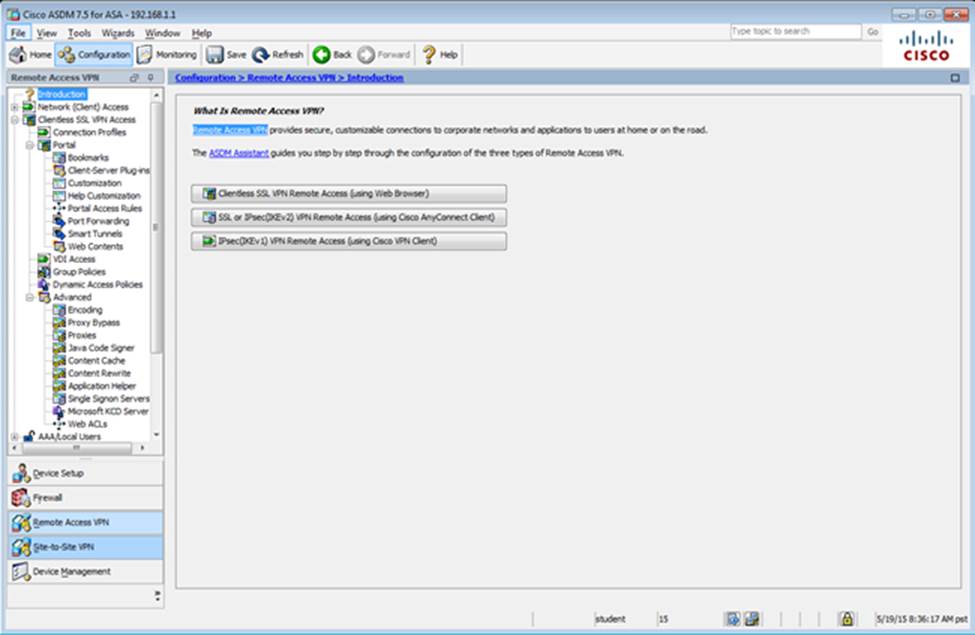
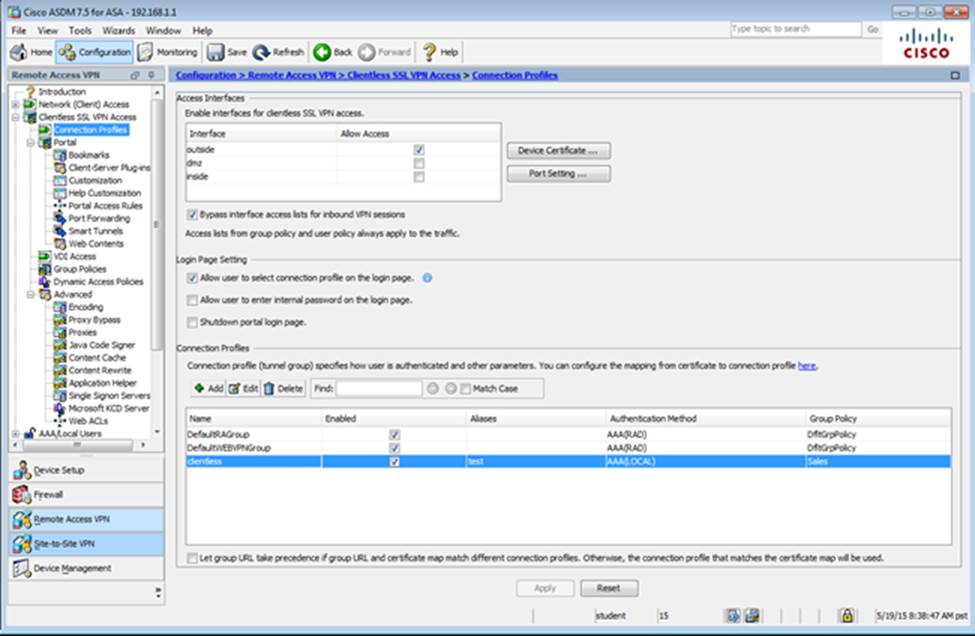
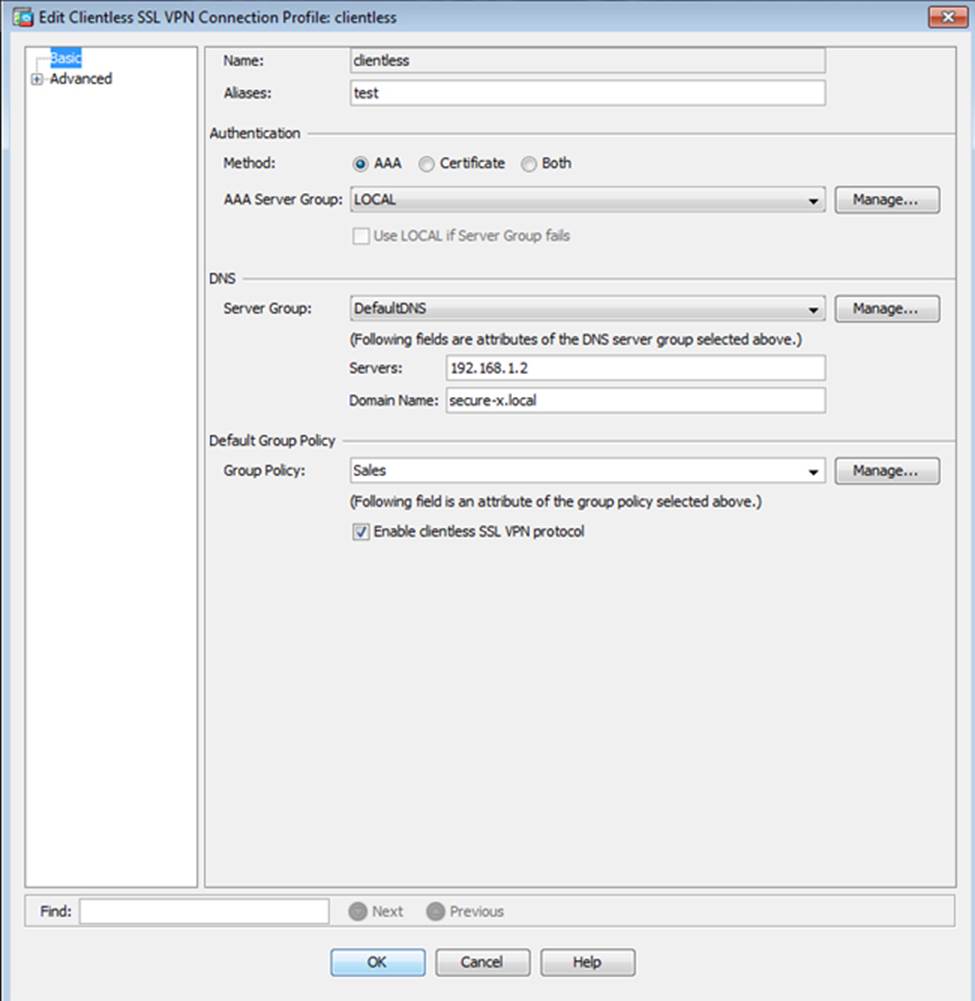
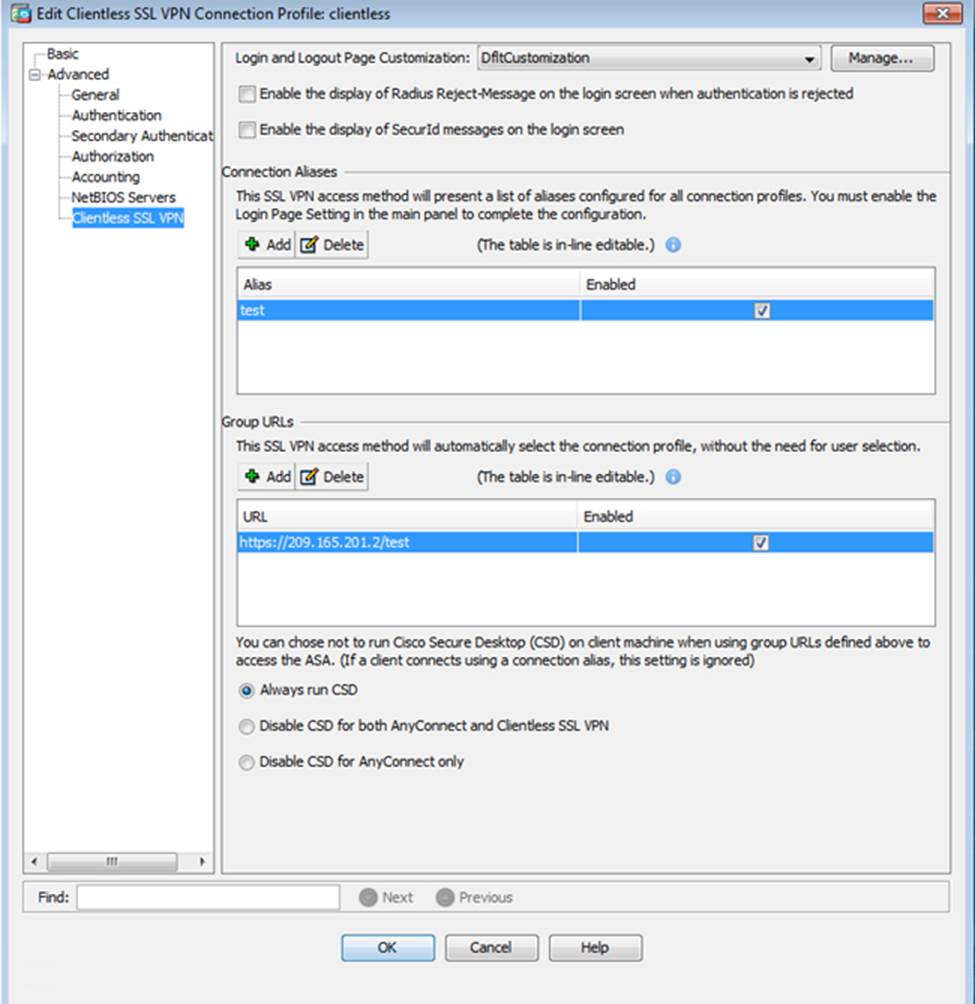
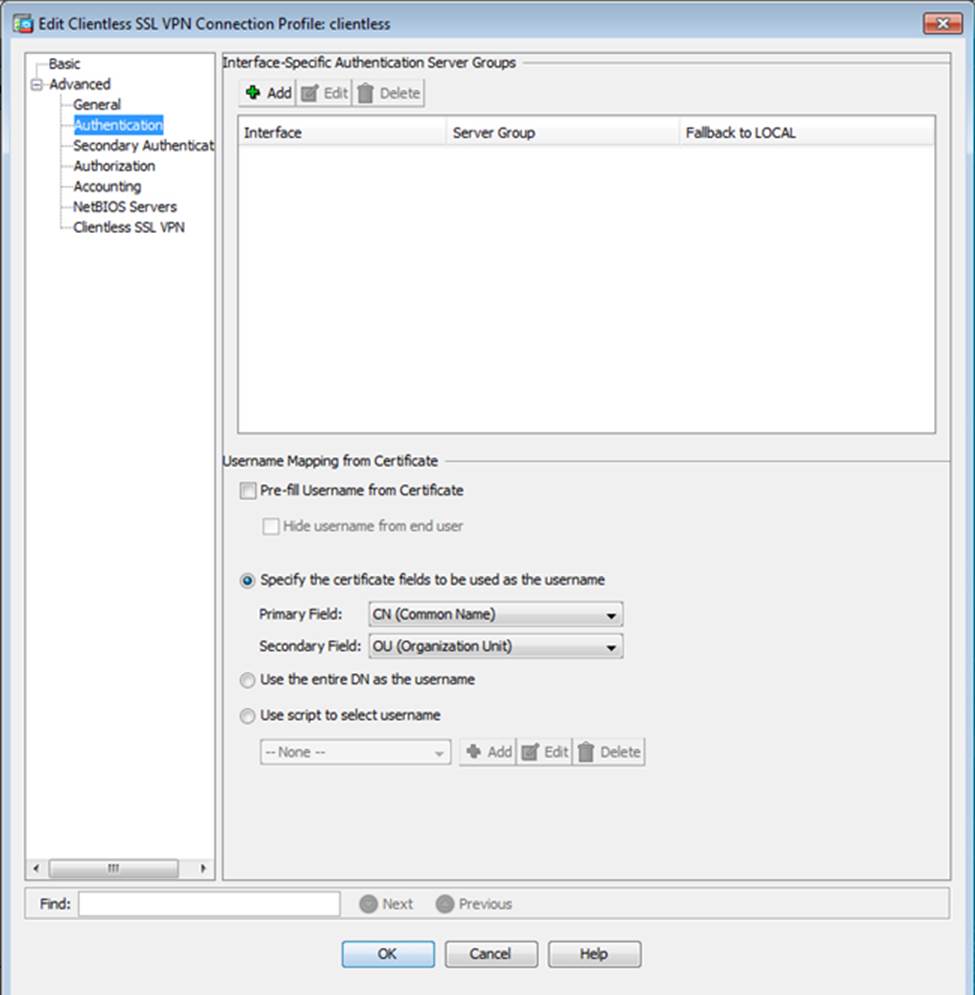
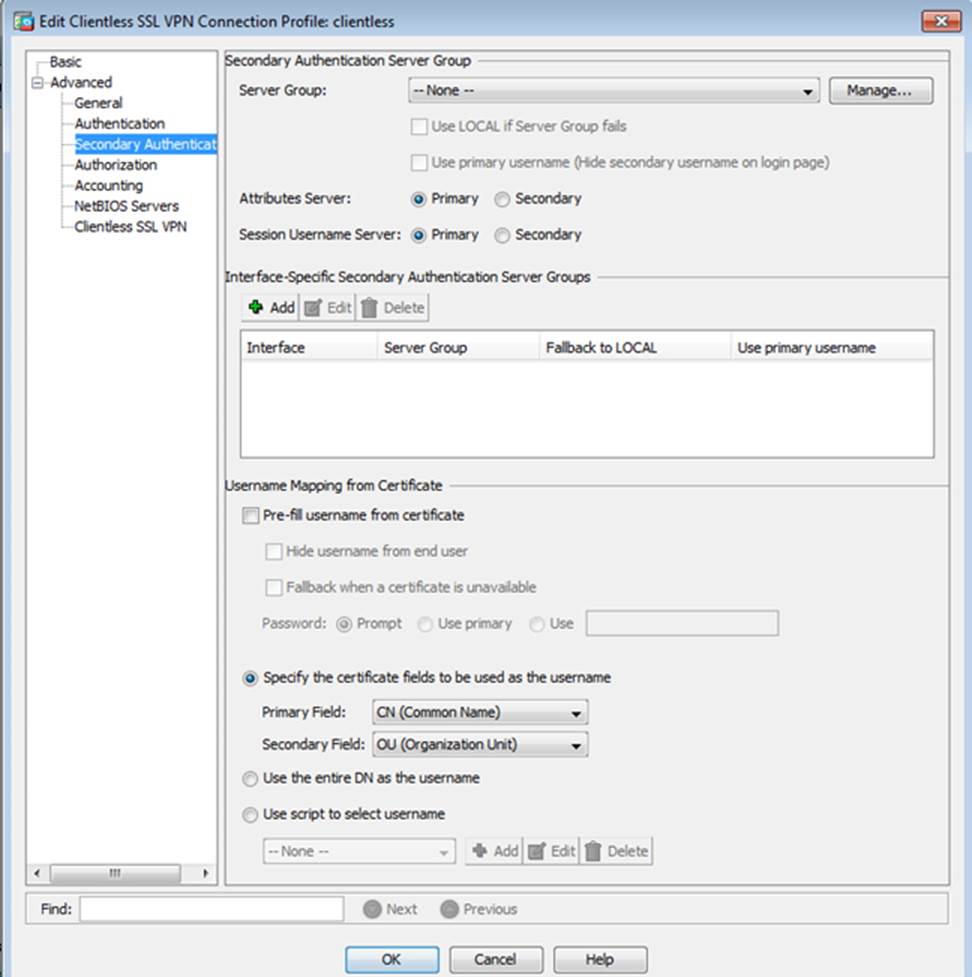
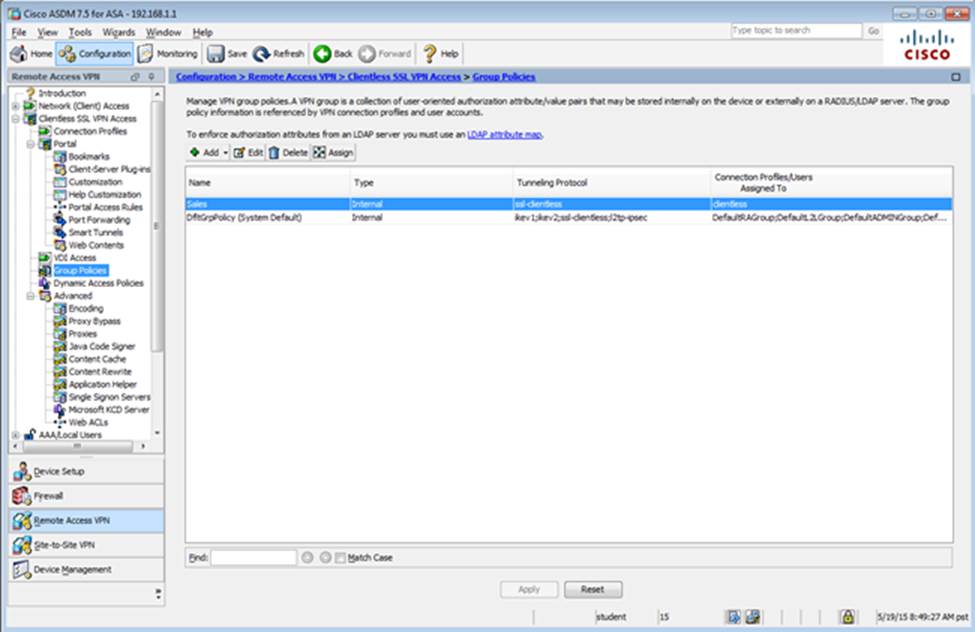
