Cisco 210-260 Implementing Cisco Network Security Online Training
Cisco 210-260 Online Training
The questions for 210-260 were last updated at Feb 22,2026.
- Exam Code: 210-260
- Exam Name: Implementing Cisco Network Security
- Certification Provider: Cisco
- Latest update: Feb 22,2026
What can the SMTP preprocessor in FirePOWER normalize?
- A . It can extract and decode email attachments in client to server traffic.
- B . It can look up the email sender.
- C . It compares known threats to the email sender.
- D . It can forward the SMTP traffic to an email filter server.
- E . It uses the Traffic Anomaly Detector.
You want to allow all of your company’s users to access the Internet without allowing other Web servers to collect the IP addresses of individual users.
What two solutions can you use? (Choose two).
- A . Configure a proxy server to hide users’ local IP addresses.
- B . Assign unique IP addresses to all users.
- C . Assign the same IP address to all users.
- D . Install a Web content filter to hide users’ local IP addresses.
- E . Configure a firewall to use Port Address Translation.
You have implemented a Sourcefire IPS and configured it to block certain addresses utilizing Security Intelligence IP Address Reputation. A user calls and is not able to access a certain IP address.
What action can you take to allow the user access to the IP address?
- A . Create a whitelist and add the appropriate IP address to allow the traffic.
- B . Create a custom blacklist to allow the traffic.
- C . Create a user based access control rule to allow the traffic.
- D . Create a network based access control rule to allow the traffic.
- E . Create a rule to bypass inspection to allow the traffic.
A specific URL has been identified as containing malware.
What action can you take to block users from accidentally visiting the URL and becoming infected with malware.
- A . Enable URL filtering on the perimeter router and add the URLs you want to block to the router’s local URL list.
- B . Enable URL filtering on the perimeter firewall and add the URLs you want to allow to the router’s local URL list.
- C . Enable URL filtering on the perimeter router and add the URLs you want to allow to the firewall’s local URL list.
- D . Create a blacklist that contains the URL you want to block and activate the blacklist on the perimeter router.
- E . Create a whitelist that contains the URLs you want to allow and activate the whitelist on the perimeter router.
When is the best time to perform an anti-virus signature update?
- A . Every time a new update is available.
- B . When the local scanner has detected a new virus.
- C . When a new virus is discovered in the wild.
- D . When the system detects a browser hook.
Which statement about application blocking is true?
- A . It blocks access to specific programs.
- B . It blocks access to files with specific extensions.
- C . It blocks access to specific network addresses.
- D . It blocks access to specific network services.
Scenario
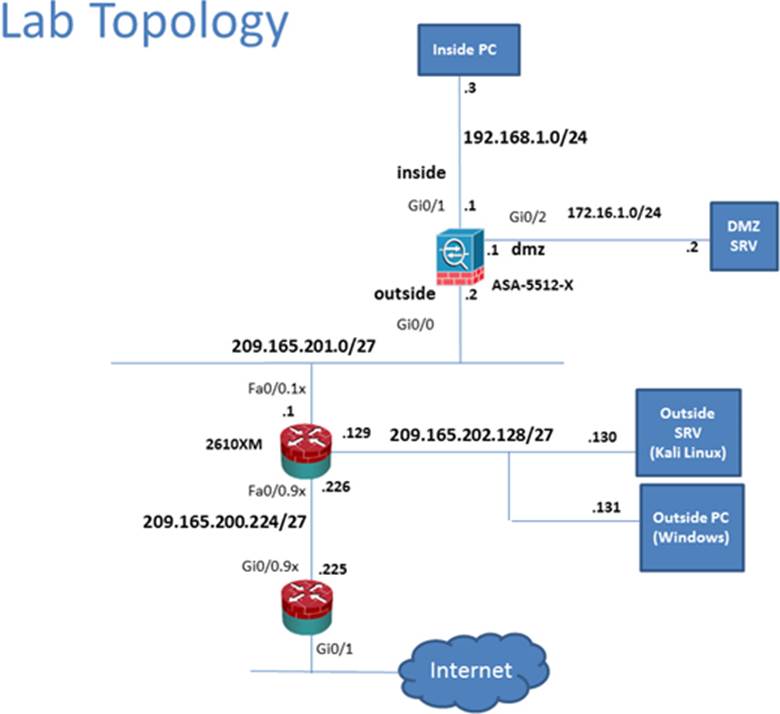
In this simulation, you have access to ASDM only. Review the various ASA configurations using ASDM then answer the five multiple choice questions about the ASA SSLVPN configurations.
To access ASDM, click the ASA icon in the topology diagram.
Note: Not all ASDM functionalities are enabled in this simulation.
To see all the menu options available on the left navigation pane, you may also need to un-expand the expanded menu first.
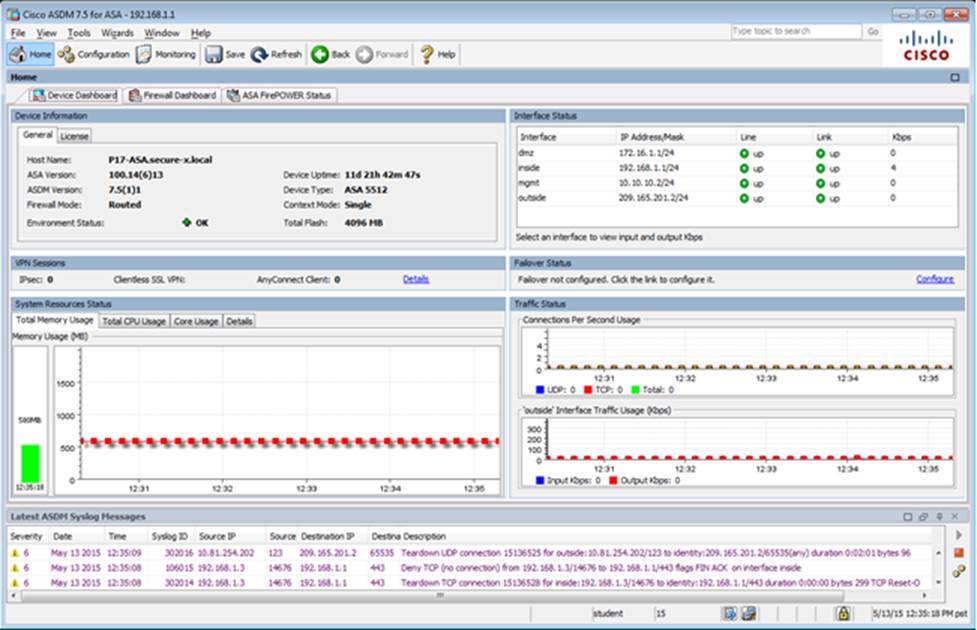
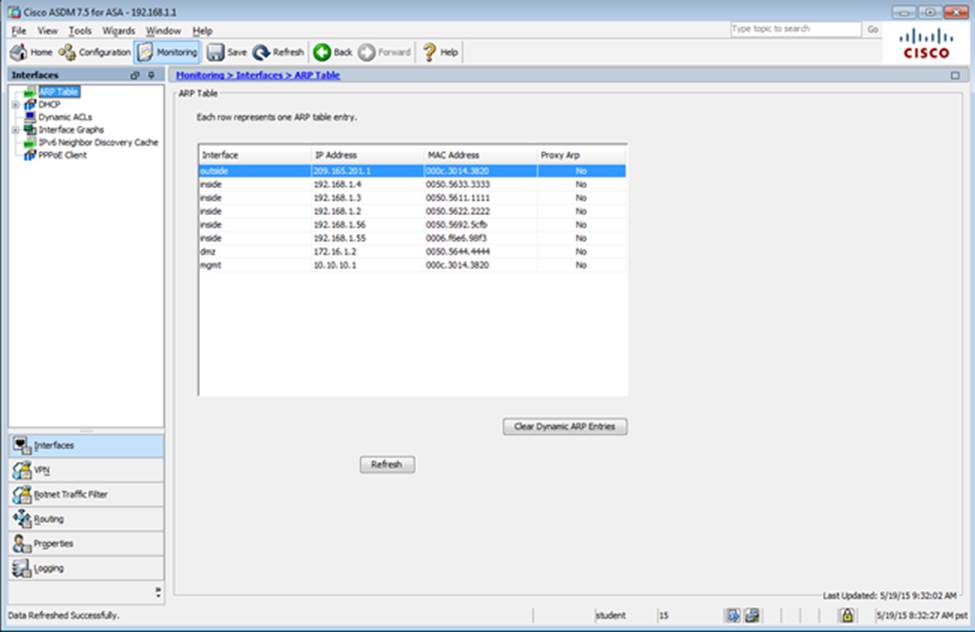
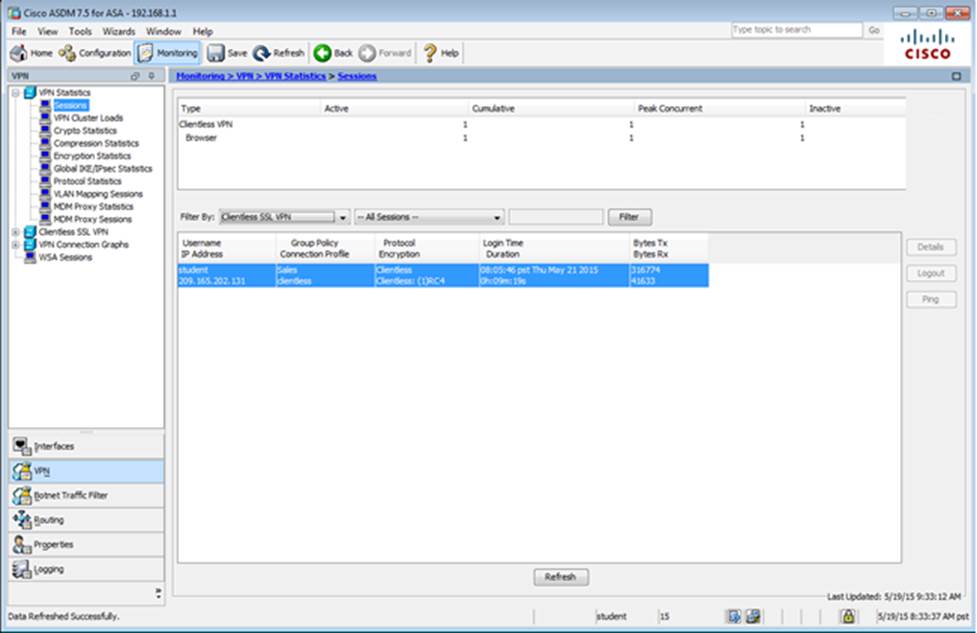


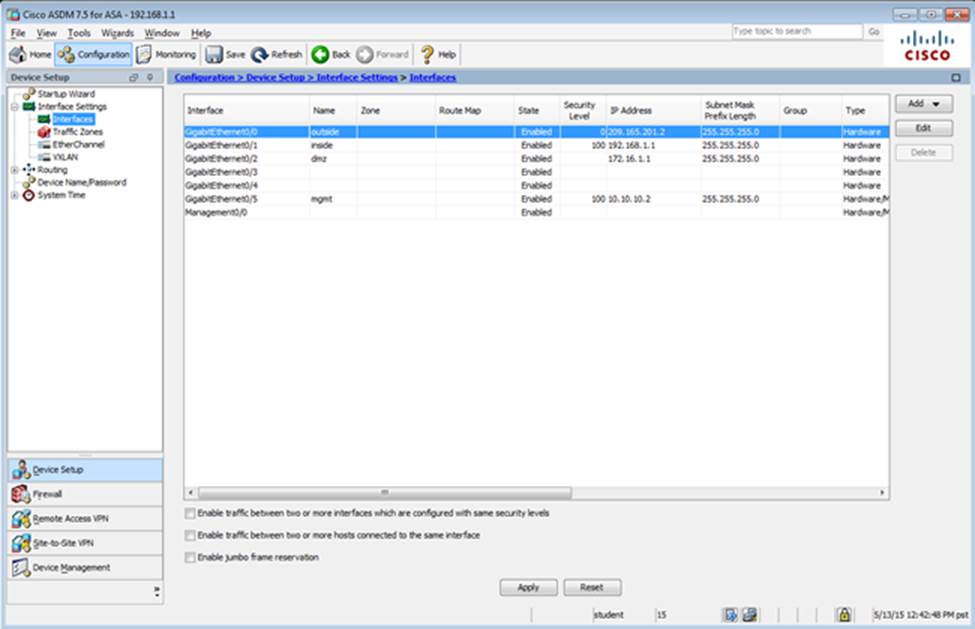
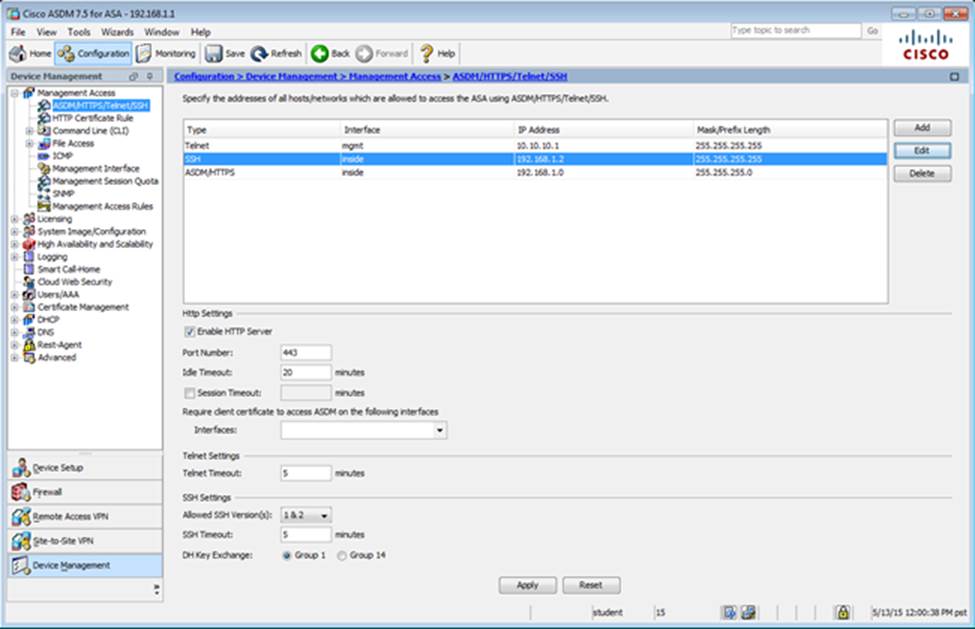


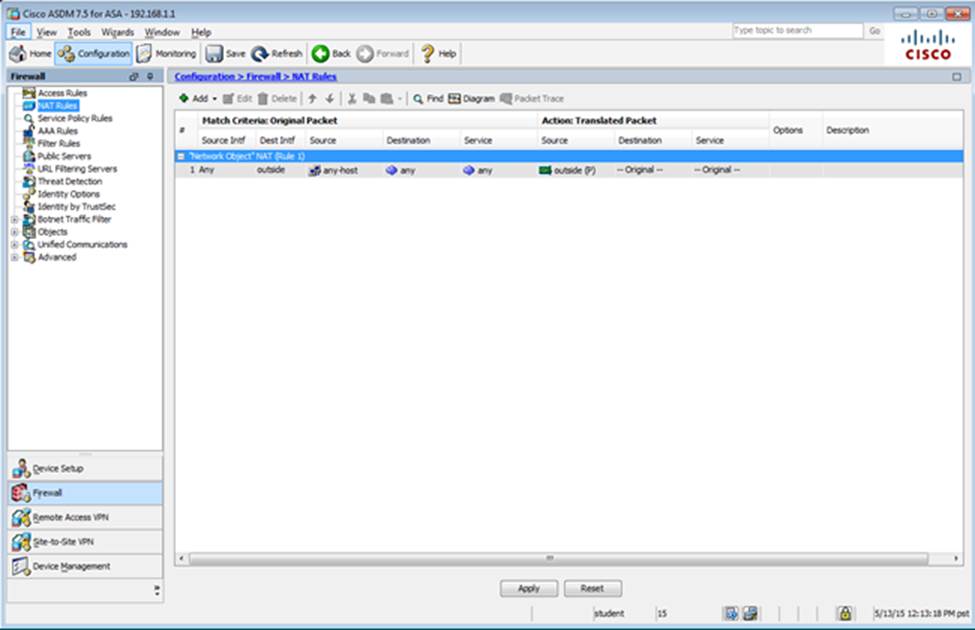

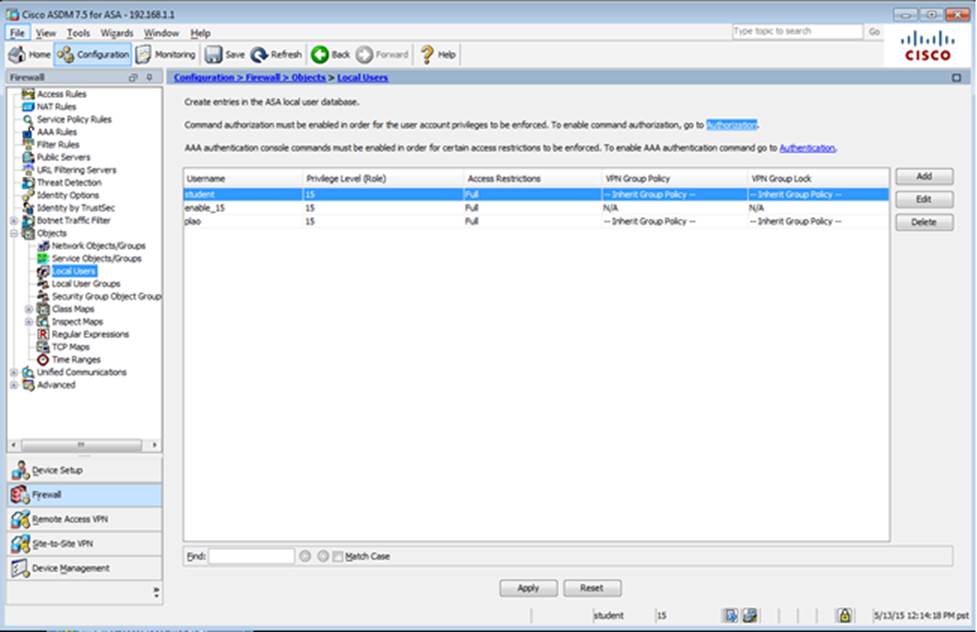
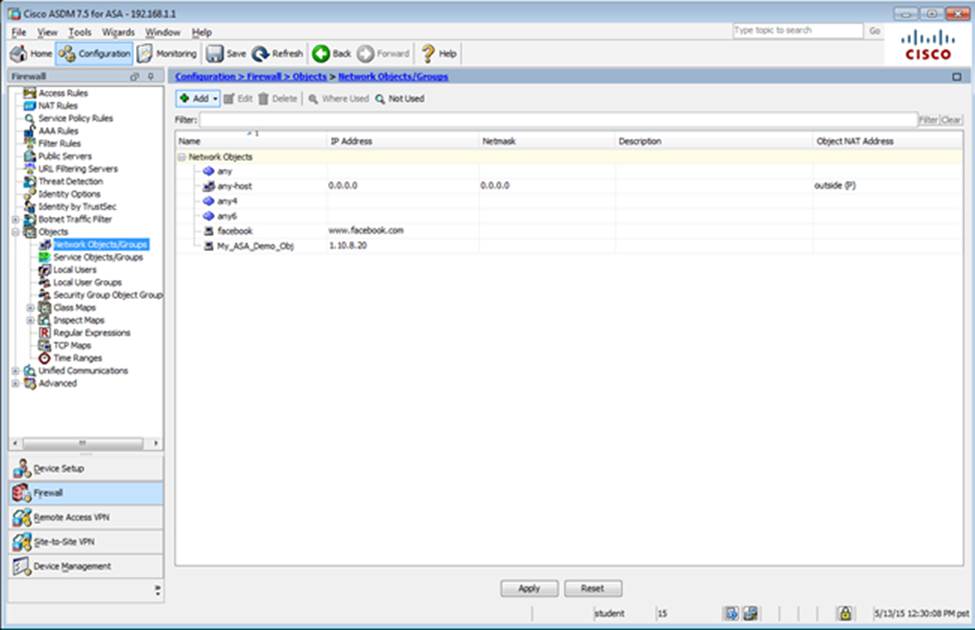

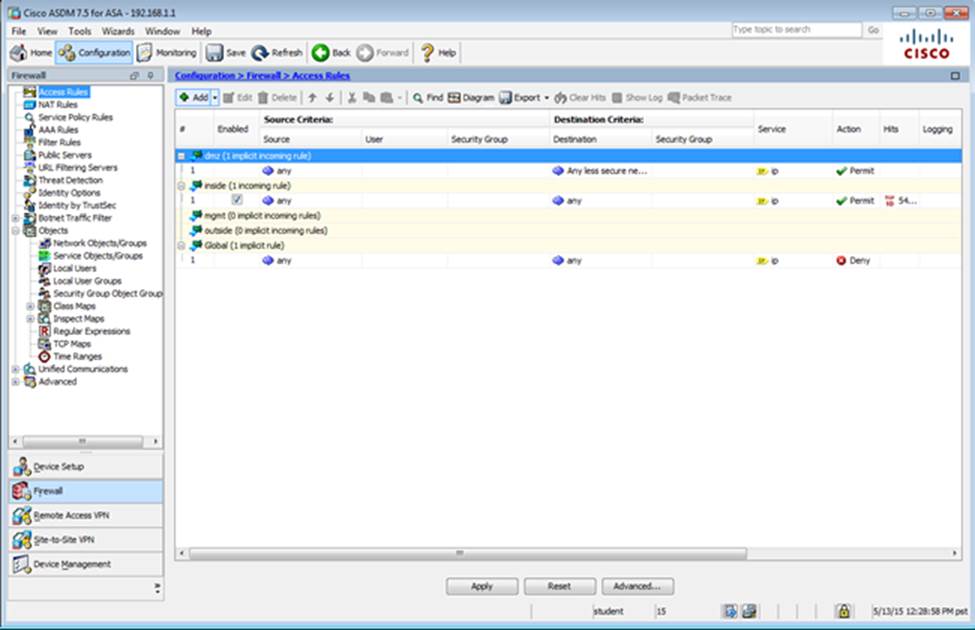
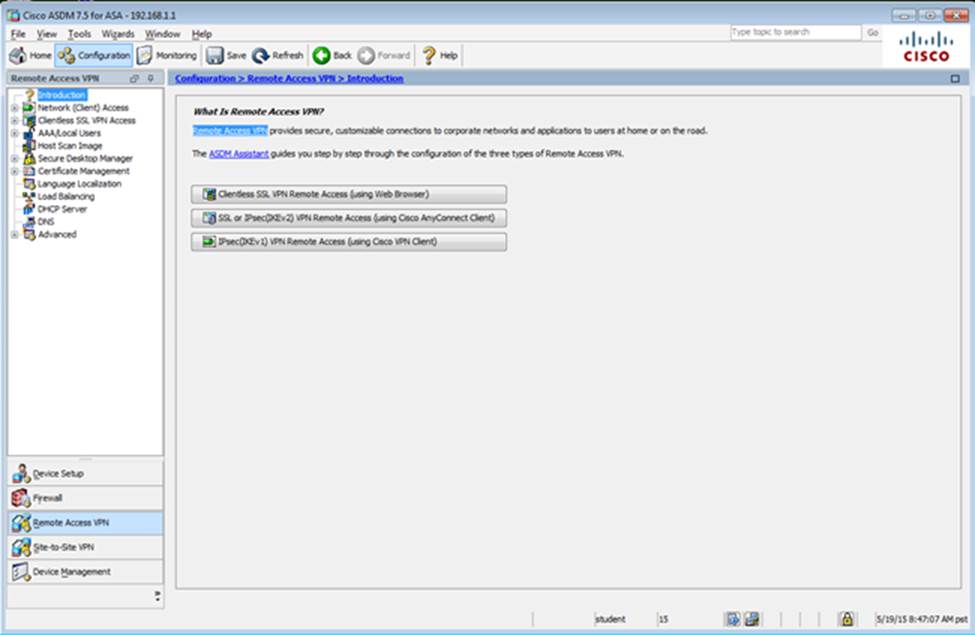
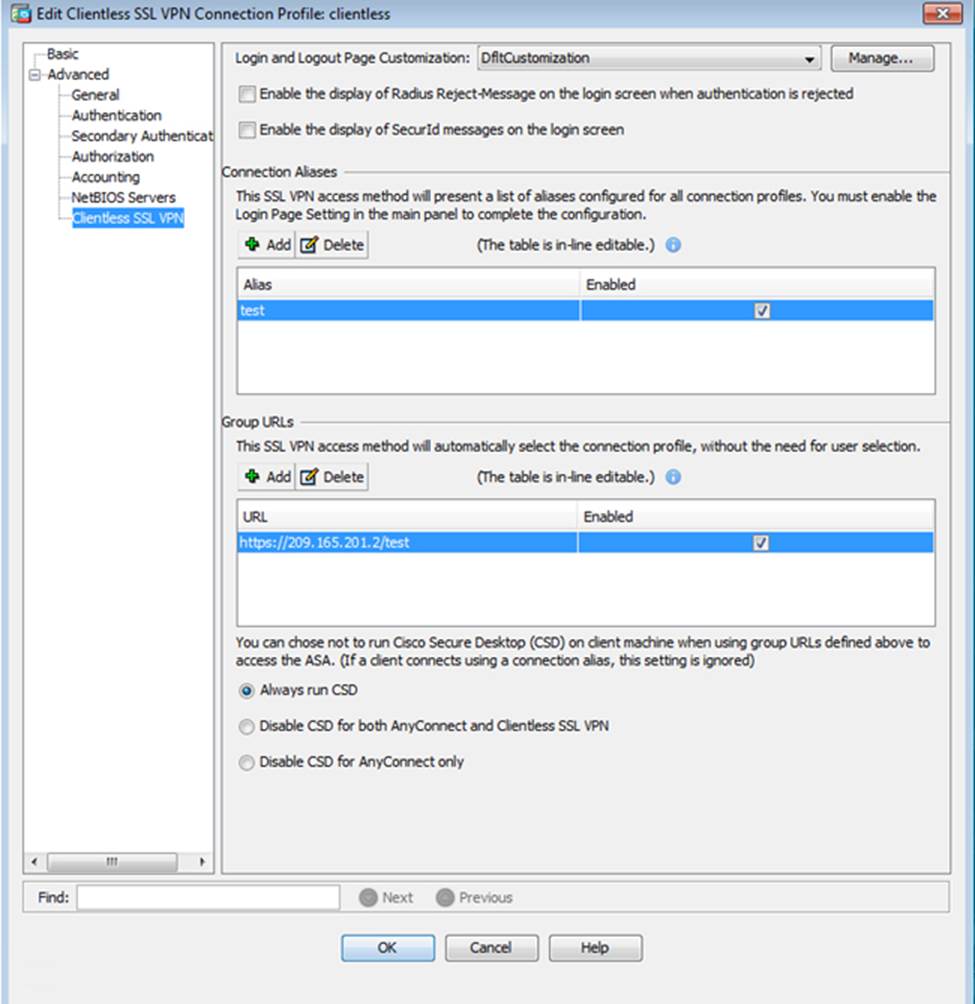
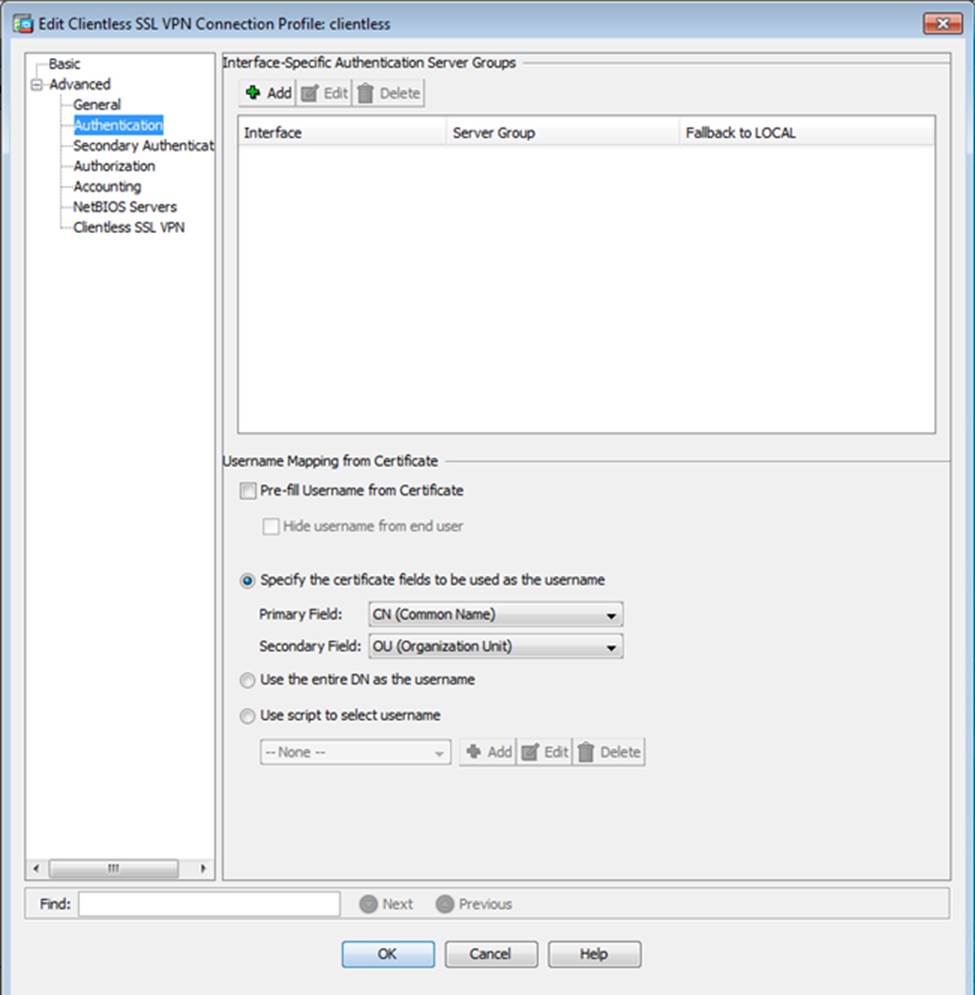
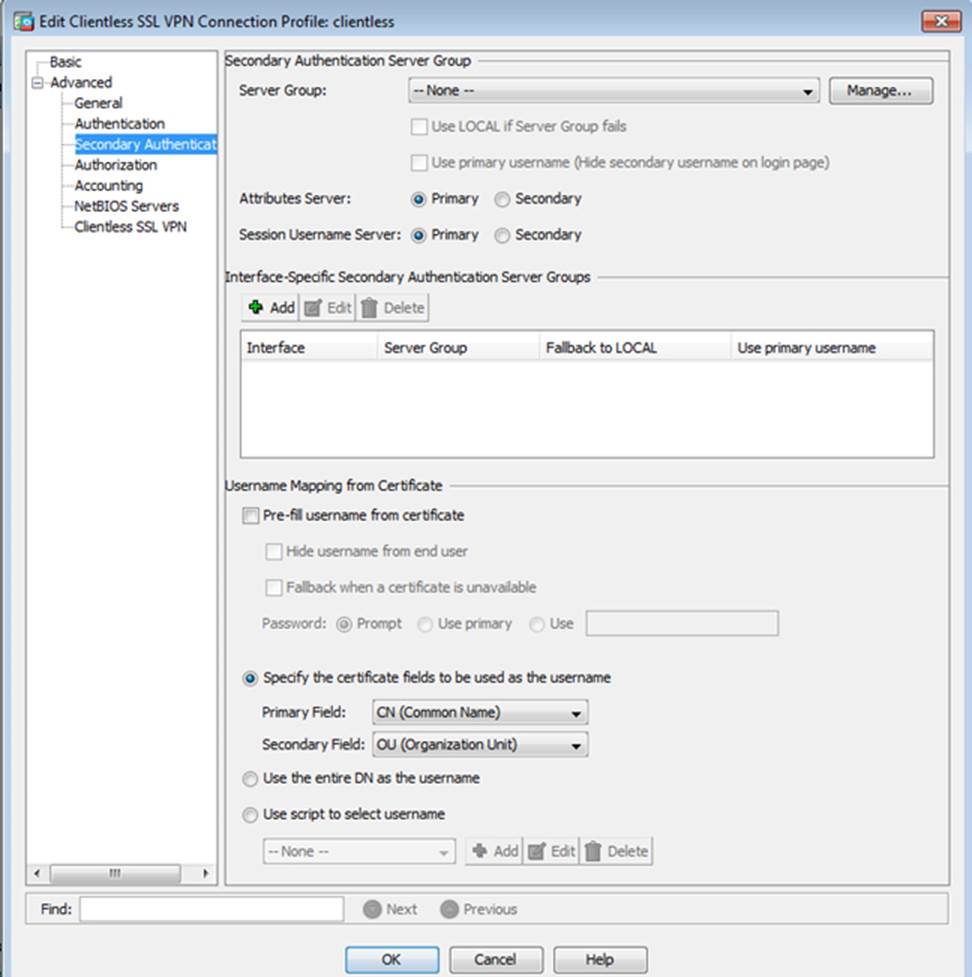
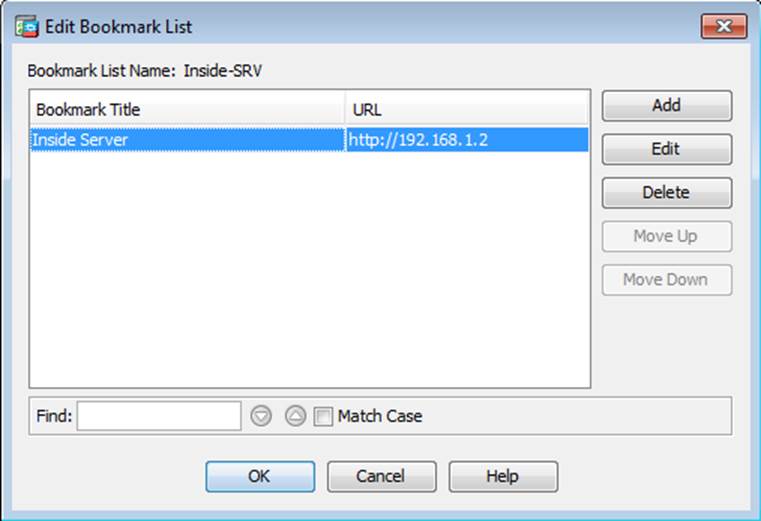
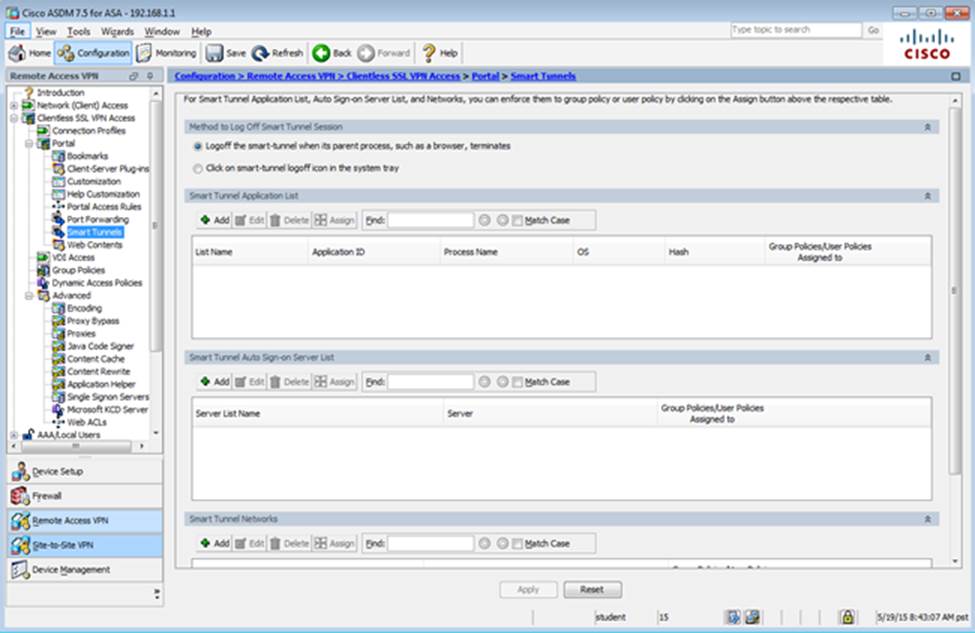
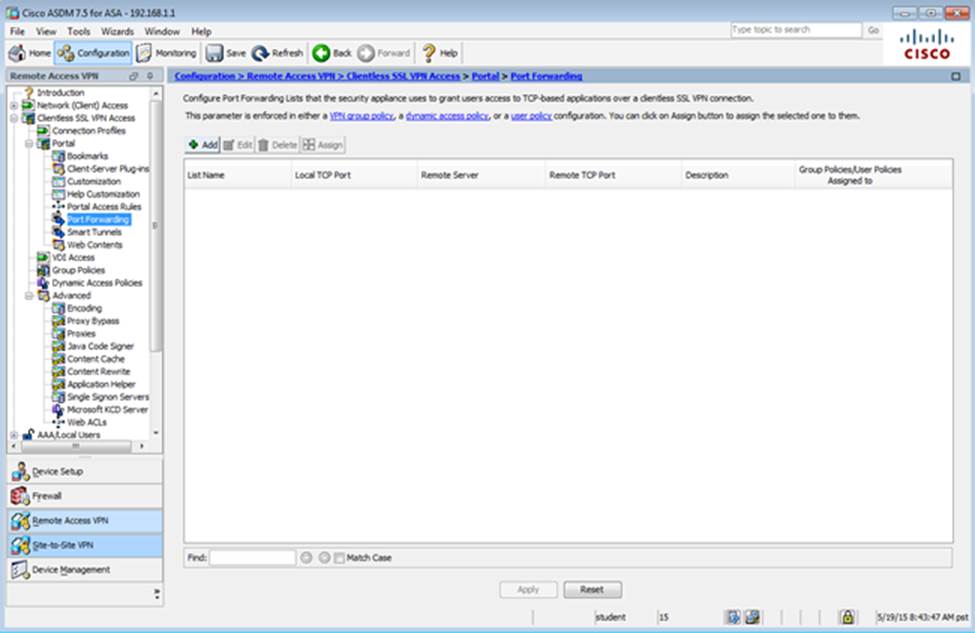
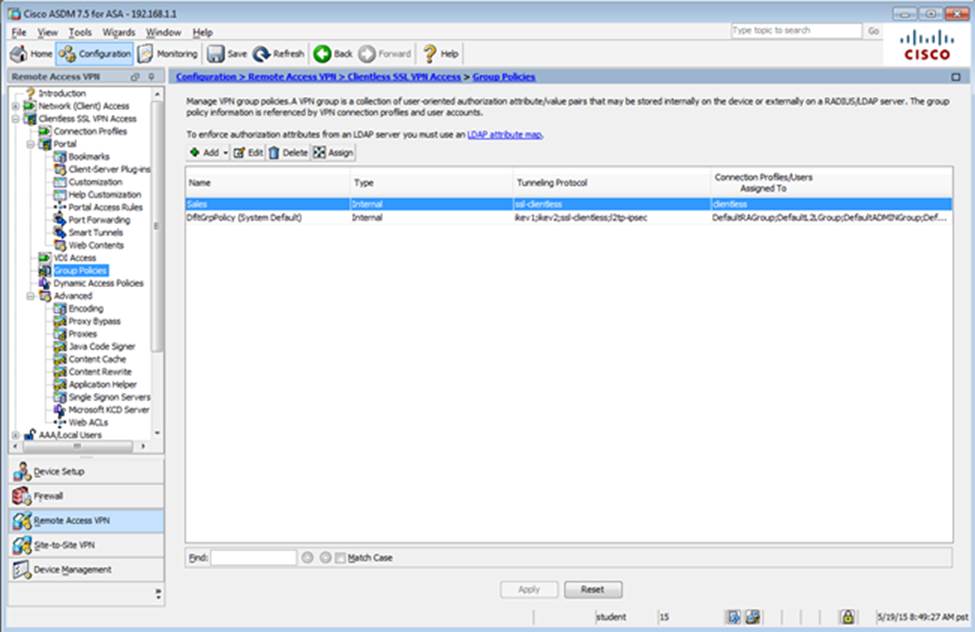
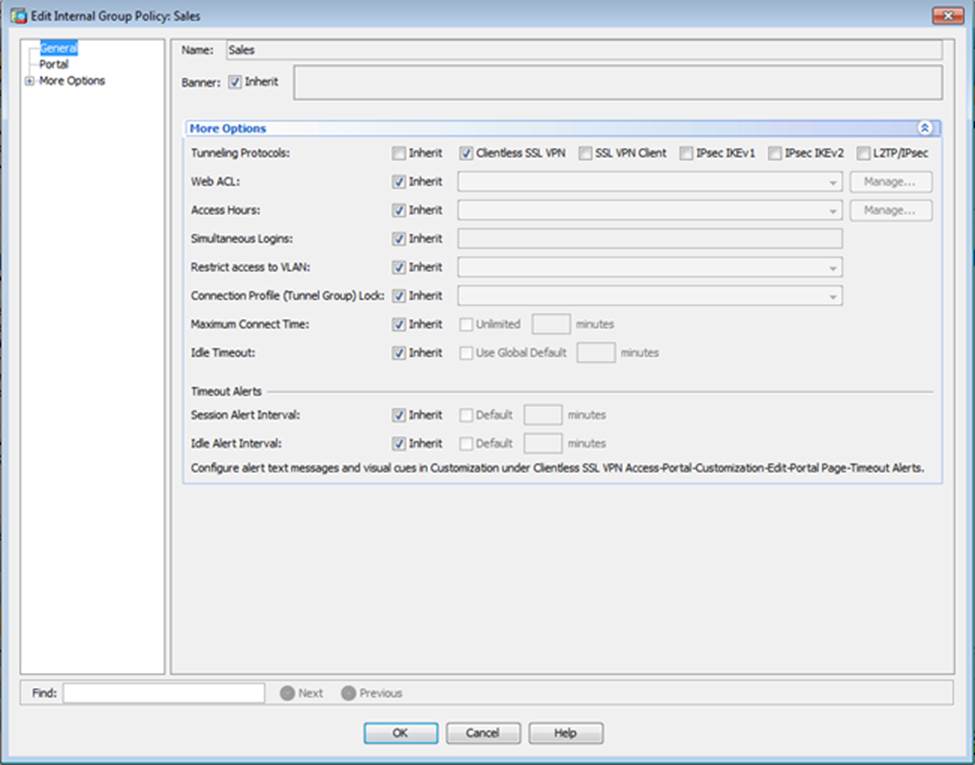
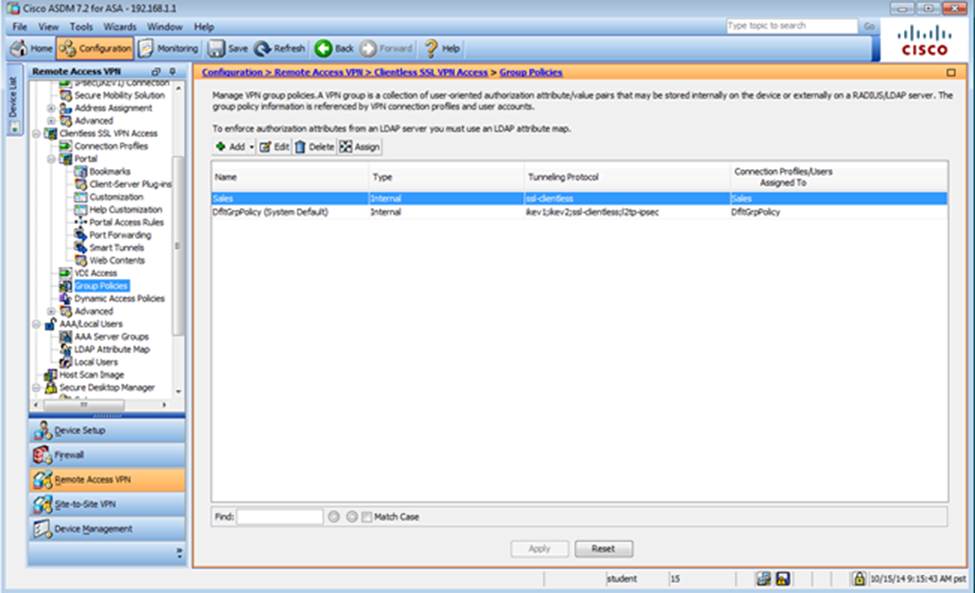
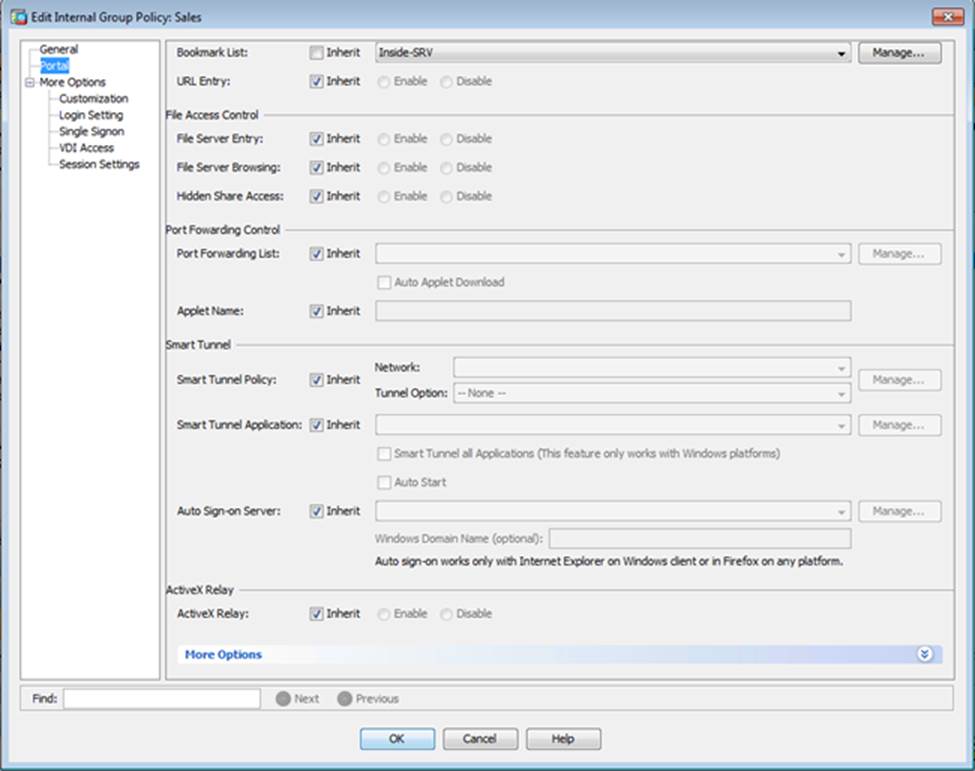
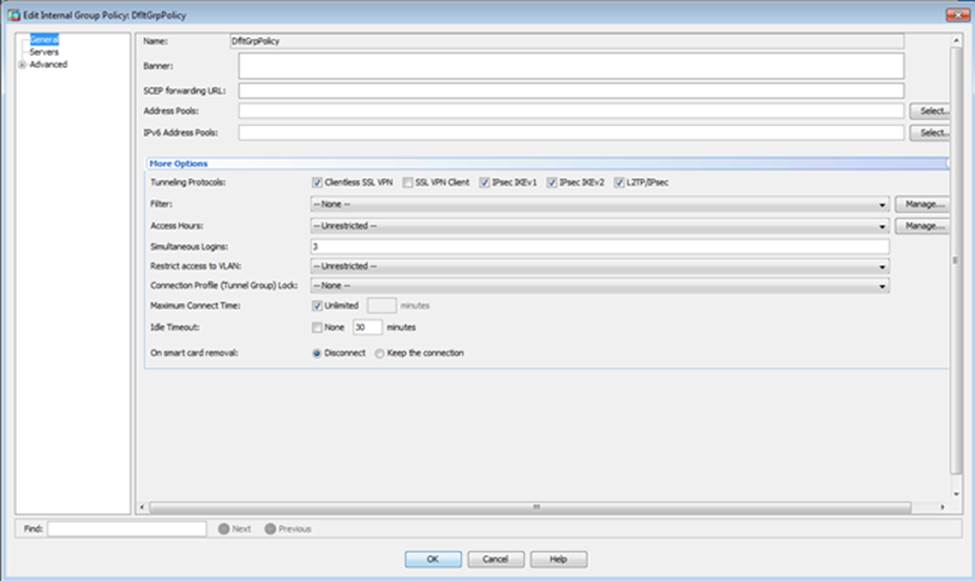
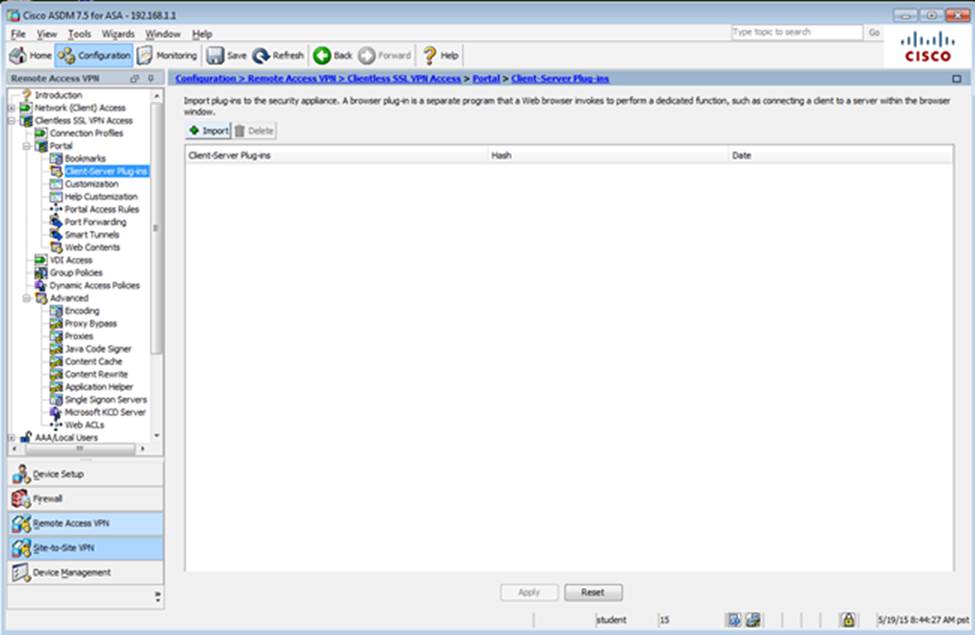
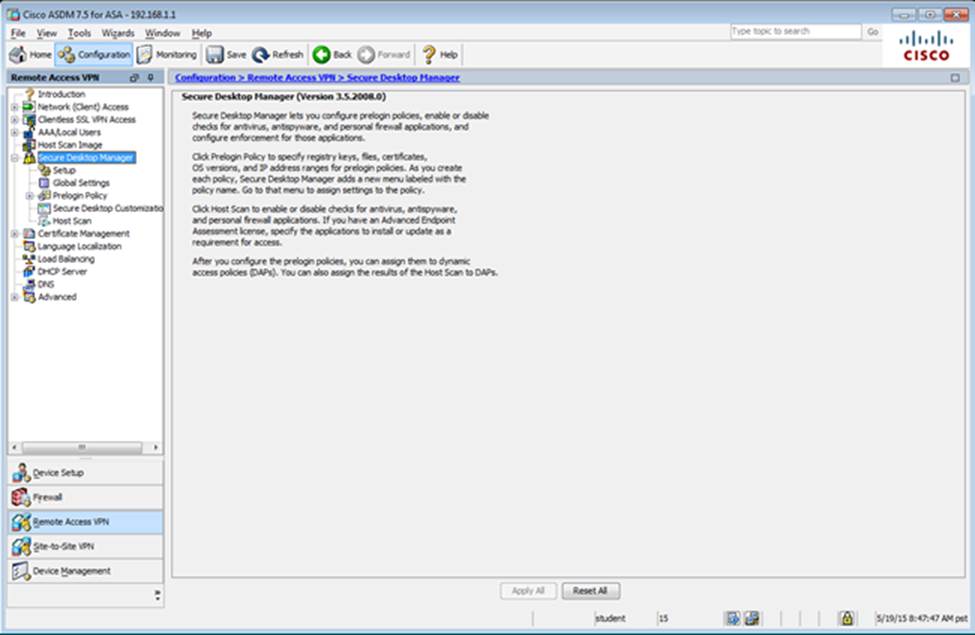



