Amazon DVA-C01 AWS Certified Developer – Associate Online Training
Amazon DVA-C01 Online Training
The questions for DVA-C01 were last updated at Mar 02,2026.
- Exam Code: DVA-C01
- Exam Name: AWS Certified Developer – Associate
- Certification Provider: Amazon
- Latest update: Mar 02,2026
A development team is creating a new application designed to run on AWS. While the test and production environments will run on Amazon EC2 instances, developers will each run their own environment on their laptops.
Which of the following is the simplest and MOST secure way to access AWS services from the local development machines?
- A . Use an IAM role to assume a role and execute API calls using the role.
- B . Create an IAM user to be shared with the entire development team, provide the development team with the access key.
- C . Create an IAM user for each developer on the team: provide each developer with a unique access key
- D . Set up a federation through an Amazon Cognito user pool.
A Developer must repeatedly and consistently deploy a serverless RESTful API on AWS.
Which techniques will work? (Choose two.)
- A . Define a Swagger file. Use AWS Elastic Beanstalk to deploy the Swagger file.
- B . Define a Swagger file. Use AWS CodeDeploy to deploy the Swagger file.
- C . Deploy a SAM template with an inline Swagger definition.
- D . Define a Swagger file. Deploy a SAM template that references the Swagger file.
- E . Define an inline Swagger definition in a Lambda function. Invoke the Lambda function.
An ecommerce startup is preparing for an annual sales event As the traffic to the company’s application increases, the development team wants to be notified when the Amazon EC2 instance’s CPU utilization exceeds 80%.
Which solution will meet this requirement?
- A . Create a custom Amazon CloudWatch alarm that sends a notification to an Amazon SNS topic when the CPU utilization exceeds 80%.
- B . Create a custom AWS CloudTrail alarm that sends a notification to an Amazon SNS topic when the CPU utilization exceeds 80%
- C . Create a cron job on the EC2 instance that executes the –describe-instance-information command on the host instance every 15 minutes and sends the results to an Amazon SNS topic
- D . Create an AWS Lambda function that queries the AWS CloudTrail logs for the CPU Utihzation metric every 15 minutes and sends a notification to an Amazon SNS topic when the CPU utilization exceeds 80%
A Developer is testing a Docker-based application that uses the AWS SDK to interact with Amazon
DynamoDB. In the local development environment, the application has used IAM access keys. The application is now ready for deployment onto an ECS cluster.
How should the application authenticate with AWS services in production?
- A . Configure an ECS task IAM role for the application to use
- B . Refactor the application to call AWS STS AssumeRole based on an instance role
- C . Configure AWS access key/secret access key environment variables with new credentials
- D . Configure the credentials file with a new access key/secret access key
A developer wants the ability to roll back to a previous version of an AWS Lambda function in the event of errors caused by a new deployment.
How can the developer achieve this with MINIMAL impact on users?
- A . Change the application to use an alias that points to the current version Deploy the new version of the code Update the alias to use the newly deployed version. If too many errors are encountered, point the alias back to the previous version
- B . Change the application to use an alias that points to the current version Deploy the new version of the code. Update the alias to direct 10% of users to the newly deployed version. If too many errors are encountered, send 100% of traffic to the previous version
- C . Do not make any changes to the application Deploy the new version of the code. If too
many errors are encountered, point the application back to the previous version using the version number in the Amazon Resource Name (ARN) - D . Create three aliases: new, existing, and router Point the existing alias to the current version Have the router alias direct 100% of users to the existing alias Update the application to use the router alias Deploy the new version of the code Point the new alias to this version Update the router alias to direct 10% of users to the new alias If too many errors are encountered, send 100% of traffic to the existing alias
A company is developing a serverless ecommerce web application. The application needs to make coordinated, all-or-nothing changes to multiple items in the company’s inventory table in Amazon DynamoDB.
Which solution will meet these requirements?
- A . Enable transactions for the DynamoDB table Use the Batch Writeltem operation to update the items.
- B . Use the Transact Writeitem operation to group the changes Update the items in the table
- C . Set up a FIFO queue using Amazon SQS. Group the changes in the queue. Update the table based on the grouped changes
- D . Create a transaction table in an Amazon Aurora DB cluster to manage the transactions Write a backend process to sync the Aurora DB table and the DynamoDB table
A legacy service has an XML-based SOAP interface. The Developer wants to expose the functionality of the service to external clients with the Amazon API Gateway .
Which technique will accomplish this?
- A . Create a RESTful API with the API Gateway; transform the incoming JSON into a valid XML message for the SOAP interface using mapping templates.
- B . Create a RESTful API with the API Gateway; pass the incoming JSON to the SOAP interface through an Application Load Balancer.
- C . Create a RESTful API with the API Gateway; pass the incoming XML to the SOAP interface through an Application Load Balancer.
- D . Create a RESTful API with the API Gateway; transform the incoming XML into a valid message for the
SOAP interface using mapping templates.
A Developer executed a AWS CLI command and received the error shown below:
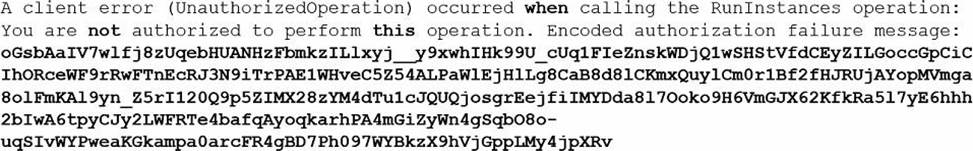
What action should the Developer perform to make this error human-readable?
- A . Make a call to AWS KMS to decode the message.
- B . Use the AWS STS decode-authorization-message API to decode the message.
- C . Use an open source decoding library to decode the message.
- D . Use the AWS IAM decode-authorization-message API to decode this message.
Which of the following services are key/value stores? Choose 3 answers
- A . Amazon ElastiCache
- B . Simple Notification Service
- C . DynamoDB
- D . Simple Workflow Service
- E . Simple Storage Service
A developer is building an application that needs to store date in Amazon S3. Management requires that the data be encrypted before is it sent to Amazon S3 for storage. The encryption keys need to be managed by the security team.
Which approach should the developer take to meet these requirements?
- A . Implement server-side encryption using customer-provided encryption keys (SSE-C).
- B . Implement server-side encryption by using client-side master key.
- C . Implement client-side encryption using an AWS KMS managed customer master key (CMK).
- D . Implement Client-side encryption using Amazon S3 managed keys.
Latest DVA-C01 Dumps Valid Version with 463 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