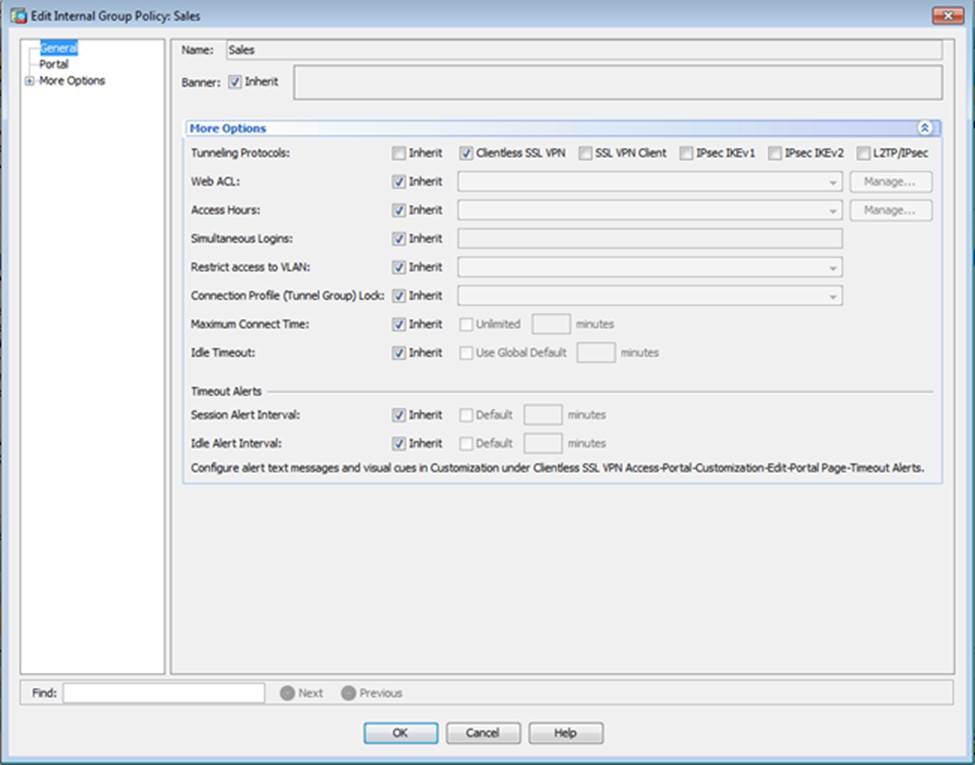
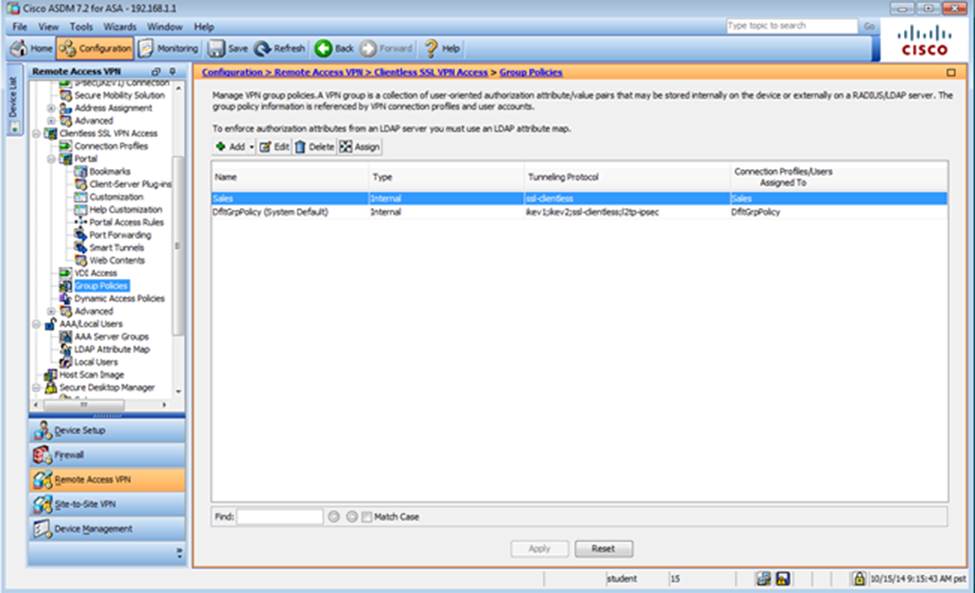
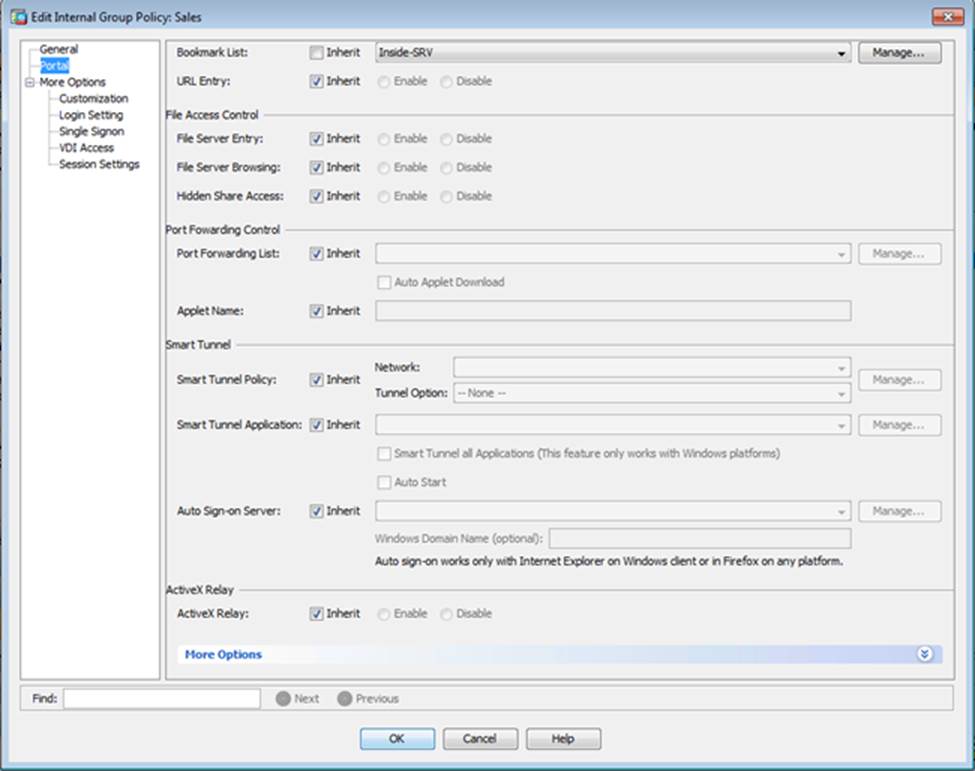
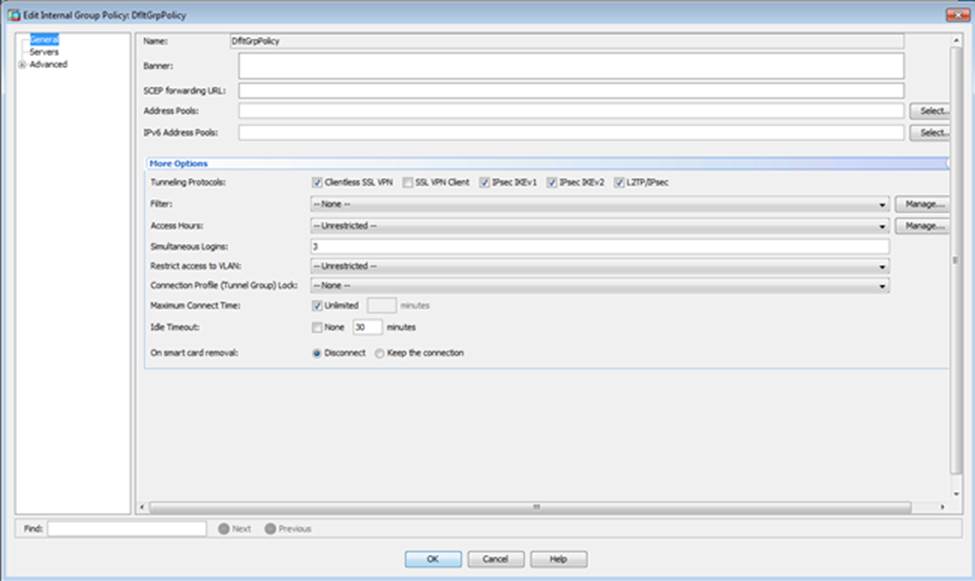
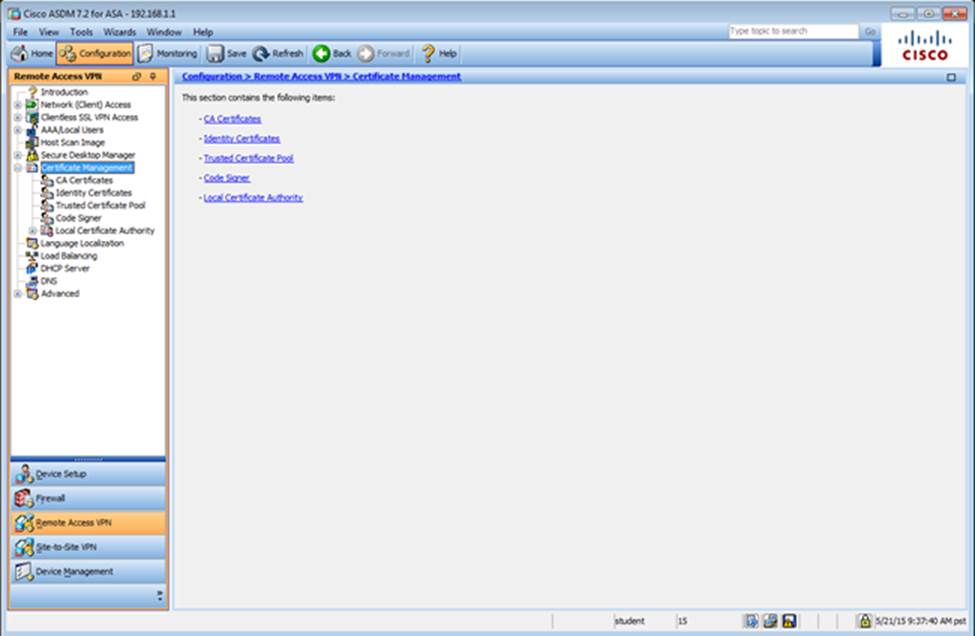
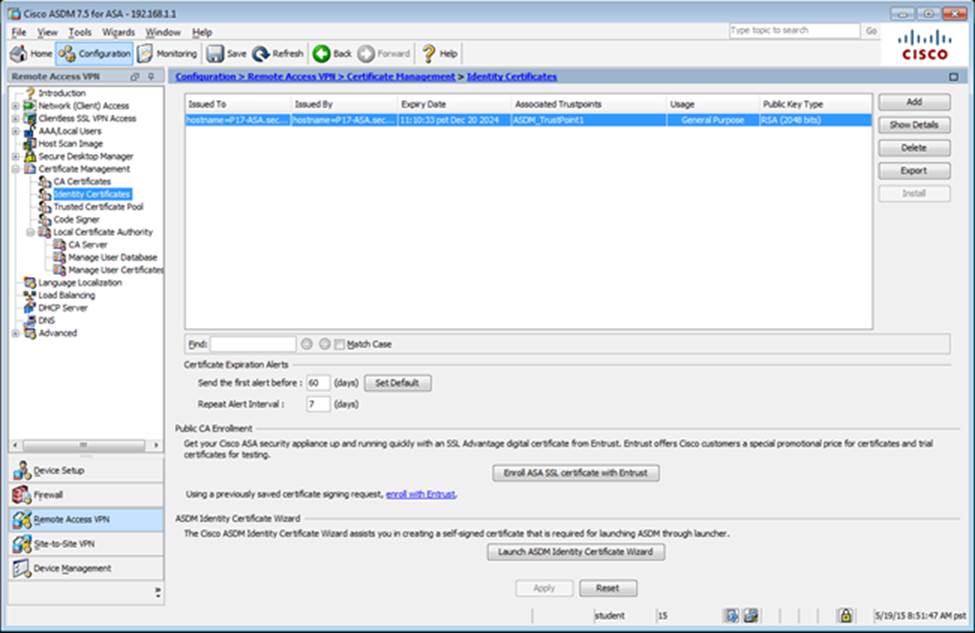
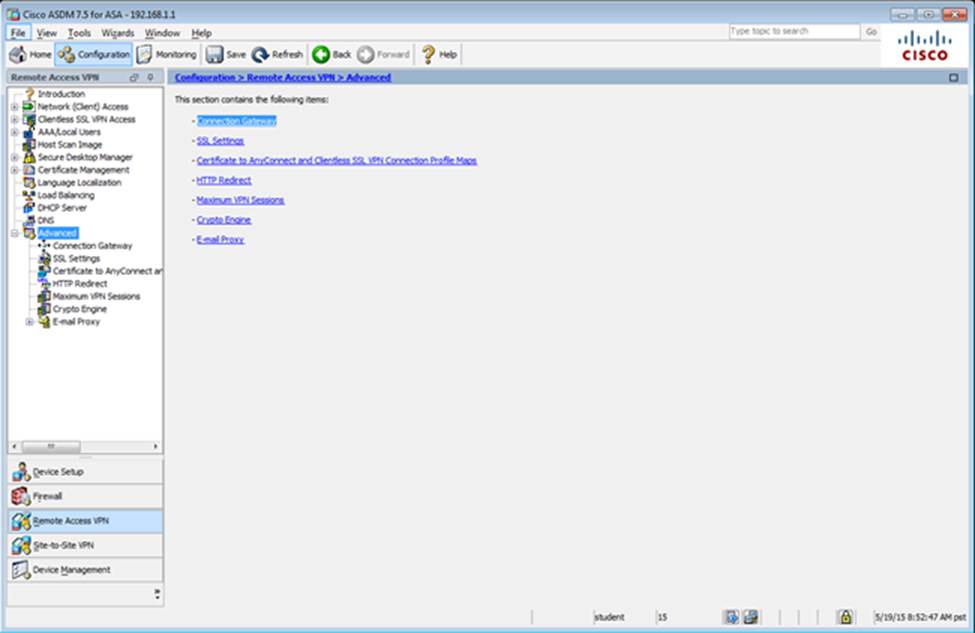