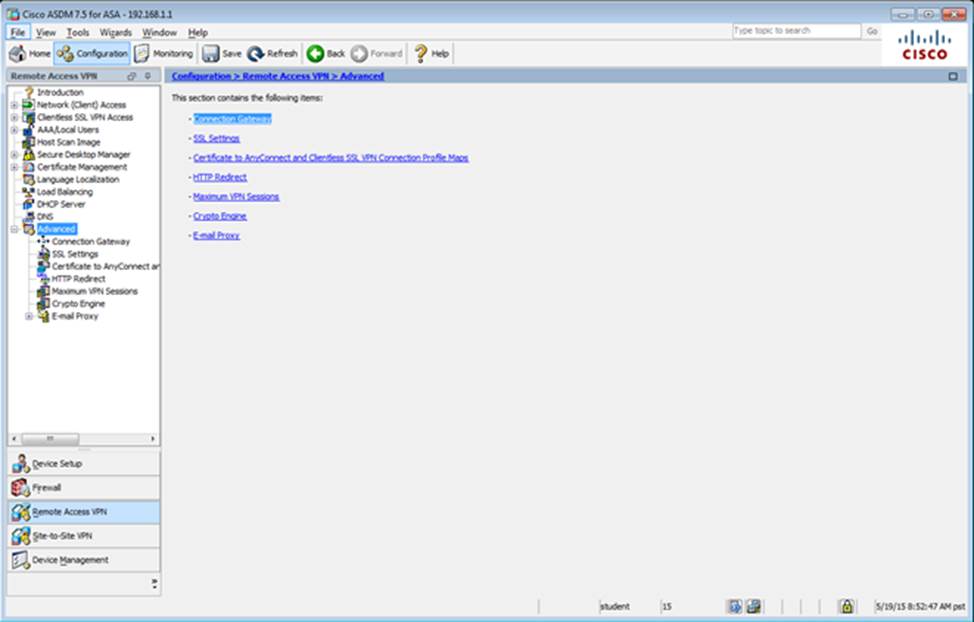
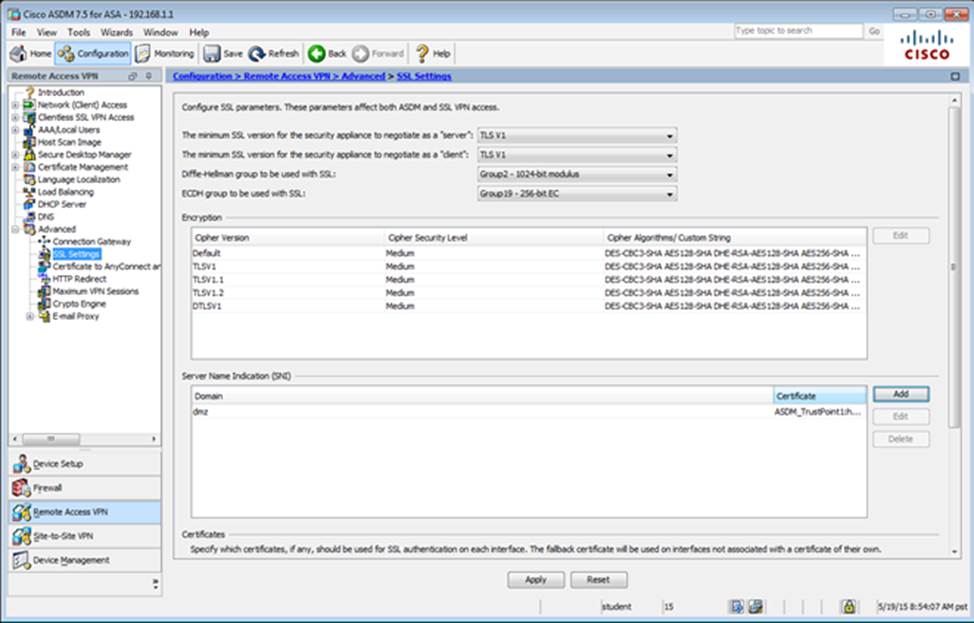
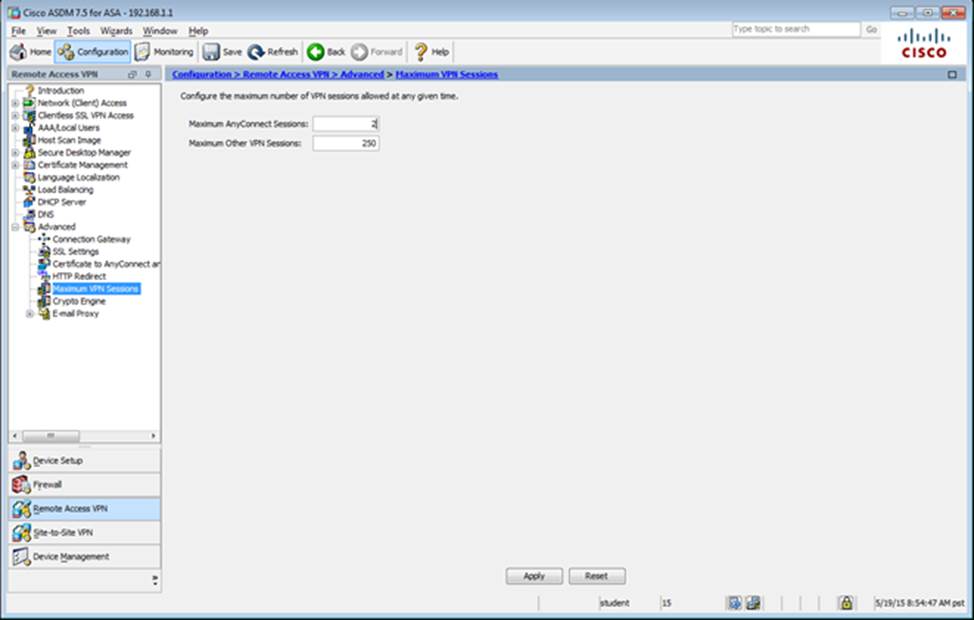

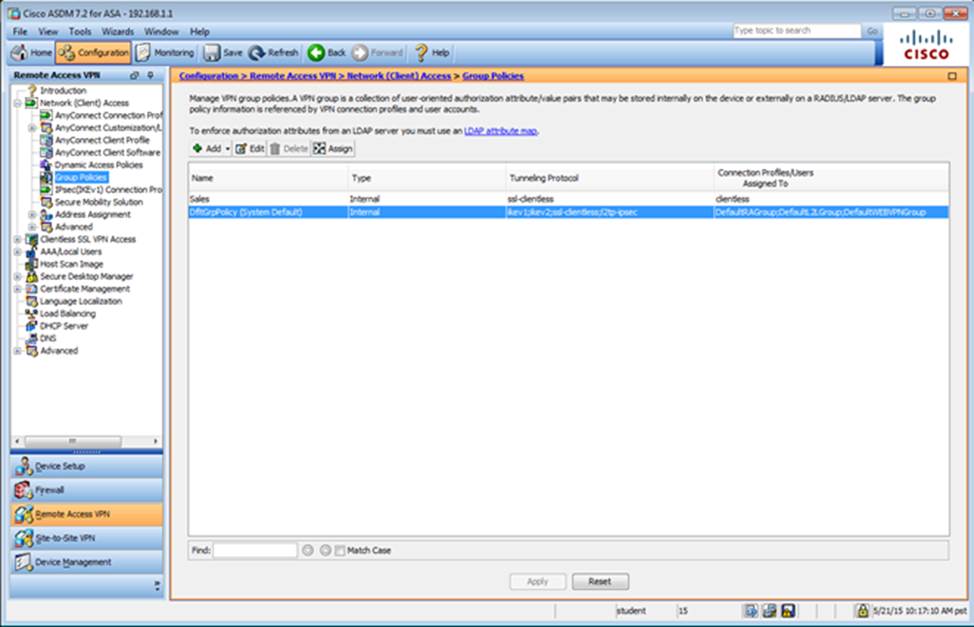
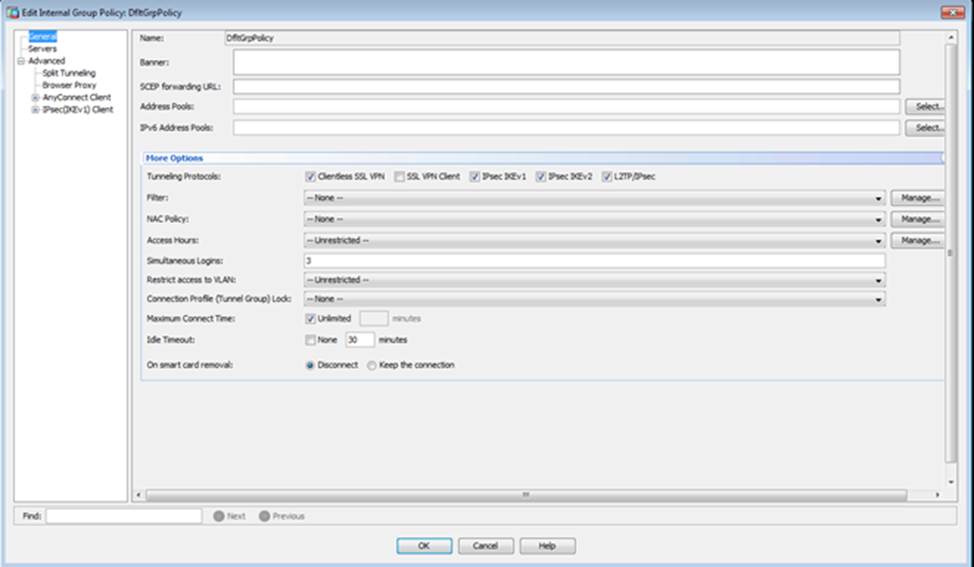
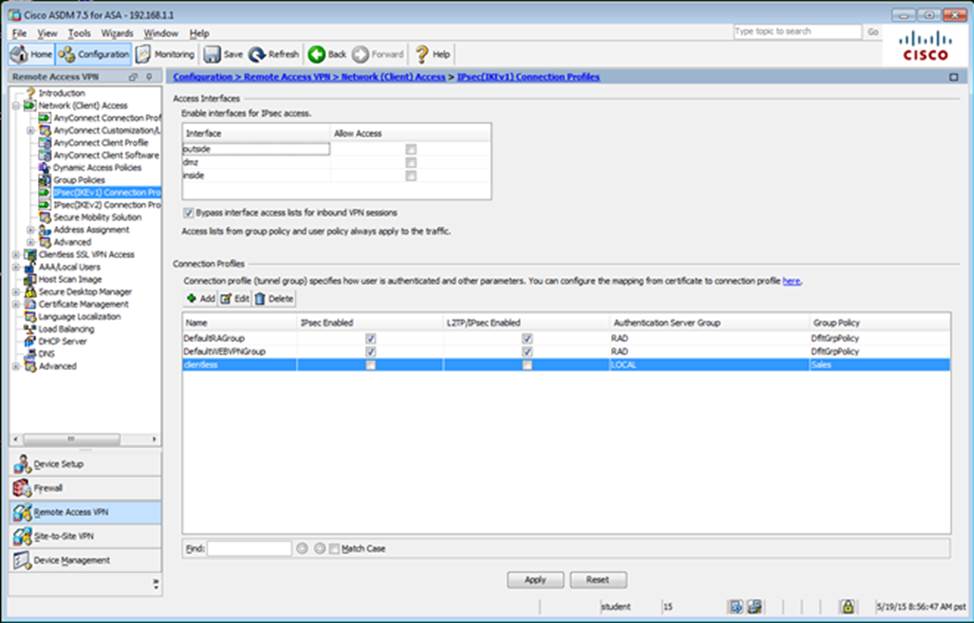
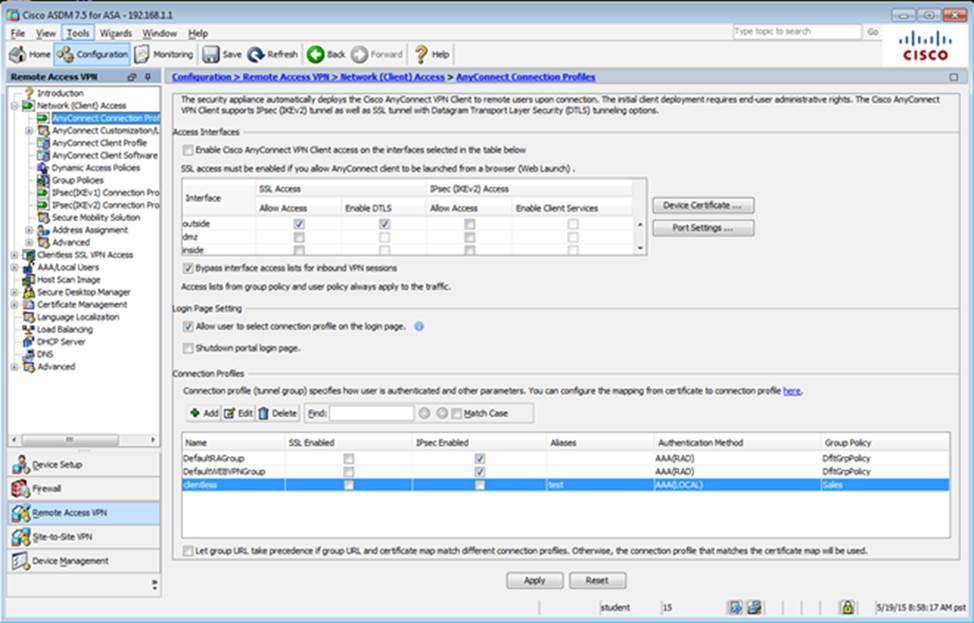

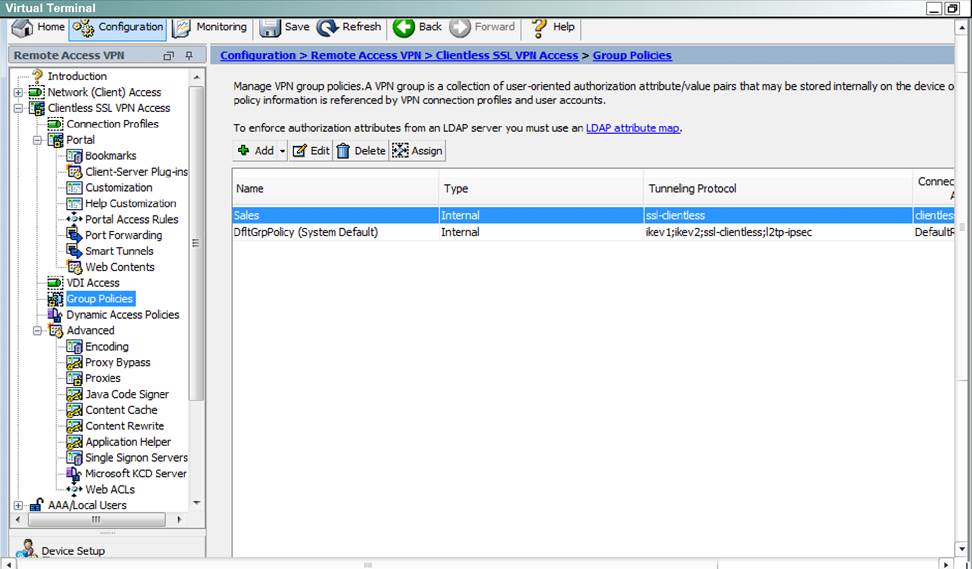
Which four tunneling protocols are enabled in the DfltGrpPolicy group policy? (Choose four)
- A . Clientless SSL VPN
- B . SSL VPN Client
- C . PPTP
- D . L2TP/IPsec
- E . IPsec IKEv1
- F . IPsec IKEv2
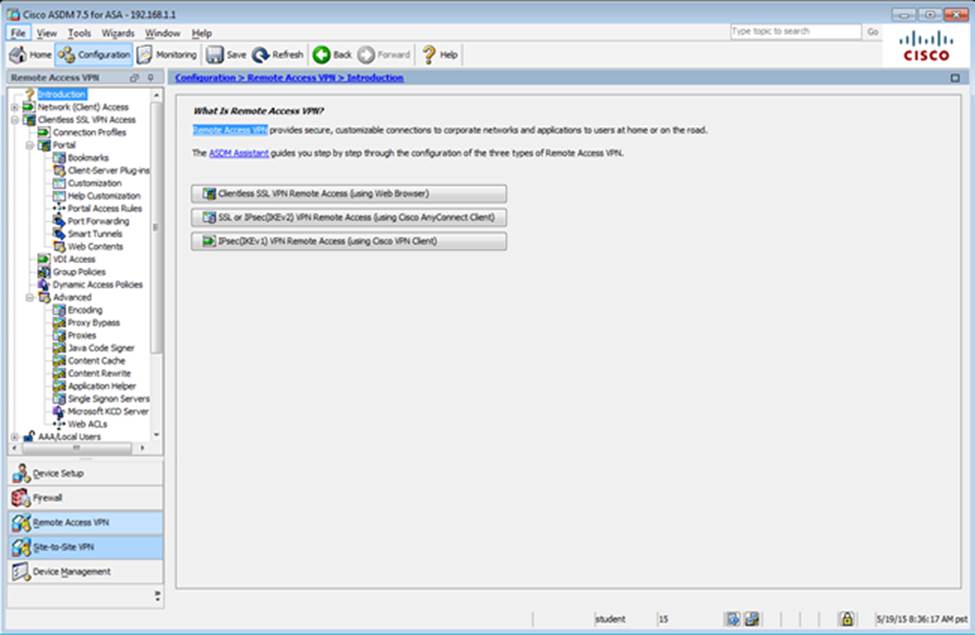
Scenario
In this simulation, you have access to ASDM only. Review the various ASA configurations using ASDM then answer the five multiple choice questions about the ASA SSLVPN configurations.
To access ASDM, click the ASA icon in the topology diagram.
Note: Not all ASDM functionalities are enabled in this simulation.
To see all the menu options available on the left navigation pane, you may also need to un-expand the expanded menu first.
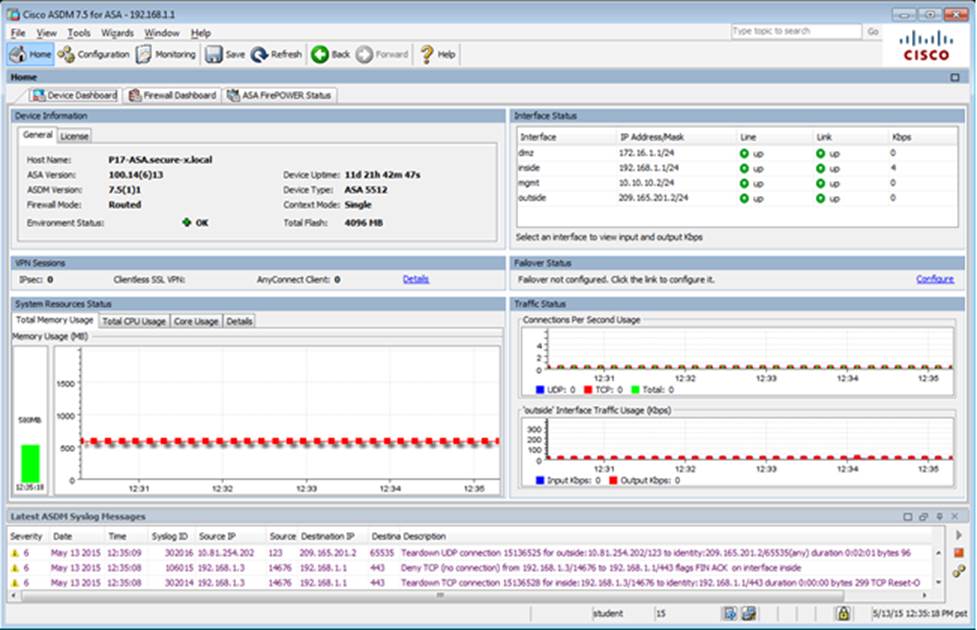
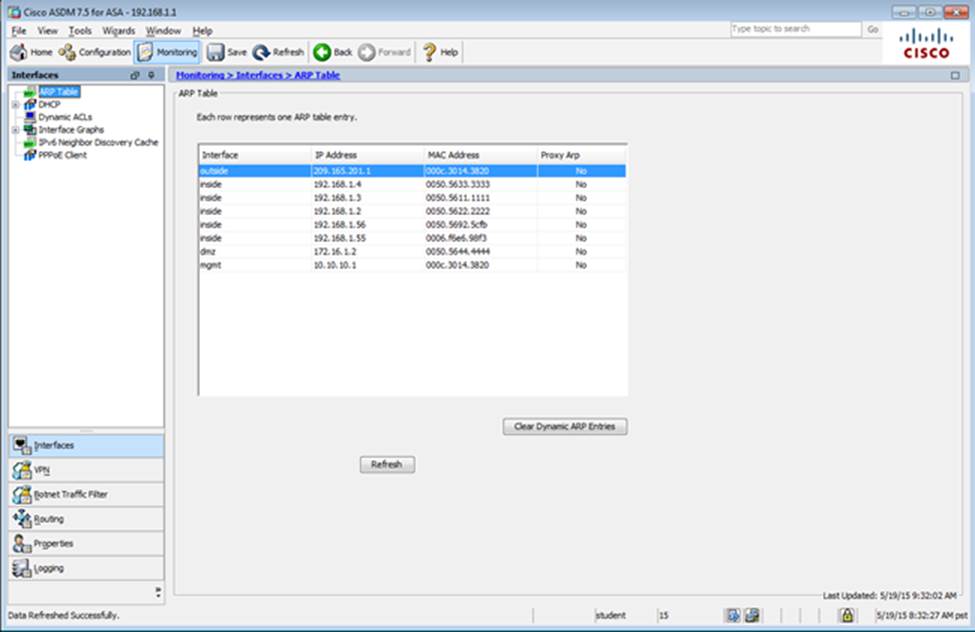
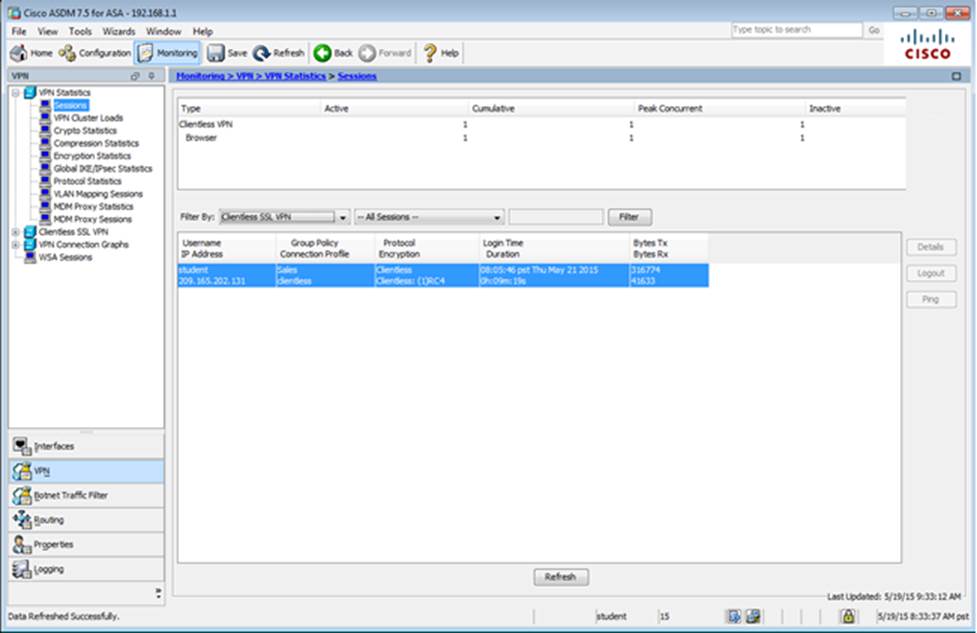

