Cisco 200-201 Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Online Training
Cisco 200-201 Online Training
The questions for 200-201 were last updated at Jan 31,2026.
- Exam Code: 200-201
- Exam Name: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
- Certification Provider: Cisco
- Latest update: Jan 31,2026
Refer to the exhibit.
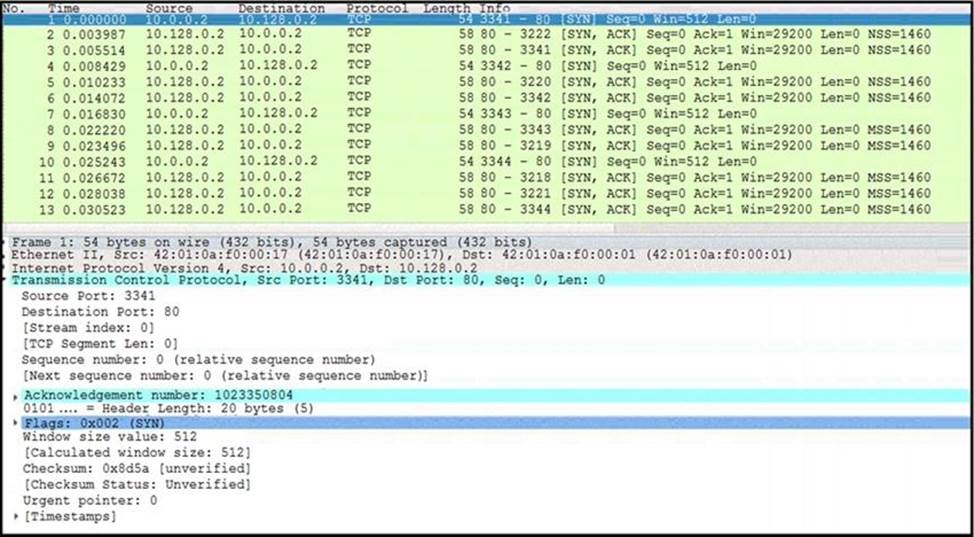
What is occurring in this network traffic?
- A . High rate of SYN packets being sent from a multiple source towards a single destination IP.
- B . High rate of ACK packets being sent from a single source IP towards multiple destination IPs.
- C . Flood of ACK packets coming from a single source IP to multiple destination IPs.
- D . Flood of SYN packets coming from a single source IP to a single destination IP.
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet inspection to identify unknown software by its network traffic flow.
Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
- A . management and reporting
- B . traffic filtering
- C . adaptive AVC
- D . metrics collection and exporting
- E . application recognition
Which security technology guarantees the integrity and authenticity of all messages transferred to and from a web application?
- A . Hypertext Transfer Protocol
- B . SSL Certificate
- C . Tunneling
- D . VPN
An engineer is investigating a case of the unauthorized usage of the “Tcpdump” tool. The analysis revealed that a malicious insider attempted to sniff traffic on a specific interface.
What type of information did the malicious insider attempt to obtain?
- A . tagged protocols being used on the network
- B . all firewall alerts and resulting mitigations
- C . tagged ports being used on the network
- D . all information and data within the datagram
At a company party a guest asks questions about the company’s user account format and password complexity.
How is this type of conversation classified?
- A . Phishing attack
- B . Password Revelation Strategy
- C . Piggybacking
- D . Social Engineering
Which security monitoring data type requires the largest storage space?
- A . transaction data
- B . statistical data
- C . session data
- D . full packet capture
What are two denial of service attacks? (Choose two.)
- A . MITM
- B . TCP connections
- C . ping of death
- D . UDP flooding
- E . code red
An engineer needs to discover alive hosts within the 192.168.1.0/24 range without triggering intrusive portscan alerts on the IDS device using Nmap.
Which command will accomplish this goal?
- A . nmap –top-ports 192.168.1.0/24
- B . nmap CsP 192.168.1.0/24
- C . nmap -sL 192.168.1.0/24
- D . nmap -sV 192.168.1.0/24
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
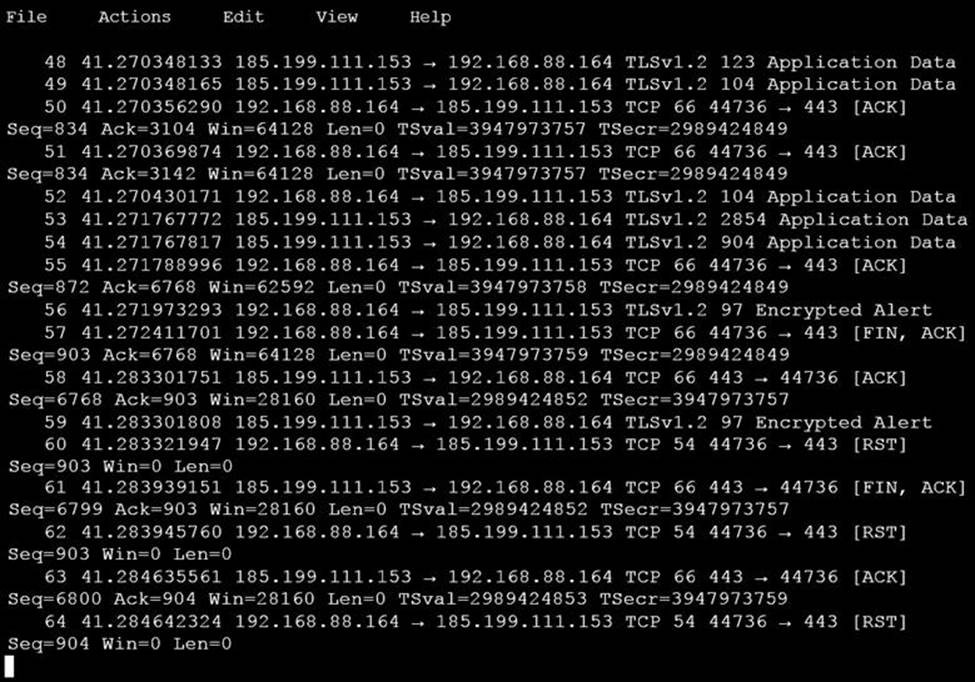
Which obfuscation technique is the attacker using?
- A . Base64 encoding
- B . TLS encryption
- C . SHA-256 hashing
- D . ROT13 encryption
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
- A . Untampered images are used in the security investigation process
- B . Tampered images are used in the security investigation process
- C . The image is tampered if the stored hash and the computed hash match
- D . Tampered images are used in the incident recovery process
- E . The image is untampered if the stored hash and the computed hash match
Latest 200-201 Dumps Valid Version with 154 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

