As the ISMS audit team leader, you are conducting a second-party audit of an international logistics company on behalf of an online retailer. During the audit, one of your team members reports a nonconformity relating to control 5.18 (Access rights) of Appendix A of ISO/IEC 27001:2022. She found evidence that removing the server access protocols of 20 people who left in the last 3 months took up to 1 week whereas the policy required removing access within 24 hours of their departure
DRAG DROP
As the ISMS audit team leader, you are conducting a second-party audit of an international logistics company on behalf of an online retailer. During the audit, one of your team members reports a nonconformity relating to control 5.18 (Access rights) of Appendix A of ISO/IEC 27001:2022. She found evidence that removing the server access protocols of 20 people who left in the last 3 months took up to 1 week whereas the policy required removing access within 24 hours of their departure.
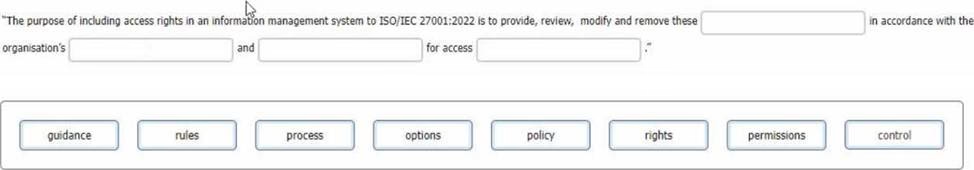
Complete the sentence with the best word(s), dick on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the option to the appropriate blank section.
Answer: 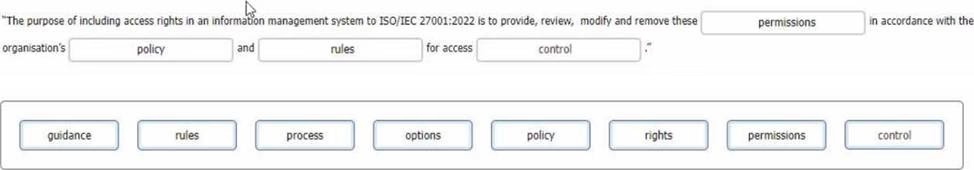
Explanation:
The purpose of including access rights in an information management system to ISO/IEC 27001:2022 is to provide, review, modify and remove these permissions in accordance with the organisation’s policy and rules for access control.
Access rights are the permissions granted to users or groups of users to access, use, modify, or delete information assets. Access rights should be aligned with the organisation’s access control policy, which defines the objectives, principles, roles, and responsibilities for managing access to information systems. Access rights should also follow the organisation’s rules for access control, which specify the criteria, procedures, and controls for granting, reviewing, modifying, and revoking access rights. The purpose of including access rights in an information management system is to ensure that only authorised users can access information assets according to their business needs and roles, and to prevent unauthorised or inappropriate access that could compromise the confidentiality, integrity, or availability of information assets.
Reference: ISO/IEC 27001:2022 Annex A Control 5.181
ISO/IEC 27002:2022 Control 5.182
CQI & IRCA Certified ISO/IEC 27001:2022 Lead Auditor (Information Security Management Systems) Training Course3