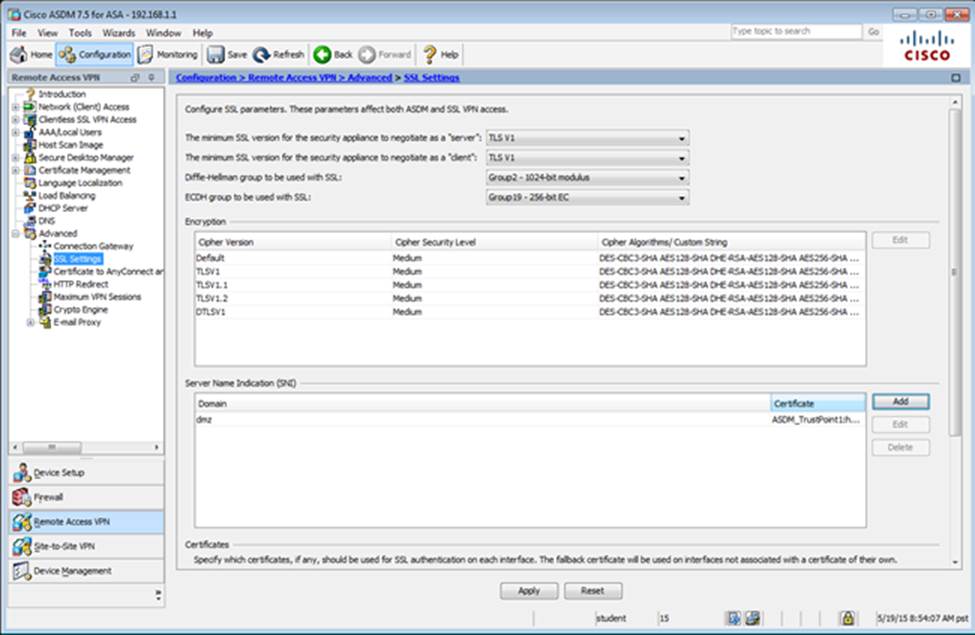
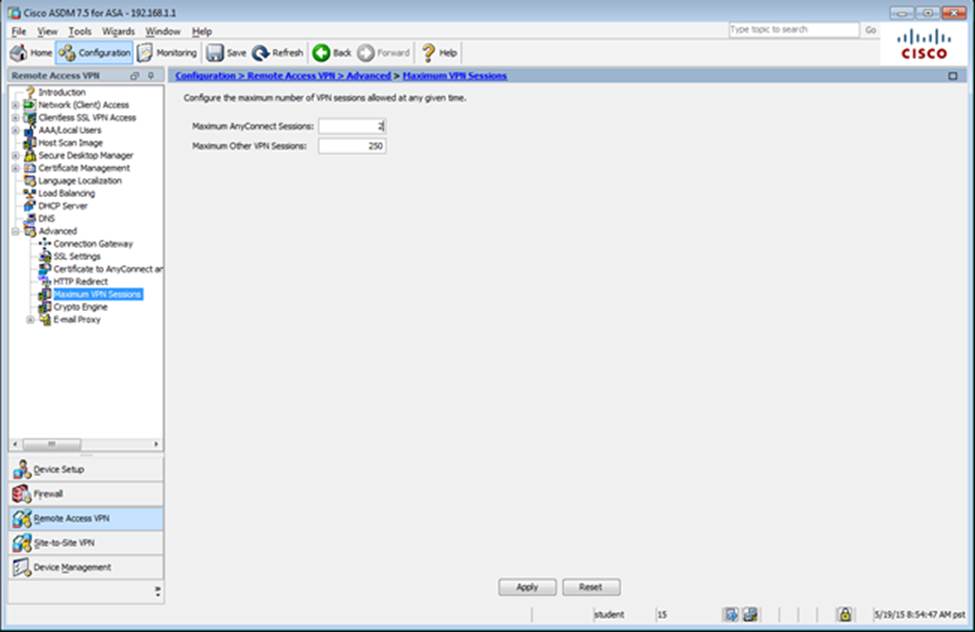
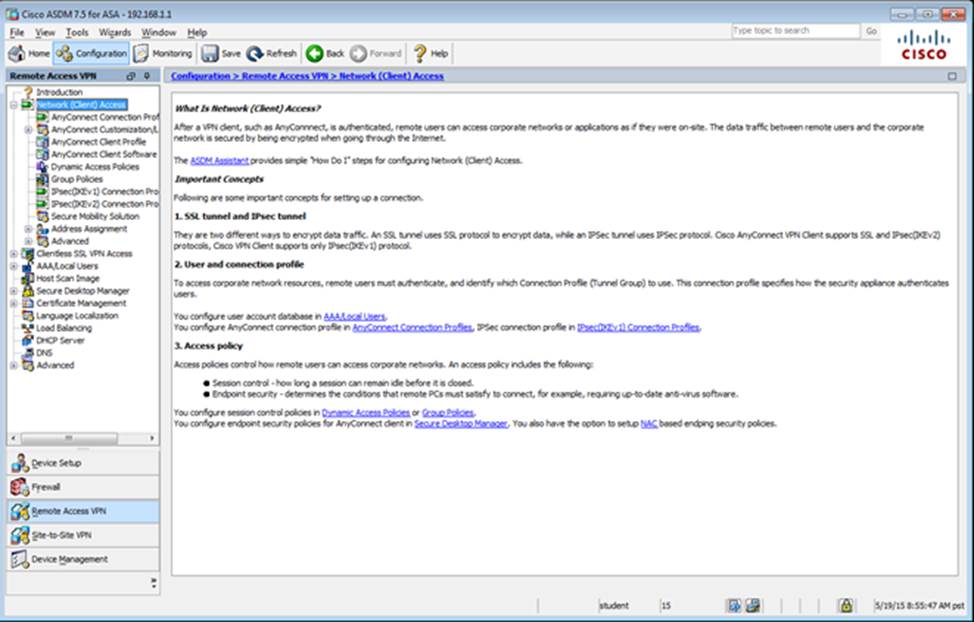
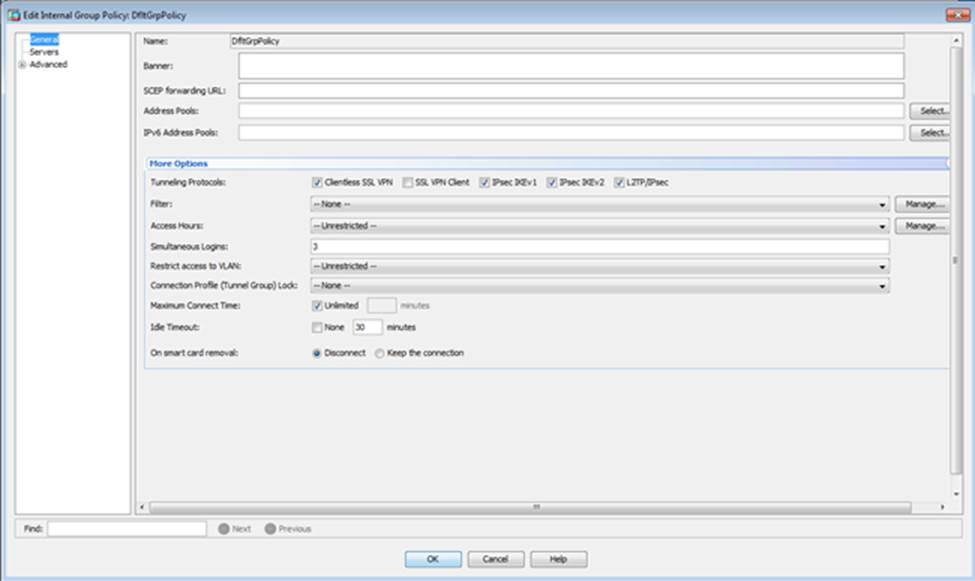
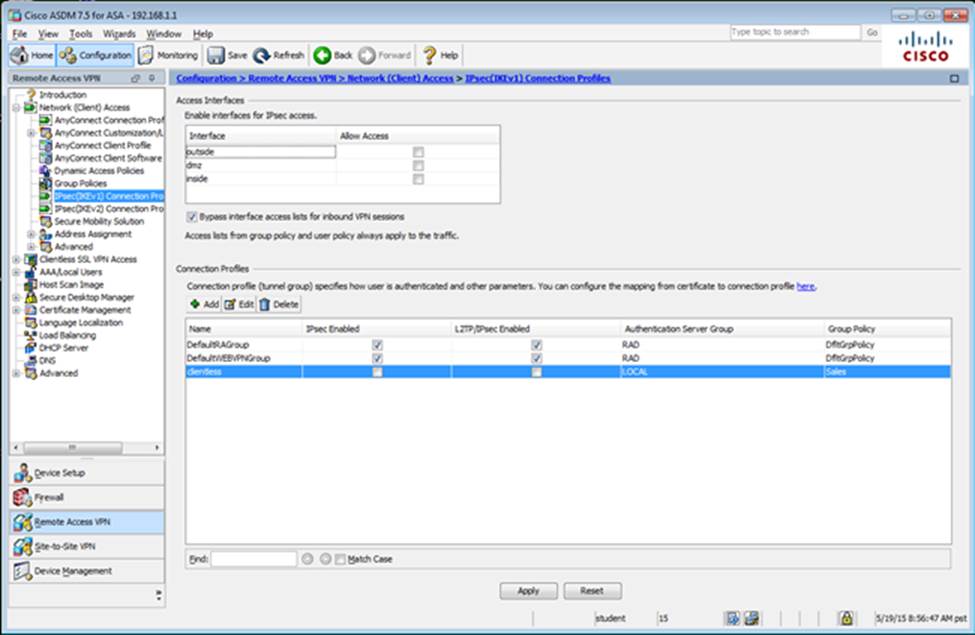
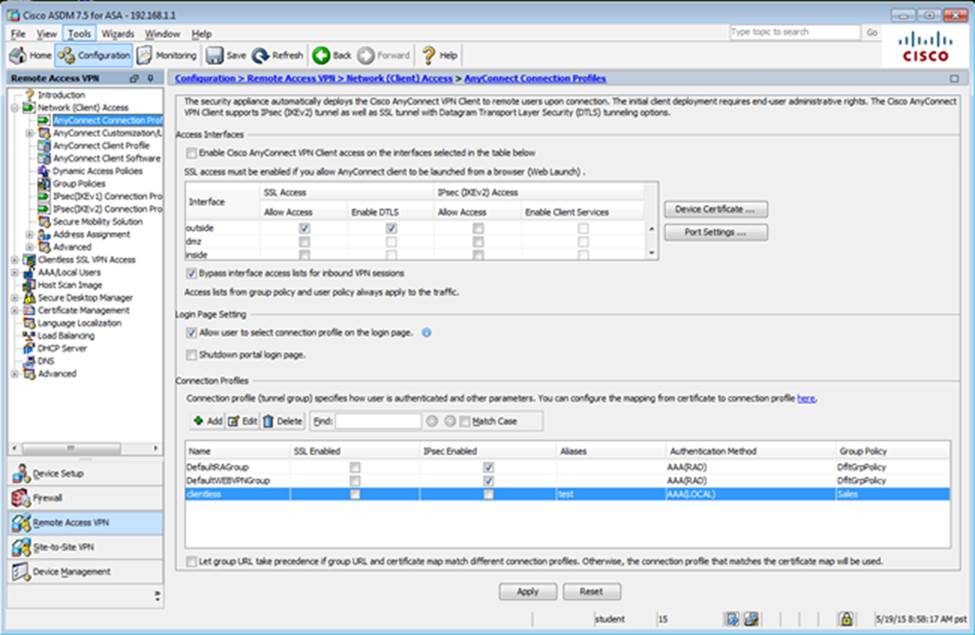
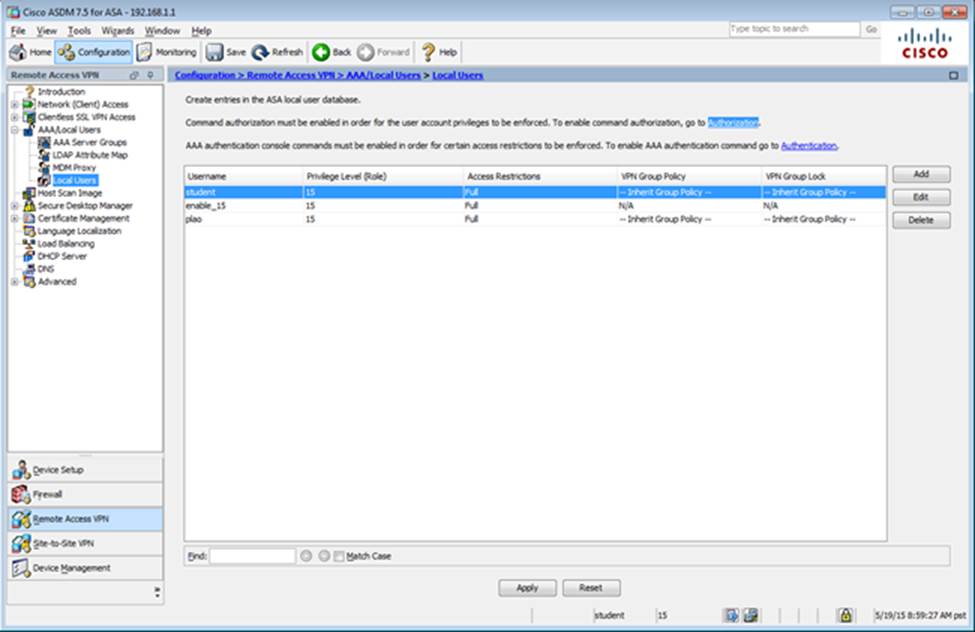