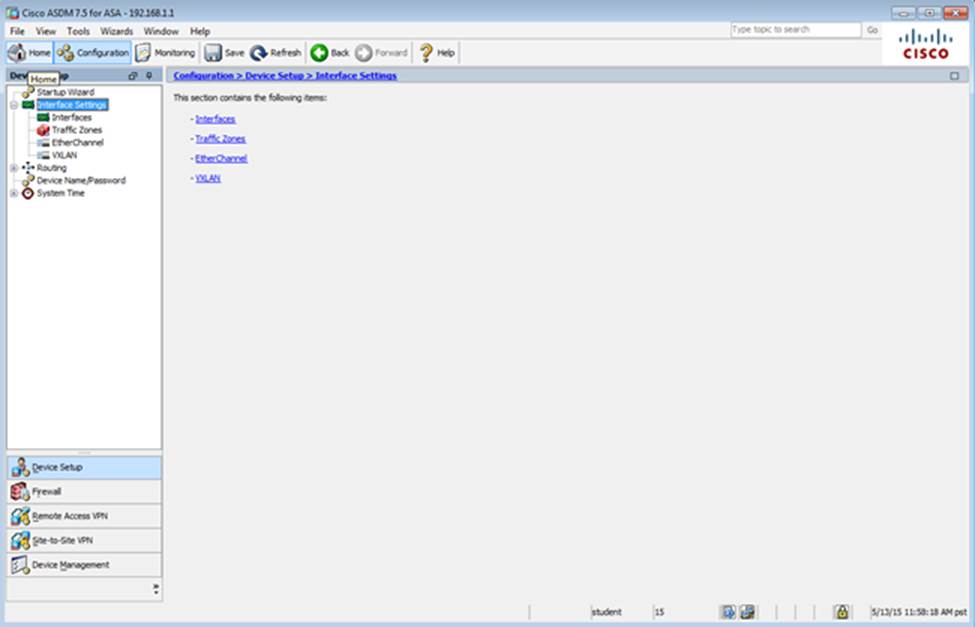
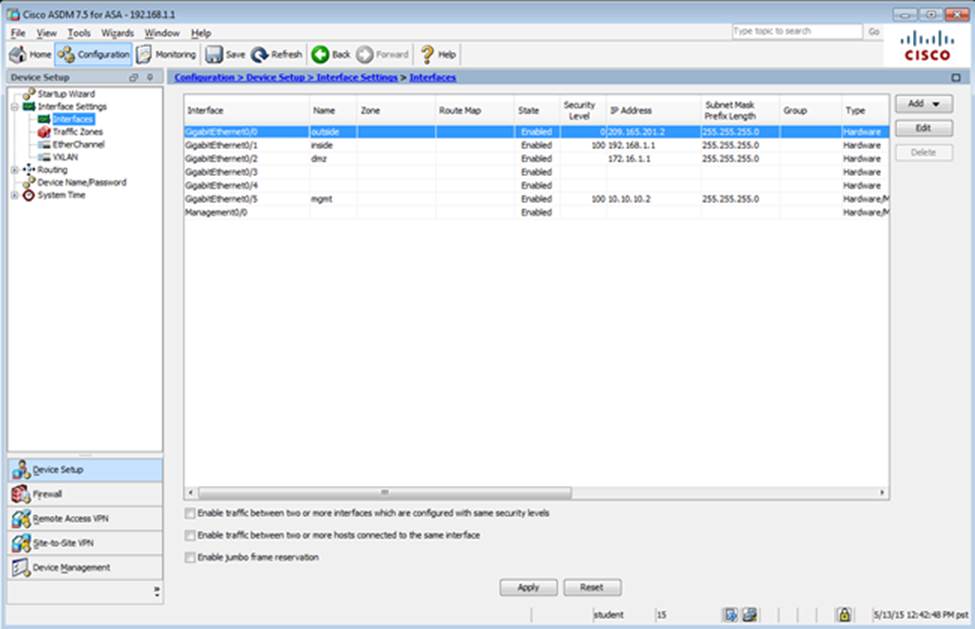
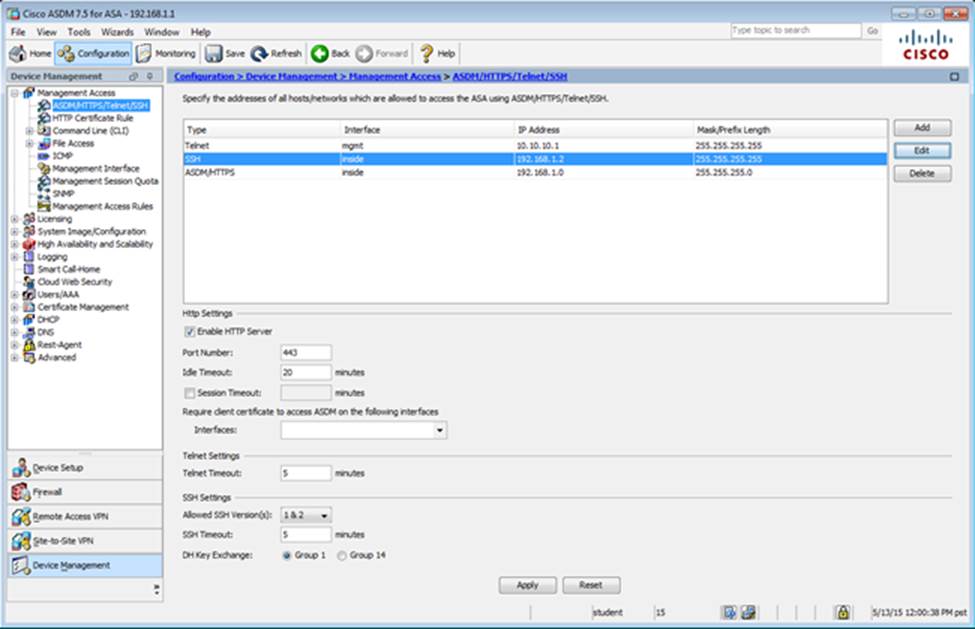
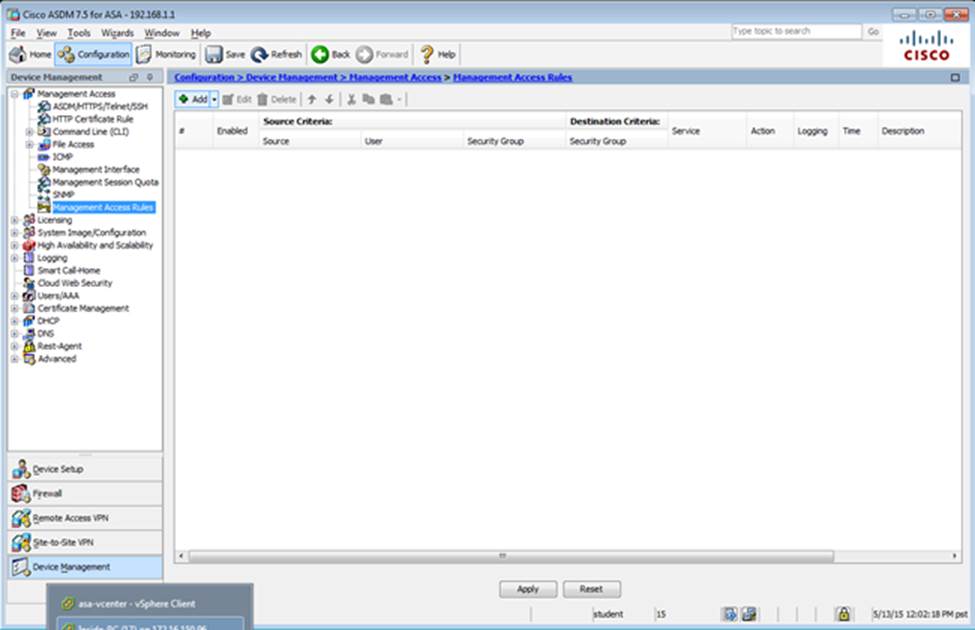
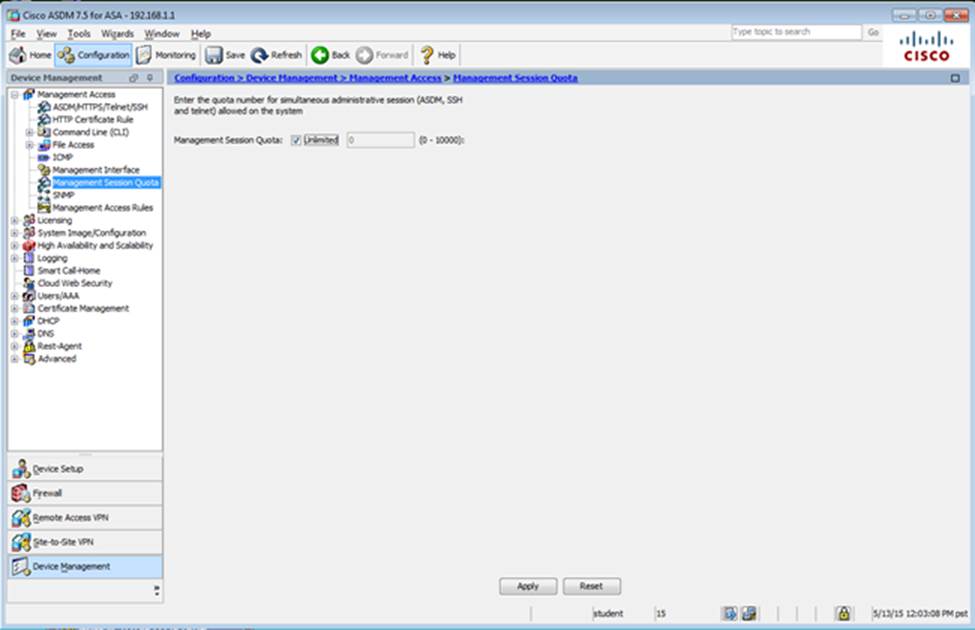
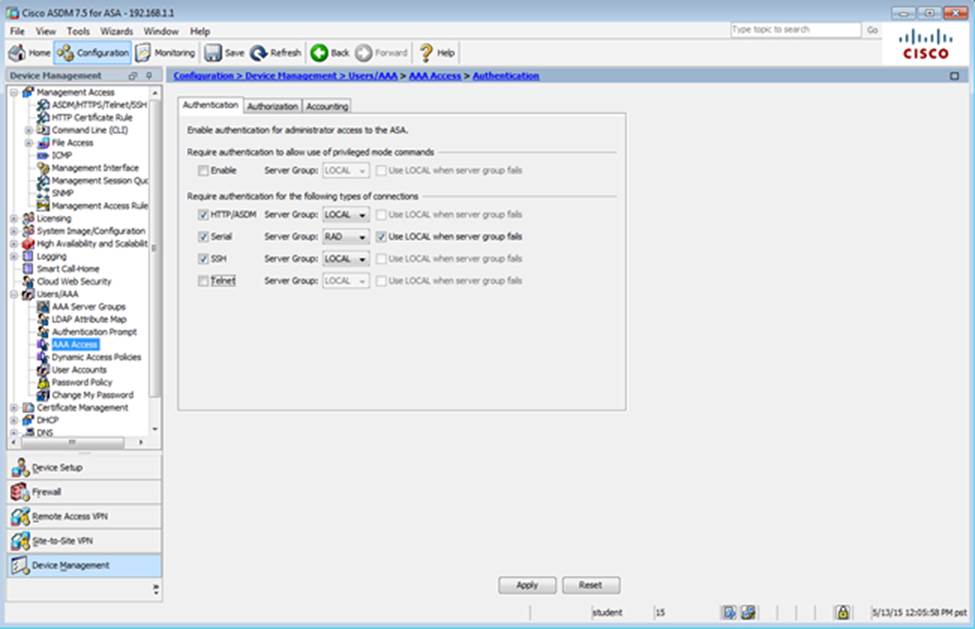
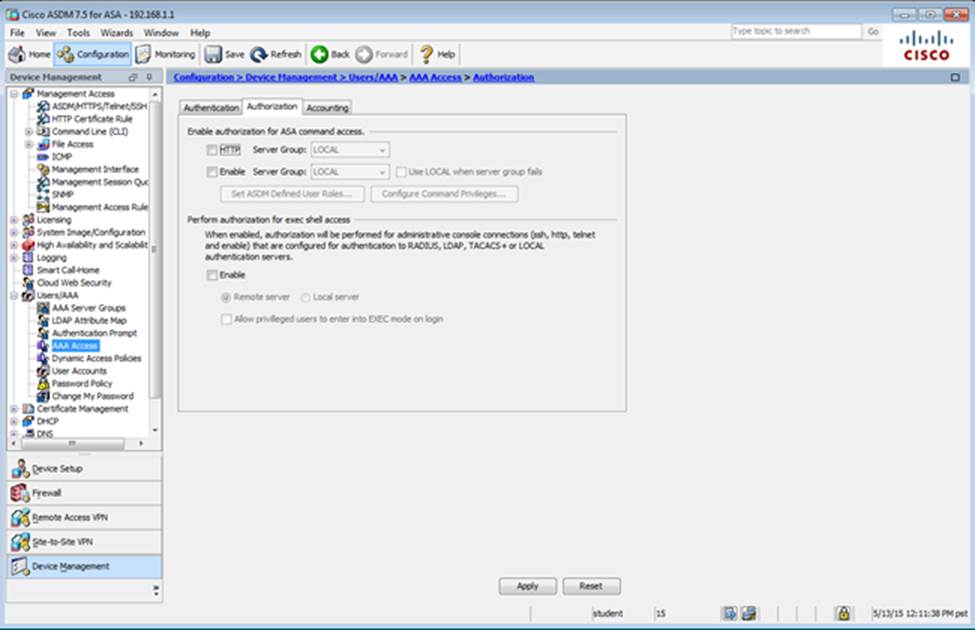
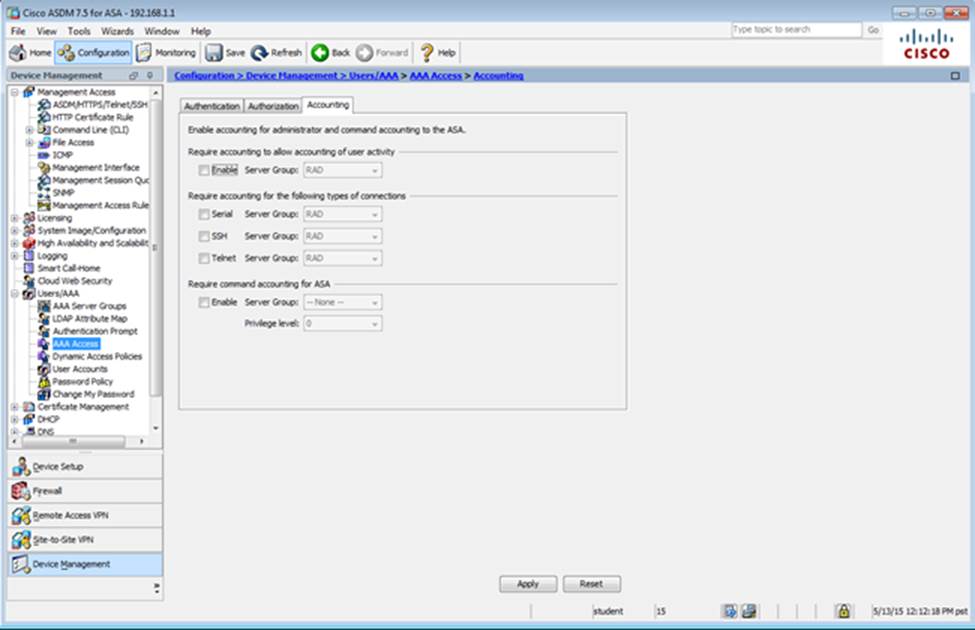
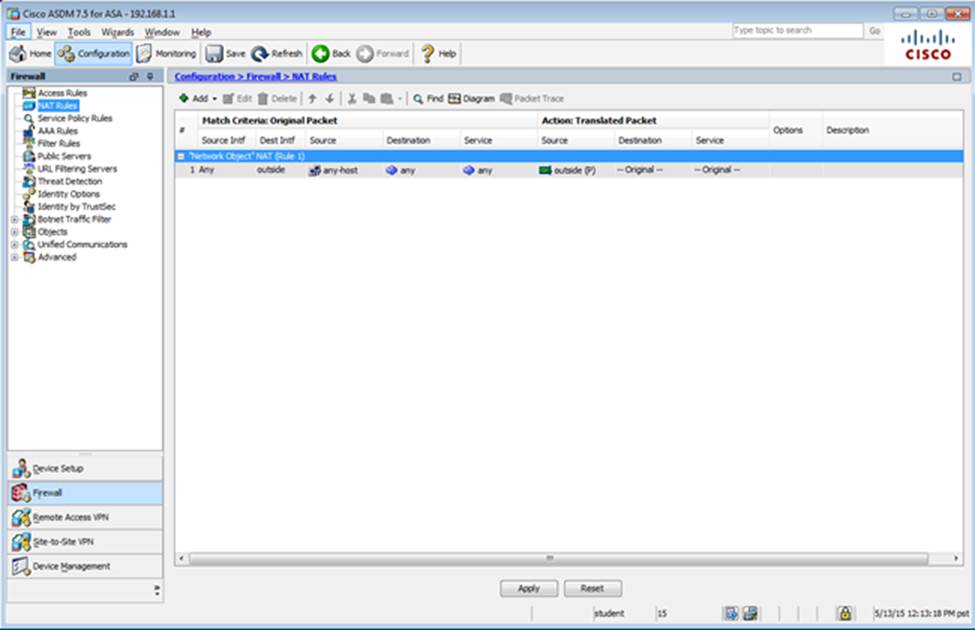
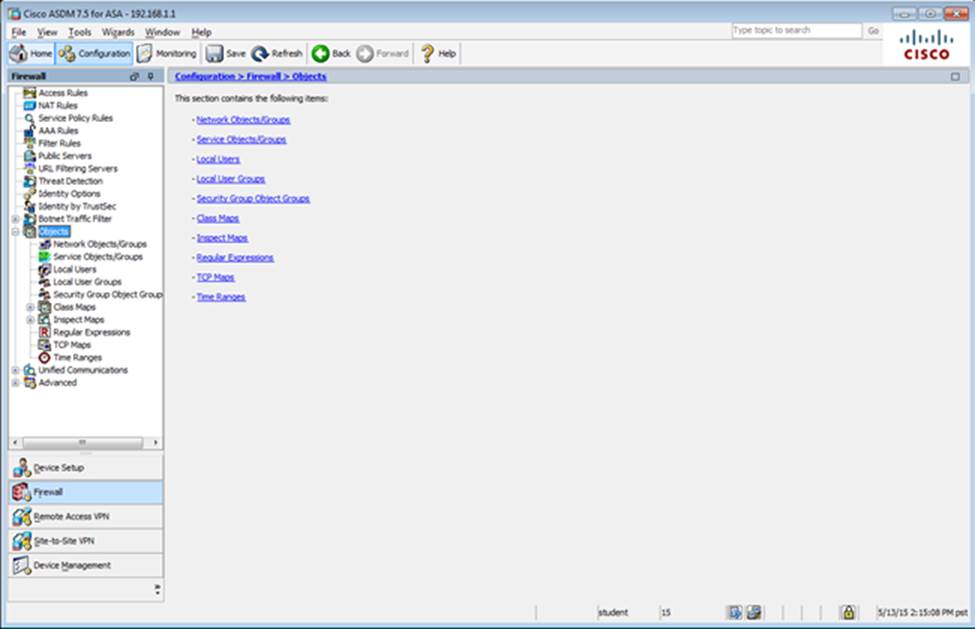
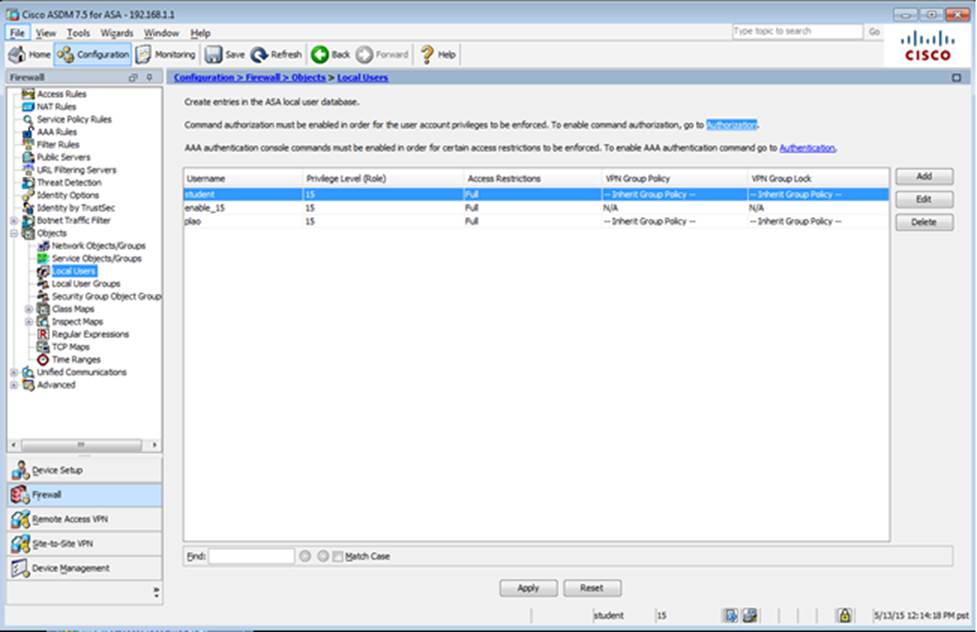
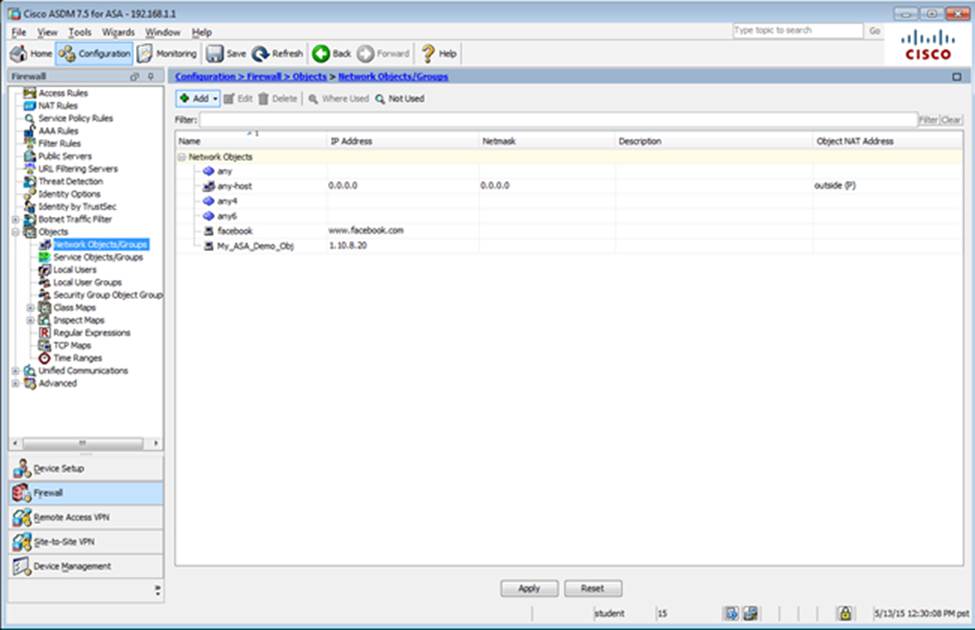
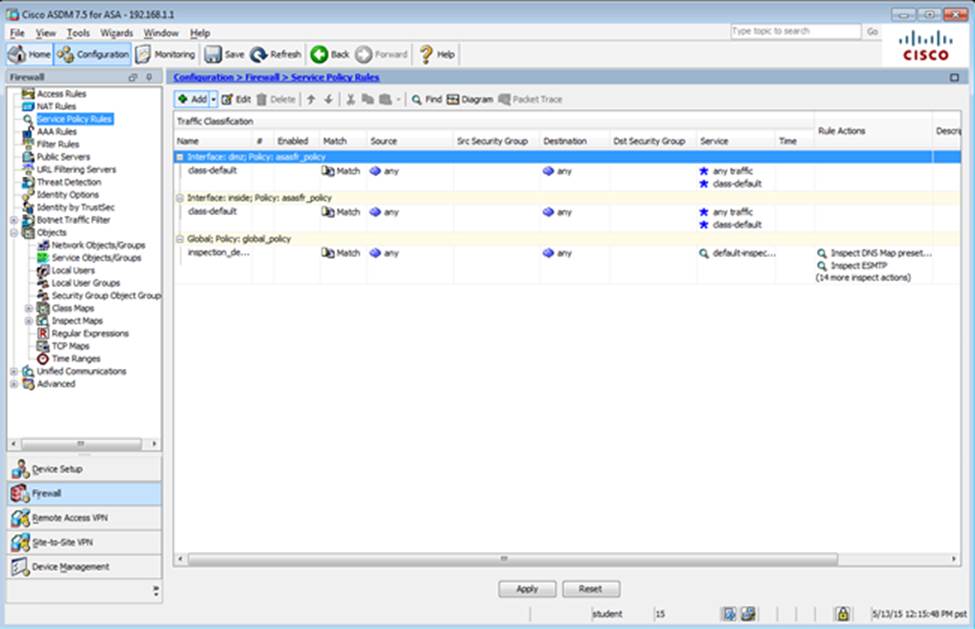
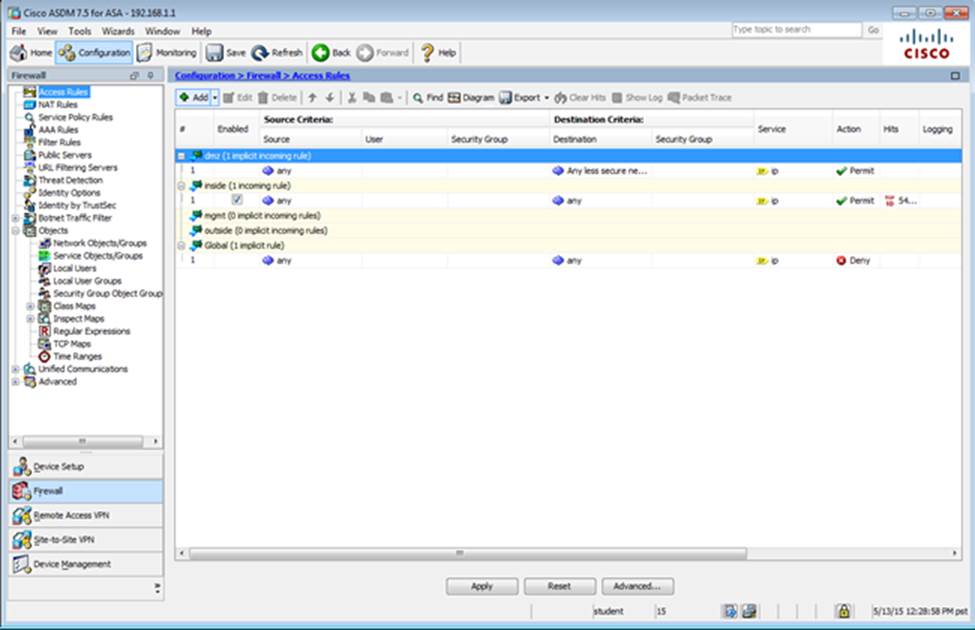
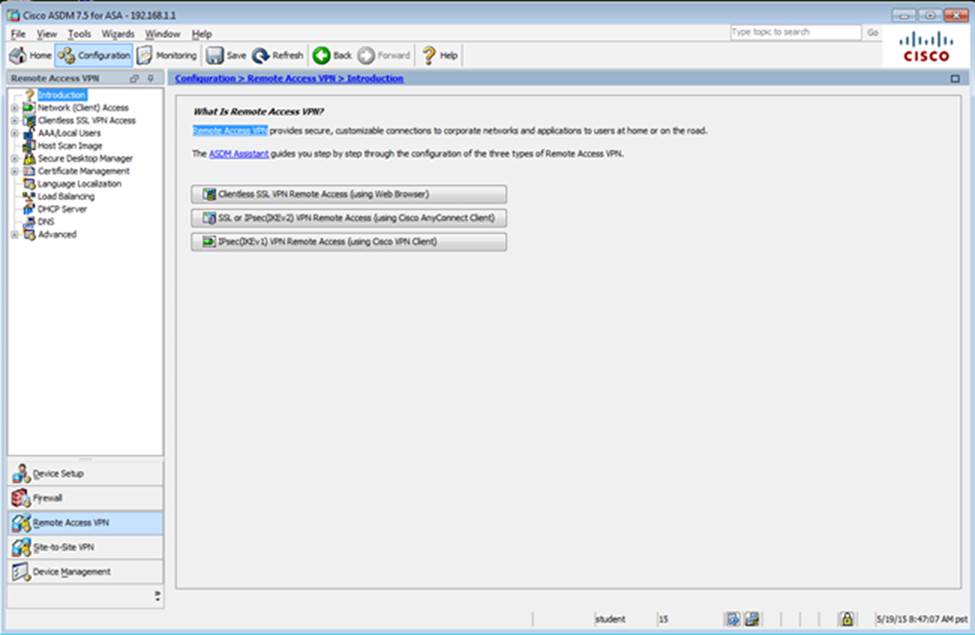
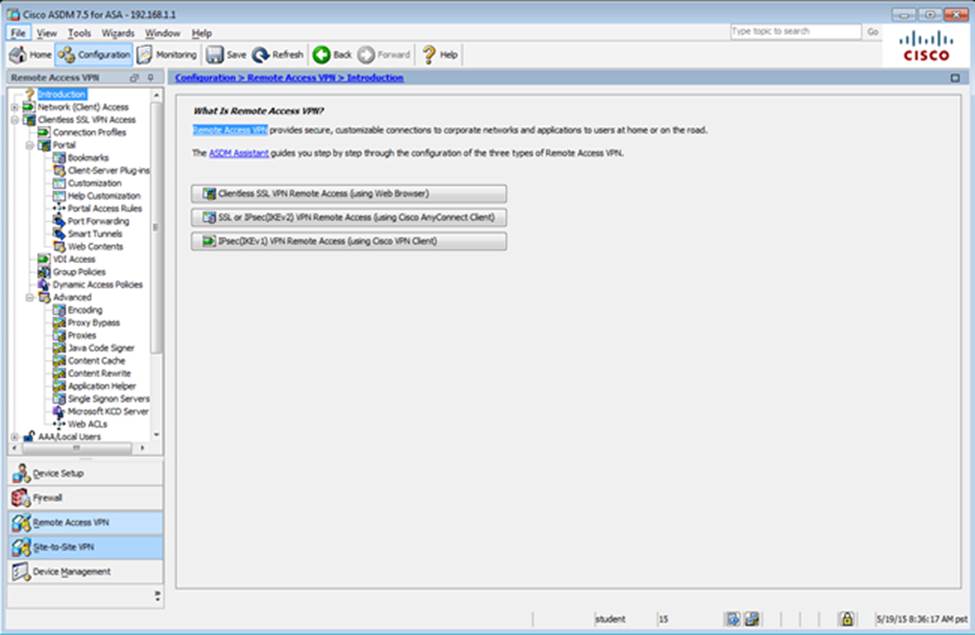
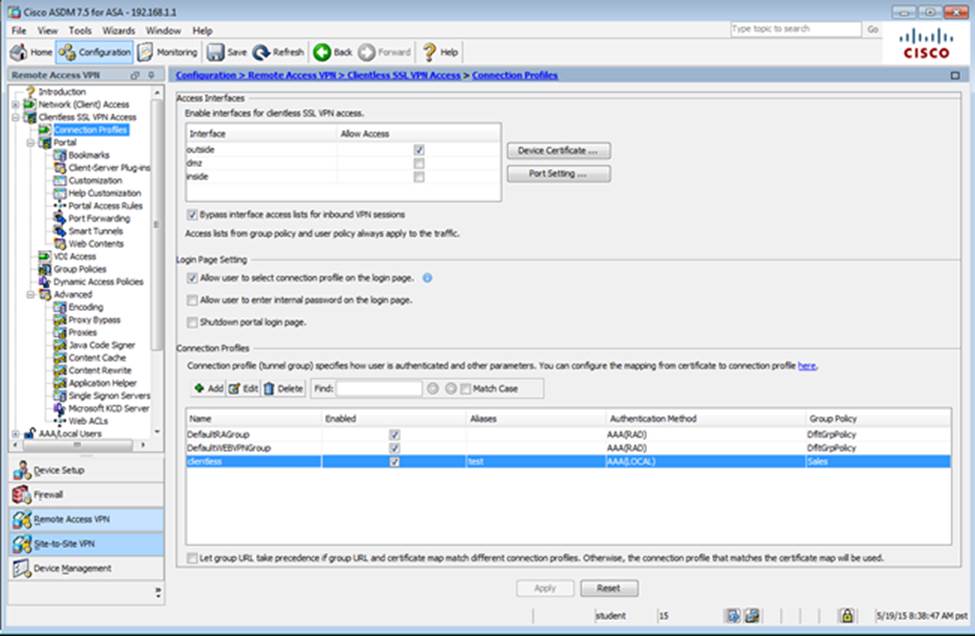
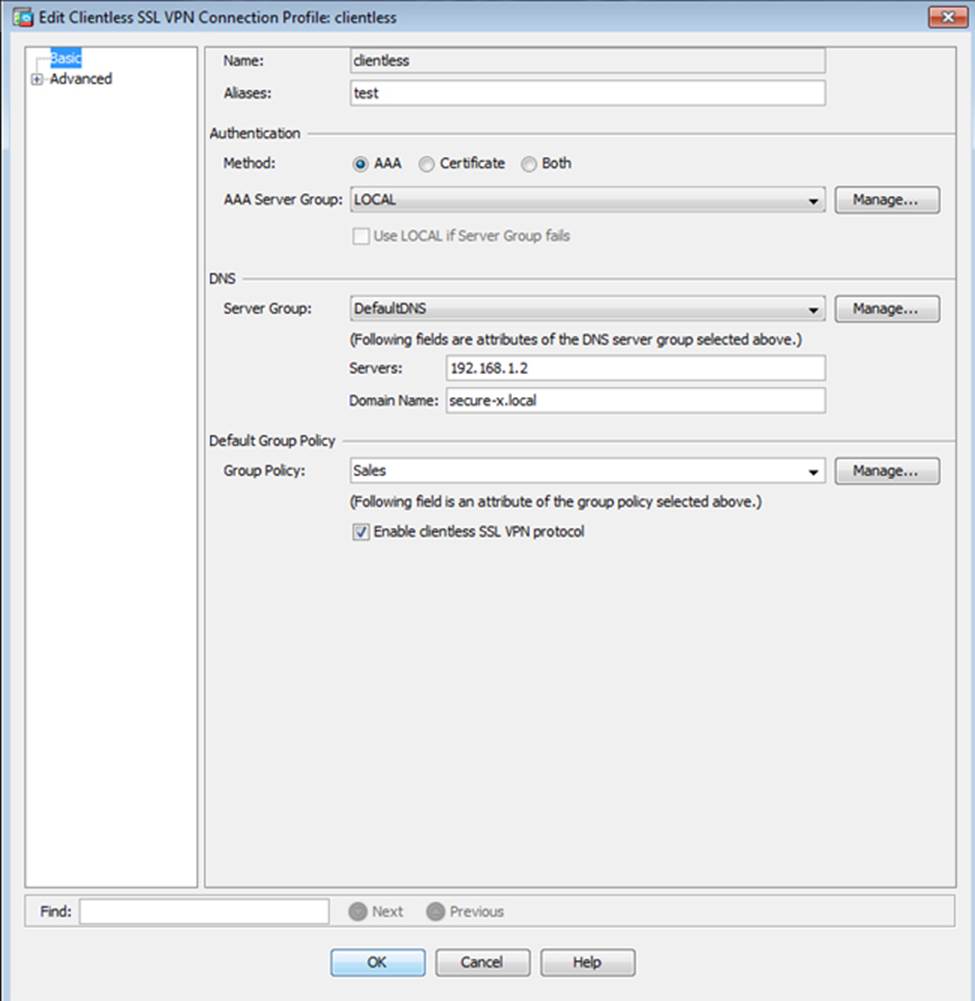
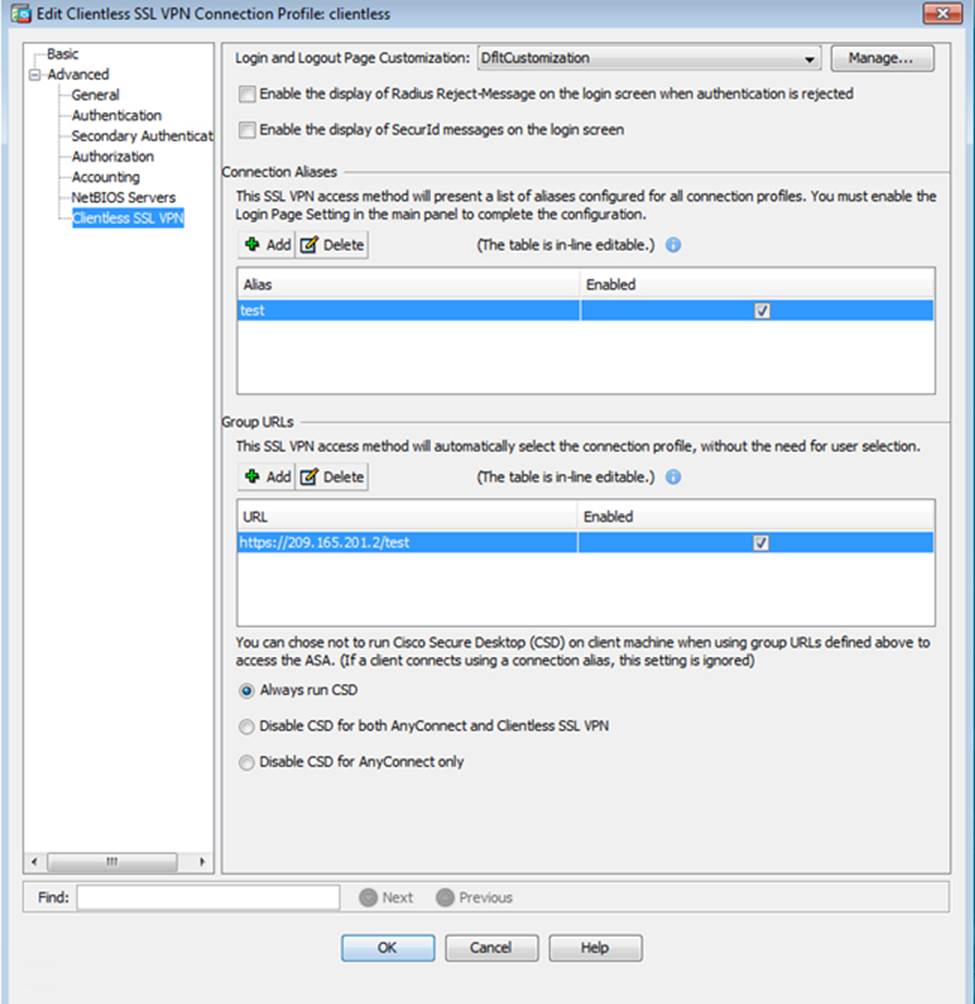
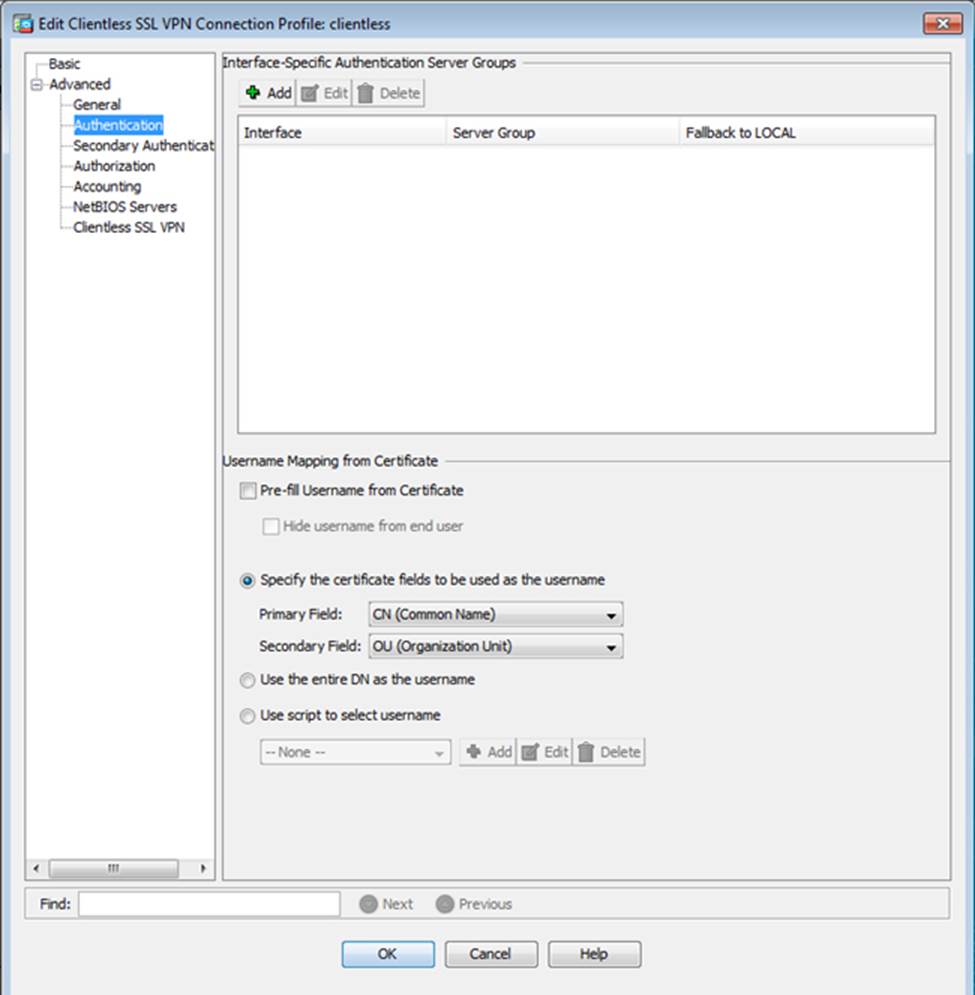


