Cisco 200-201 Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Online Training
Cisco 200-201 Online Training
The questions for 200-201 were last updated at Jan 31,2026.
- Exam Code: 200-201
- Exam Name: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
- Certification Provider: Cisco
- Latest update: Jan 31,2026
What is a difference between SOAR and SIEM?
- A . SOAR platforms are used for threat and vulnerability management, but SIEM applications are not
- B . SIEM applications are used for threat and vulnerability management, but SOAR platforms are not
- C . SOAR receives information from a single platform and delivers it to a SIEM
- D . SIEM receives information from a single platform and delivers it to a SOAR
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?
- A . MAC is controlled by the discretion of the owner and DAC is controlled by an administrator
- B . MAC is the strictest of all levels of control and DAC is object-based access
- C . DAC is controlled by the operating system and MAC is controlled by an administrator
- D . DAC is the strictest of all levels of control and MAC is object-based access
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
- A . least privilege
- B . need to know
- C . integrity validation
- D . due diligence
What is the virtual address space for a Windows process?
- A . physical location of an object in memory
- B . set of pages that reside in the physical memory
- C . system-level memory protection feature built into the operating system
- D . set of virtual memory addresses that can be used
Which security principle is violated by running all processes as root or administrator?
- A . principle of least privilege
- B . role-based access control
- C . separation of duties
- D . trusted computing base
What is the function of a command and control server?
- A . It enumerates open ports on a network device
- B . It drops secondary payload into malware
- C . It is used to regain control of the network after a compromise
- D . It sends instruction to a compromised system
What is the difference between deep packet inspection and stateful inspection?
- A . Deep packet inspection is more secure than stateful inspection on Layer 4
- B . Stateful inspection verifies contents at Layer 4 and deep packet inspection verifies connection at Layer 7
- C . Stateful inspection is more secure than deep packet inspection on Layer 7
- D . Deep packet inspection allows visibility on Layer 7 and stateful inspection allows visibility on Layer 4
Which evasion technique is a function of ransomware?
- A . extended sleep calls
- B . encryption
- C . resource exhaustion
- D . encoding
Refer to the exhibit.
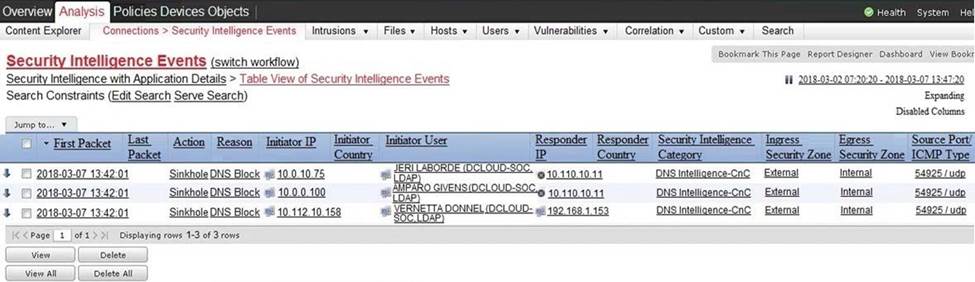
Which two elements in the table are parts of the 5-tuple? (Choose two.)
- A . First Packet
- B . Initiator User
- C . Ingress Security Zone
- D . Source Port
- E . Initiator IP
DRAG DROP
Drag and drop the security concept on the left onto the example of that concept on the right.

Latest 200-201 Dumps Valid Version with 154 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