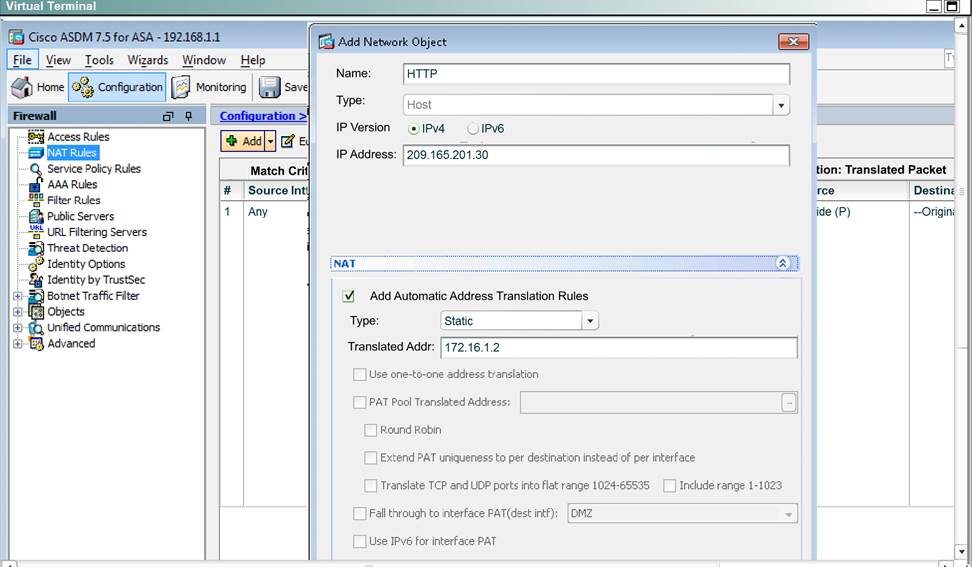
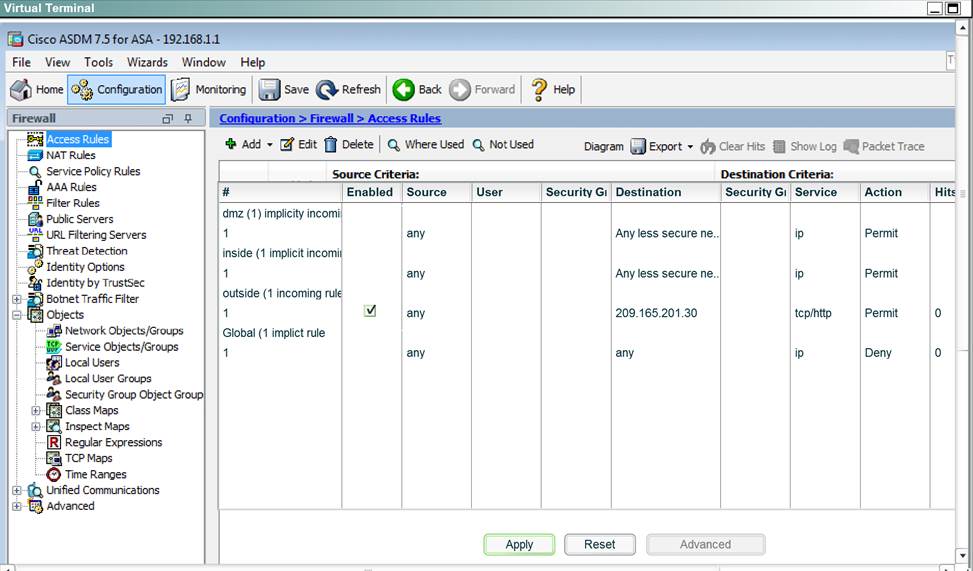
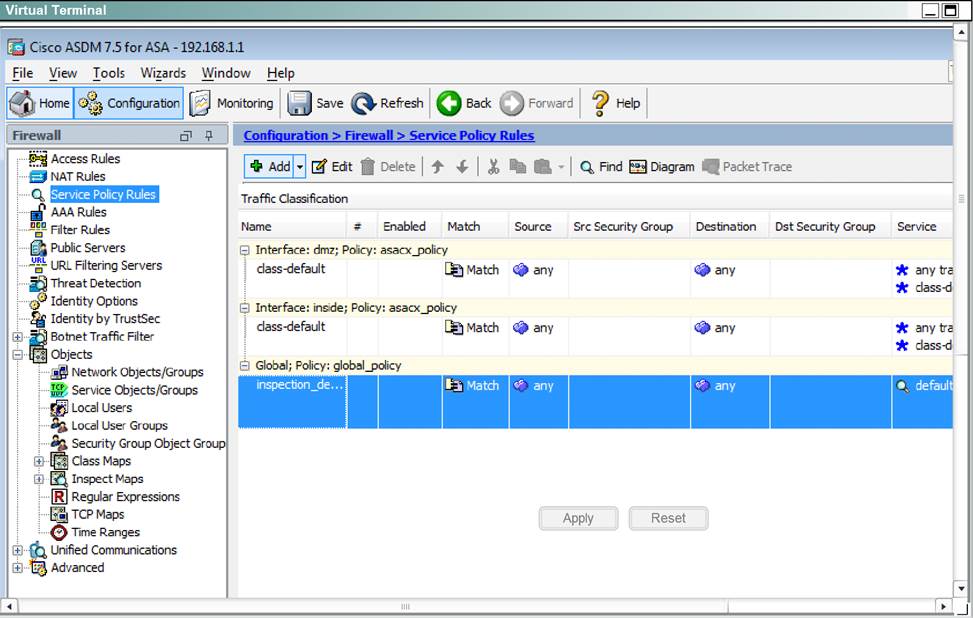
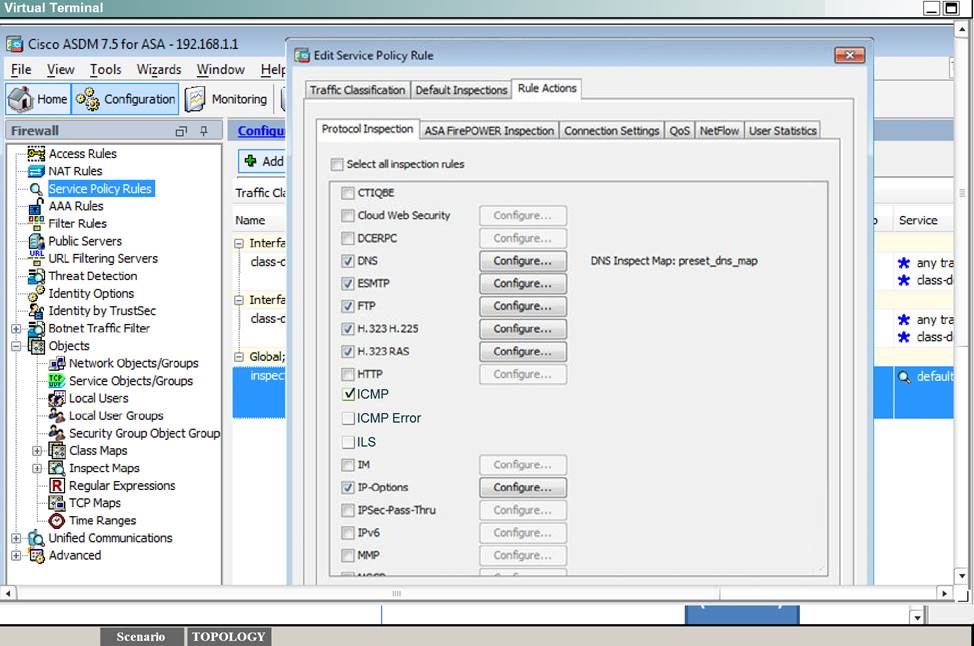
Scenario Given the new additional connectivity requirements and the topology diagram, use ASDM to