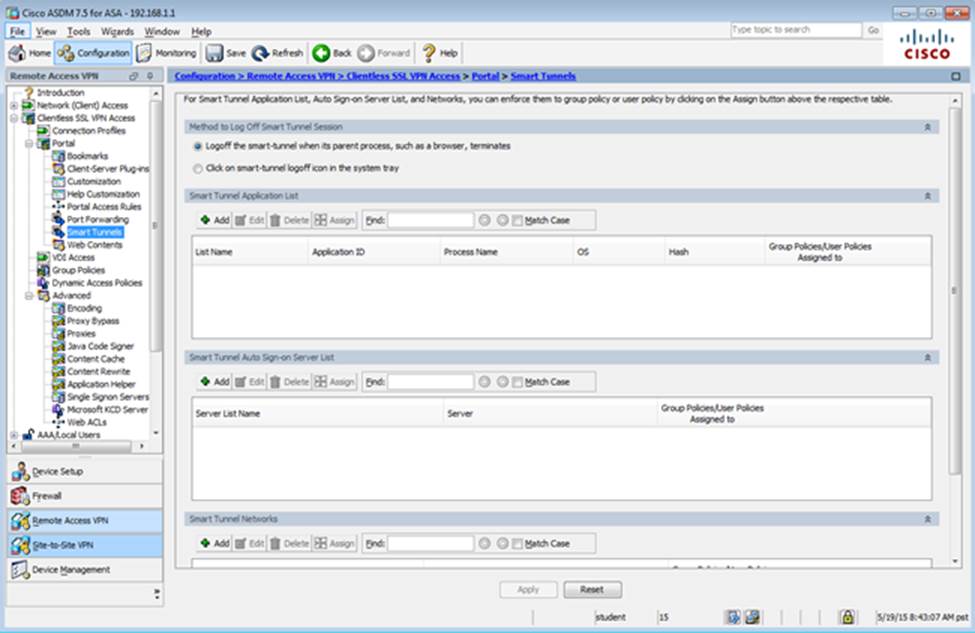
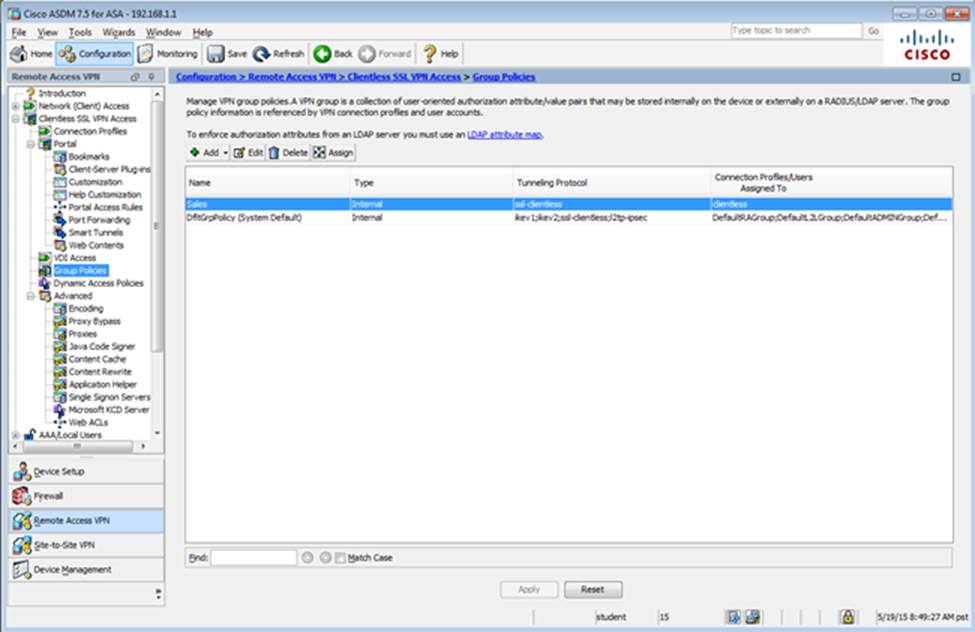
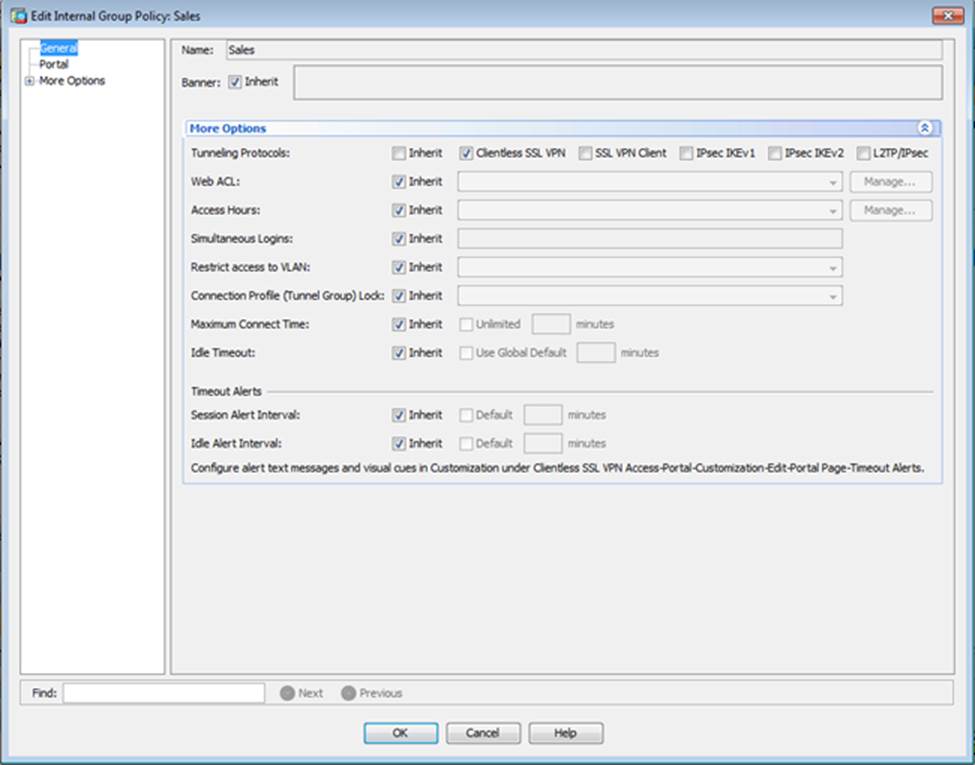
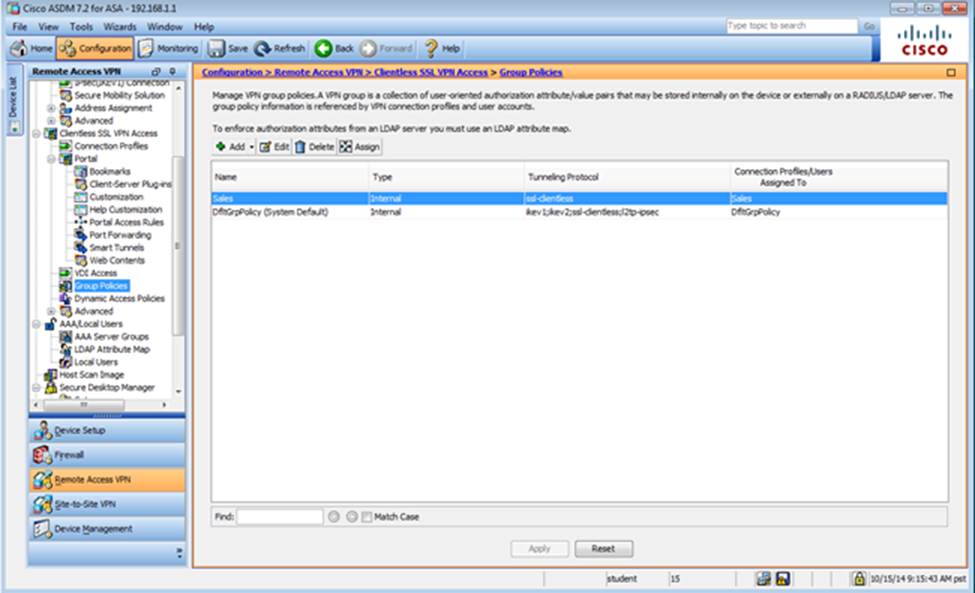
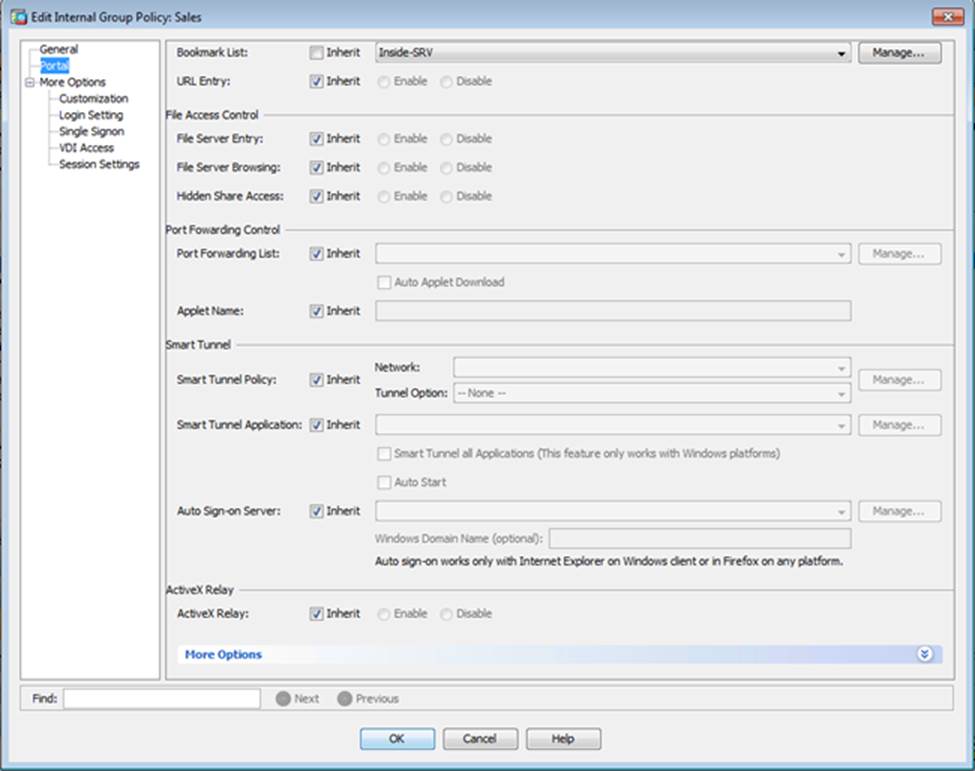
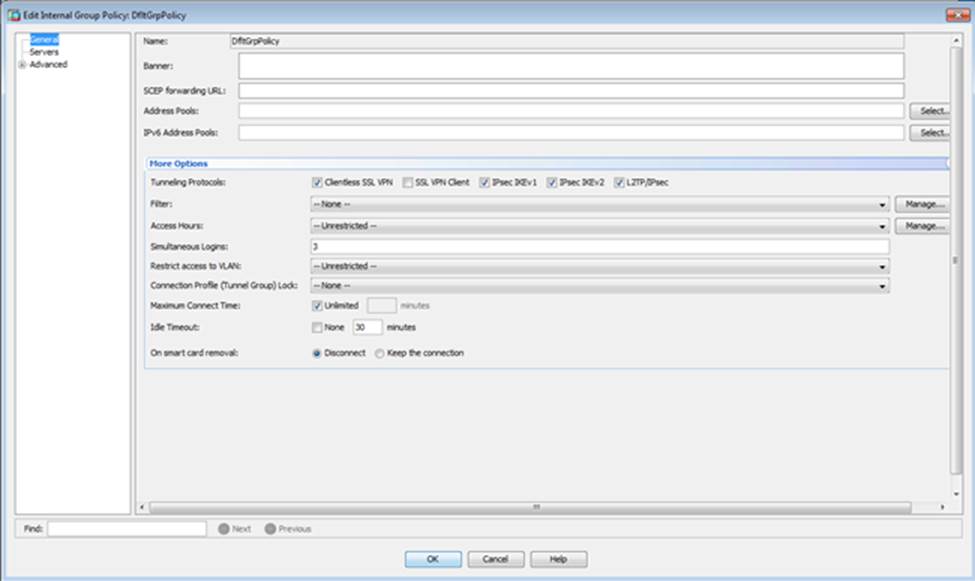

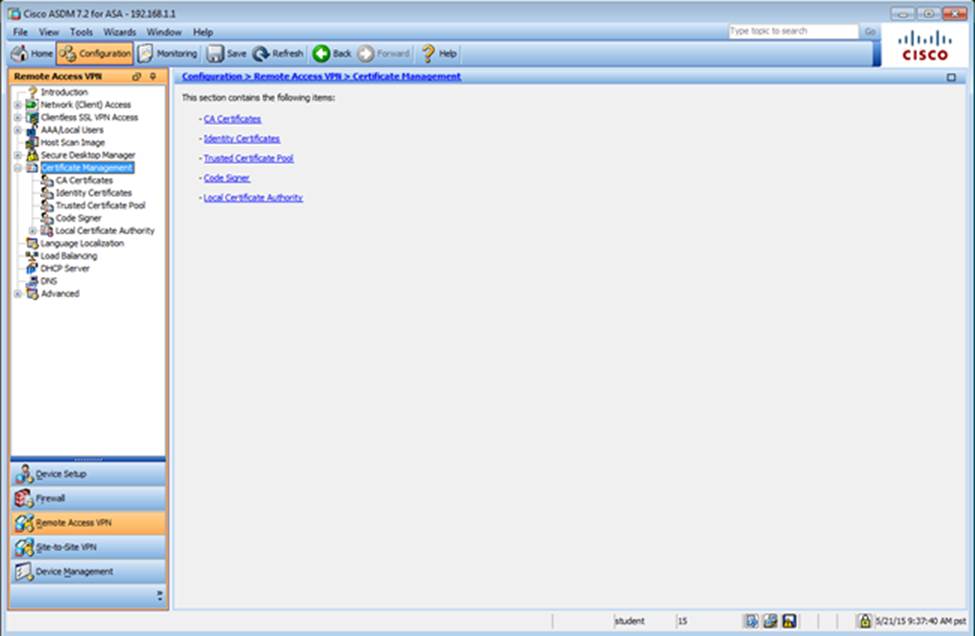
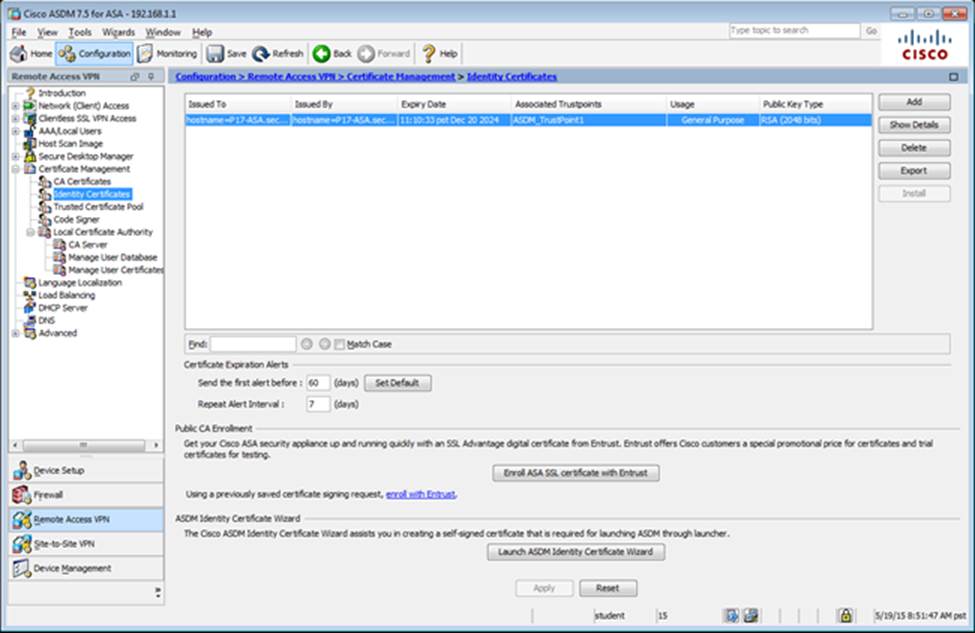
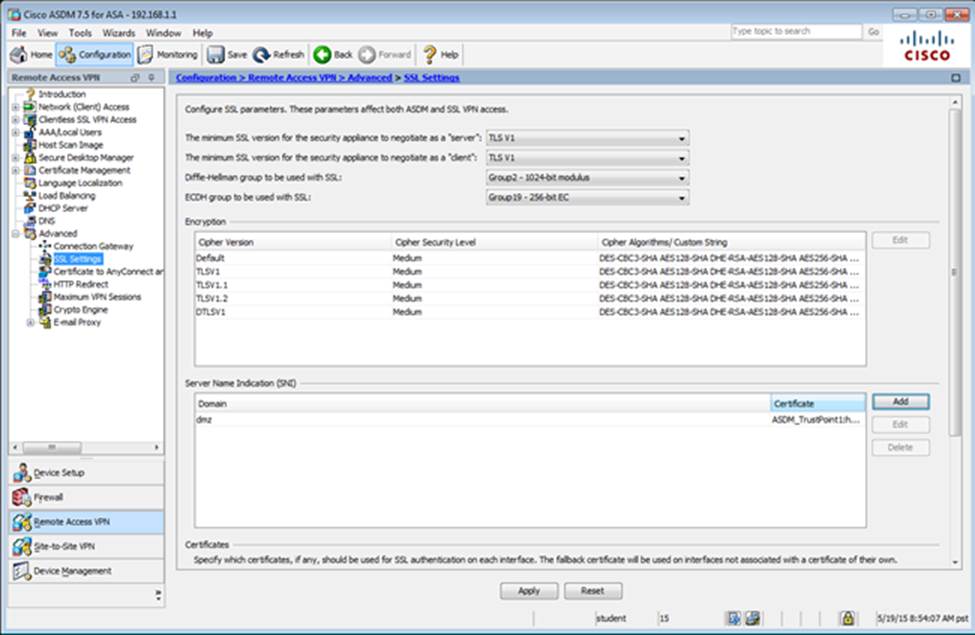
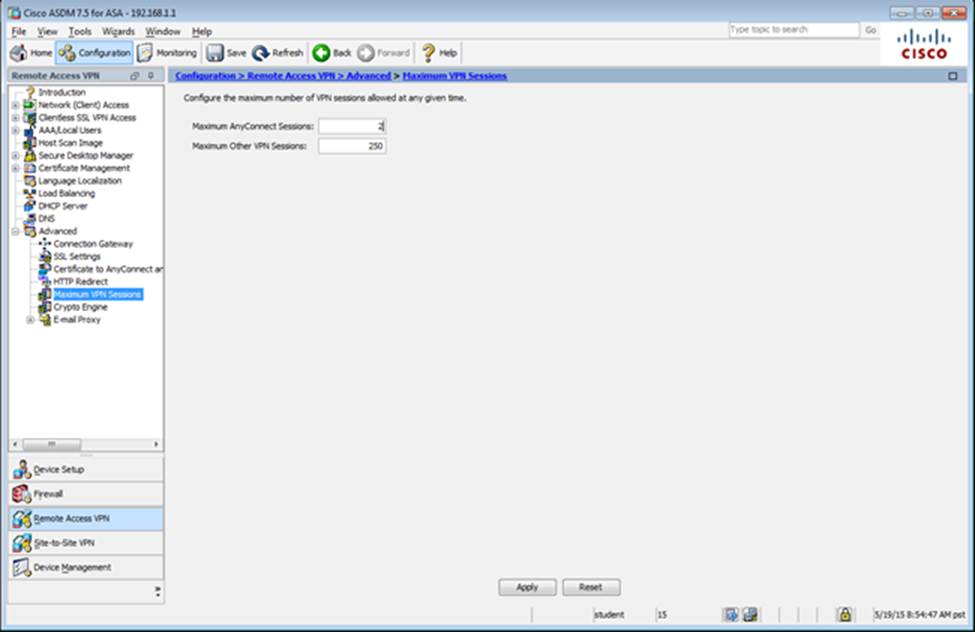
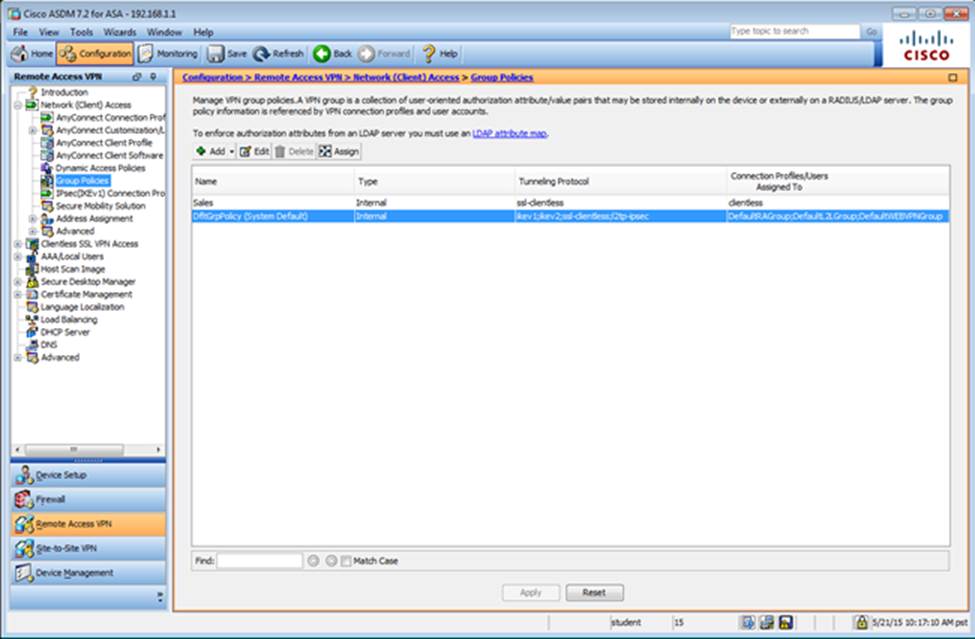
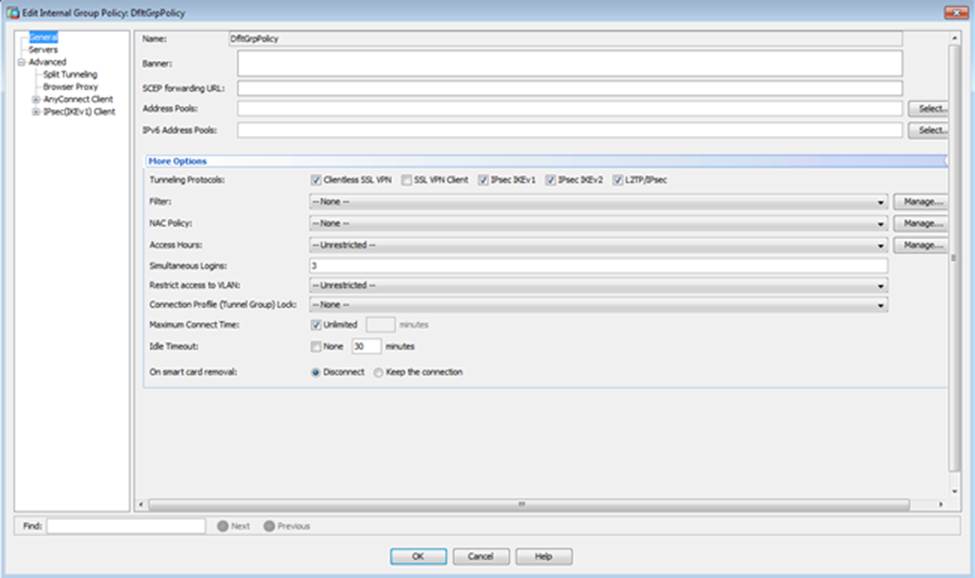
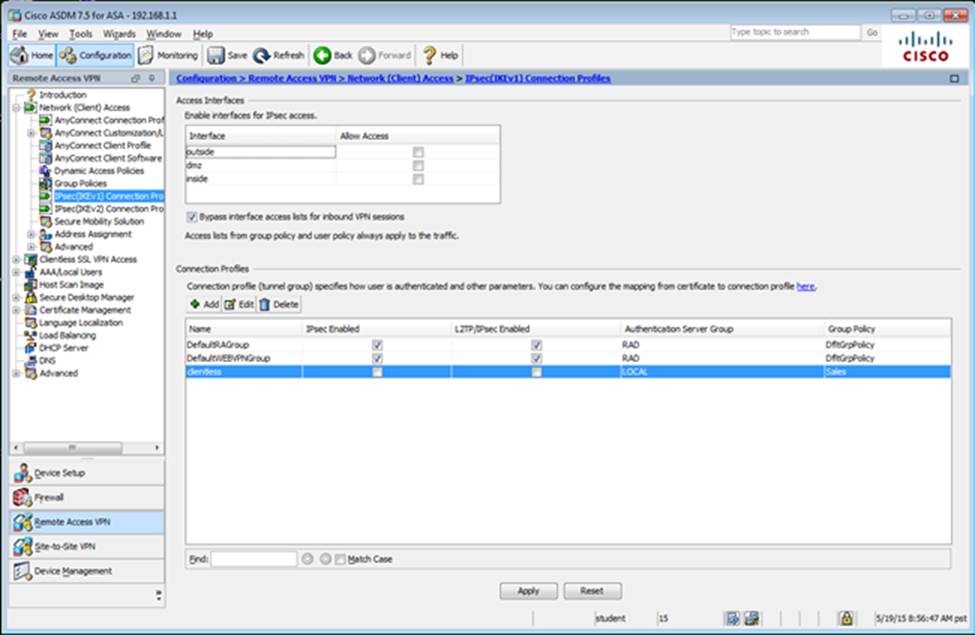

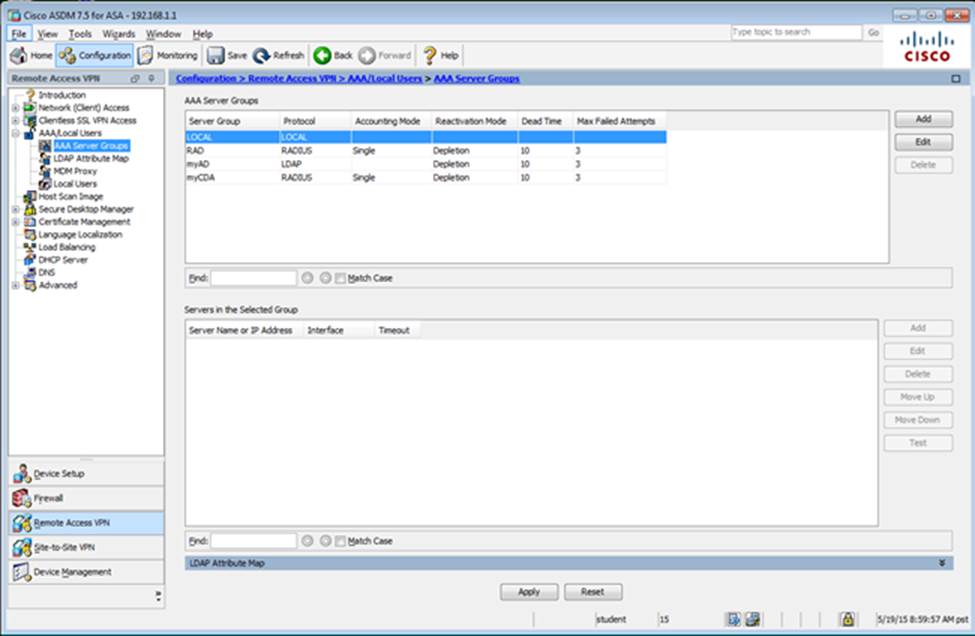
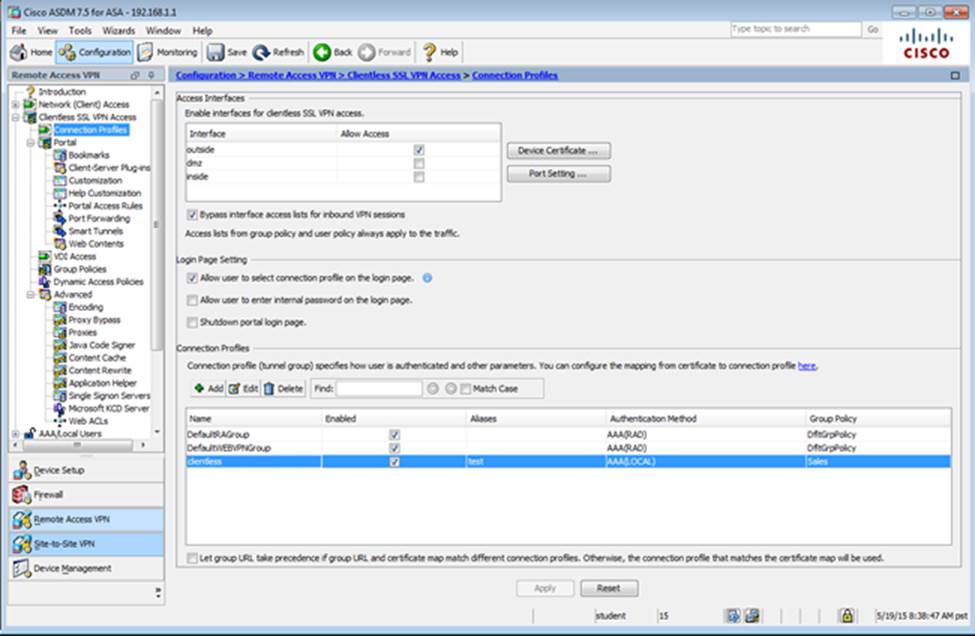
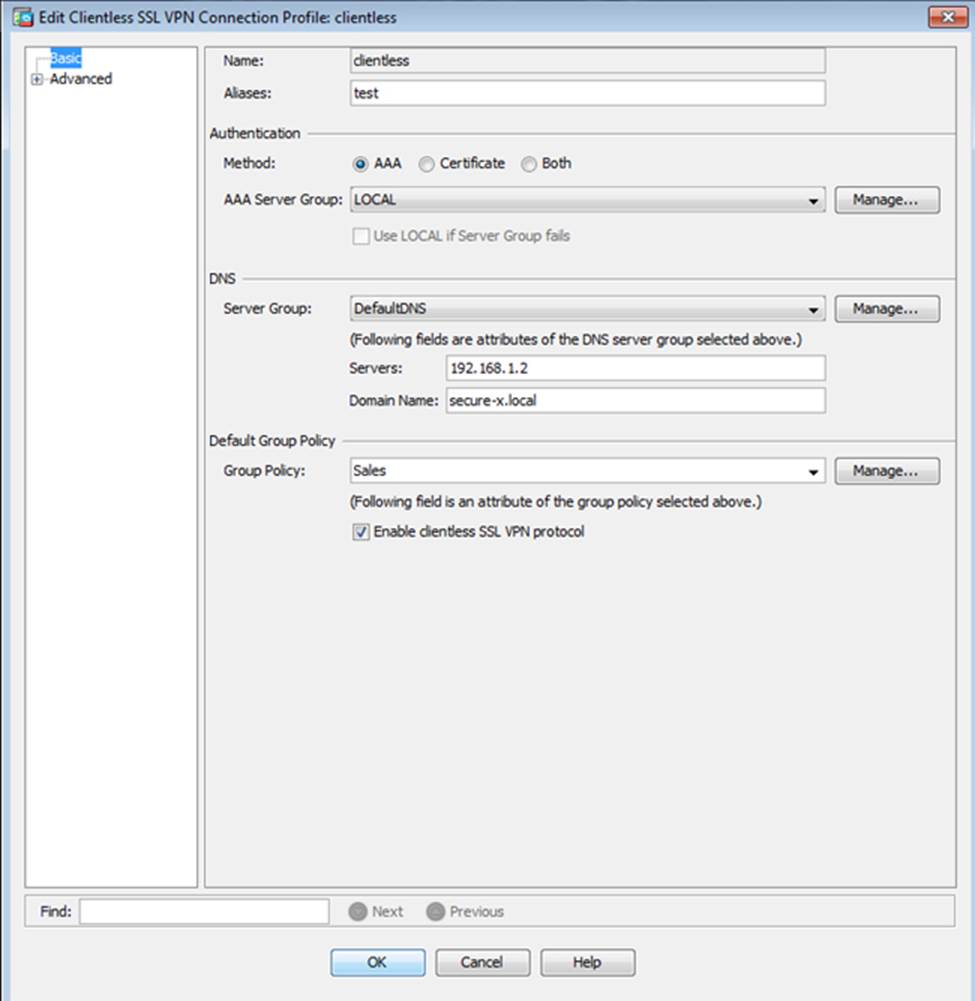
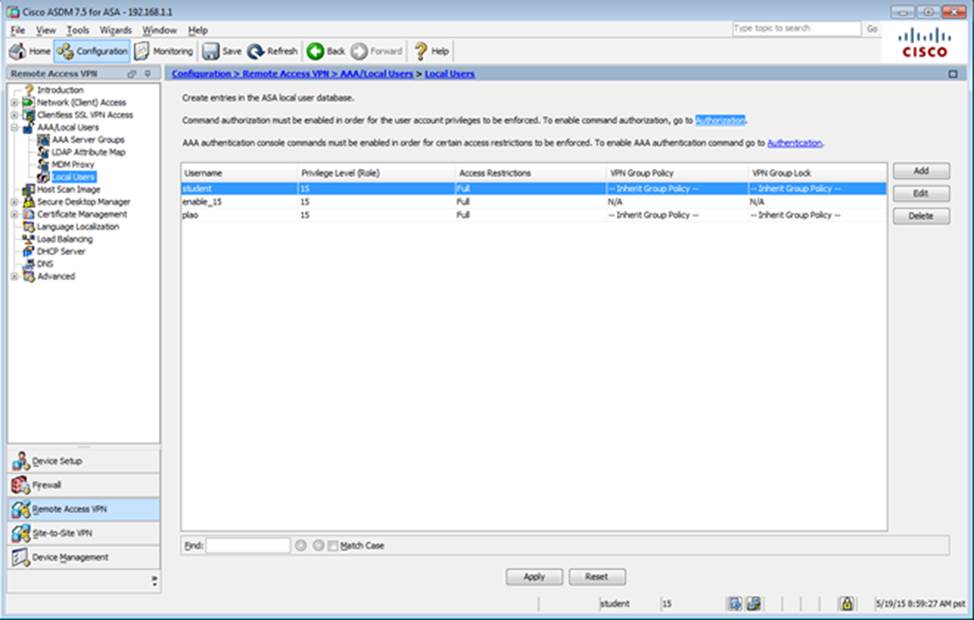
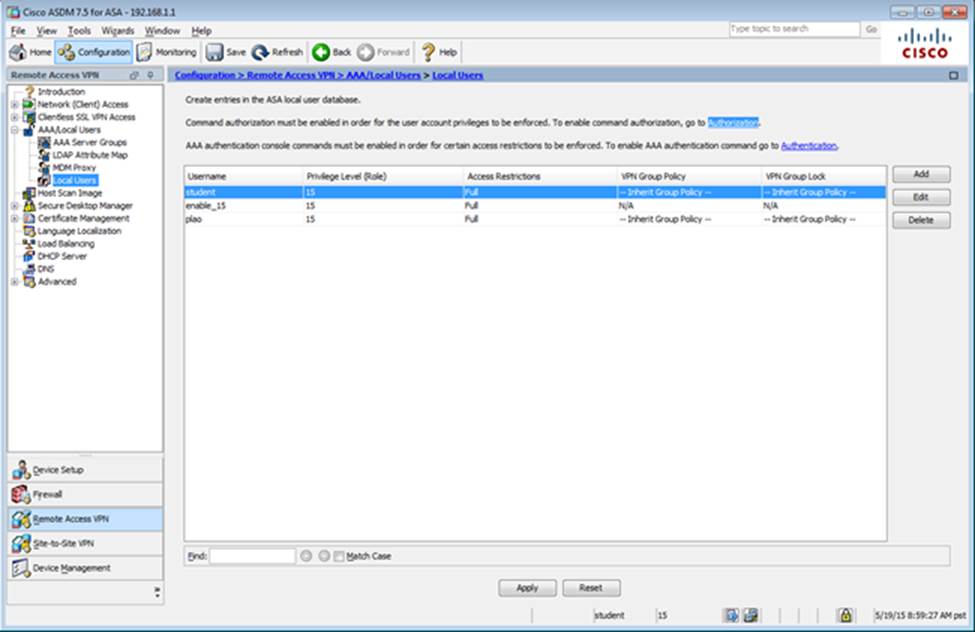
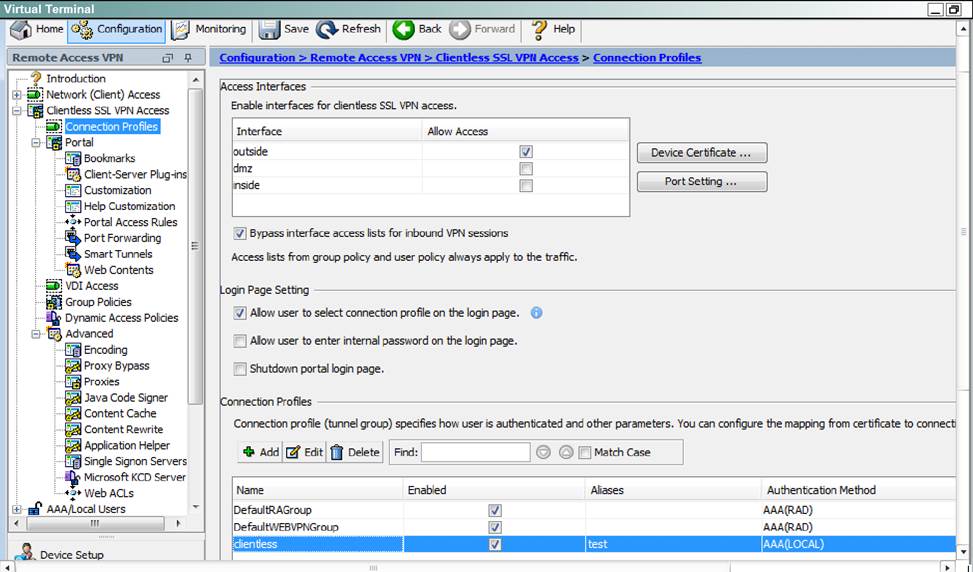
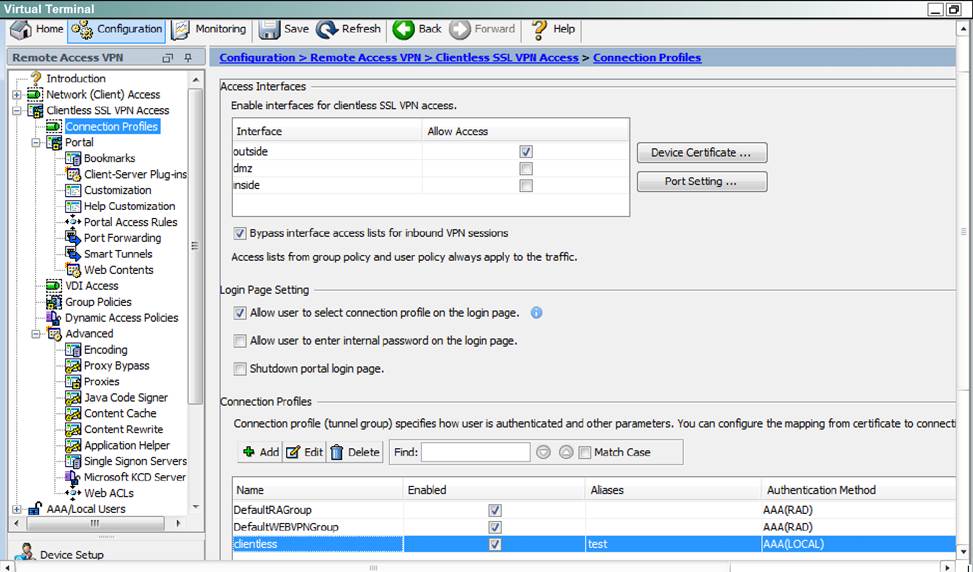
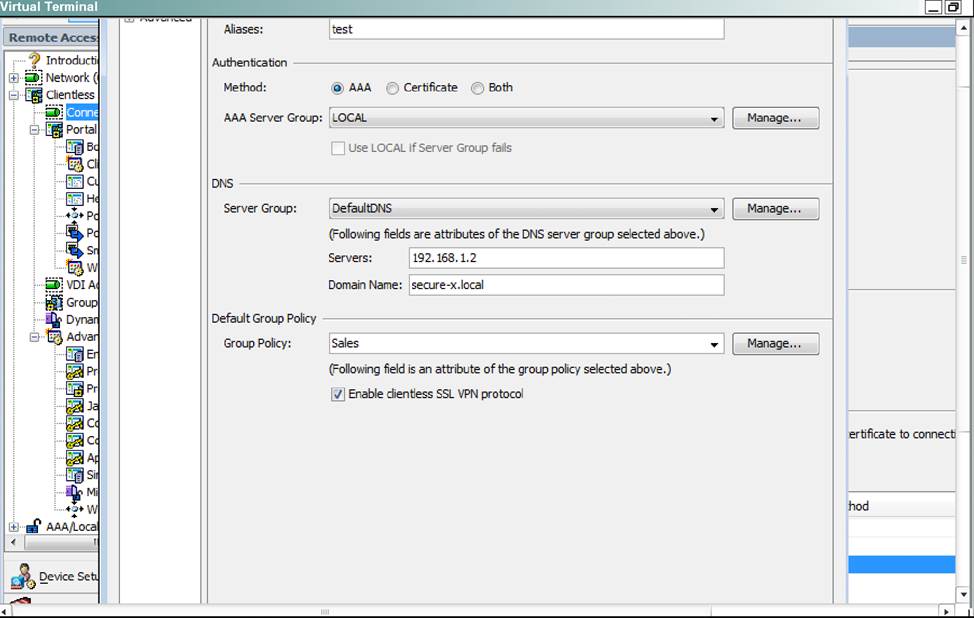
Which user authentication method is used when users login to the Clientless SSLVPN portal using https://209.165.201.2/test?
- A . AAA with LOCAL database
- B . AAA with RADIUS server
- C . Certificate
- D . Both Certificate and AAA with LOCAL database
- E . Both Certificate and AAA with RADIUS server
Scenario
In this simulation, you have access to ASDM only. Review the various ASA configurations using ASDM then answer the five multiple choice questions about the ASA SSLVPN configurations.
To access ASDM, click the ASA icon in the topology diagram.
Note: Not all ASDM functionalities are enabled in this simulation.
To see all the menu options available on the left navigation pane, you may also need to un-expand the expanded menu first.

