Amazon SOA-C02 AWS Certified SysOps Administrator – Associate Online Training
Amazon SOA-C02 Online Training
The questions for SOA-C02 were last updated at Feb 27,2026.
- Exam Code: SOA-C02
- Exam Name: AWS Certified SysOps Administrator - Associate
- Certification Provider: Amazon
- Latest update: Feb 27,2026
A SysOps administrator noticed that a large number of Elastic IP addresses are being created on the company’s AWS account, but they are not being associated with Amazon EC2 instances, and are incurring Elastic IP address charges in the monthly bill.
How can the administrator identify who is creating the Elastic IP addresses?
- A . Attach a cost-allocation tag to each requested Elastic IP address with the IAM user name of the developer who creates it.
- B . Query AWS CloudTrail logs by using Amazon Athena to search for Elastic IP address events.
- C . Create a CloudWatch alarm on the ElPCreated metric and send an Amazon SNS notification when the alarm triggers.
- D . Use Amazon Inspector to get a report of all Elastic IP addresses created in the last 30 days.
A company has an Amazon CloudFront distribution that uses an Amazon S3 bucket as its origin. During a review of the access logs, the company determines that some requests are going directly to the S3 bucket by using the website hosting endpoint. A SysOps administrator must secure the S3 bucket to allow requests only from CloudFront.
What should the SysOps administrator do to meet this requirement?
- A . Create an origin access identity (OAI) in CloudFront. Associate the OAI with the distribution. Remove access to and from other principals in the S3 bucket policy. Update the S3 bucket policy to allow access only from the OAI.
- B . Create an origin access identity (OAI) in CloudFront. Associate the OAI with the distribution. Update the S3 bucket policy to allow access only from the OAI. Create a new origin, and specify the S3 bucket as the new origin. Update the distribution behavior to use the new origin. Remove the existing origin.
- C . Create an origin access identity (OAI) in CloudFront. Associate the OAI with the distribution. Update the S3 bucket policy to allow access only from the OAI. Disable website hosting. Create a new origin, and specify the S3 bucket as the new origin. Update the distribution behavior to use the new origin. Remove the existing origin.
- D . Update the S3 bucket policy to allow access only from the CloudFront distribution. Remove access to and from other principals in the S3 bucket policy. Disable website hosting. Create a new origin, and specify the S3 bucket as the new origin. Update the distribution behavior to use the new origin. Remove the existing origin.
A SysOps administrator must create an IAM policy for a developer who needs access to specific AWS services.
Based on the requirements, the SysOps administrator creates the following policy:
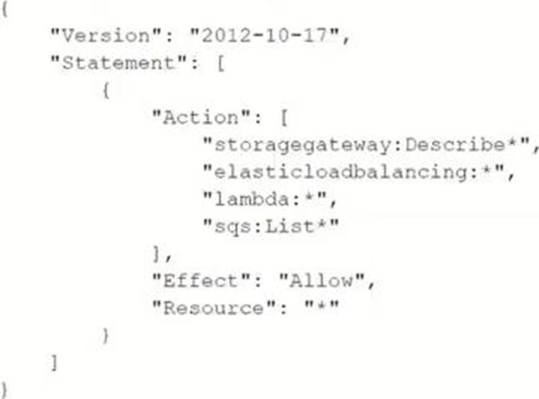
Which actions does this policy allow? (Select TWO.)
- A . Create an AWS Storage Gateway.
- B . Create an IAM role for an AWS Lambda function.
- C . Delete an Amazon Simple Queue Service (Amazon SQS) queue.
- D . Describe AWS load balancers.
- E . Invoke an AWS Lambda function.
A company is trying to connect two applications. One application runs in an on-premises data center that has a hostname of hostl .onprem.private. The other application runs on an Amazon EC2 instance that has a hostname of hostl.awscloud.private. An AWS Site-to-Site VPN connection is in place between the on-premises network and AWS.
The application that runs in the data center tries to connect to the application that runs on the EC2 instance, but DNS resolution fails. A SysOps administrator must implement DNS resolution between on-premises and AWS resources.
Which solution allows the on-premises application to resolve the EC2 instance hostname?
- A . Set up an Amazon Route 53 inbound resolver endpoint with a forwarding rule for the onprem.private hosted zone. Associate the resolver with the VPC of the EC2 instance. Configure the on-premises DNS resolver to forward onprem.private DNS queries to the inbound resolver endpoint.
- B . Set up an Amazon Route 53 inbound resolver endpoint. Associate the resolver with the VPC of the EC2 instance. Configure the on-premises DNS resolver to forward awscloud.private DNS queries to the inbound resolver endpoint.
- C . Set up an Amazon Route 53 outbound resolver endpoint with a forwarding rule for the onprem.private hosted zone. Associate the resolver with the AWS Region of the EC2 instance. Configure the on-premises DNS resolver to forward onprem.private DNS queries to the outbound resolver endpoint.
- D . Set up an Amazon Route 53 outbound resolver endpoint. Associate the resolver with the AWS Region of the EC2 instance. Configure the on-premises DNS resolver to forward awscloud.private DNS queries to the outbound resolver endpoint.
While setting up an AWS managed VPN connection, a SysOps administrator creates a customer gateway resource in AWS. The customer gateway device resides in a data center with a NAT gateway in front of it.
What address should be used to create the customer gateway resource?
- A . The private IP address of the customer gateway device
- B . The MAC address of the NAT device in front of the customer gateway device
- C . The public IP address of the customer gateway device
- D . The public IP address of the NAT device in front of the customer gateway device
A large company is using AWS Organizations to manage its multi-account AWS environment. According to company policy, all users should have read-level access to a particular Amazon S3 bucket in a central account. The S3 bucket data should not be available outside the organization. A SysOps administrator must set up the permissions and add a bucket policy to the S3 bucket.
