Cisco 200-201 Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Online Training
Cisco 200-201 Online Training
The questions for 200-201 were last updated at Jan 31,2026.
- Exam Code: 200-201
- Exam Name: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
- Certification Provider: Cisco
- Latest update: Jan 31,2026
Which open-sourced packet capture tool uses Linux and Mac OS X operating systems?
- A . NetScout
- B . tcpdump
- C . SolarWinds
- D . netsh
Refer to the exhibit.
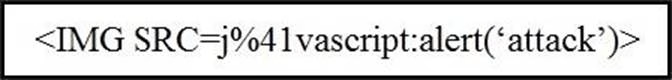
Which kind of attack method is depicted in this string?
- A . cross-site scripting
- B . man-in-the-middle
- C . SQL injection
- D . denial of service
Which two components reduce the attack surface on an endpoint? (Choose two.)
- A . secure boot
- B . load balancing
- C . increased audit log levels
- D . restricting USB ports
- E . full packet captures at the endpoint
What is an attack surface as compared to a vulnerability?
- A . any potential danger to an asset
- B . the sum of all paths for data into and out of the environment
- C . an exploitable weakness in a system or its design
- D . the individuals who perform an attack
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email. When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
- A . social engineering
- B . eavesdropping
- C . piggybacking
- D . tailgating
What are two social engineering techniques? (Choose two.)
- A . privilege escalation
- B . DDoS attack
- C . phishing
- D . man-in-the-middle
- E . pharming
Refer to the exhibit.
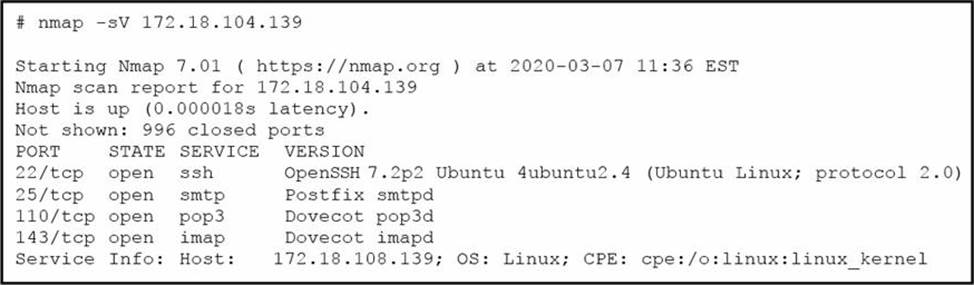
What does the output indicate about the server with the IP address 172.18.104.139?
- A . open ports of a web server
- B . open port of an FTP server
- C . open ports of an email server
- D . running processes of the server
How does certificate authority impact a security system?
- A . It authenticates client identity when requesting SSL certificate
- B . It validates domain identity of a SSL certificate
- C . It authenticates domain identity when requesting SSL certificate
- D . It validates client identity when communicating with the server
When communicating via TLS, the client initiates the handshake to the server and the server
responds back with its certificate for identification.
Which information is available on the server certificate?
- A . server name, trusted subordinate CA, and private key
- B . trusted subordinate CA, public key, and cipher suites
- C . trusted CA name, cipher suites, and private key
- D . server name, trusted CA, and public key
How does an SSL certificate impact security between the client and the server?
- A . by enabling an authenticated channel between the client and the server
- B . by creating an integrated channel between the client and the server
- C . by enabling an authorized channel between the client and the server
- D . by creating an encrypted channel between the client and the server
Latest 200-201 Dumps Valid Version with 154 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

