Cisco 200-201 Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Online Training
Cisco 200-201 Online Training
The questions for 200-201 were last updated at Jan 31,2026.
- Exam Code: 200-201
- Exam Name: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
- Certification Provider: Cisco
- Latest update: Jan 31,2026
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
- A . forgery attack
- B . plaintext-only attack
- C . ciphertext-only attack
- D . meet-in-the-middle attack
Which list identifies the information that the client sends to the server in the negotiation phase of the TLS handshake?
- A . ClientStart, ClientKeyExchange, cipher-suites it supports, and suggested compression methods
- B . ClientStart, TLS versions it supports, cipher-suites it supports, and suggested compression methods
- C . ClientHello, TLS versions it supports, cipher-suites it supports, and suggested compression methods
- D . ClientHello, ClientKeyExchange, cipher-suites it supports, and suggested compression methods
Refer to the exhibit.
Which type of log is displayed?
- A . IDS
- B . proxy
- C . NetFlow
- D . sys
Refer to the exhibit.
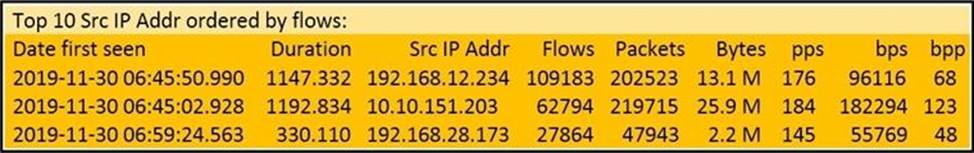
What information is depicted?
- A . IIS data
- B . NetFlow data
- C . network discovery event
- D . IPS event data
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
- A . The RST flag confirms the beginning of the TCP connection, and the ACK flag responds when the data for the payload is complete
- B . The ACK flag confirms the beginning of the TCP connection, and the RST flag responds when the data for the payload is complete
- C . The RST flag confirms the receipt of the prior segment, and the ACK flag allows for the spontaneous termination of a connection
- D . The ACK flag confirms the receipt of the prior segment, and the RST flag allows for the spontaneous termination of a connection
Refer to the exhibit.
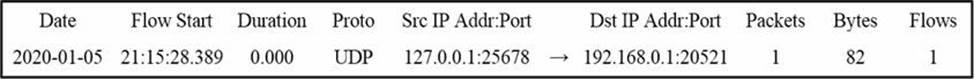
Which type of log is displayed?
- A . proxy
- B . NetFlow
- C . IDS
- D . sys
How is NetFlow different from traffic mirroring?
- A . NetFlow collects metadata and traffic mirroring clones data.
- B . Traffic mirroring impacts switch performance and NetFlow does not.
- C . Traffic mirroring costs less to operate than NetFlow.
- D . NetFlow generates more data than traffic mirroring.
What makes HTTPS traffic difficult to monitor?
- A . SSL interception
- B . packet header size
- C . signature detection time
- D . encryption
How does an attacker observe network traffic exchanged between two users?
- A . port scanning
- B . man-in-the-middle
- C . command injection
- D . denial of service
Which type of data consists of connection level, application-specific records generated from network traffic?
- A . transaction data
- B . location data
- C . statistical data
- D . alert data
Latest 200-201 Dumps Valid Version with 154 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