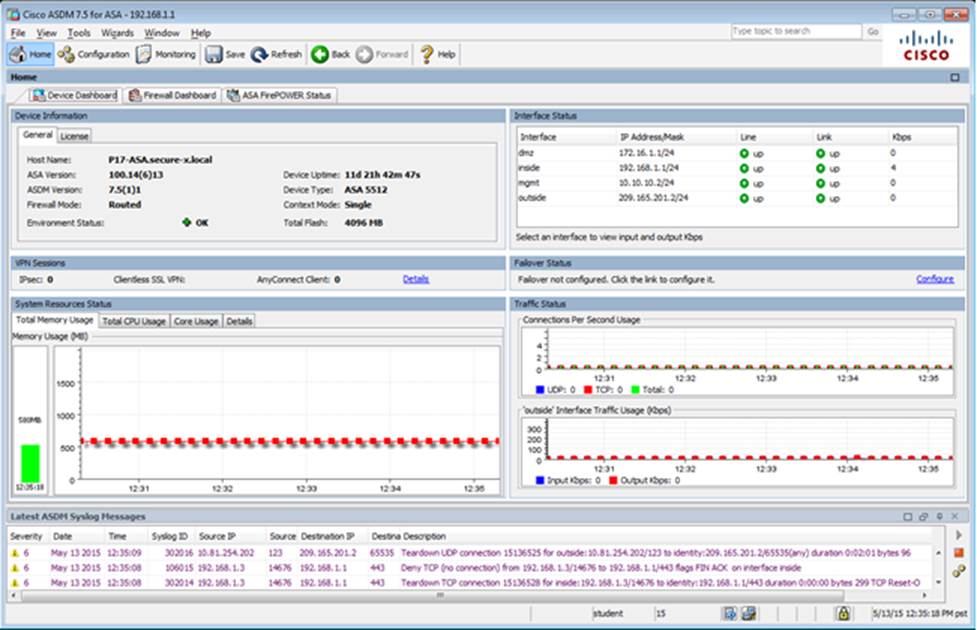

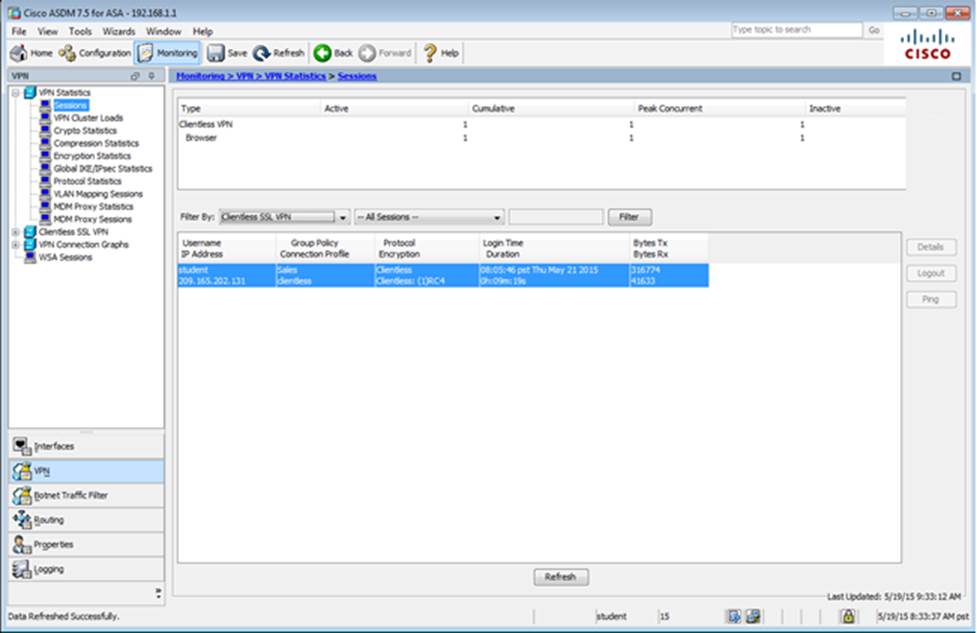
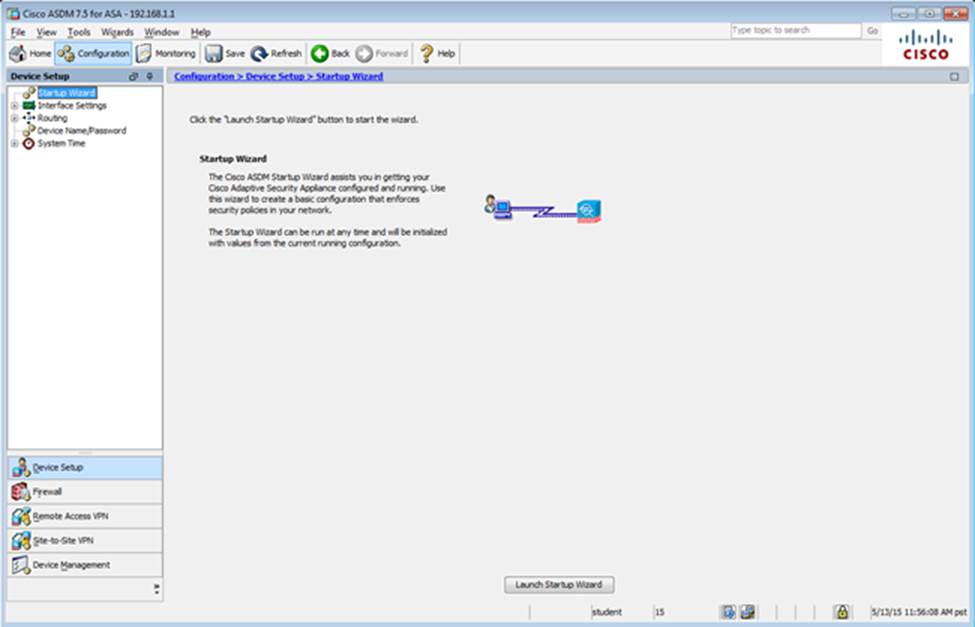
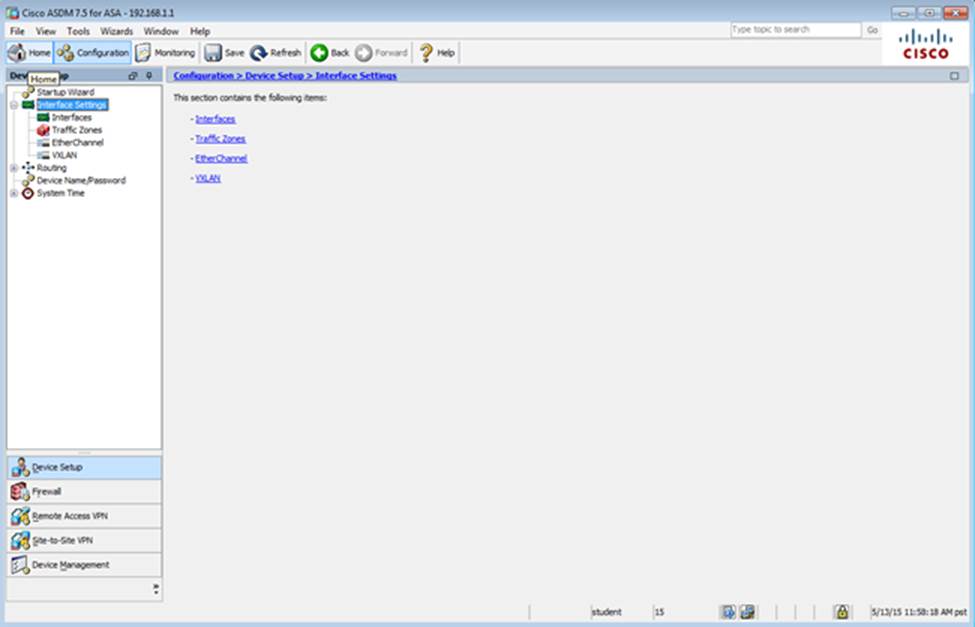
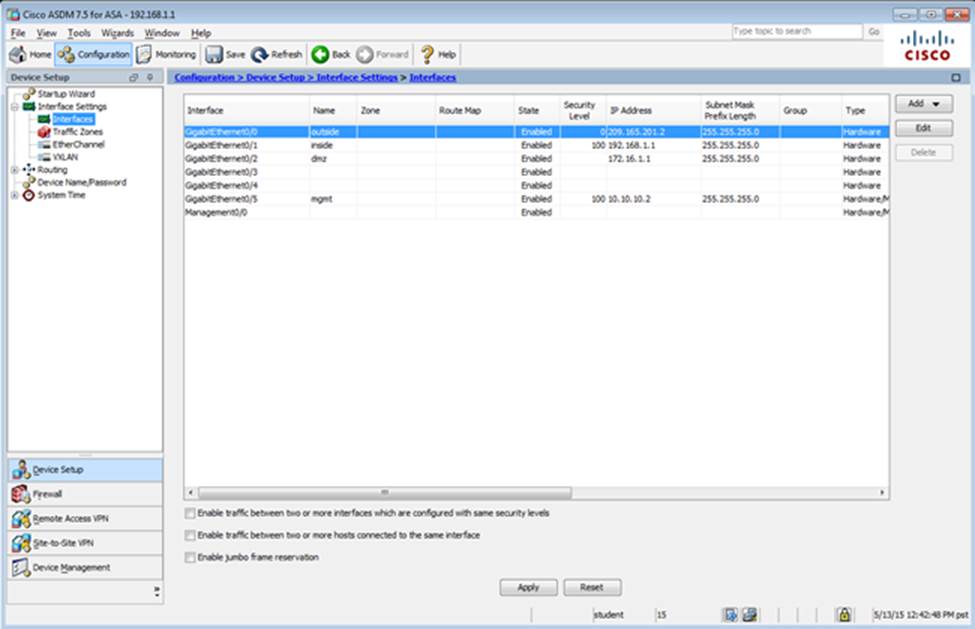
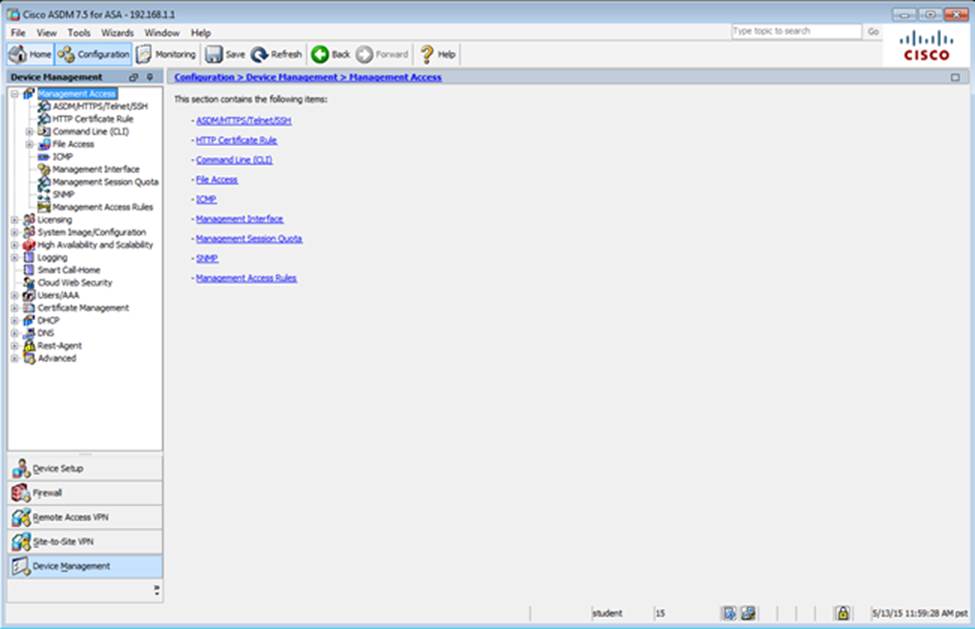

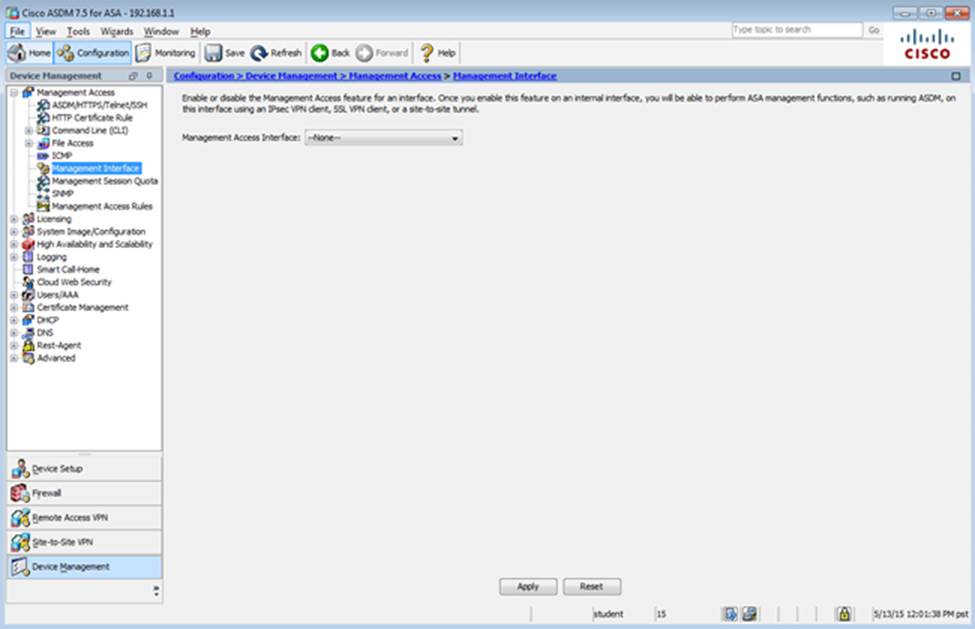
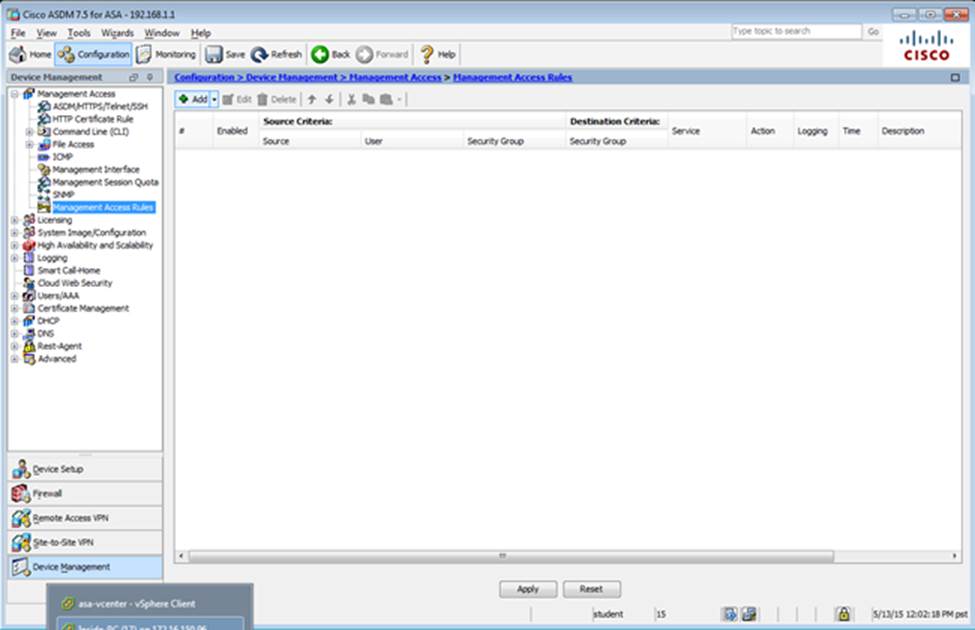


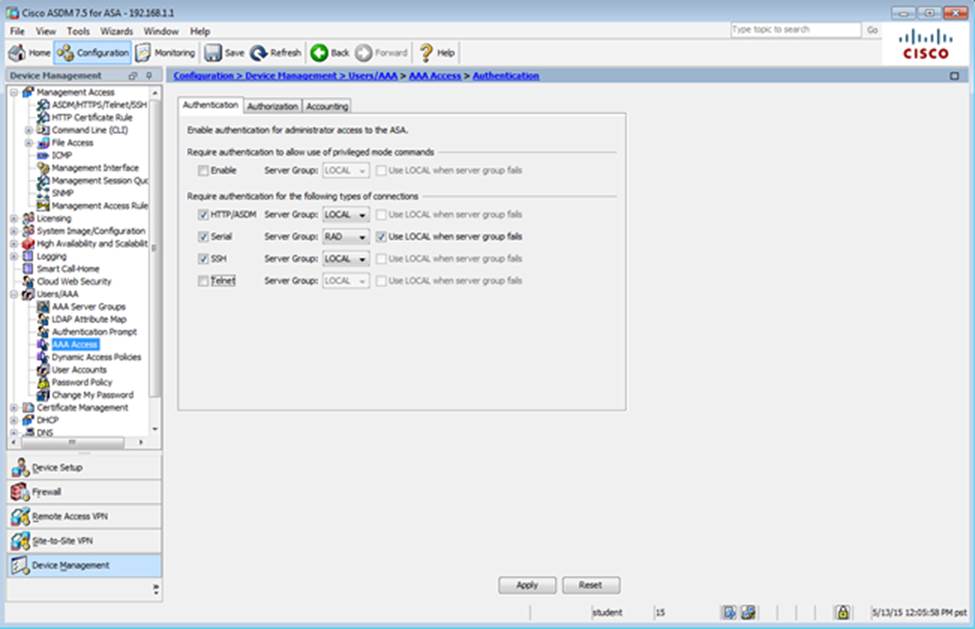
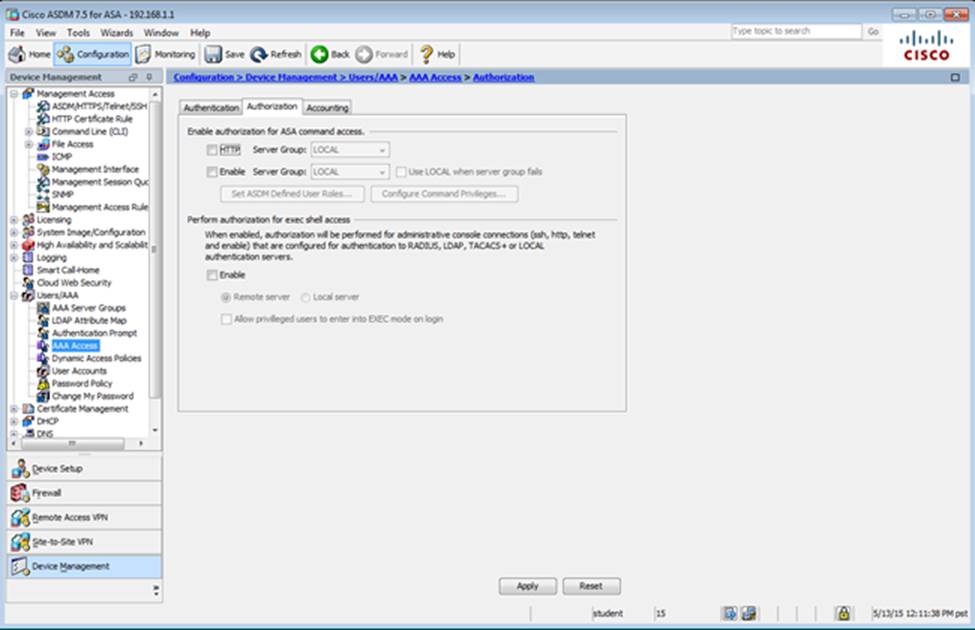
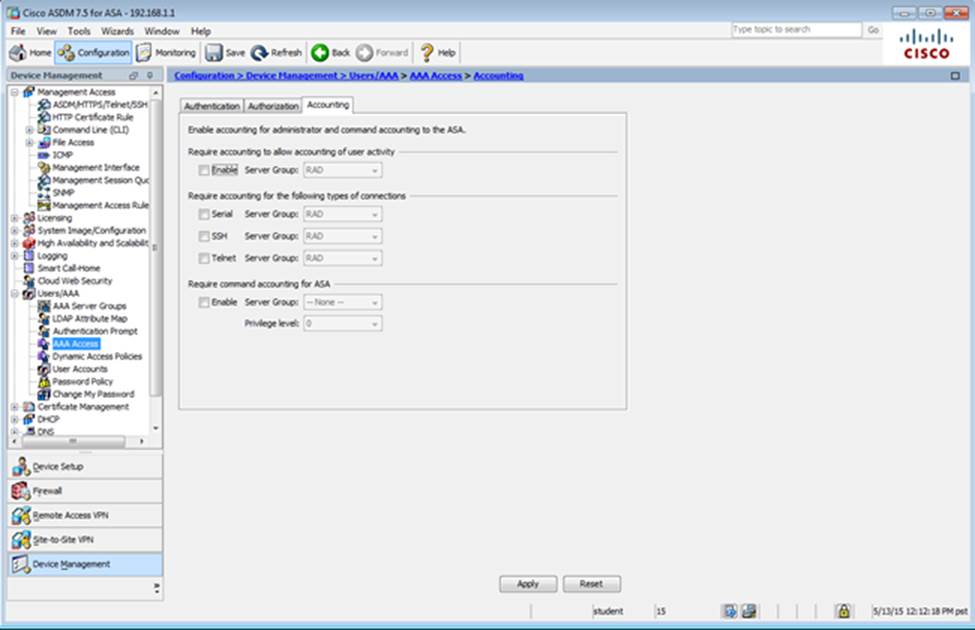
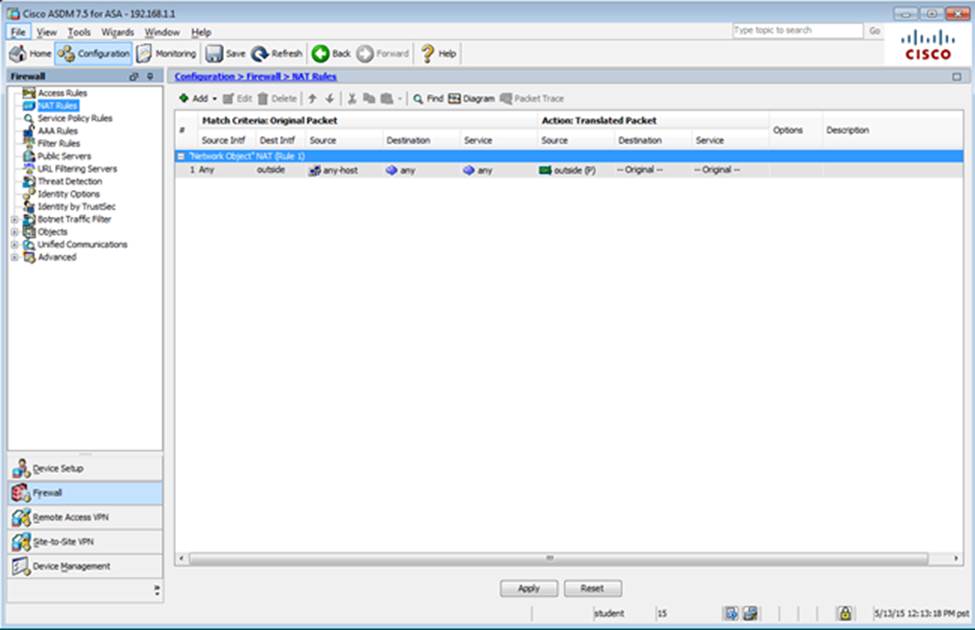
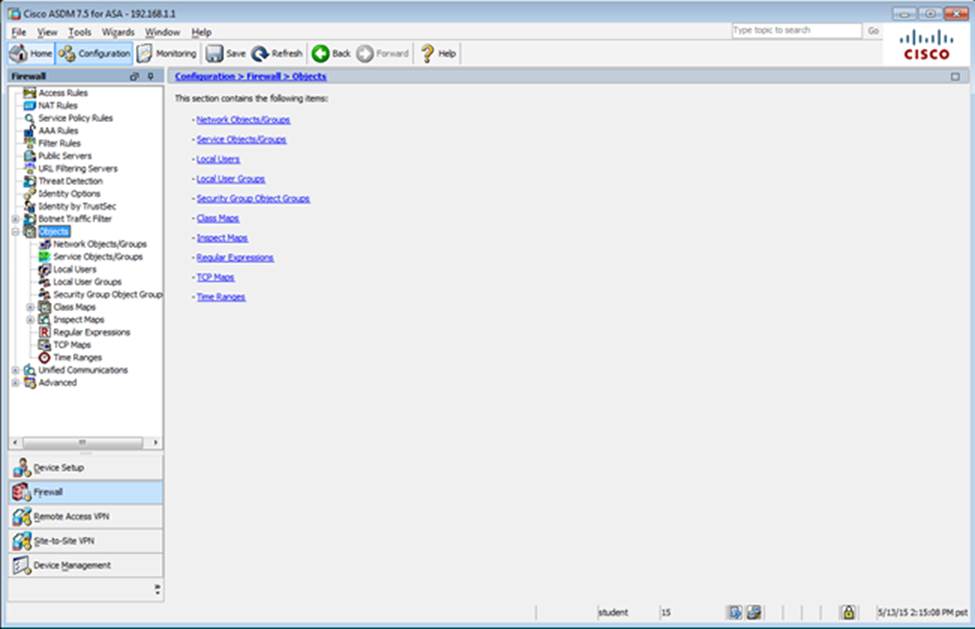
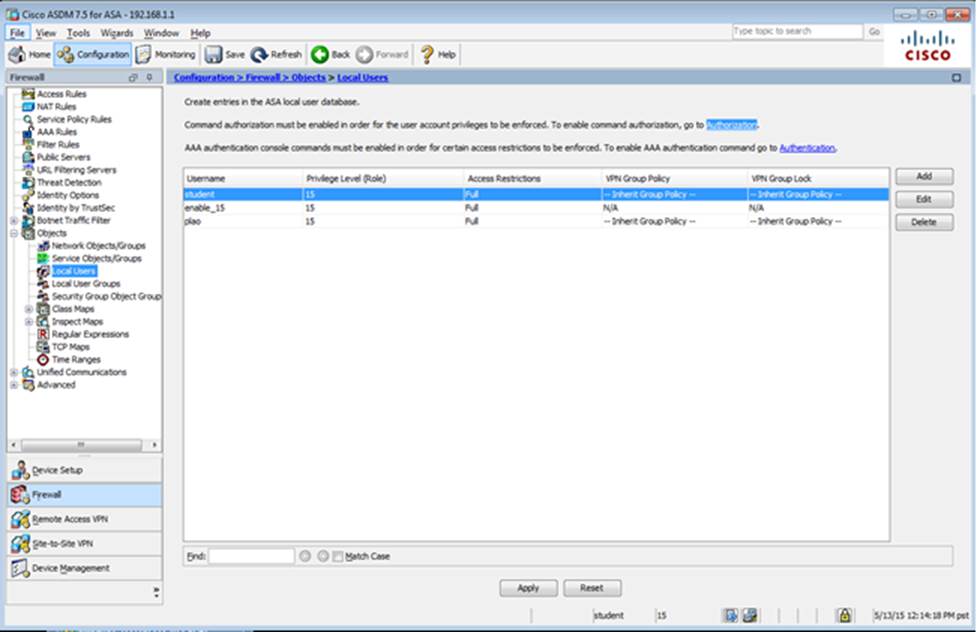
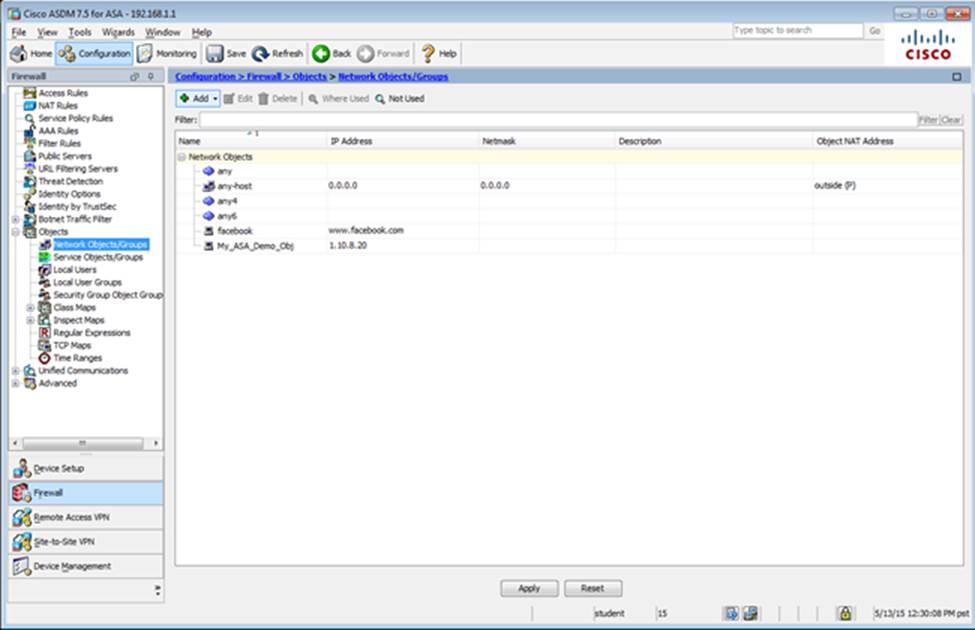
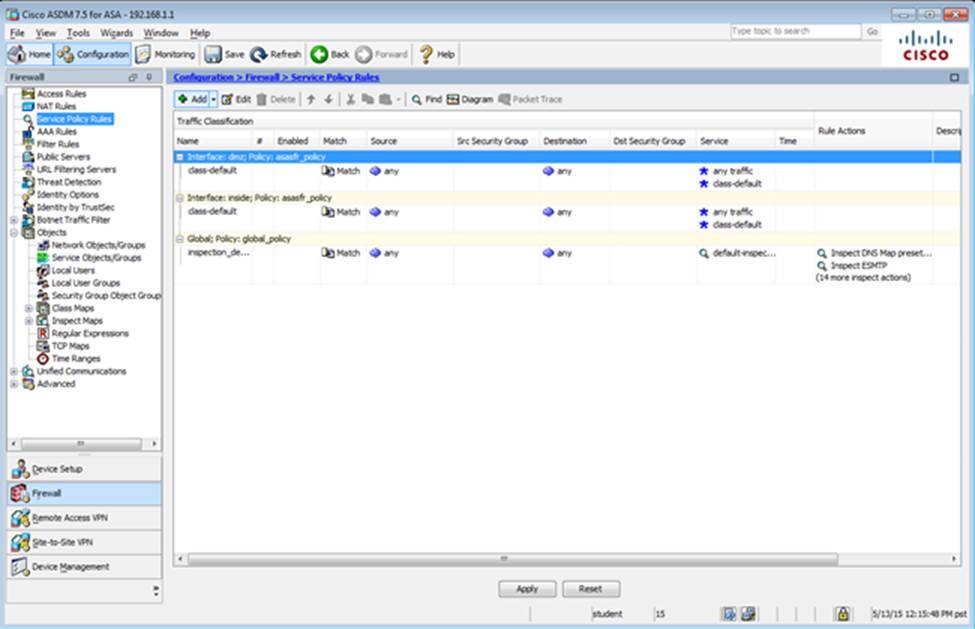
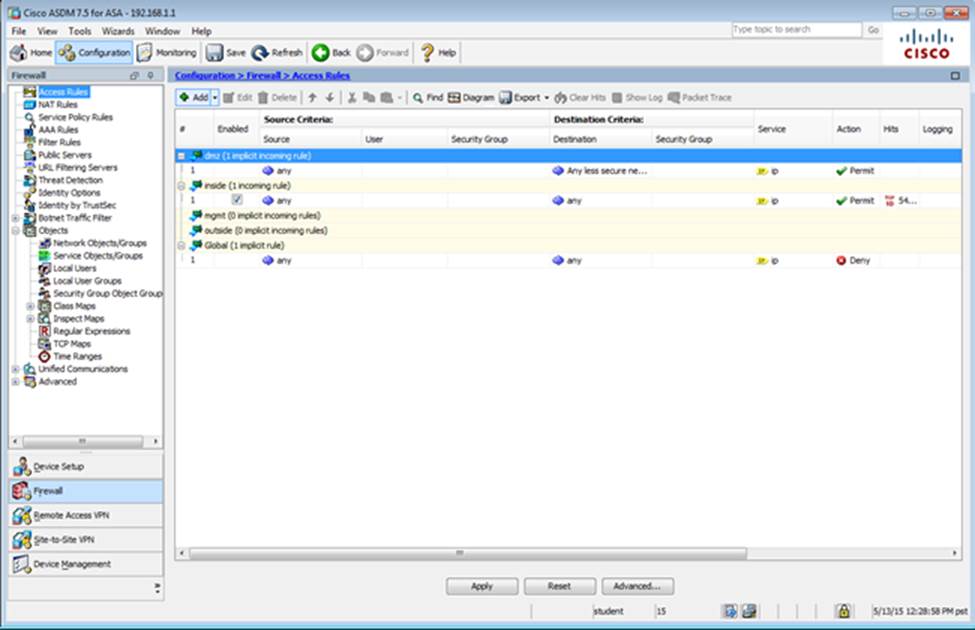
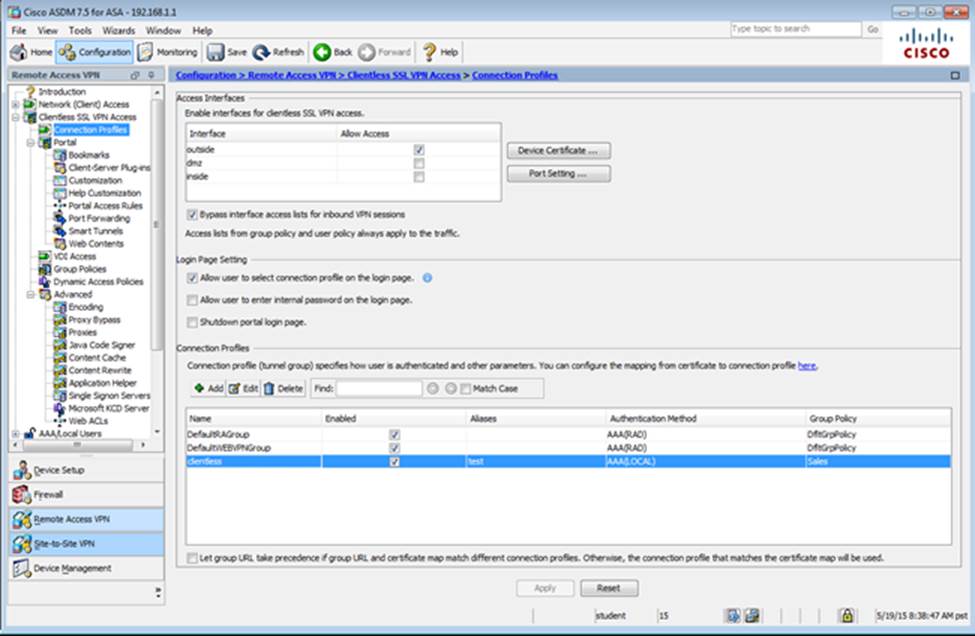

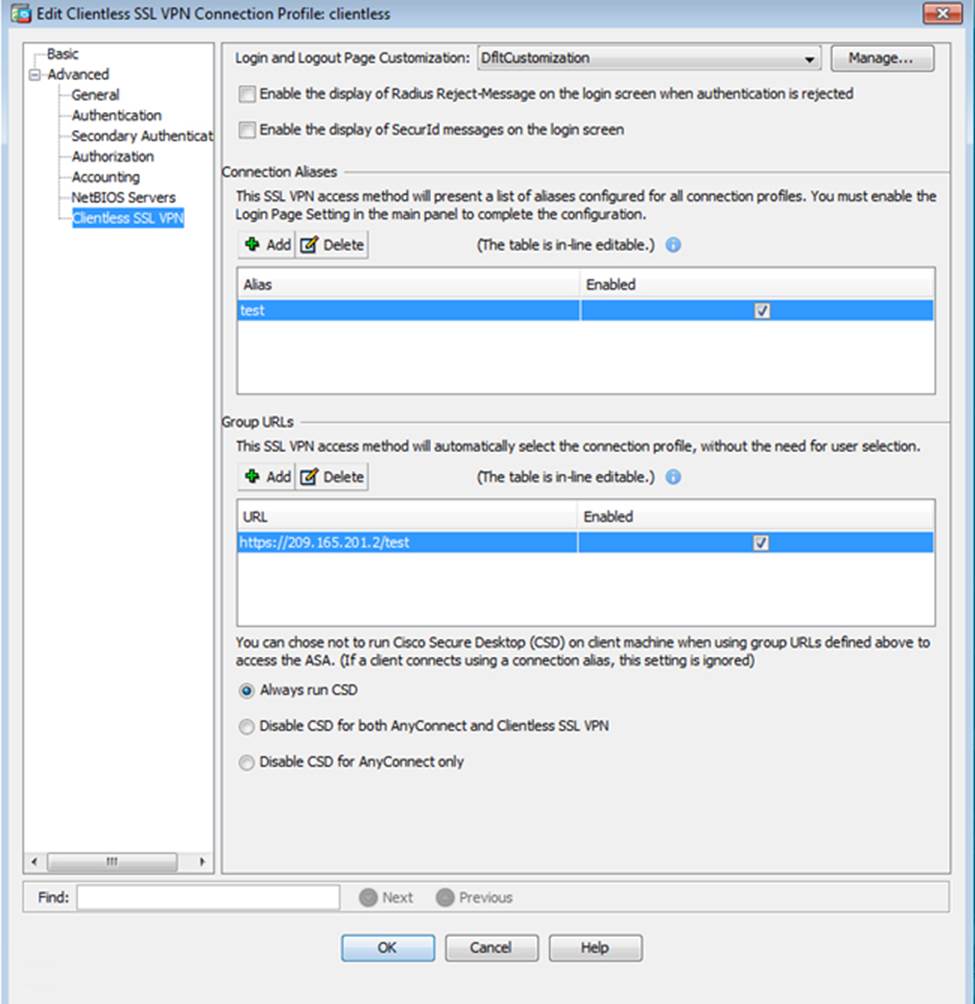
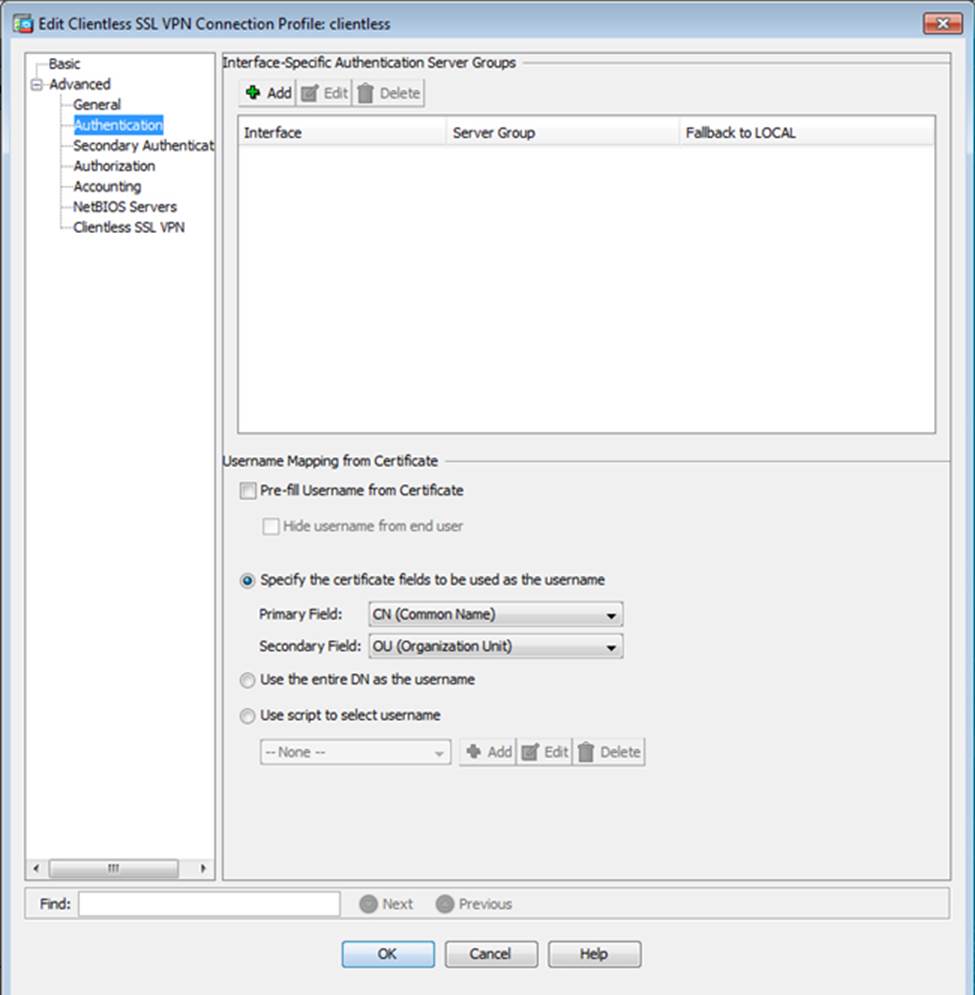
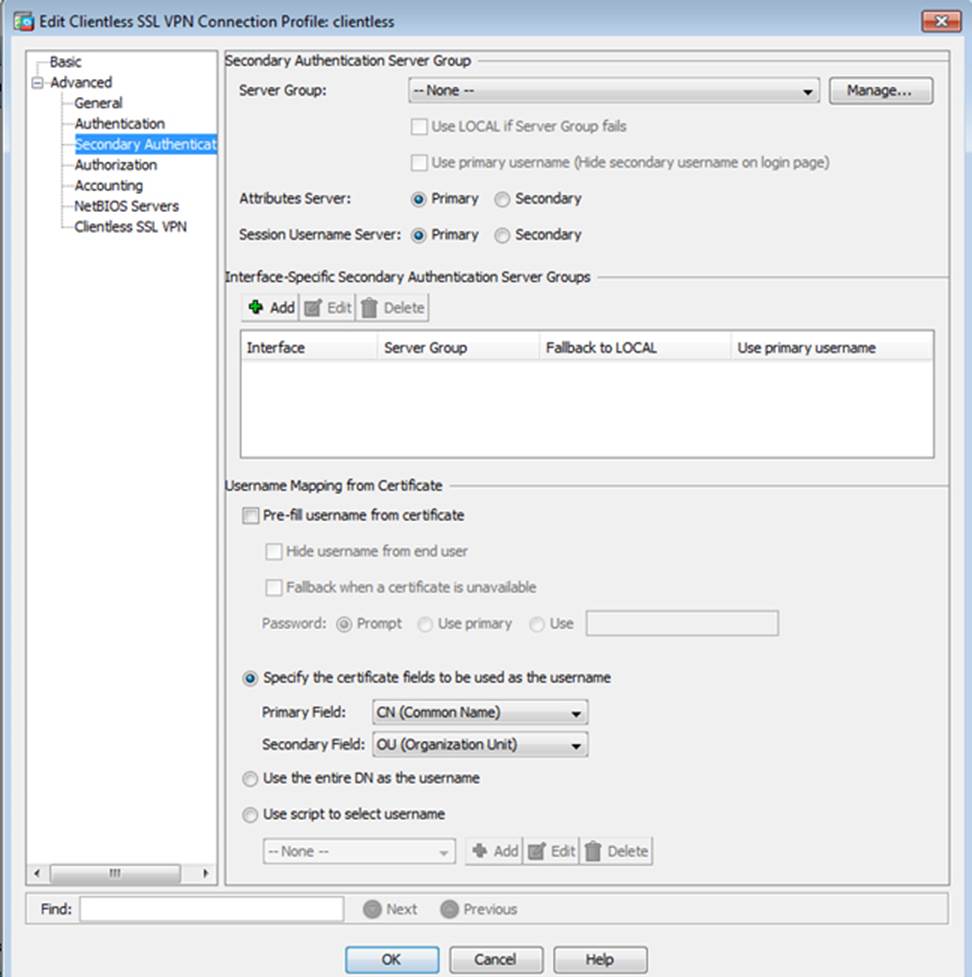
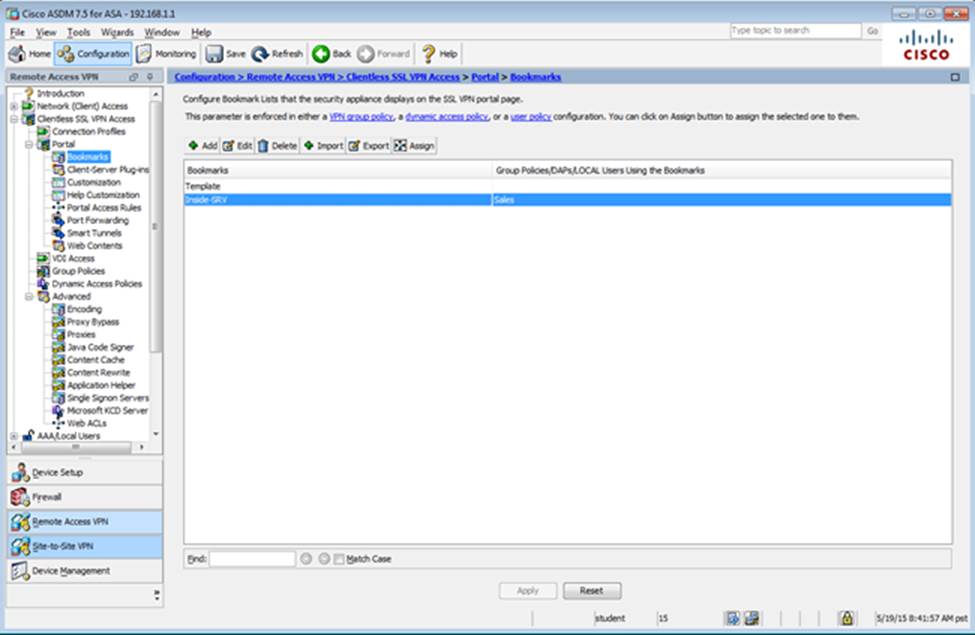

