Cisco 210-260 Implementing Cisco Network Security Online Training
Cisco 210-260 Online Training
The questions for 210-260 were last updated at Feb 23,2026.
- Exam Code: 210-260
- Exam Name: Implementing Cisco Network Security
- Certification Provider: Cisco
- Latest update: Feb 23,2026
What type of attack was the Stuxnet virus?
- A . cyber warfare
- B . hacktivism
- C . botnet
- D . social engineering
What type of algorithm uses the same key to encrypt and decrypt data?
- A . a symmetric algorithm
- B . an asymmetric algorithm
- C . a Public Key Infrastructure algorithm
- D . an IP security algorithm
Refer to the exhibit.
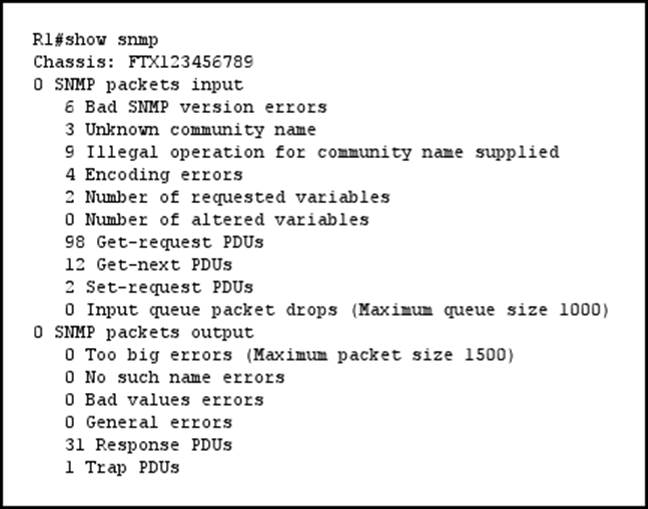
How many times was a read-only string used to attempt a write operation?
- A . 9
- B . 6
- C . 4
- D . 3
- E . 2
Refer to the exhibit.
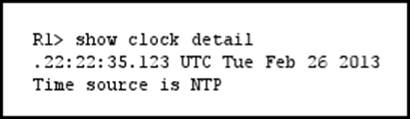
Which statement about the device time is true?
- A . The time is authoritative, but the NTP process has lost contact with its servers.
- B . The time is authoritative because the clock is in sync.
- C . The clock is out of sync.
- D . NTP is configured incorrectly.
- E . The time is not authoritative.
How does the Cisco ASA use Active Directory to authorize VPN users?
- A . It queries the Active Directory server for a specific attribute for the specified user.
- B . It sends the username and password to retrieve an ACCEPT or REJECT message from the Active Directory server.
- C . It downloads and stores the Active Directory database to query for future authorization requests.
- D . It redirects requests to the Active Directory server defined for the VPN group.
Which statement about Cisco ACS authentication and authorization is true?
- A . ACS servers can be clustered to provide scalability.
- B . ACS can query multiple Active Directory domains.
- C . ACS uses TACACS to proxy other authentication servers.
- D . ACS can use only one authorization profile to allow or deny requests.
Refer to the exhibit.
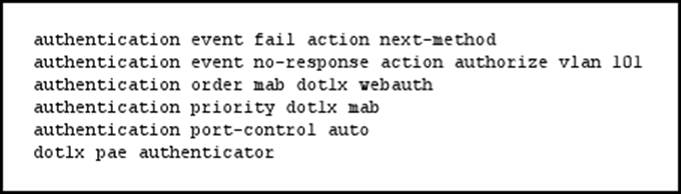
If a supplicant supplies incorrect credentials for all authentication methods configured on the switch, how will the switch respond?
- A . The supplicant will fail to advance beyond the webauth method.
- B . The switch will cycle through the configured authentication methods indefinitely.
- C . The authentication attempt will time out and the switch will place the port into the unauthorized state.
- D . The authentication attempt will time out and the switch will place the port into VLAN 101.
Which EAP method uses Protected Access Credentials?
- A . EAP-FAST
- B . EAP-TLS
- C . EAP-PEAP
- D . EAP-GTC
What is one requirement for locking a wired or wireless device from ISE?
- A . The ISE agent must be installed on the device.
- B . The device must be connected to the network when the lock command is executed.
- C . The user must approve the locking action.
- D . The organization must implement an acceptable use policy allowing device locking.
What VPN feature allows traffic to exit the security appliance through the same interface it entered?
- A . hairpinning
- B . NAT
- C . NAT traversal
- D . split tunneling
Latest 210-260 Dumps Valid Version with 498 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


Hello. And Bye.