accomplish the required ASA configurations to meet the requirements.
New additional connectivity requirements:
Once the correct ASA configurations have been configured:
To access ASDM, click the ASA icon in the topology diagram.
To access the Firefox Browser on the Outside PC, click the Outside PC icon in the topology diagram.
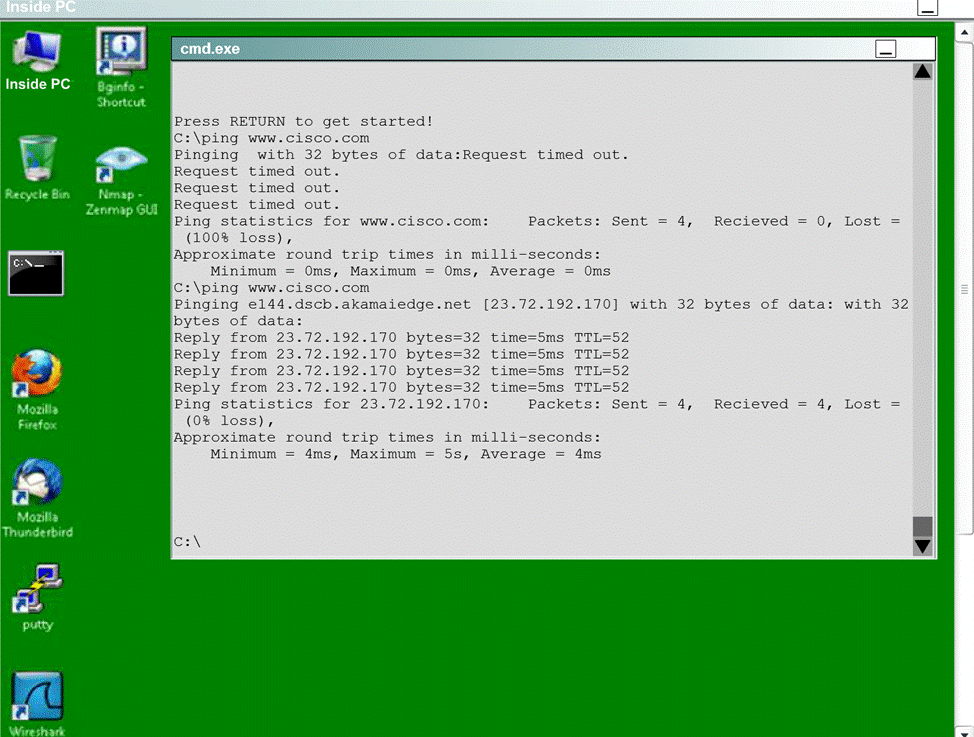
To access the Command prompt on the Inside PC, click the Inside PC icon in the topology diagram.
Note:
After you make the configuration changes in ASDM, remember to click Apply to apply the configuration changes.
Not all ASDM screens are enabled in this simulation, if some screen is not enabled, try to use different methods to configure the ASA to meet the requirements.
In this simulation, some of the ASDM screens may not look and function exactly like the real ASDM.