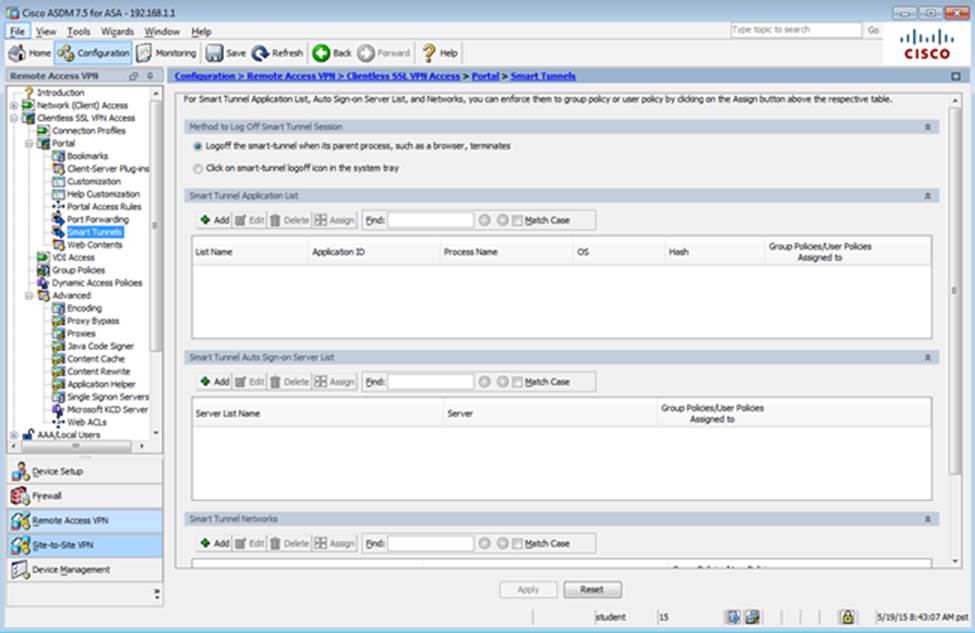
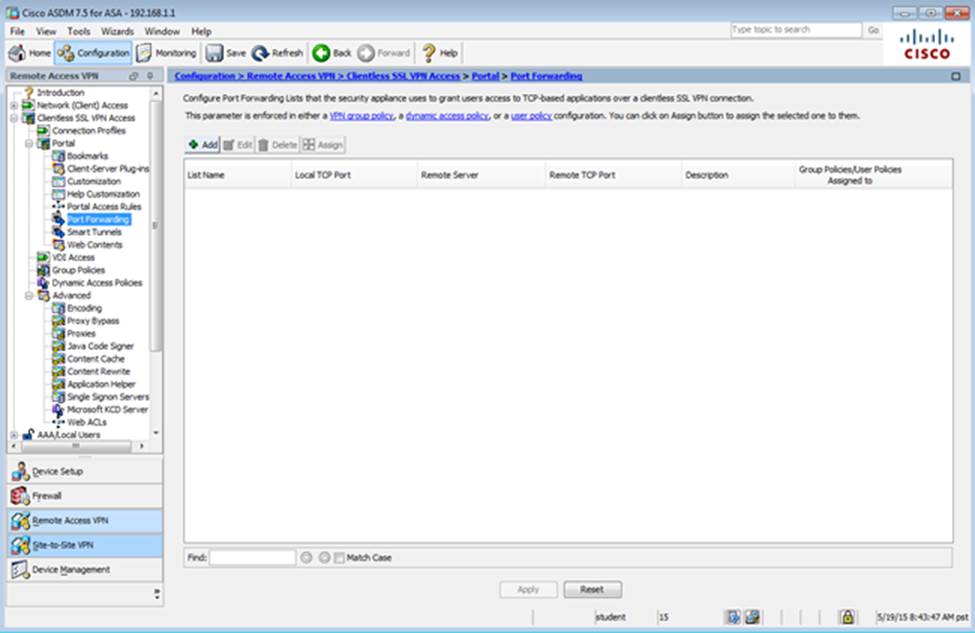
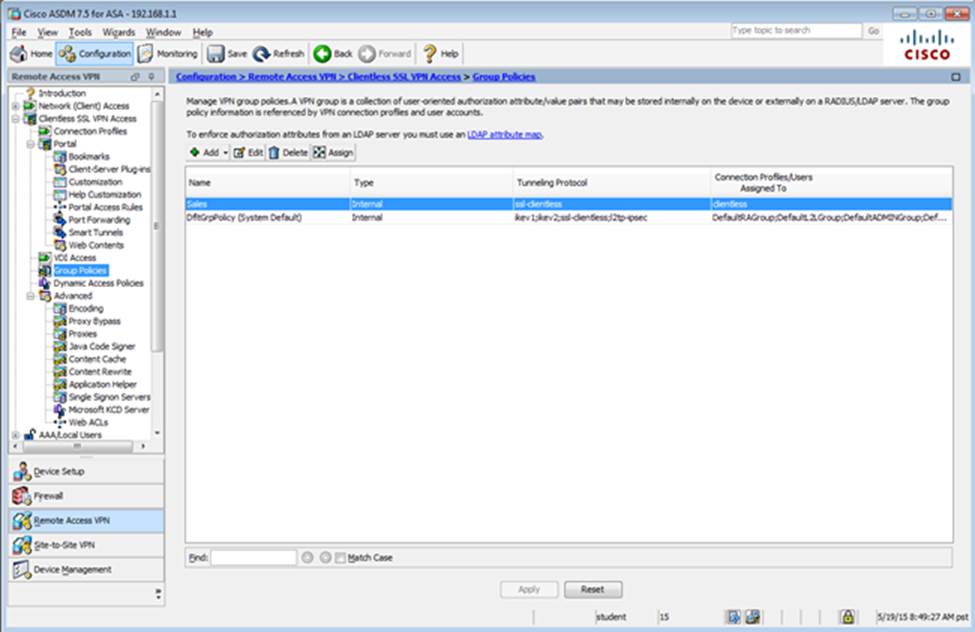

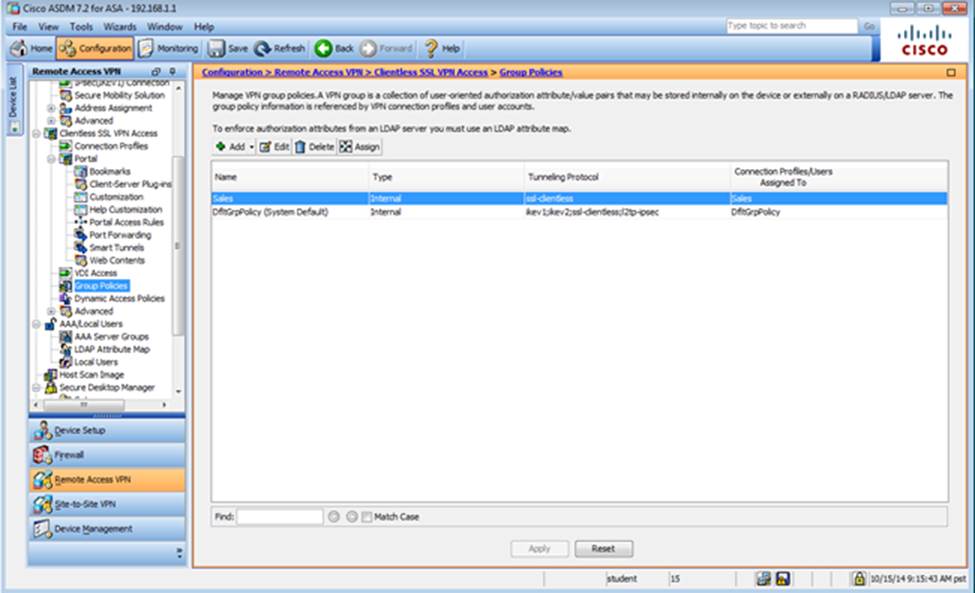
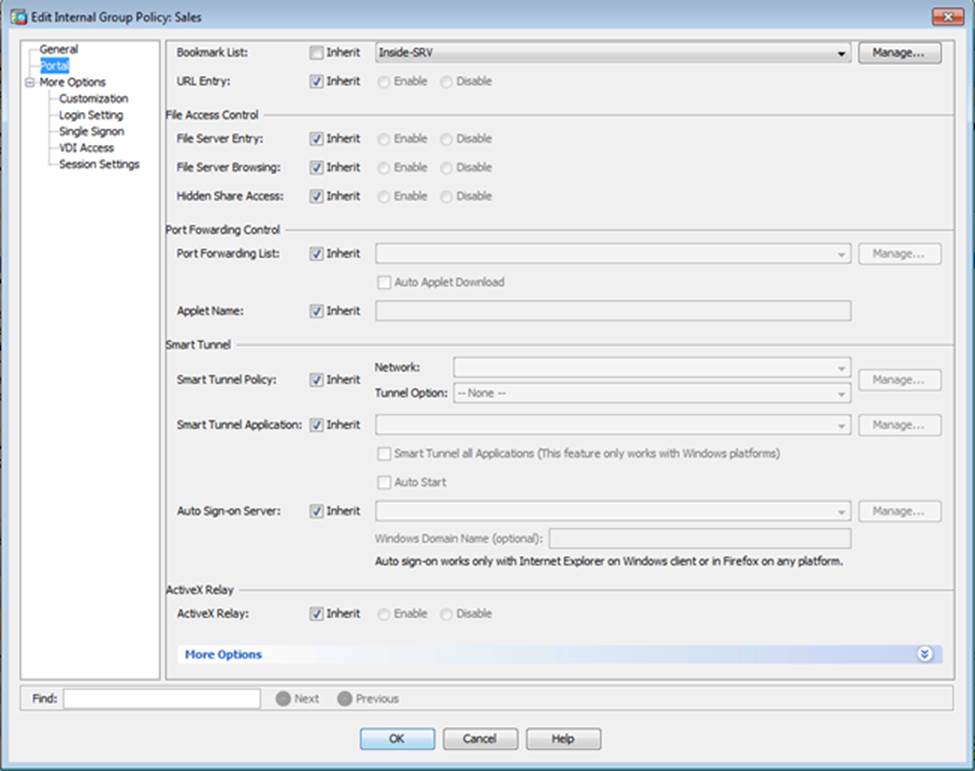
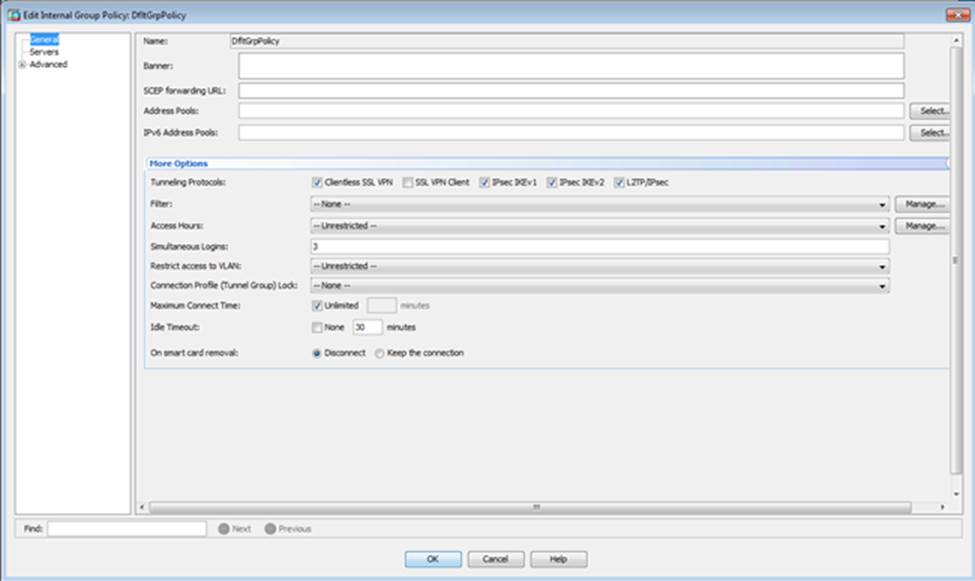

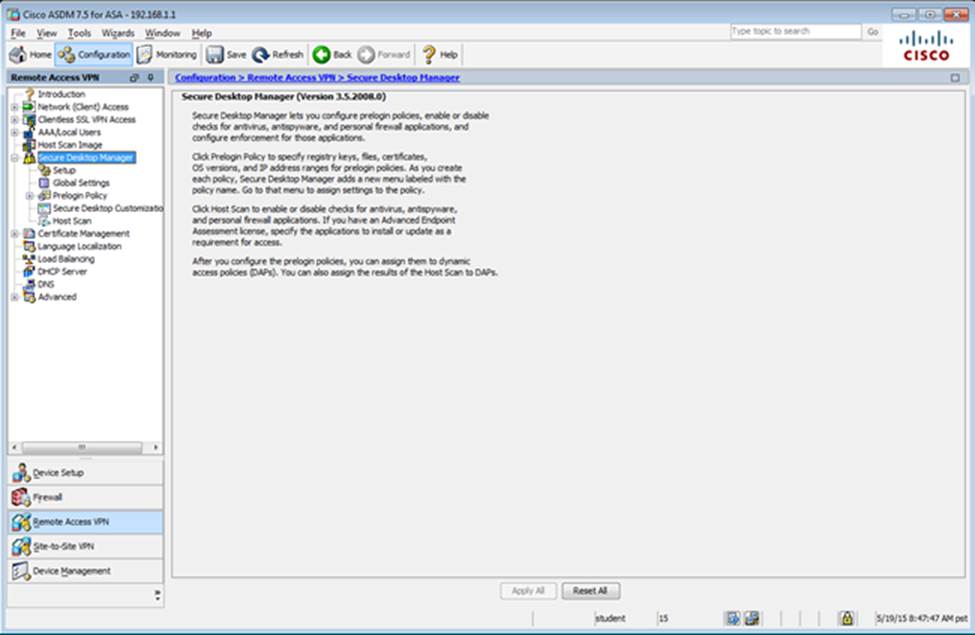

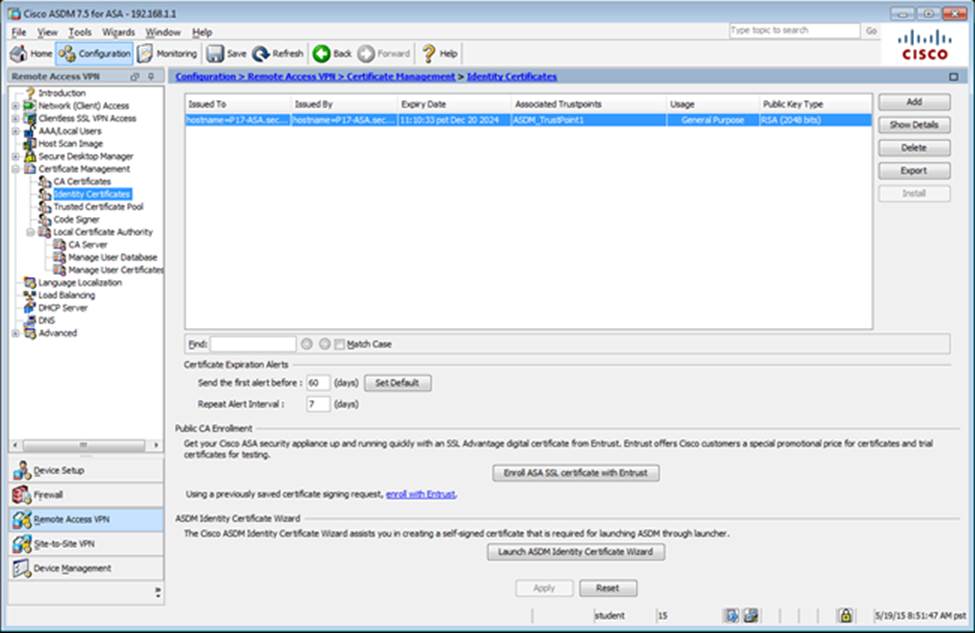
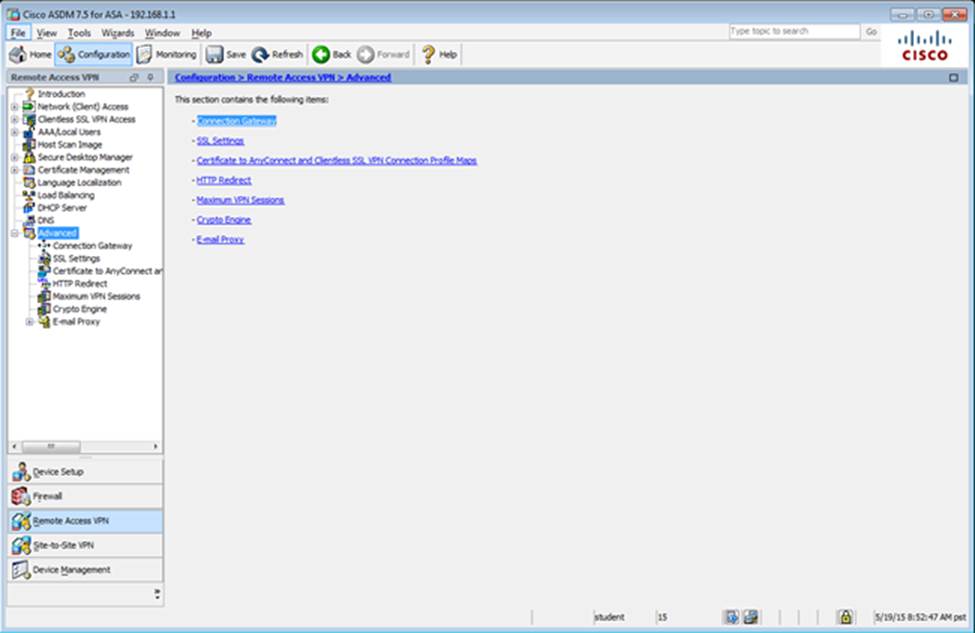