Which parameters should be specified to accomplish this in the MOST efficient manner?
- A . Specify "’ as the principal and PrincipalOrgld as a condition.
- B . Specify all account numbers as the principal.
- C . Specify PrincipalOrgld as the principal.
- D . Specify the organization’s management account as the principal.
A SysOps administrator is attempting to download patches from the internet into an instance in a private subnet. An internet gateway exists for the VPC, and a NAT gateway has been deployed on the public subnet; however, the instance has no internet connectivity. The resources deployed into the private subnet must be inaccessible directly from the public internet.
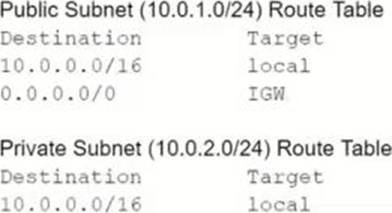
What should be added to the private subnet’s route table in order to address this issue, given the information provided?
- A . 0.0.0.0/0 IGW
- B . 0.0.0.0/0 NAT
- C . 10.0.1.0/24 IGW
- D . 10.0.1.0/24 NAT
A SysOps administrator applies the following policy to an AWS CloudFormation stack:
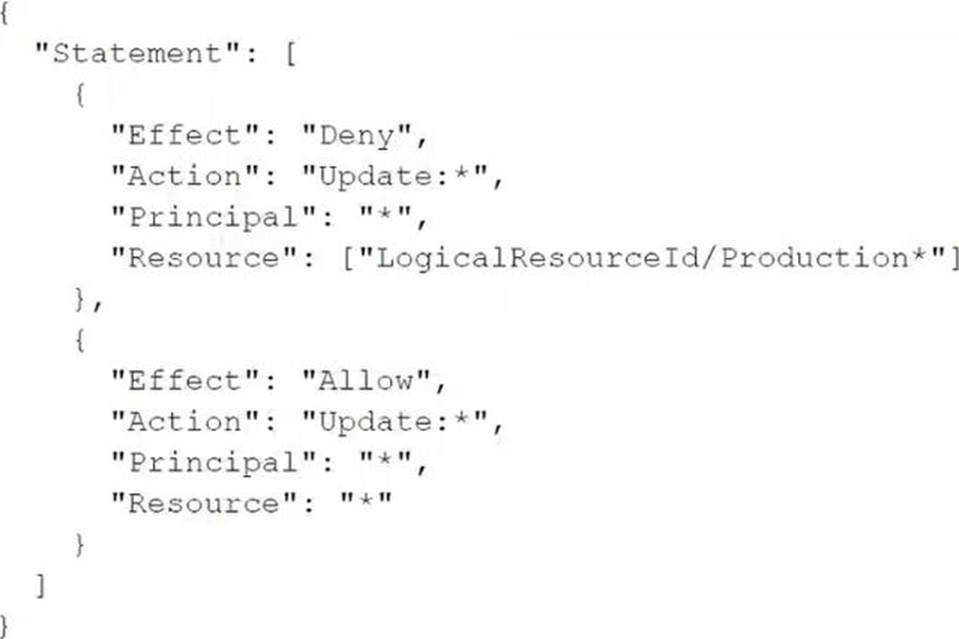
What is the result of this policy?
- A . Users that assume an IAM role with a logical ID that begins with "Production" are prevented from running the update-stack command.
- B . Users can update all resources in the stack except for resources that have a logical ID that begins with "Production".
- C . Users can update all resources in the stack except for resources that have an attribute that begins with "Production".
- D . Users in an IAM group with a logical ID that begins with "Production" are prevented from running the update-stack command.
A company’s IT department noticed an increase in the spend of their developer AWS account. There are over 50 developers using the account, and the finance team wants to determine the service costs incurred by each developer.
What should a SysOps administrator do to collect this information? (Select TWO.)
- A . Activate the createdBy tag in the account.
- B . Analyze the usage with Amazon CloudWatch dashboards.
- C . Analyze the usage with Cost Explorer.
- D . Configure AWS Trusted Advisor to track resource usage.
- E . Create a billing alarm in AWS Budgets.
A company website contains a web tier and a database tier on AWS. The web tier consists of Amazon EC2 instances that run in an Auto Scaling group across two Availability Zones. The database tier runs on an Amazon ROS for MySQL Multi-AZ DB instance. The database subnet network ACLs are restricted to only the web subnets that need access to the database. The web subnets use the default network ACL with the default rules.
The company’s operations team has added a third subnet to the Auto Scaling group configuration. After an Auto Scaling event occurs, some users report that they intermittently receive an error
message. The error message states that the server cannot connect to the database. The operations team has confirmed that the route tables are correct and that the required ports are open on all security groups.
Which combination of actions should a SysOps administrator take so that the web servers can communicate with the DB instance? (Select TWO.)
- A . On the default ACL. create inbound Allow rules of type TCP with the ephemeral port range and the source as the database subnets.
- B . On the default ACL, create outbound Allow rules of type MySQL/Aurora (3306). Specify the destinations as the database subnets.
- C . On the network ACLs for the database subnets, create an inbound Allow rule of type MySQL/Aurora (3306). Specify the source as the third web subnet.
- D . On the network ACLs for the database subnets, create an outbound Allow rule of type TCP with the ephemeral port range and the destination as the third web subnet.
- E . On the network ACLs for the database subnets, create an outbound Allow rule of type MySQL/Aurora (3306). Specify the destination as the third web subnet.
Latest SOA-C02 Dumps Valid Version with 54 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