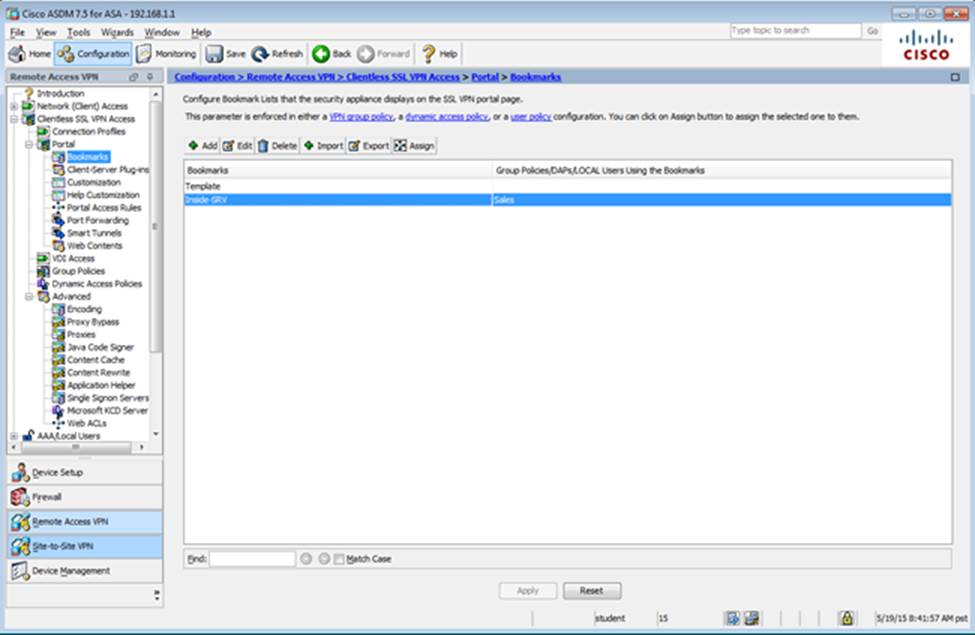
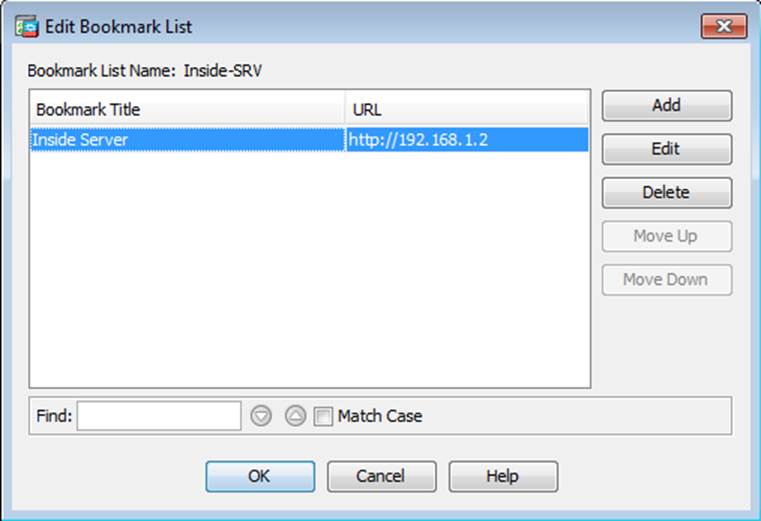
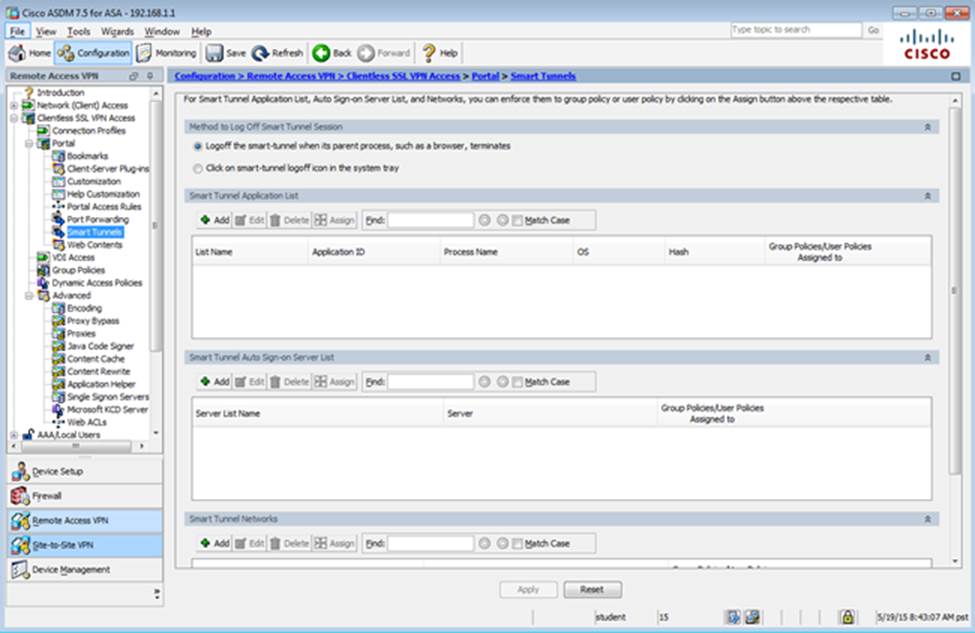
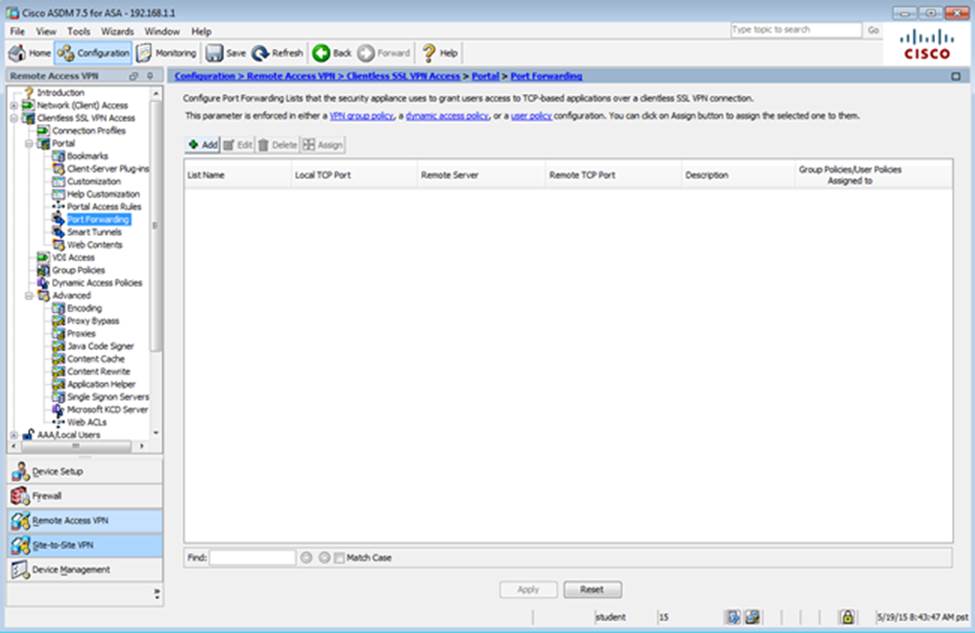
What features can protect the data plane? (Choose three.)
- A . policing
- B . ACLs
- C . IPS
- D . antispoofing
- E . QoS
- F . DHCP-snooping
How many crypto map sets can you apply to a router interface?
- A . 3
- B . 2
- C . 4
- D . 1
What is the transition order of STP states on a Layer 2 switch interface?
- A . listening, learning, blocking, forwarding, disabled
- B . listening, blocking, learning, forwarding, disabled
- C . blocking, listening, learning, forwarding, disabled
- D . forwarding, listening, learning, blocking, disabled
Which sensor mode can deny attackers inline?
- A . IPS
- B . fail-close
- C . IDS
- D . fail-open
Which options are filtering options used to display SDEE message types? (Choose two.)
- A . stop
- B . none
- C . error
- D . all
When a company puts a security policy in place, what is the effect on the company’s business?
- A . Minimizing risk
- B . Minimizing total cost of ownership
- C . Minimizing liability
- D . Maximizing compliance
Which wildcard mask is associated with a subnet mask of /27?
- A . 0.0.0.31
- B . 0.0.027
- C . 0.0.0.224
- D . 0.0.0.255
Which statements about reflexive access lists are true? (Choose three.)
- A . Reflexive access lists create a permanent ACE
- B . Reflexive access lists approximate session filtering using the established keyword
- C . Reflexive access lists can be attached to standard named IP ACLs
- D . Reflexive access lists support UDP sessions
- E . Reflexive access lists can be attached to extended named IP ACLs
- F . Reflexive access lists support TCP sessions
Which actions can a promiscuous IPS take to mitigate an attack? (Choose three.)
- A . Modifying packets
- B . Requesting connection blocking
- C . Denying packets
- D . Resetting the TCP connection
- E . Requesting host blocking
- F . Denying frames
Latest 210-260 Dumps Valid Version with 498 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund




Hello. And Bye.