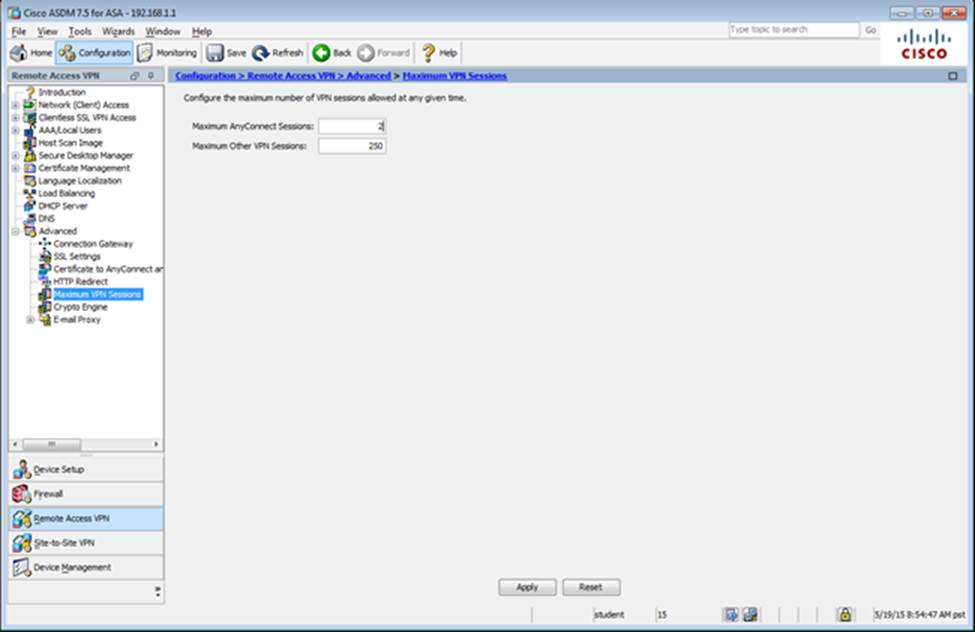

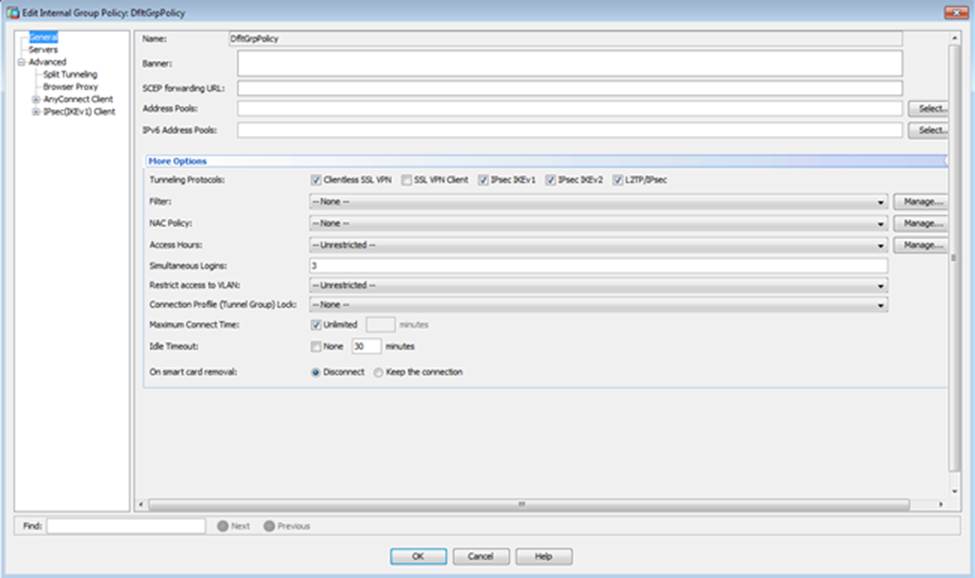

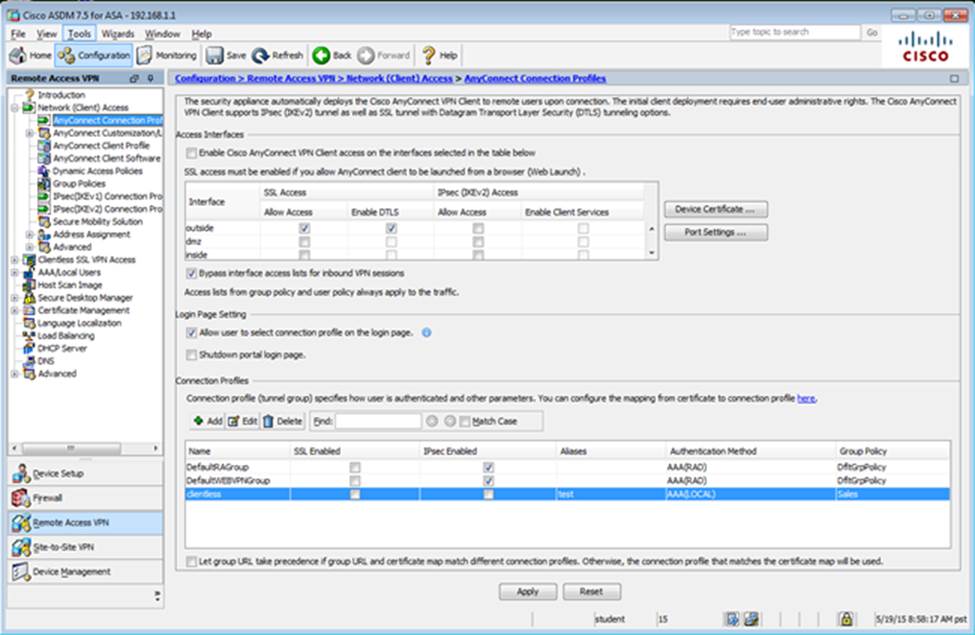

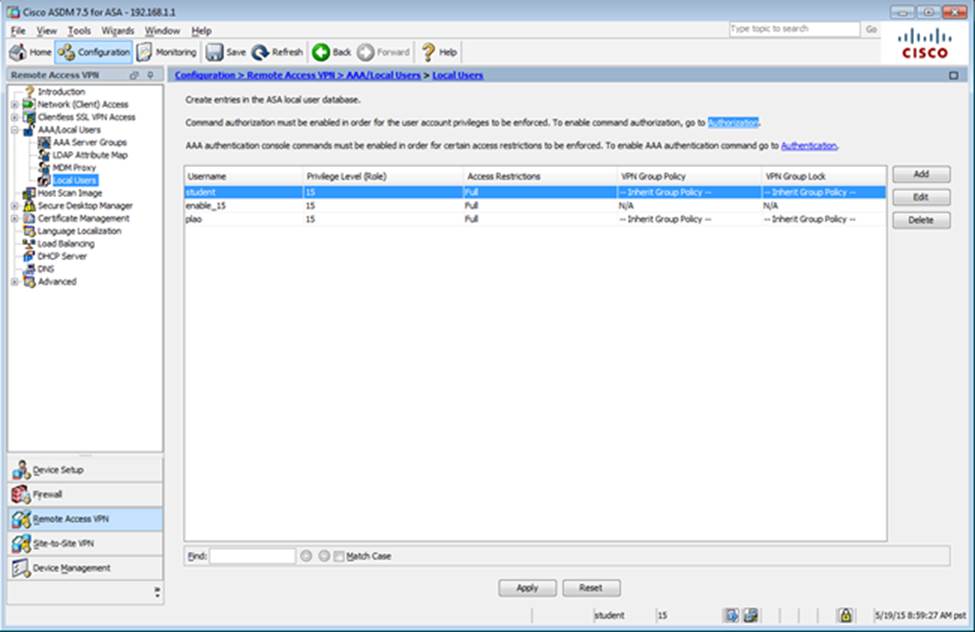
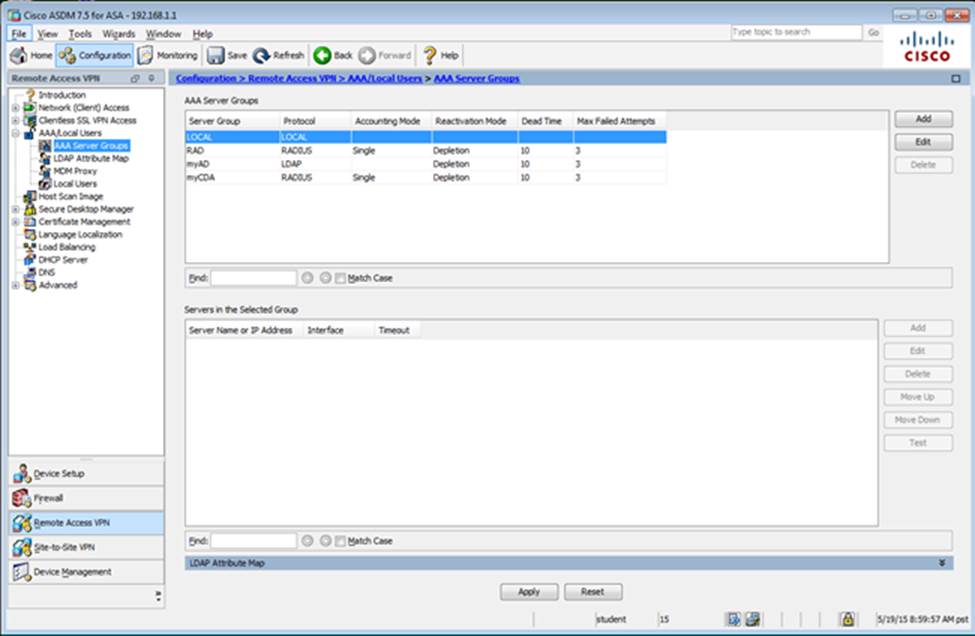
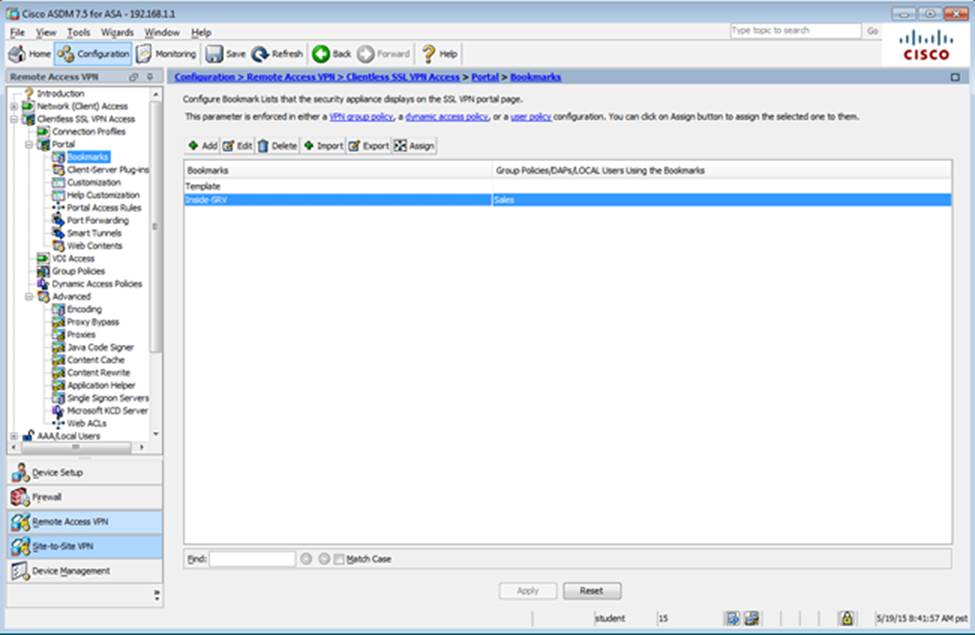
Which two statements regarding the ASA VPN configurations are correct? (Choose two)
- A . The ASA has a certificate issued by an external Certificate Authority associated to the ASDM_TrustPoint1.
- B . The DefaultWEBVPNGroup Connection Profile is using the AAA with RADIUS server method.
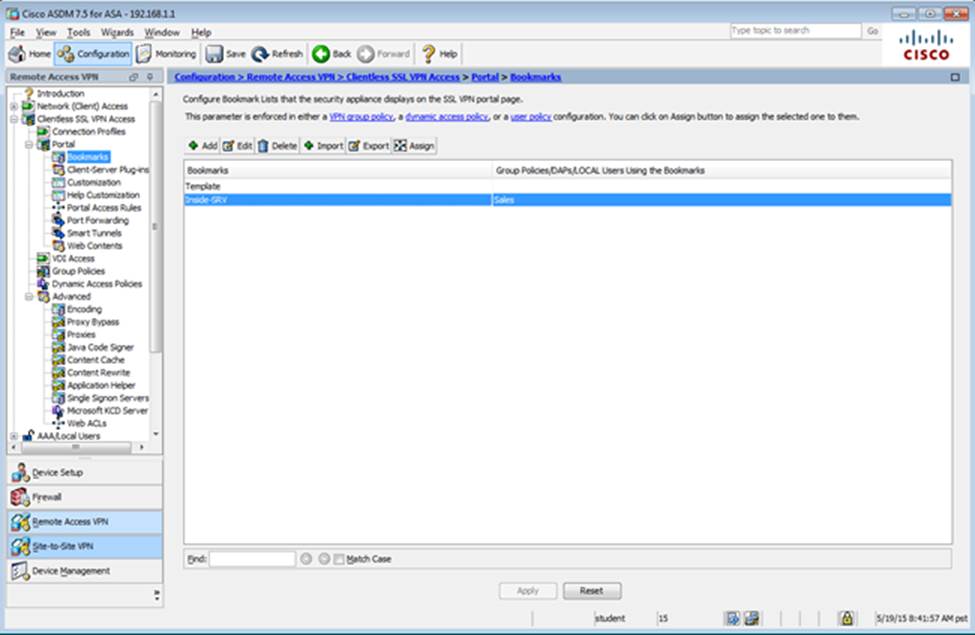
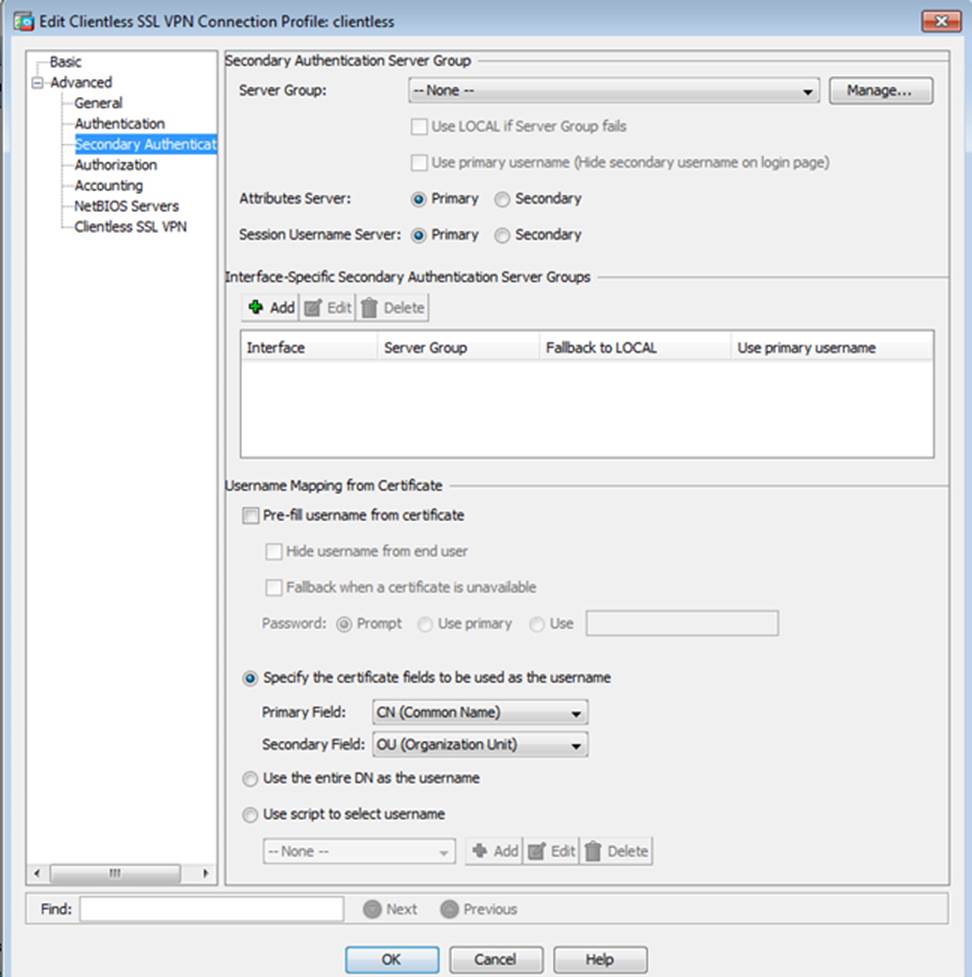
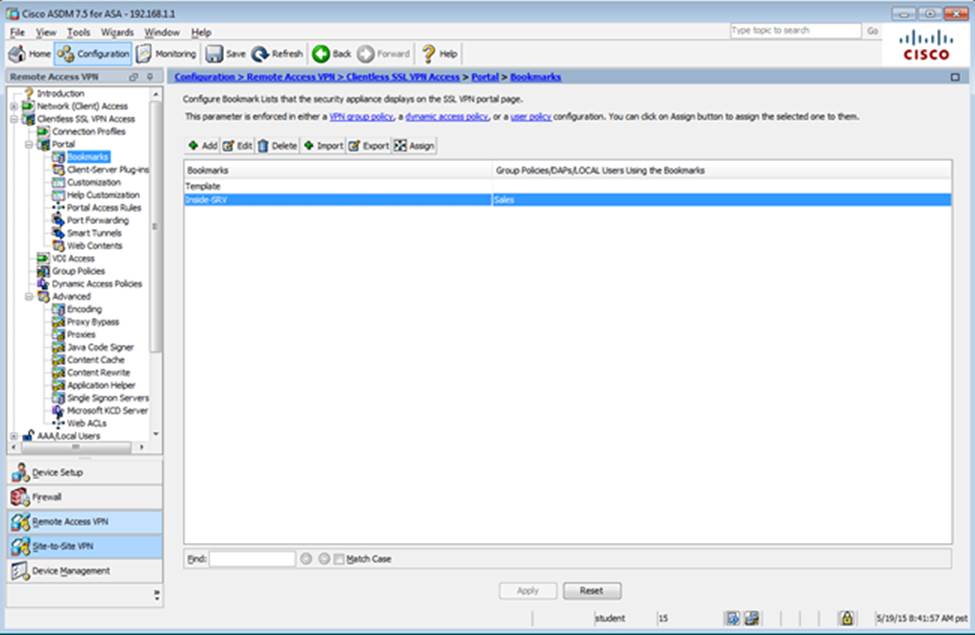
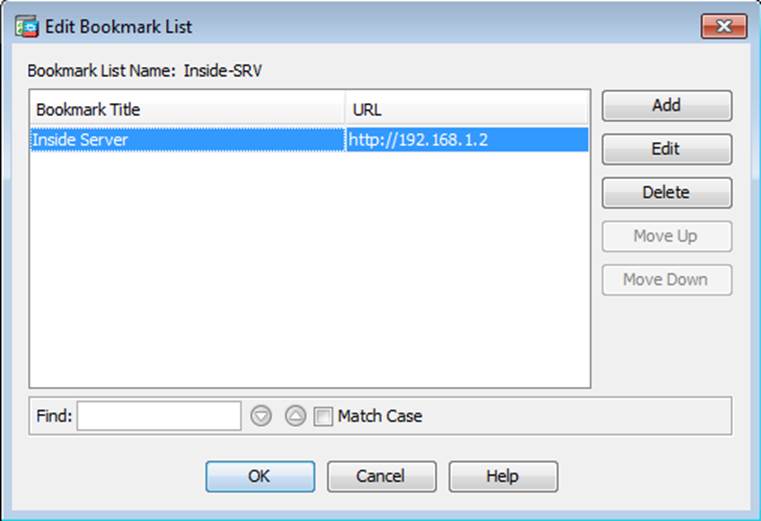
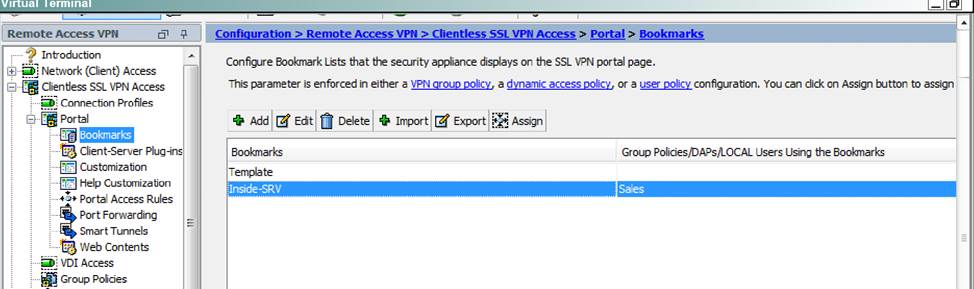
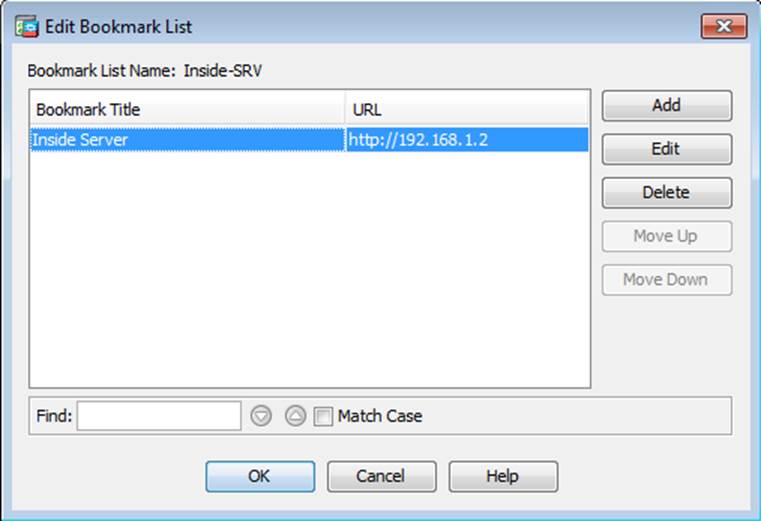
- C . The Inside-SRV bookmark references thehttps://192.168.1.2URL
- D . Only Clientless SSL VPN access is allowed with the Sales group policy
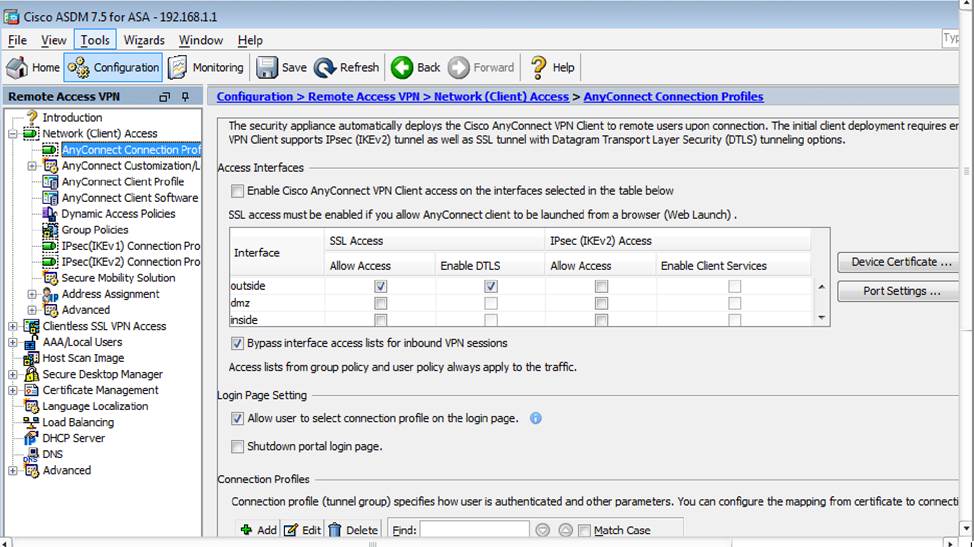
- E . AnyConnect, IPSec IKEv1, and IPSec IKEv2 VPN access is enabled on the outside interface
- F . The Inside-SRV bookmark has not been applied to the Sales group policy
Scenario
In this simulation, you have access to ASDM only. Review the various ASA configurations using ASDM then answer the five multiple choice questions about the ASA SSLVPN configurations.
To access ASDM, click the ASA icon in the topology diagram.
Note: Not all ASDM functionalities are enabled in this simulation.
To see all the menu options available on the left navigation pane, you may also need to un-expand the expanded menu first.
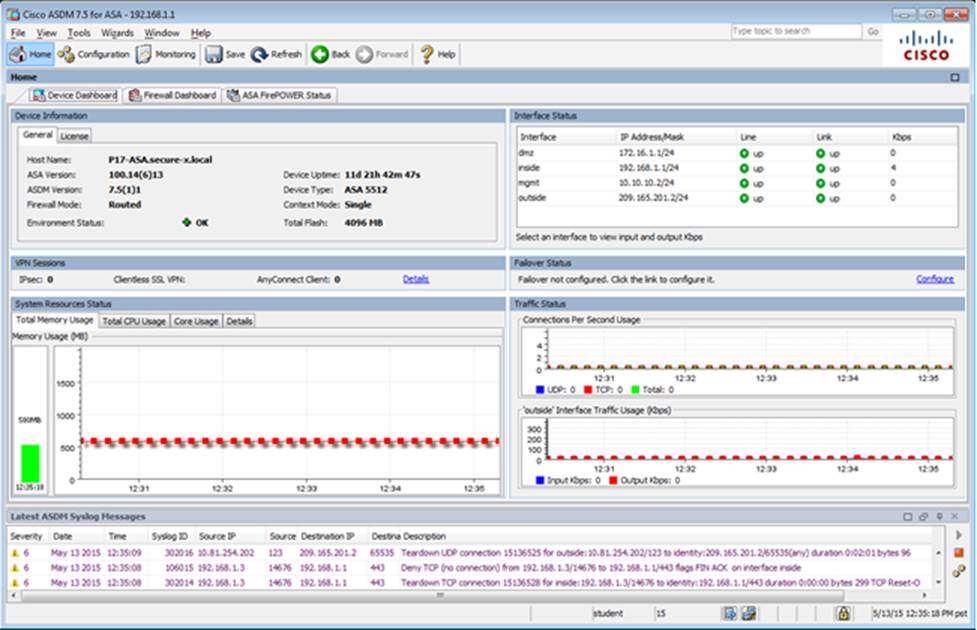
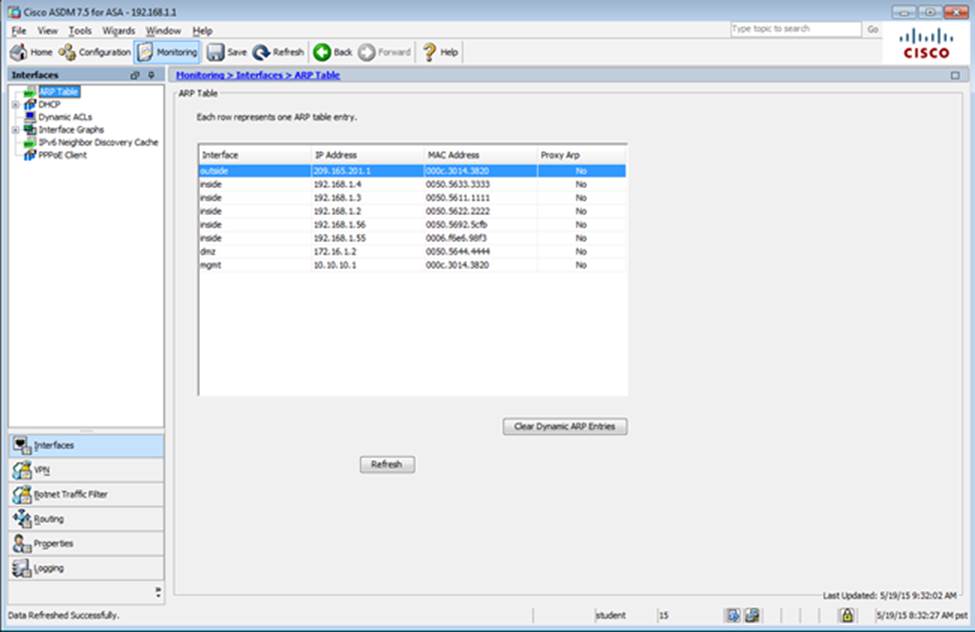
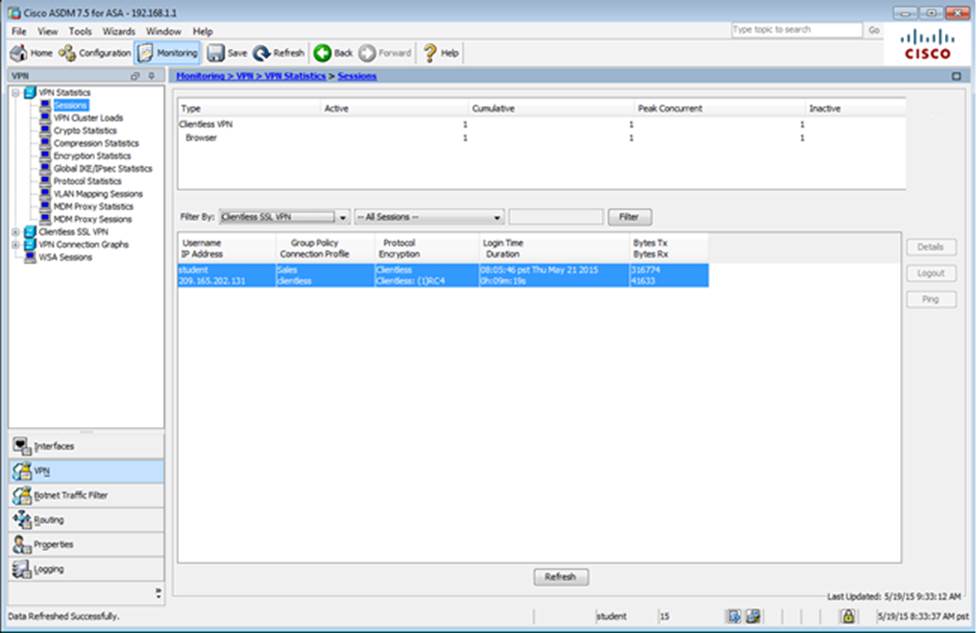
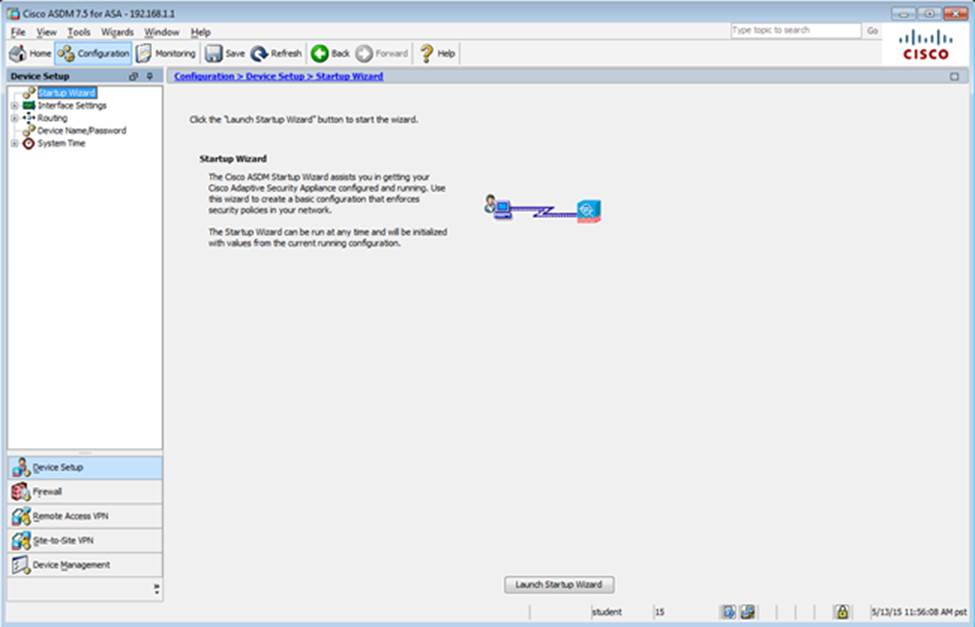

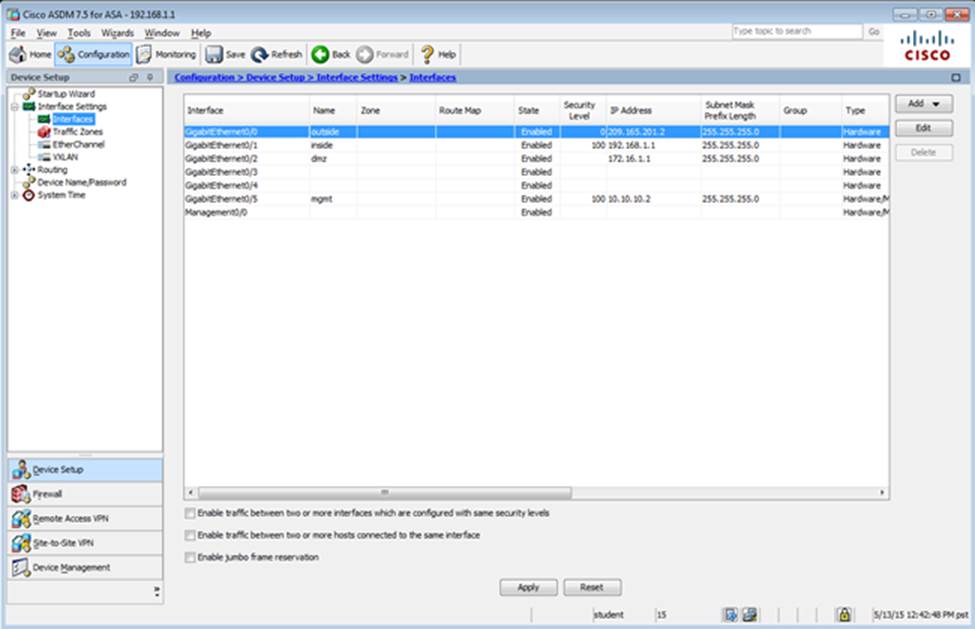
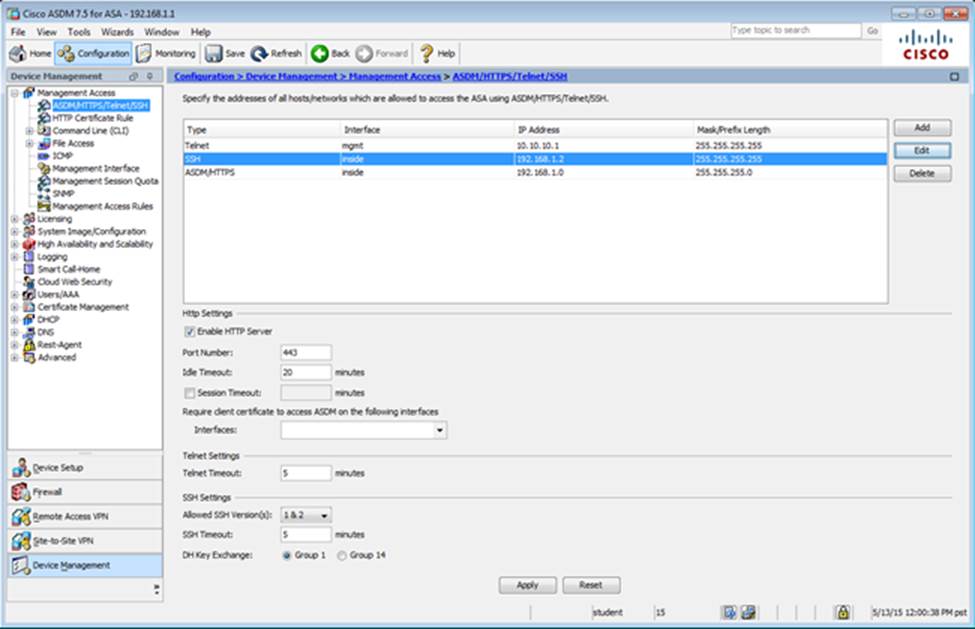
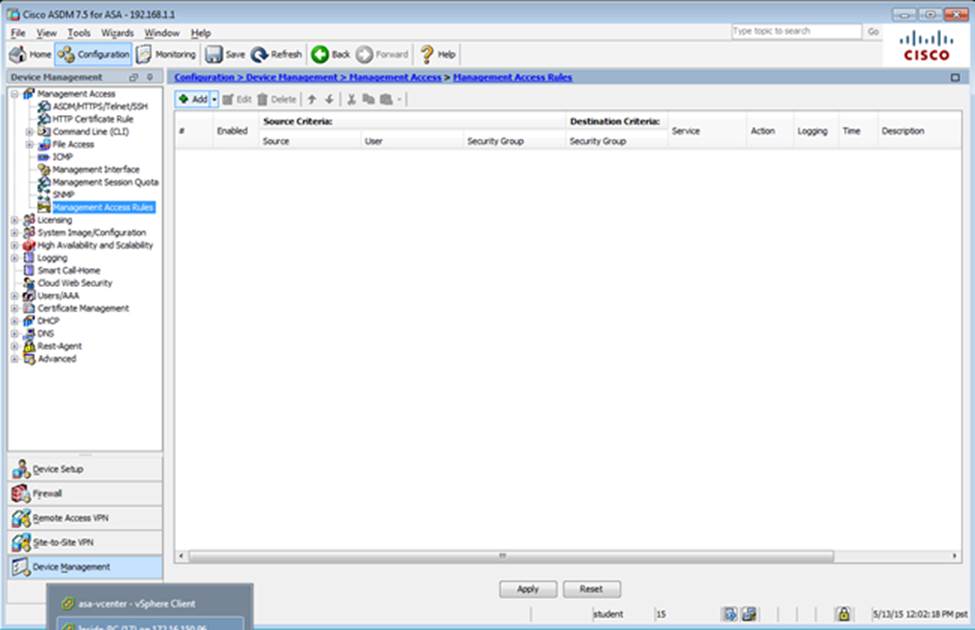
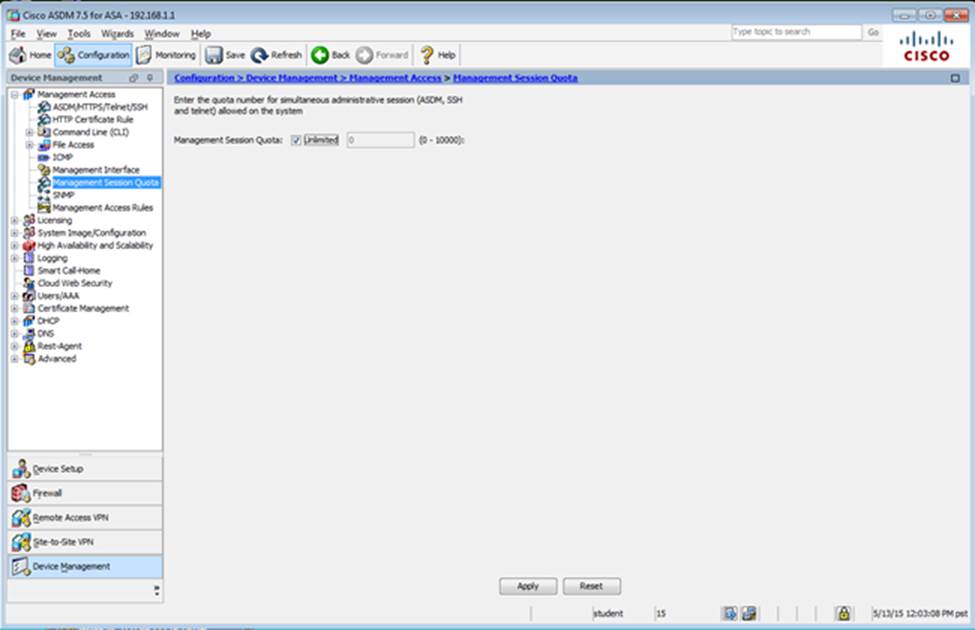
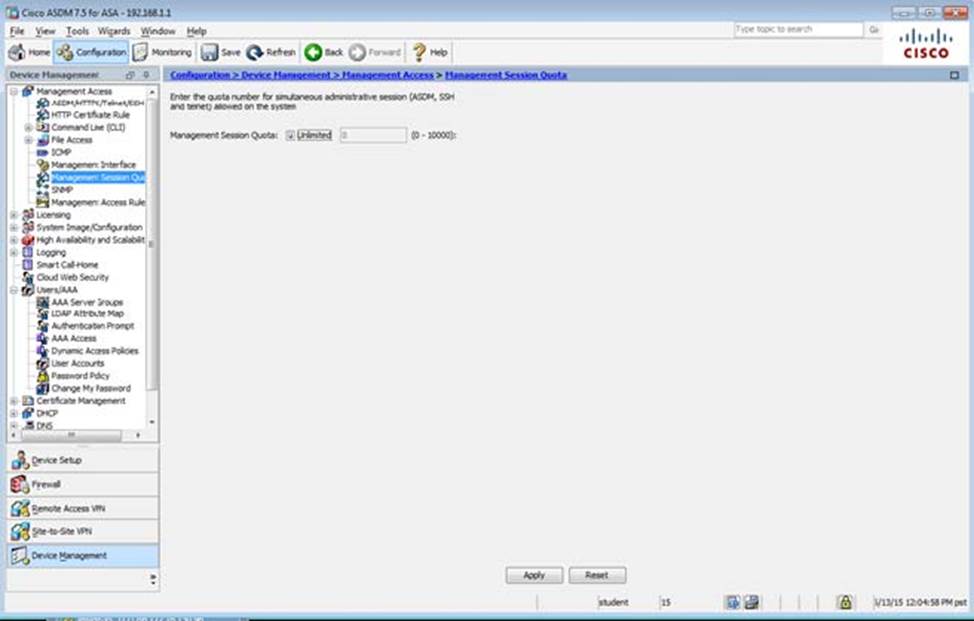
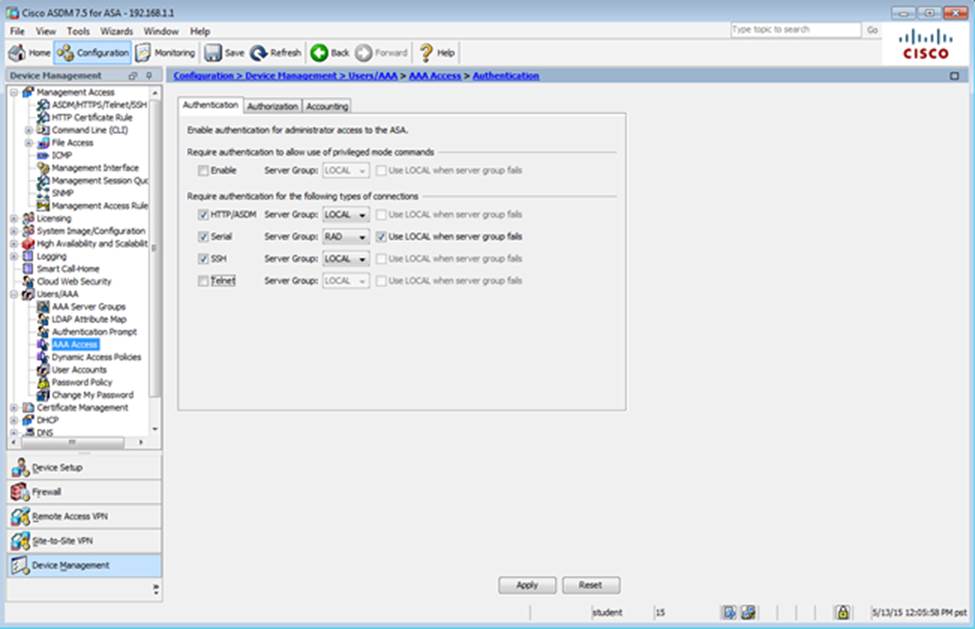
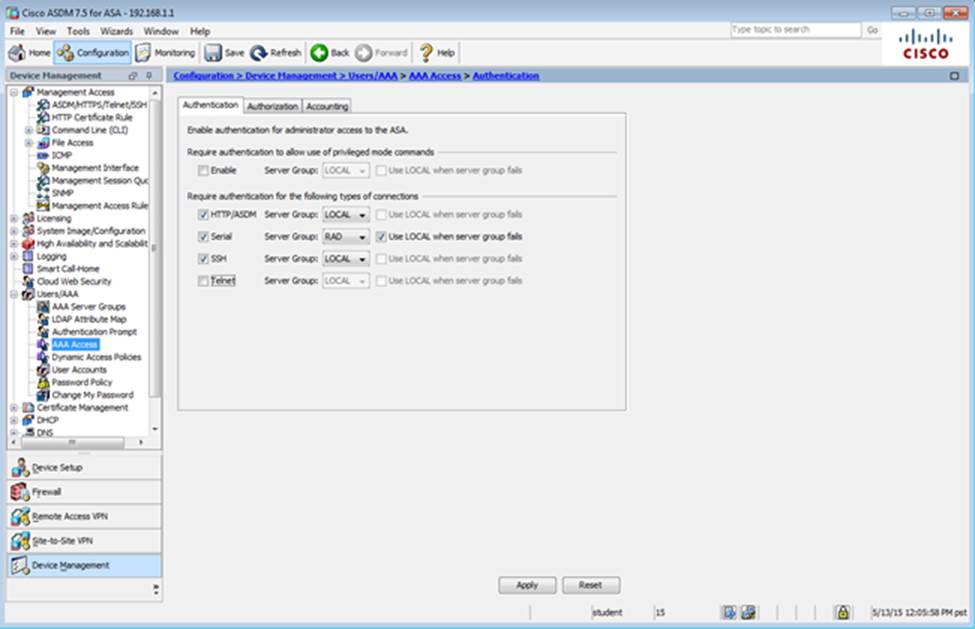

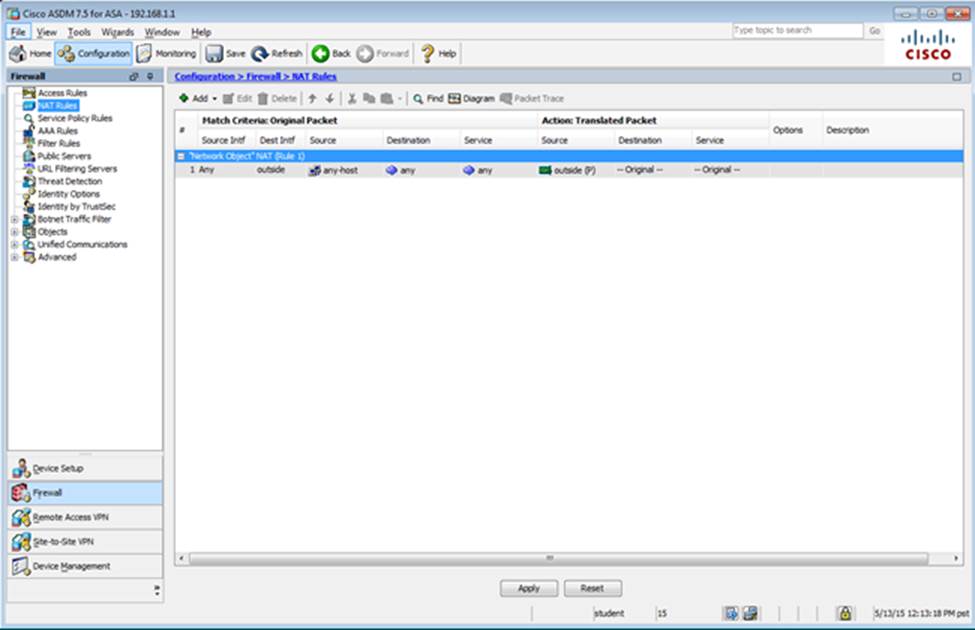
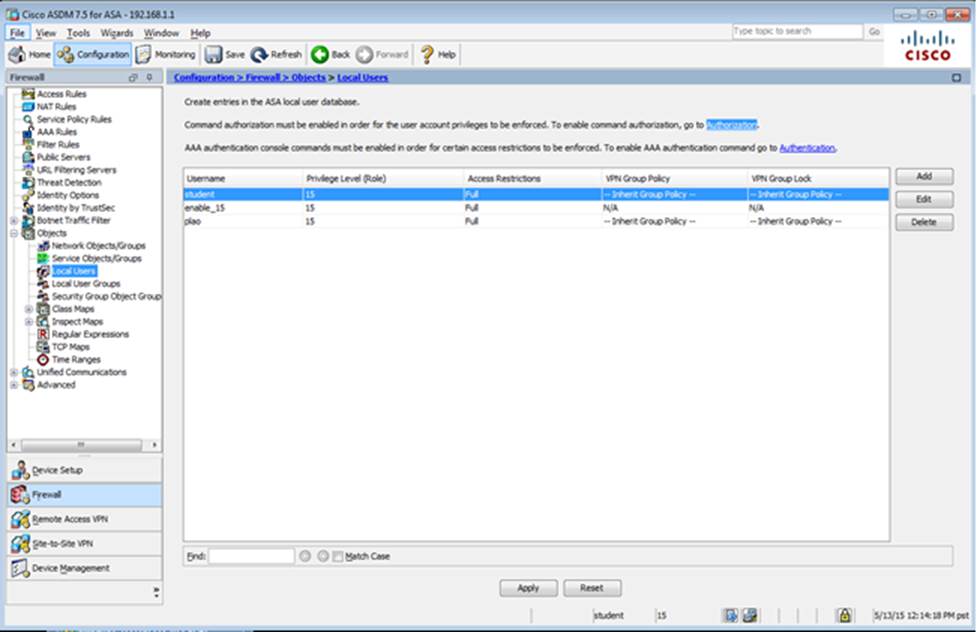
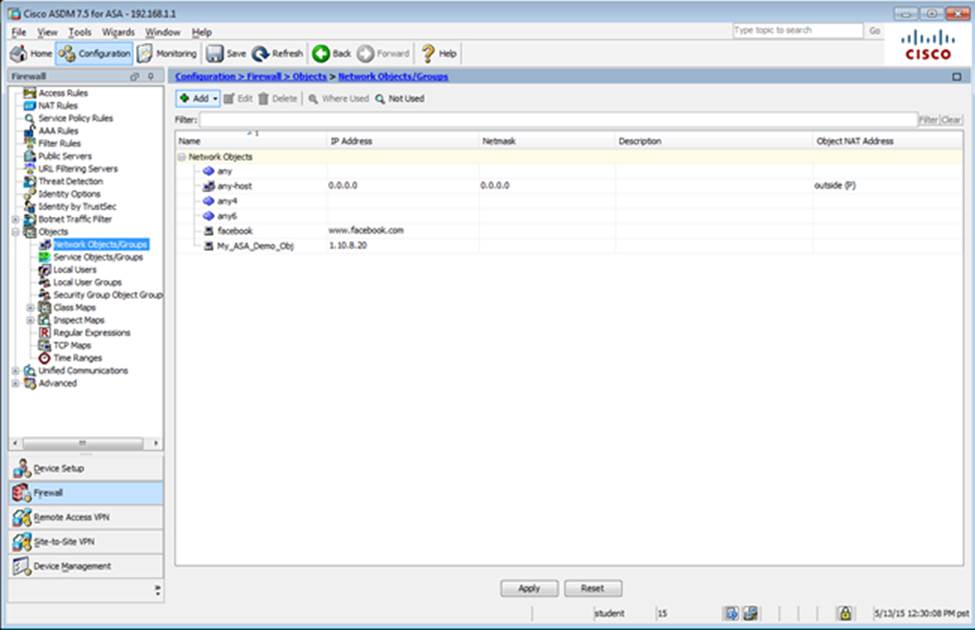

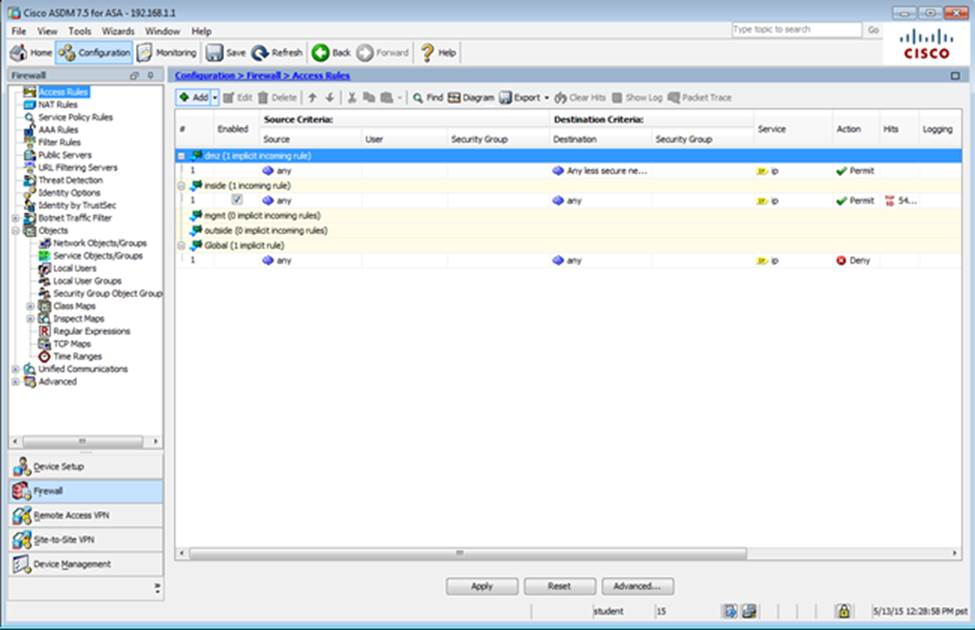
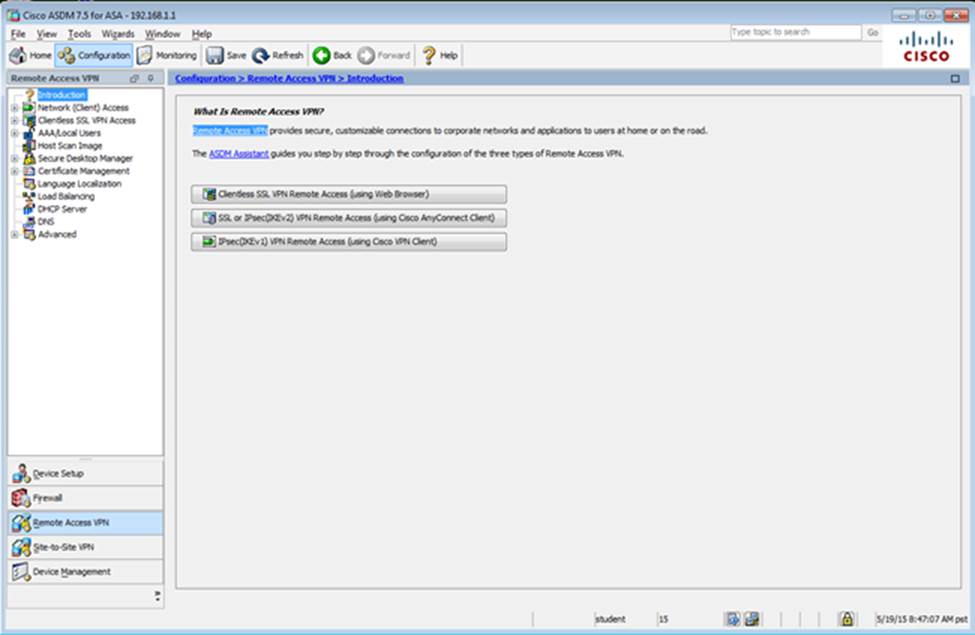
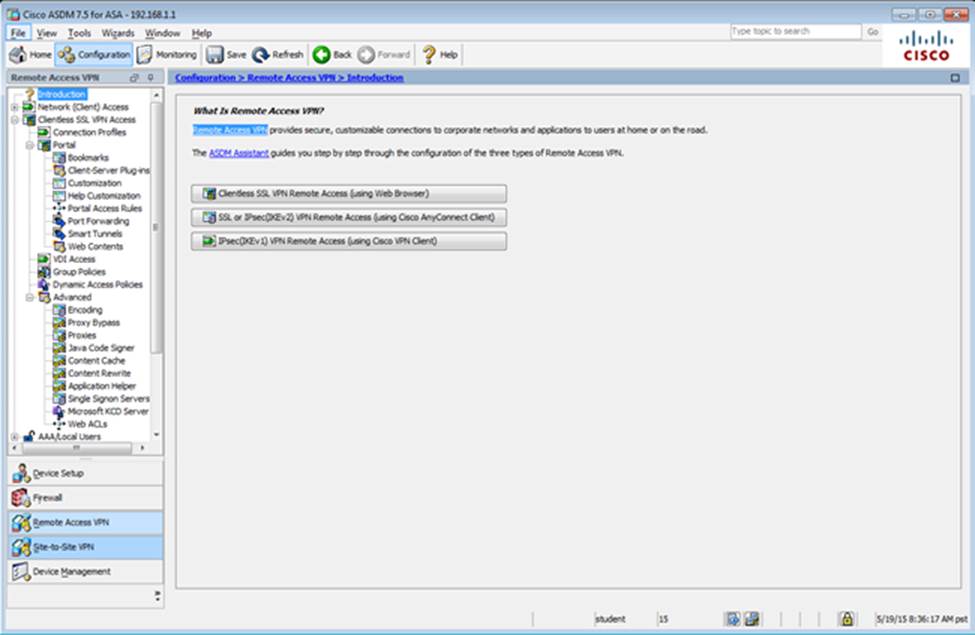
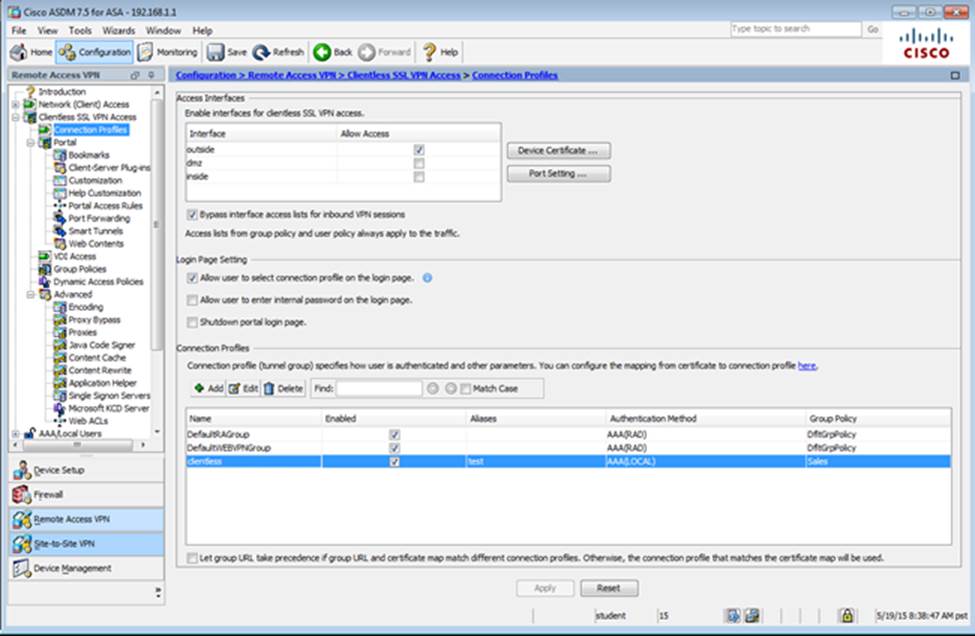
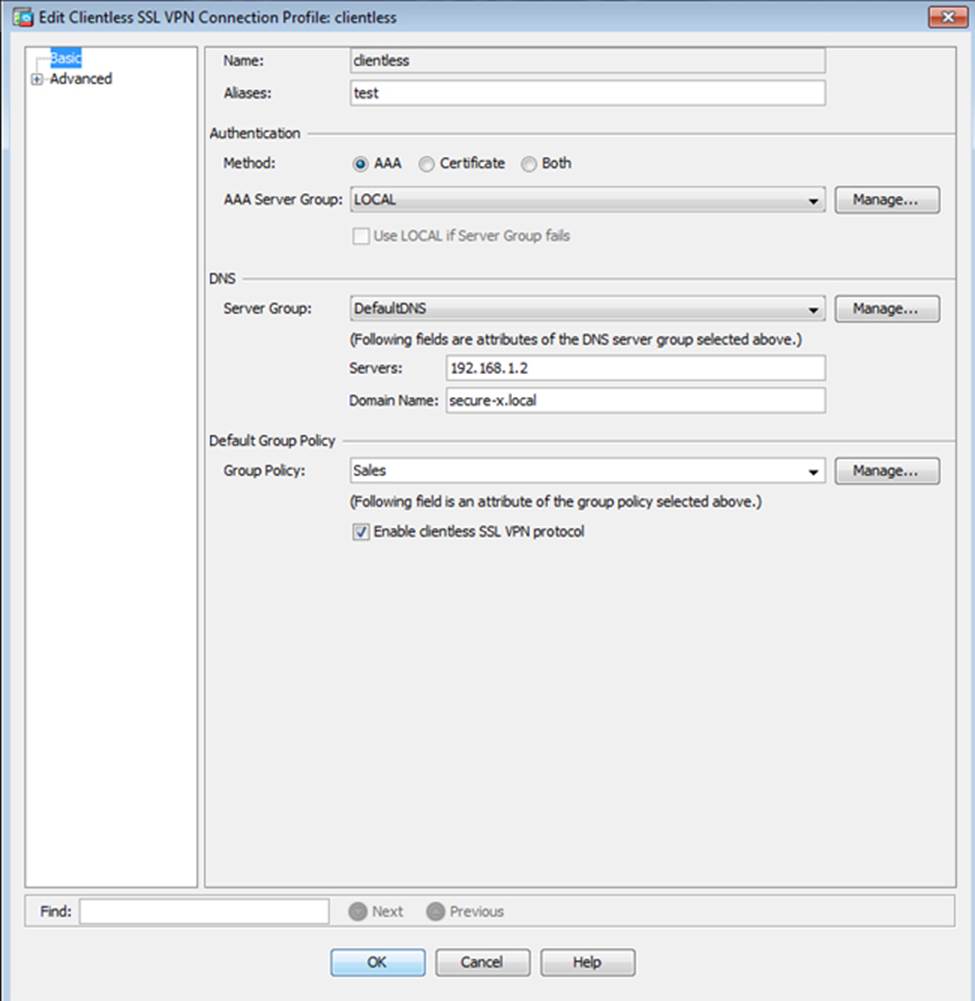
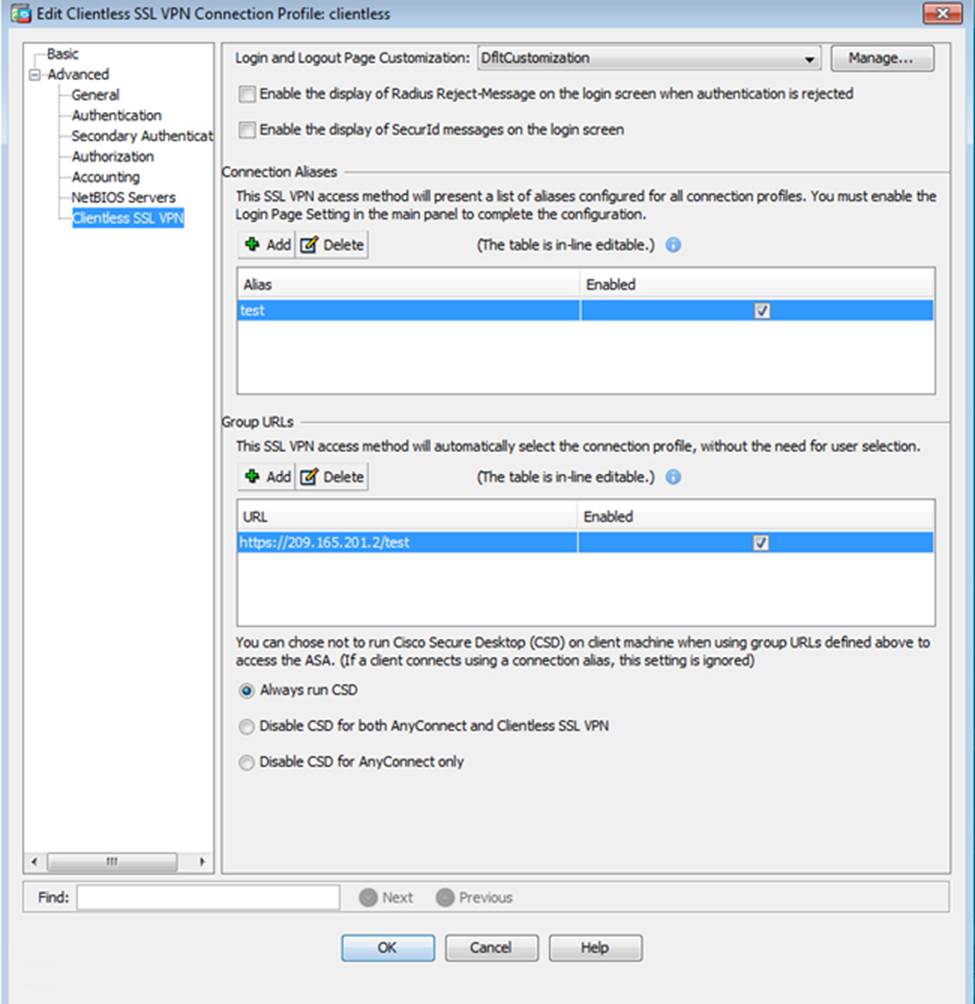
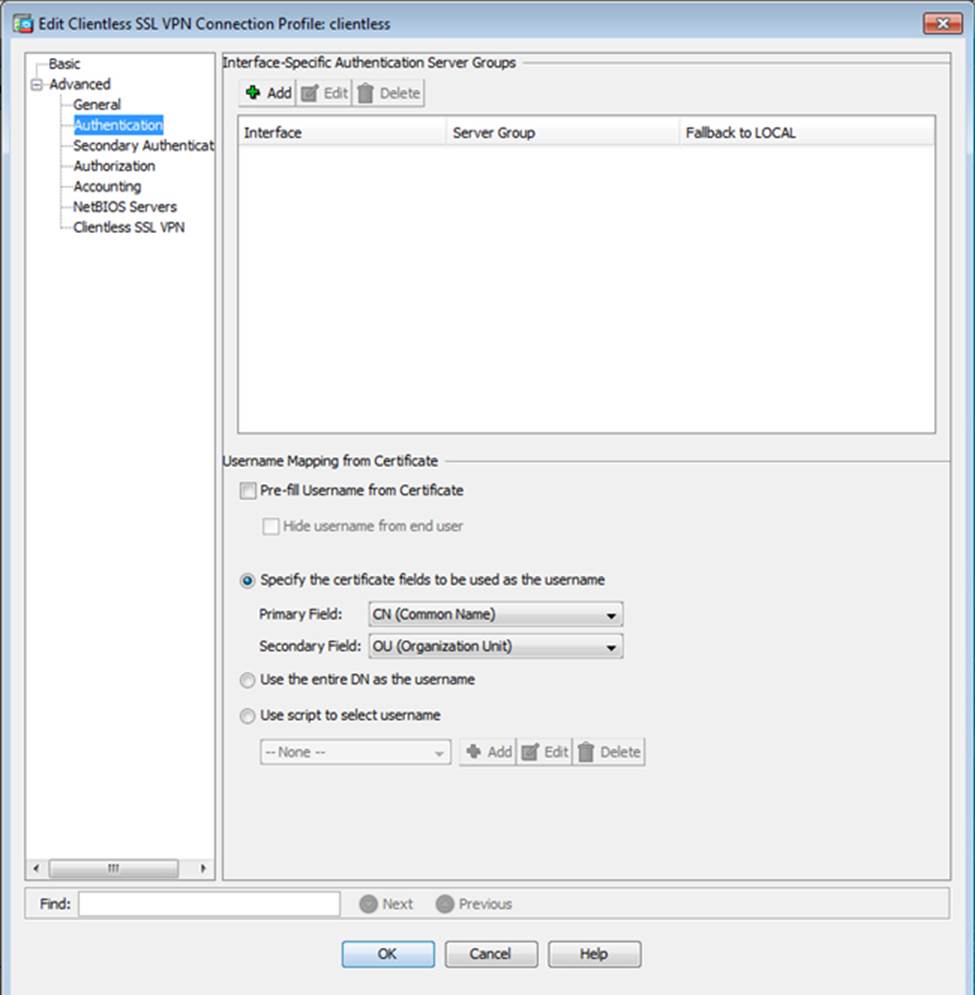
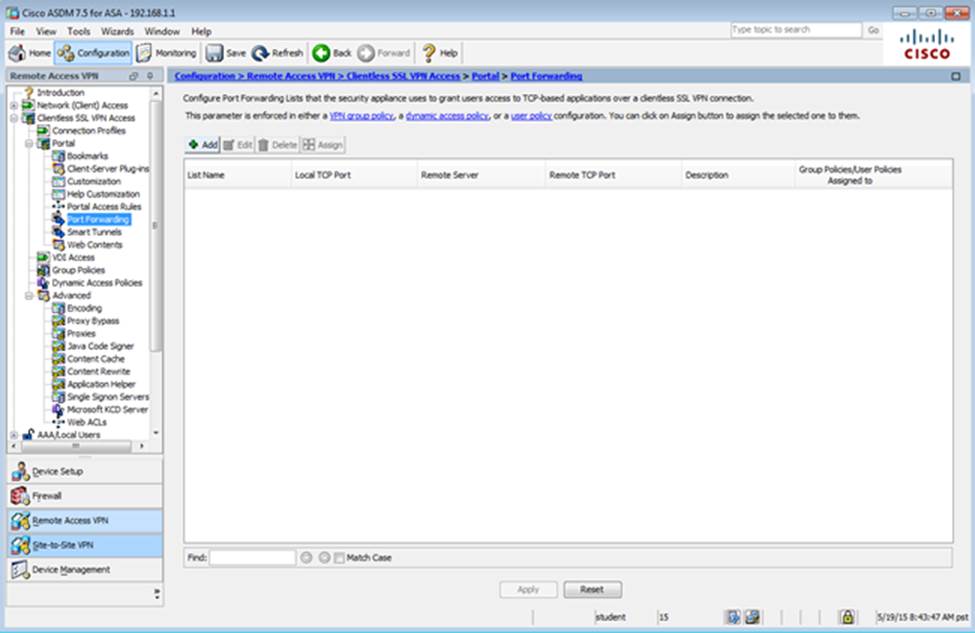
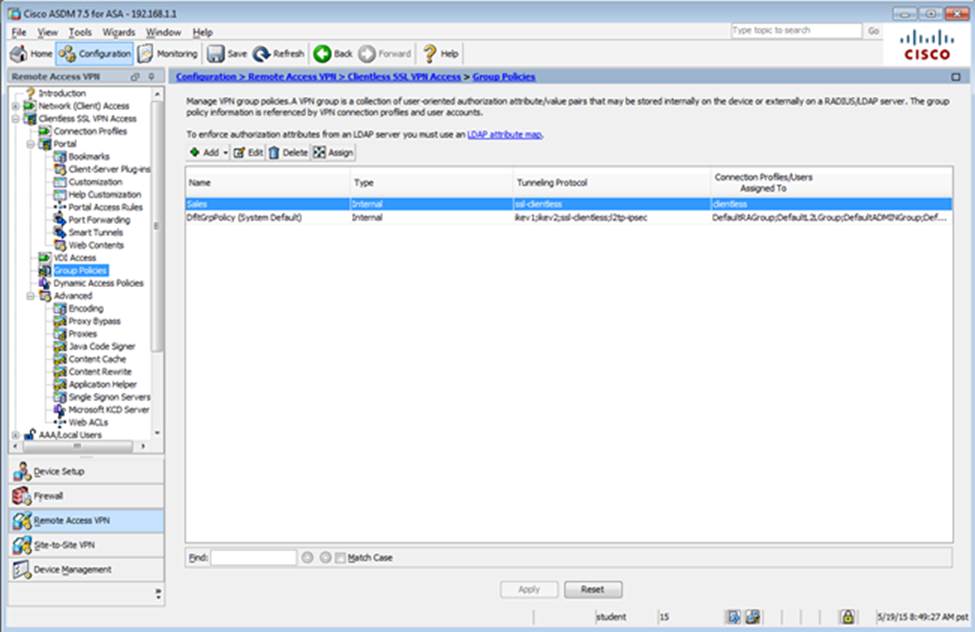
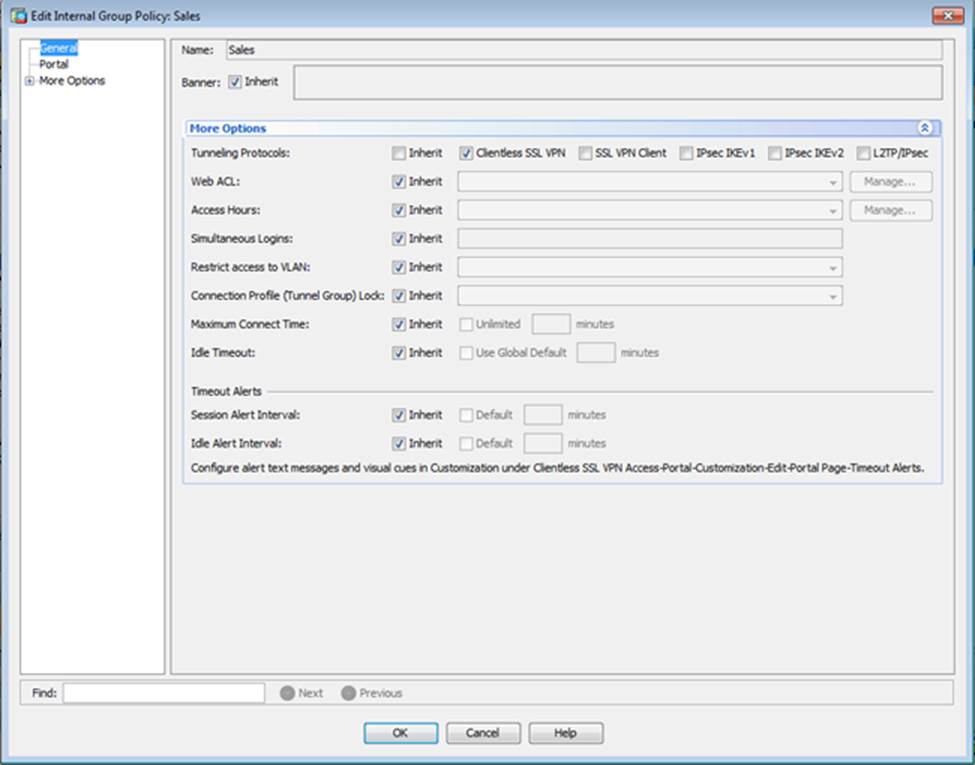
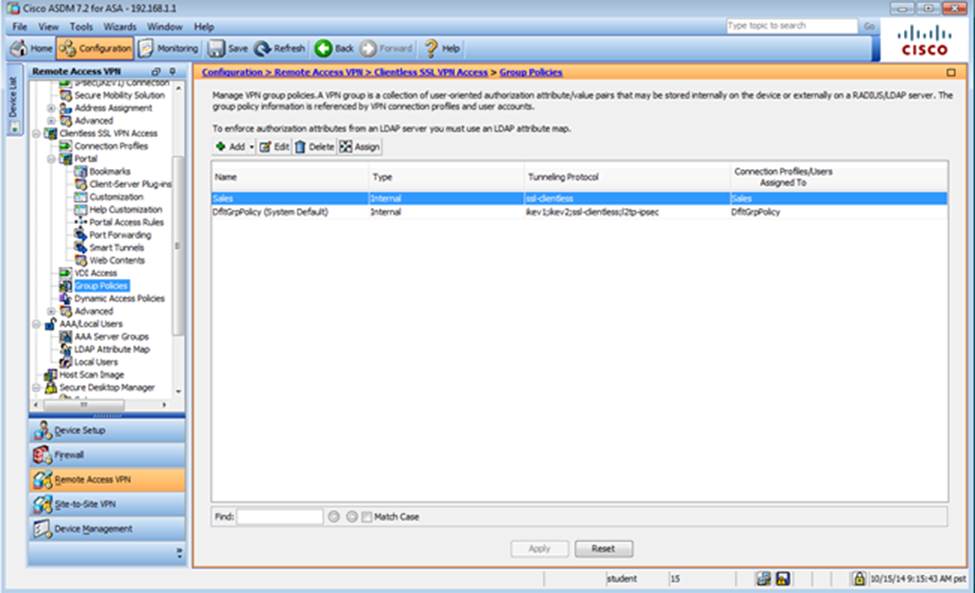
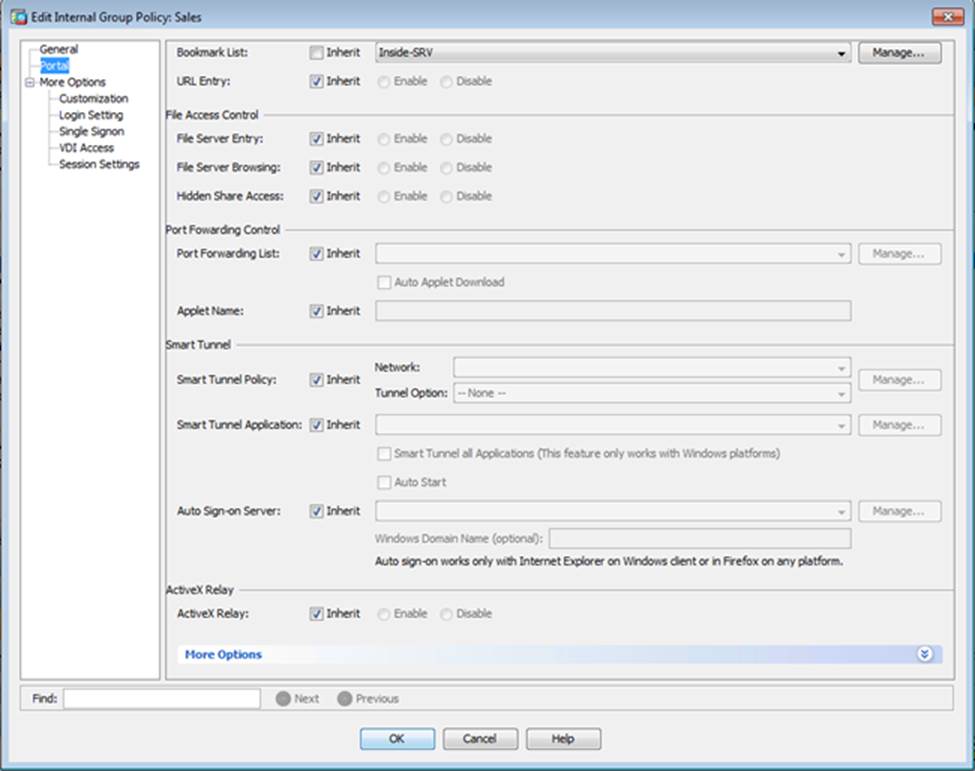
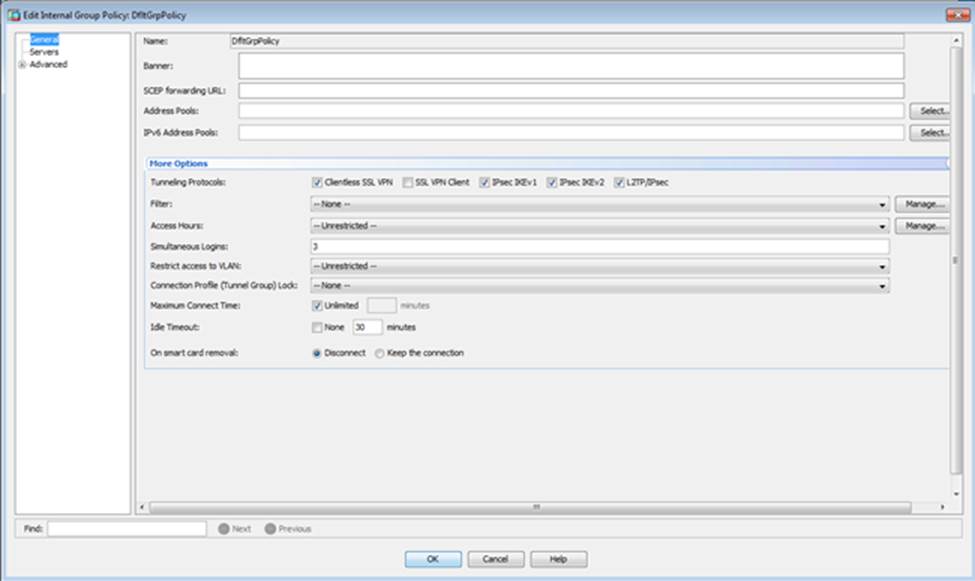
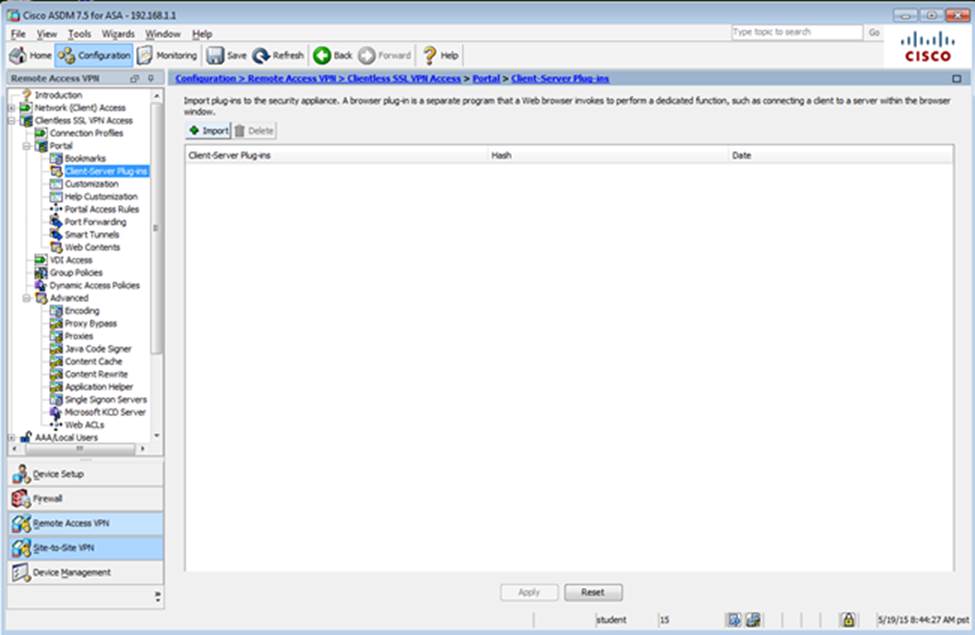


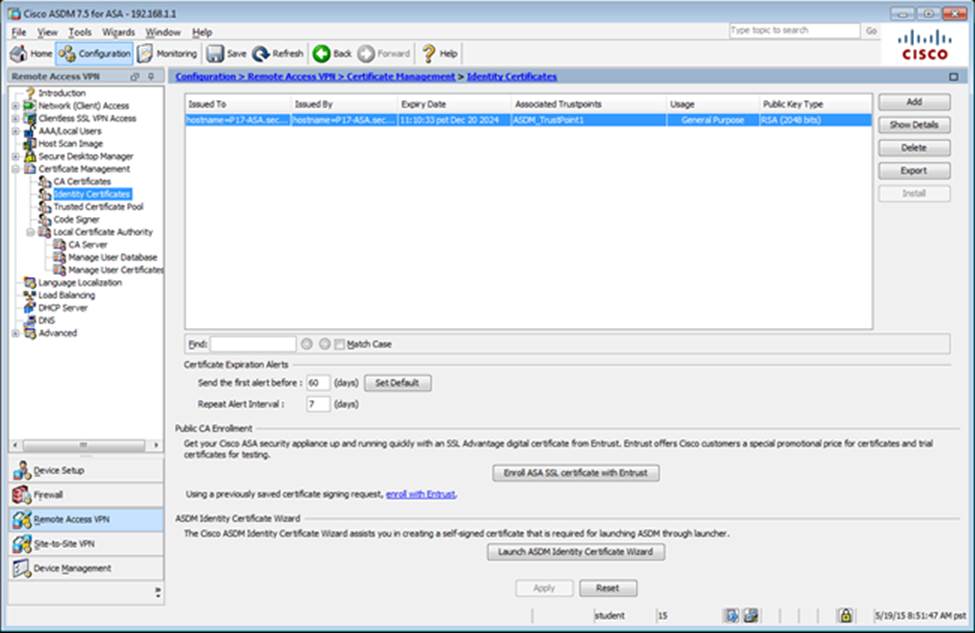
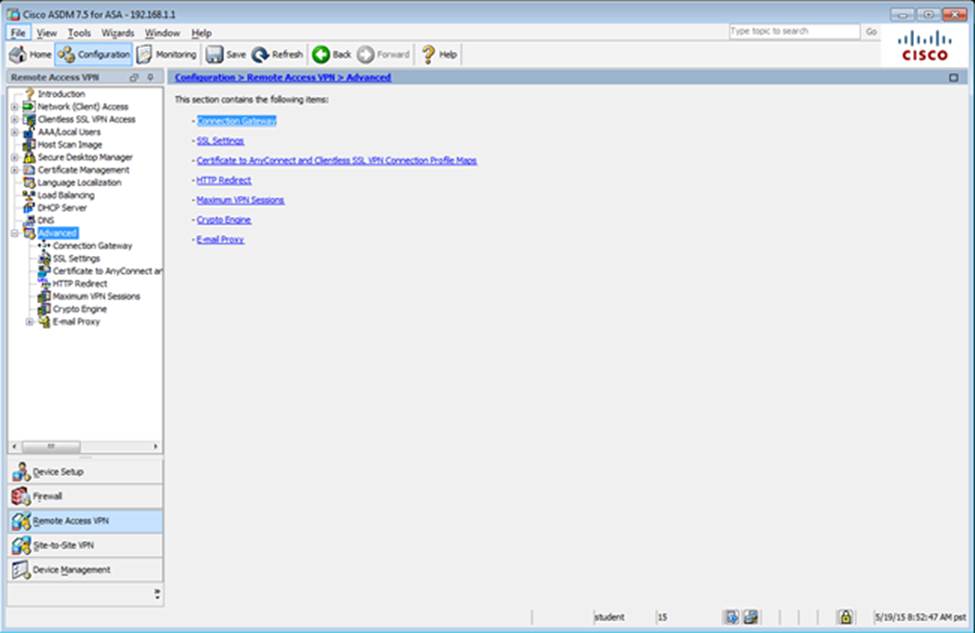
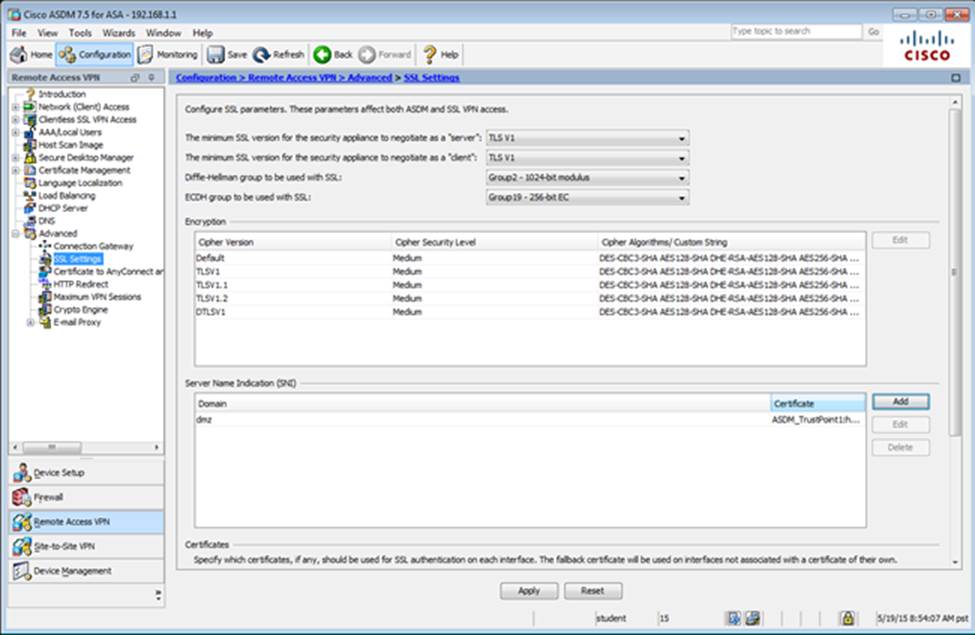

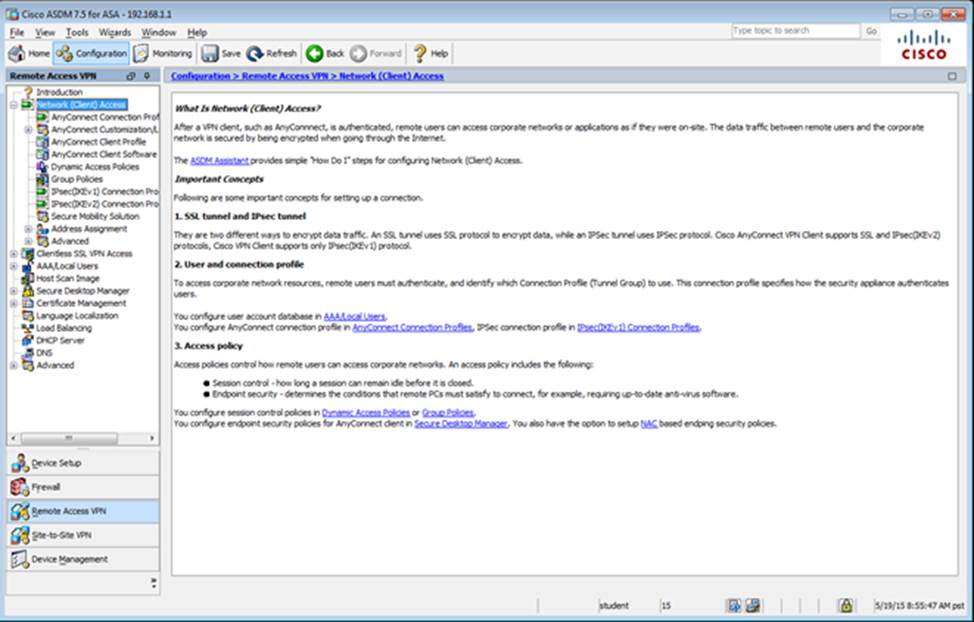

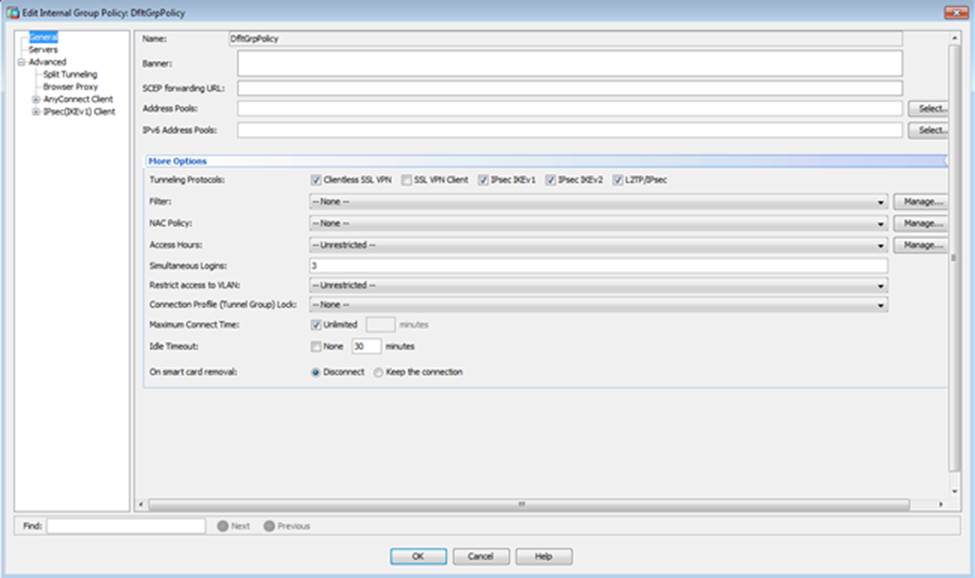
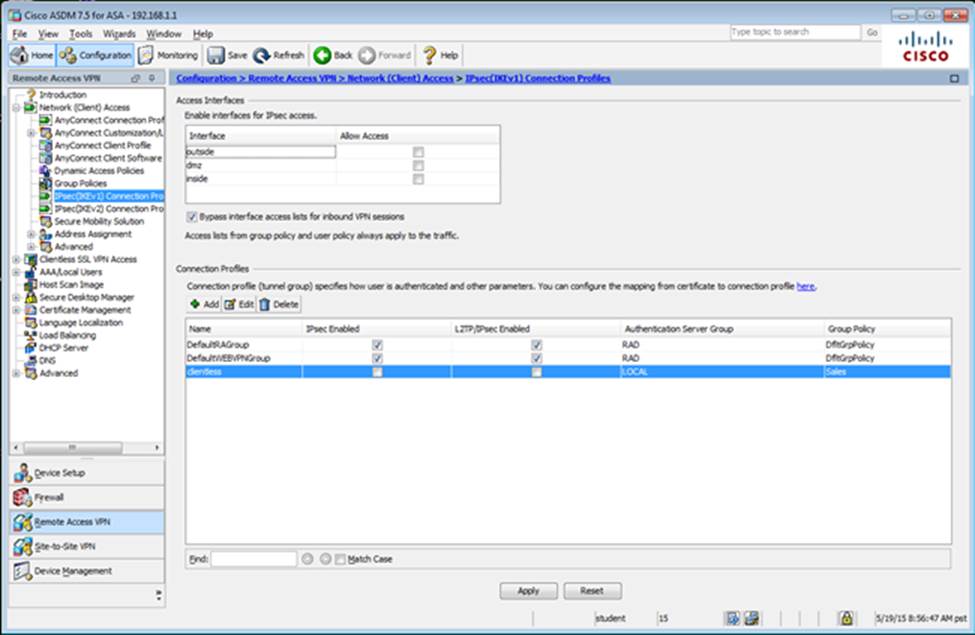
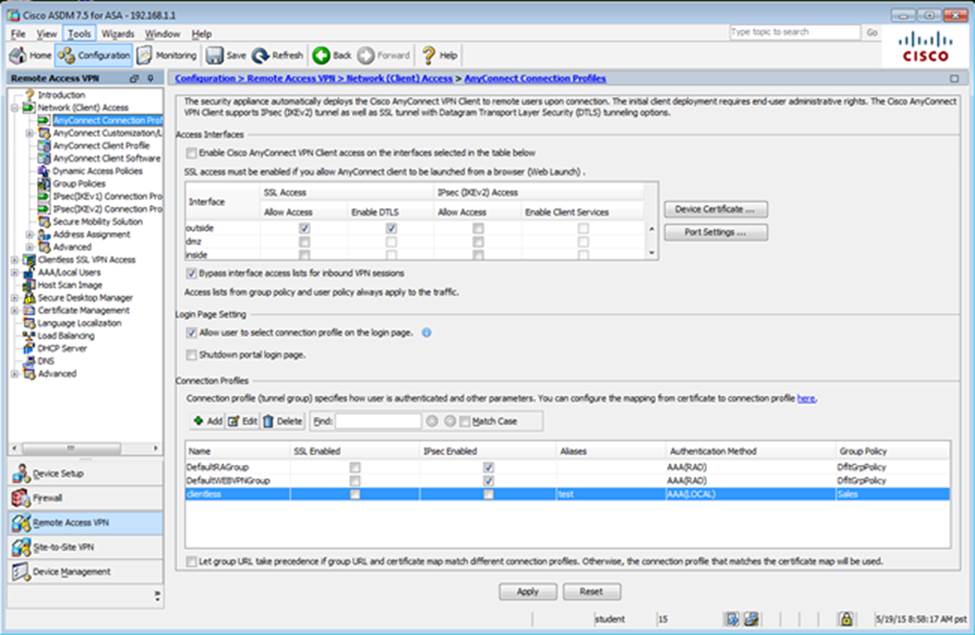
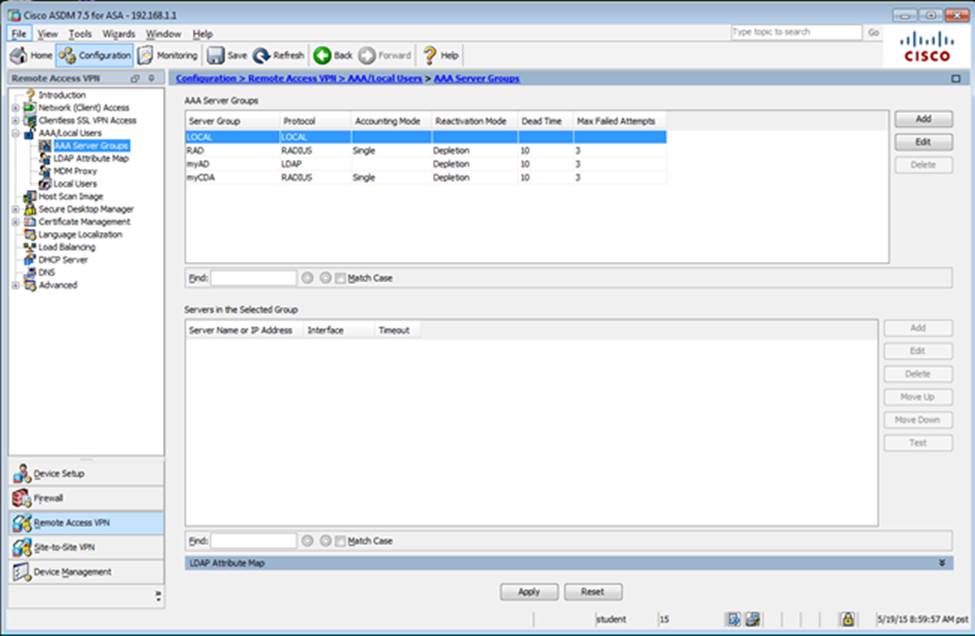
When users login to the Clientless SSLVPN using https://209.165.201.2/test, which group policy will be applied?
- A . test
- B . clientless
- C . Sales
- D . DfltGrpPolicy
- E . DefaultRAGroup
- F . DefaultWEBVPNGroup
Latest 210-260 Dumps Valid Version with 498 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund



Hello. And Bye.